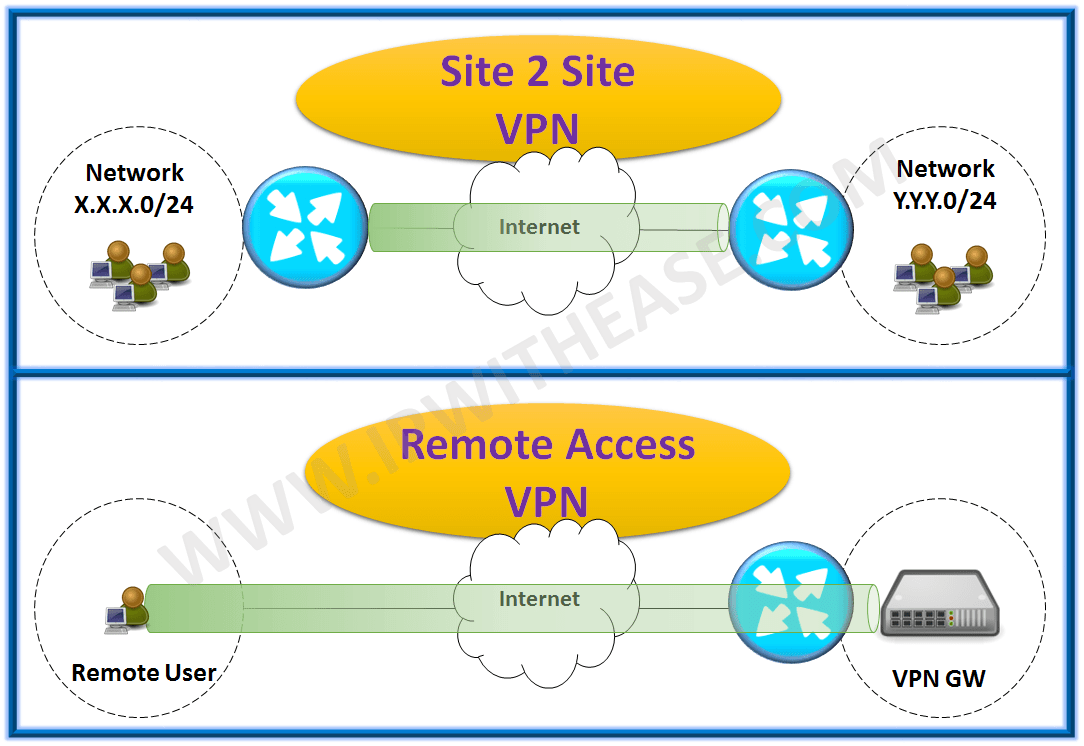
PPTP (remote access) Using the Point-to-Point Tunneling Protocol (PPTP), you can provide connections to your network through private tunnels over the internet. The protocol itself does not describe encryption or authentication features.
- Note: ...
- 1) Click Add. ...
- Select Connect to a workplace and click Next. ...
- Enter the internet IP address of the router (for example: 218.18. ...
- Enter the User name and Password you have set for the PPTP VPN server on your router, and click Connect.
How to configure PPTP VPN connection on your remote device?
Configure the PPTP VPN connection account for the remote device, you can create up to 16 accounts. 1) Click Add. 2) Enter the Username and Password to authenticate devices to the PPTP VPN Server. 3) Click OK. Step 2. Configure PPTP VPN Connection on Your Remote Device
How to set the PPTP connection permission?
In the Client IP Address filed, enter the range of IP addresses (up to 10) that can be leased to the devices by the PPTP VPN server. 4. Click Advanced to set the PPTP connection permission according to your needs.
How do I set up a VPN on my computer?
Go to Start > Control Panel > Network and Internet > Network and Sharing Center. 2. Select Set up a new connection or network. 3. Select Connect to a workplace and click Next. 4. Select Use my Internet connection (VPN). 5. Enter the internet IP address of the router (for example: 218.18.1.73) in the Internet address field. Click Next.
What should I do Before I enable VPN Server?
Before you enable VPN Server, we recommend you configure Dynamic DNS Service (recommended) or assign a static IP address for router’s WAN port and synchronize your System Time with internet.

What is PPTP remote access?
Point-to-Point Tunneling Protocol allows organizations to extend their own private network through private tunnels over the public Internet.
What is PPTP VPN?
PPTP (Point-to-Point Tunneling Protocol) is a VPN protocol that's used to ensure proper communications between a VPN client and a VPN server. It got its start in 1995 on Windows platforms, but is now available on many other operating systems and devices too.
What is the authentication protocol for a PPTP based remote access to a network?
PPTP connections are encrypted through Microsoft Point-to-Point Encryption (MPPE), which uses the Rivest-Shamir-Aldeman (RSA) RC-4 encryption algorithm. PPTP connections require user-level authentication through a PPP-based authentication protocol (MSCHAPv2 is the currently-supported method).
How a PPTP connection works?
As a tunneling protocol, PPTP encapsulates network protocol datagrams within an IP envelope. After the packet is encapsulated, any router or machine that encounters it from that point on will treat it as an IP packet.
Is PPTP VPN safe?
PPTP provides weak protection to the integrity of the data being tunneled. The RC4 cipher, while providing encryption, does not verify the integrity of the data as it is not an Authenticated Encryption with Associated Data (AEAD) cipher.
What port does PPTP VPN use?
TCP port 1723Point-to-Point Tunneling Protocol (PPTP) uses TCP port 1723 and IP protocol 47 Generic Routing Encapsulation (GRE). PPTP provides a low-cost, private connection to a corporate network through the Internet.
What protocols does PPTP use?
PPTP uses Generic Routing Encapsulation (GRE) to pass PPP via IP, and uses TCP for a control channel (using TCP port 1723). The Layer 2 Tunneling Protocol (L2TP) combines PPTP and Layer 2 Forwarding (L2F), designed to tunnel PPP.
Does PPTP change IP address?
If you are using PPTP on your Mac and it appears to connect but does not change your IP address, it sounds as if you may have missed a step during the setup of the VPN.
What is the server address for PPTP?
Setting up your Android Device for VPN PPTP Protocol: In the Set VPN Server field, enter us-ny2.serverlocation.co or any other server address you want to get connected.
Why is PPTP still used?
In spite of its age and security shortcomings, PPTP is still used in some network implementations—mostly internal business VPNs in older offices. The advantages of PPTP are that it's easy to set up, it's fast, and because it's built-in on most platforms, you don't need any special software to use it.
When should you use PPTP?
PPTP has mostly outlived its usefulness, but it's still one of the most common protocols thanks to its speed and ease of setup....Best Uses for PPTP:Torrent downloading.Streaming/Unblocking.Access websites with usage or location restrictions.Use on devices where other protocols are unavailable or unstable.
Is PPTP used today?
Nowadays, PPTP is considered obsolete for use in VPN's because of its many known security deficiencies. Nevertheless, PPTP is still in use in some networks. The phrase Point to Point refers to the specific type of connection created by the protocol.
When should you use PPTP?
PPTP has mostly outlived its usefulness, but it's still one of the most common protocols thanks to its speed and ease of setup....Best Uses for PPTP:Torrent downloading.Streaming/Unblocking.Access websites with usage or location restrictions.Use on devices where other protocols are unavailable or unstable.
Which is better PPTP or L2TP?
Conclusion: PPTP VPN is easy to setup and use with faster speeds, but can result in a less secure connection. L2TP VPN, on the other hand, has slower speeds, but offers stronger security which makes it a good choice.
Which is better OpenVPN or PPTP?
Conclusion. PPTP has faster speeds and is easier to set up but offers a poorly secured connection. On the other hand, OpenVPN provides decent speeds and excellent security, plus it's great at circumventing geo-blocks and firewalls undetected.
What type of VPN is best?
Blazing speeds, proven privacy ExpressVPN is currently the fastest VPN we've tested in 2022, causing us to lose less than 2% of our total internet speeds. Its apps for iOS and Android are designed with a streamlined approach aimed at connecting fast without a fuss.
Introduction
Although VPN's are considered as an extension of a private network, in reality they are nothing close to the equivalent of a private network. This is so because you can't compare physically connected devices in a closed environment to a remote connection.
A step-by-step guide
The following is a step-by-step guide of how to setup a client based VPN connection using the Point to Point Tunneling protocol.
Chapter Description
This chapter will focus on using a concentrator to terminate other types of remote access sessions, including PPTP, L2TP over IPsec, and WebVPN. The remainder of this chapter will focus on the configuration of the concentrator to support these types of remote access VPN implementations.
From the Book
The last chapter introduced how to configure the VPN 3000 concentrators to accept IPsec remote access sessions. This chapter will focus on using a concentrator to terminate other types of remote access sessions, including: