
Privileged Remote Access handles creating and managing the access to the endpoint, as well as recording and controlling the level of access granted to the user. This includes what the user can see and do on that endpoint.
Full Answer
What is privileged remote access and how does it work?
Privileged Remote Access enables security professionals to control, monitor, and manage privileged access to critical systems. Privileged Remote Access eliminates the need for privileged users to remember or share credentials for the systems they need to access. Passwords can be stored in the on-appliance vault.
How to configure privileged access workstation and privileged endpoint access?
Privileged Access Workstation and privileged endpoint access 1 Configuring the WinRM. To allow connections to the privileged endpoint from the PAW, ensure that the privileged endpoint IP addresses, as defined in the Azure Stack Hub Admin Portal, are ... 2 Connect to the privileged endpoint. ... 3 Close the privileged endpoint 4 Further reading. ...
What is the privileged endpoint (Pep)?
However, for some less common operations, you need to use the privileged endpoint (PEP). The PEP is a pre-configured remote PowerShell console that provides you with just enough capabilities to help you do a required task. The endpoint uses PowerShell JEA (Just Enough Administration) to expose only a restricted set of cmdlets.
How do I allow connections to the privileged endpoint from the paw?
To allow connections to the privileged endpoint from the PAW, ensure that the privileged endpoint IP addresses, as defined in the Azure Stack Hub Admin Portal, are set as a trusted host on the PAW. The instructions for obtaining these IP addresses from the Administrator Portal are in Verifying scale unit node access and health on page 16.
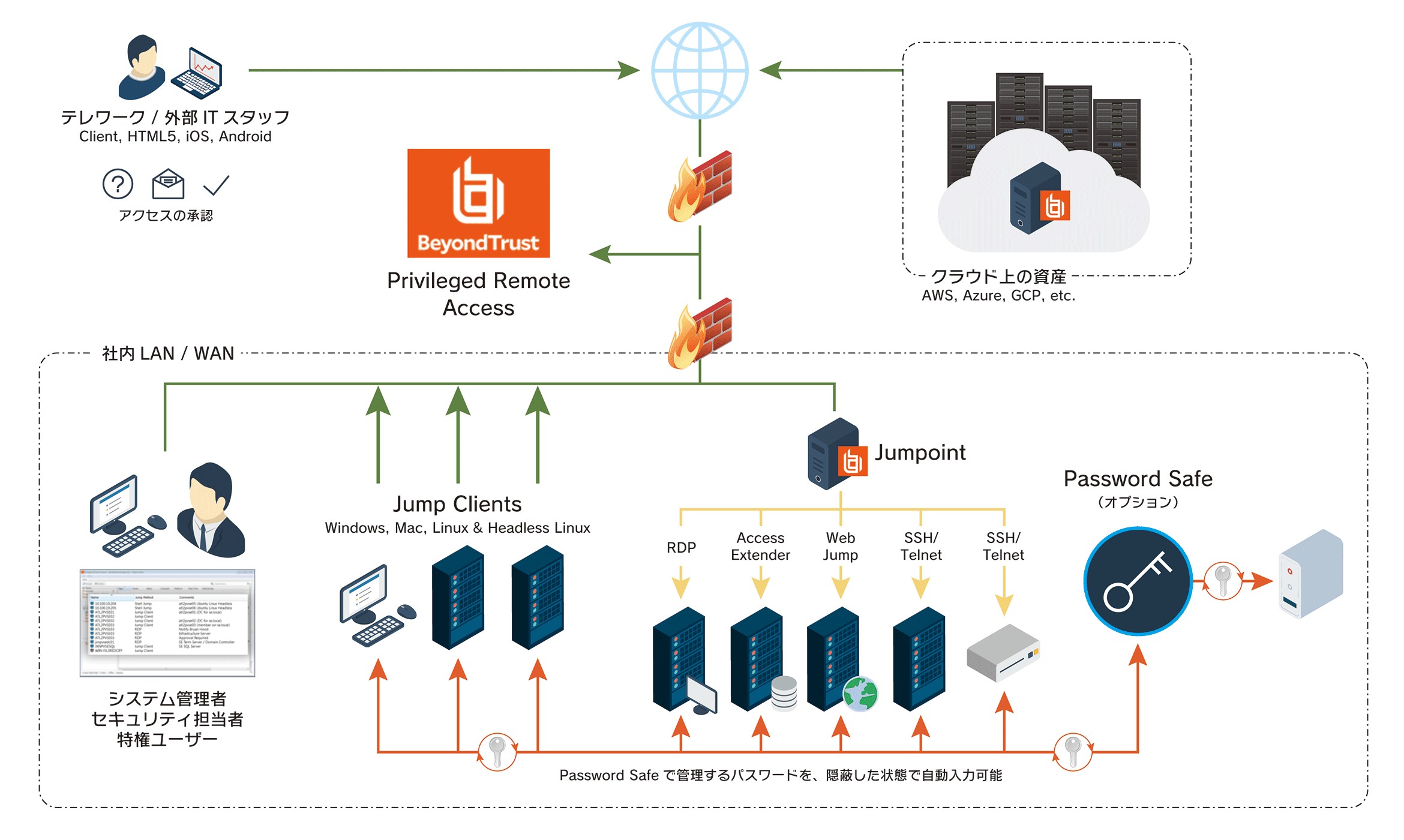
What is privileged remote access?
Privileged remote access is about ensuring employees, third-party vendors, and other insiders don't have free access to systems while accessing the network remotely. You're able to define who has permissions, when they have it, and the appropriate level of access each role needs to complete their work.
What is Endpoint privilege management?
Endpoint privilege management is the process of governing privileges so that admin privileges aren't excessively distributed among users. This prevents users from exploiting functions beyond their requirements, which is a common risk of elevating the entire user account privilege.
What is BeyondTrust PRA?
The BeyondTrust Privileged Remote Access (PRA) Integration Client is used to transfer session logs and recordings from the BeyondTrust Appliance B Series to an external system. Two external systems are currently supported: Microsoft SQL Server and Windows-based file systems.
What is BeyondTrust remote?
BeyondTrust Remote Support Software enables support organizations to access and support nearly any remote computer or mobile device. Troubleshoot PCs and servers, provide remote assistance, train remote employees, or perform system maintenance . . . all with the highest levels of security.
Is CyberArk a PIM?
Cyber-Ark's Enterprise Password Vault® (EPV), part of the PIM Suite, enables organisations to enforce an enterprise policy to protect the most critical systems, managing the entire lifecycle of shared and privileged accounts across data centres.
What is CyberArk endpoint?
CyberArk Endpoint Privilege Manager (EPM) enforces least privilege and allows organizations to block and contain attacks at the endpoint, reducing the risk of information being stolen or encrypted and held for ransom.
How do I use BeyondTrust?
Simply copy the URL and paste it in an email to your customer. Clicking the link will initiate a download of the BeyondTrust Custom Client. Once the user has followed the prompts to run the BeyondTrust Custom Client, his session should appear in your Personal queue on the Sessions tab.
What is BeyondTrust remote support Jump client?
A Jump Client is an installable application that enables a user to access a remote computer, regardless of its location. The remote computer does not need to reside on a known network.
How do I log into Bomgar?
By default, in Windows, you can access the console from Start Menu > All Programs > Bomgar > access.example.com, where access.example.com is the hostname of the site from which you downloaded the console. If the Login Agreement has been enabled, you must click Accept to proceed.
Is BeyondTrust the same as Bomgar?
Bomgar Is Now BeyondTrust, but Some Things Haven't Changed. New Name, Same Leading Support Software. Bomgar is still the most secure remote support software in the world. Now called BeyondTrust Remote Support, it's trusted by more customers than ever before.
When did bomgar become BeyondTrust?
October 3, 2018Editor's Note: Bomgar's acquisition of BeyondTrust was completed on October 3, 2018.
Is bomgar safe?
BeyondTrust (Bomgar) is a safe secure and private way to allow the support personnel to view and control your computer. Your technician will not be able to view any information you do not want them to see and you will be able to see what they are doing at all times.
What is CyberArk endpoint Privilege Manager?
CyberArk Endpoint Privilege Manager (EPM) helps to remove the barriers to enforcing least privilege and allows organizations to block and contain attacks at the endpoint, reducing the risk of information being stolen or encrypted and held for ransom.
What is privileged account manager?
Privileged account management can be defined as managing and auditing account and data access by privileged users. A privileged user is someone who has administrative access to critical systems. For instance, anyone who can set up and delete user accounts and roles on your Oracle database is a privileged user.
What is EPM security?
EPM security controls access to specific data within the EPM database and enables you to grant users access to specific rows, columns, or fields in an EPM database table.
What is CyberArk privileged account security?
The CyberArk's Privileged Access Security (PAS) solution is a full life-cycle solution for managing the most privileged accounts and SSH Keys in the enterprise.
What is a PEP endpoint?
How to use the privileged endpoint. As mentioned above, the PEP is a PowerShell JEA endpoint. While providing a strong security layer, a JEA endpoint reduces some of the basic PowerShell capabilities, such as scripting or tab completion.
How to access PEP?
You access the PEP through a remote PowerShell session on the virtual machine (VM) that hosts the PEP. In the ASDK, this VM is named AzS-ERCS01. If you're using an integrated system, there are three instances of the PEP, each running inside a VM ( Prefix -ERCS01, Prefix -ERCS02, or Prefix -ERCS03) on different hosts for resiliency.
What is PEP token?
The PEP support session request and authorization tokens leverage cryptography to protect access and ensure that only authorized tokens can unlock the PEP session. The tokens are designed to cryptographically guarantee that a response token can only be accepted by the PEP session that generated the request token. PEP tokens do not contain any kind of information that could uniquely identify an Azure Stack Hub environment or a customer. They are completely anonymous. Below the details of the content of each token are provided.
What happens if you fail to execute a PEP session?
Failure to do so could result in serious downtime, data loss and could require a full redeployment of the Azure Stack Hub environment.
What is a cmdlet in PowerShell?
The cmdlet returns the support session request token, a very long alphanumeric string. The operator then passes the request token to the Microsoft support engineer via a medium of their choice (e.g., chat, email). The Microsoft support engineer uses the request token to generate, if valid, a support session authorization token and sends it back to the Azure Stack Hub operator. On the same PEP PowerShell session, the operator then passes the authorization token as input to this cmdlet:
How to close a PEP session?
You must close the session by using the Close-PrivilegedEndpoint cmdlet. This cmdlet correctly closes the endpoint, and transfers the log files to an external file share for retention.
What is the user name of ASDK?
User name: Specify the CloudAdmin account, in the format <Azure Stack Hub domain>cloudadmin. (For ASDK, the user name is azurestackcloudadmin)
How to limit access to specific applications on remote Windows?
Limit access to specified applications on the remote Windows or Linux system by either allowing or denying a list of executables. You may also choose to allow or deny desktop access.
What is advanced web access?
Advanced Web Access enables administrators to appropriately manage privileged access controls over assets that utilize modern web technology in a secure, scalable, and controlled manner. The auditing capability gives your organization the visibility it needs to adhere to both internal security policies and any applicable industry compliance requirements.
How to protect against common user mistakes during SSH sessions?
Protect against common user mistakes during SSH sessions by applying basic filtering to the input at the command line. For devices or B Series Appliance s where agents are not practical or possible, command filtering provides an extra layer of control for administrators who need to provide access to that endpoint.
What is let's encrypt?
Let's Encrypt is a service provided by the Internet Security Research Group (ISRG). It is a free, automated, and open certificate authority (CA). In /appliance, you can request and automatically renew SSL/TLS certificates used by your B Series Appliance. Let's Encrypt is configured in the SSL/TLS Configuration section in /appliance for on-premises deployments and the Appliance tab for Cloud deployments.
What tools do you use to draw on a remote screen?
While screen sharing, use annotation tools to draw on the remote screen. Drawing tools, including a free-form pen and scalable shapes, can aid in collaborating with other users.
Can you cancel pending jump access?
Users can cancel pending Jump Access authorization requests from the Web Console, providing more flexibility and control over the authorization process, extending the existing functionality of the desktop Access Console.
Can BeyondInsight be used for remote access?
Administrators can leverage the BeyondInsight platform for session details and reports of Privileged Remote Access sessions . This integration includes a Dashboard view for Privileged Remote Access sessions, which users can access in the BeyondInsight interface. Administrators who utilize the existing reporting functionality of /login can continue to view session details, reports, and session recordings in the /login interface.
Overview
For this procedure, you must connect to the Privileged Access Workstation (PAW). The customer will need to provide you with the ability to connect to the PAW using Remote Desktop.
Configuring the WinRM
To allow connections to the privileged endpoint from the PAW, ensure that the privileged endpoint IP addresses, as defined in the Azure Stack Hub Admin Portal, are set as a trusted host on the PAW. The instructions for obtaining these IP addresses from the Administrator Portal are in Verifying scale unit node access and health on page 16.
Connect to the privileged endpoint
On the PAW, open an elevated PowerShell session and run the following two commands. Replace *<ERCS_IP* with an IP of one of the privileged endpoint instances as noted earlier in this procedure. When prompted enter the privileged endpoint (PEP) credentials supplied by the customer.
Further reading
For more information on connecting to and working with the privileged endpoint see Use the privileged endpoint in Azure Stack Hub.
Vendor PAM Datasheet
Learn more about CyberArk Vendor PAM, a born in the cloud SaaS solution that helps organizations secure external vendor access to critical internal systems.
Third Party Privileged Access to Critical Systems
This eBook summarizes the findings of the survey about third party access and the solutions used to reduce the risk.
Vendor Privileged Access Manager Demo Video
CyberArk Vendor PAM gives the ability to invite, provision and give vendors privileged access. In this video, we'll show how to invite and give a vendor specific privileged access to a target system.

Overview
- For this procedure, you must connect to the Privileged AccessWorkstation (PAW). The customer will need to provide you with theability to connect to the PAW using Remote Desktop.
Configuring The WinRM
- To allow connections to the privileged endpoint from the PAW, ensurethat the privileged endpoint IP addresses, as defined in the AzureStack Hub Admin Portal, are set as a trusted host on the PAW. Theinstructions for obtaining these IP addresses from the AdministratorPortal are in Verifying scale unit node access andhealth on page 16. To view or edit the WinRM trusted hosts…
Connect to The Privileged Endpoint
- On the PAW, open an elevated PowerShell session and run the followingtwo commands. Replace *<ERCS_IP* with an IP of one of theprivileged endpoint instances as noted earlier in this procedure. Whenprompted enter the privileged endpoint (PEP) credentials supplied bythe customer.
Further Reading
- For more information on connecting to and working with the privilegedendpoint see Use the privileged endpoint in AzureStackHub.