Best Privileged Access Management Software
- CyberArk. Best for: CyberArk is best for businesses with many employees working remotely or in several different...
- Thycotic. Best for: Thycotic is best for organizations with several different user types across the business, including...
- BeyondTrust. Best for: BeyondTrust is best for organizations in highly regulated industries...
How to properly secure remote access?
- Windows or Mac login when connecting remotely
- Request permission to connect to the user’s computer
- Automatically blank the remote screen when connected
- Automatically lock remote computer when disconnected
- Lock the remote computer’s keyboard and mouse while in session
- Lock the streamer settings using Splashtop admin credentials
How do I setup my computer for remote access?
To enable remote connections on Windows 10, use these steps:
- Open Control Panel.
- Click on System and Security.
- Under the “System” section, click the Allow remote access option ...
- Click the Remote tab.
- Under the “Remote Desktop” section, check the Allow remote connections to this computer option.
How secure is enabling remote access?
- iOS/Android: Swap album and artist titles in CarPlay/Android Auto.
- iOS/Android: Rare crash if your library had ~200,000 items.
- Desktop: Reduce hover play background size to allow clicking on poster.
- iOS: Crash for high CPU in some cases if server disks were offline.
- CarPlay/Android Auto: Show all albums when album types are enabled.
How BeyondTrust privileged remote access works?
BeyondTrust Privileged Remote Access gets you closer to a true zero trust strategy by applying the granularity of privileged access management (PAM), which includes secure remote access. Zero trust can ensure all access is appropriate, managed, and documented—regardless of how the perimeter has been redefined.
What is privileged remote access?
What is advanced web access?
About this website

What is a remote access solution?
The most common remote access solutions are software programs with built-in access and communication capabilities for tech admins and remote users. These tools allow admins to access employee workstations remotely and allow users to reach in-office resources from remote devices.
What are the different types of remote access methods?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
What is BeyondTrust remote client?
The BeyondTrust Customer Client enables customers to interact with representatives during remote support, chat or presentation sessions. Because it is the most secure remote support solution, BeyondTrust places a top priority on user controls.
What is BeyondTrust PRA?
The BeyondTrust Privileged Remote Access (PRA) Integration Client is used to transfer session logs and recordings from the BeyondTrust Appliance B Series to an external system. Two external systems are currently supported: Microsoft SQL Server and Windows-based file systems.
What are two types of remote access servers?
Remote Access Methods1- Remote Access Server: It's one server in organization network that it is the destination of all remote access connections.2- Remote Access Client: All computers that remote connect to network, called remote access client or remote computer.More items...•
Which technology is used in remote access?
virtual private network (VPN) technologyRemote access software is usually accomplished using a virtual private network (VPN) technology. This type of method is more available compared to others since it is a more secure remote access software that connects the user and the enterprise's networks through an internet connection.
What is privileged remote access?
Privileged remote access is about ensuring employees, third-party vendors, and other insiders don't have free access to systems while accessing the network remotely. You're able to define who has permissions, when they have it, and the appropriate level of access each role needs to complete their work.
Is BeyondTrust secure?
BeyondTrust has always been designed with security at the forefront. Not only is the product architecture superior from a security standpoint, the product itself includes a number of features that strengthen the security of your organization on a day to day basis.
What is Bomgar remote access?
BeyondTrust Remote Support (formerly Bomgar) enables you to remotely access and fix nearly any device, running any platform, located anywhere in the world.
What is BeyondTrust privilege management for Windows?
BeyondTrust Privilege Management for Windows Servers reduces the risk of privilege misuse by assigning admin privileges to only authorized tasks that require them, controlling application and script usage, and logging and monitoring on privileged activities.
How do I use BeyondTrust?
Simply copy the URL and paste it in an email to your customer. Clicking the link will initiate a download of the BeyondTrust Custom Client. Once the user has followed the prompts to run the BeyondTrust Custom Client, his session should appear in your Personal queue on the Sessions tab.
How do I use my Beyond Trust remote?
2:3115:29How BeyondTrust Privileged Remote Access Works - YouTubeYouTubeStart of suggested clipEnd of suggested clipOne common method of remote access is the use of jump clients a jump client is an agent you deployMoreOne common method of remote access is the use of jump clients a jump client is an agent you deploy to the application layer of an endpoint.
How does BeyondTrust remote support work?
BeyondTrust connects support reps with remote desktops, servers, laptops and network devices wherever they are. Support reps can see the screen, control the mouse and work as if physically in front of the remote desktop, speeding time to resolution.
How do I remove BeyondTrust remote support Jump client?
A BeyondTrust user cannot remove a Jump Client unless the user is given appropriate permissions by their admin from the /login interface. The options Attempt an Elevated Install if the Client Supports It and Prompt for Elevation Credentials If Needed do not apply to headless Jump Clients.
Is remote support safe?
Remote access solutions could leave you vulnerable. If you don't have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data. Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular.
Is bomgar safe?
BeyondTrust (Bomgar) is a safe secure and private way to allow the support personnel to view and control your computer. Your technician will not be able to view any information you do not want them to see and you will be able to see what they are doing at all times.
Download the Desktop App from the Privileged Web Access Console
Download the Native Desktop from the Privileged Web Access Console. While working in the privileged web access console, you can choose at any time to download the native desktop access console to your computer.. To download the native desktop access console from the privileged web access console, select Desktop Access Console located under the Active menu in the top right corner of the screen.
Bomgar (free version) download for PC
Bomgar enables support technicians to control remote computers over the internet or network. With Bomgar you can support remote desktops, backend servers, network devices, smartphones and systems outside the network – all from one screen! And Bomgar works on Windows, Mac, Windows Mobile, BlackBerry and multiple Linux distros.
Bomgar – How to Start a Remote Session and elevate privileges with ...
Login to Bomgar Representative Console and select the Session Key radio button.This will generate a one-time key for the client to input on their end. From the Session Key window, you will be able to set an expiration time on the key, if the client is not currently at their computer.
BeyondTrust Pricing - Crozdesk
BeyondTrust offers premium only subscription plans. View all plans and pricing for BeyondTrust in 2022.
Secure Remote Access for Employees and Vendors
Traditional remote access methods, such as RDP, Virtual Private Networks, and legacy remote desktop tools lack granular access management controls. These processes enable easy exploits via stolen credentials and session hijacking. Extending remote access to your vendors makes matters even worse.
Privileged Remote Access: Use Cases
BeyondTrust Privileged Remote Access controls, manages, and audits remote privileged access to critical IT systems by authorized employees and third-party vendors. No VPN required.
Remote Support: Use Cases
BeyondTrust Remote Support allows help desk teams to securely access and fix any remote device on any platform, located anywhere in the world. All with the same solution.
Secure Remote Access and Remote Support Features
BeyondTrust Remote Support and Privileged Remote Access solutions work hand-in-hand to secure remote access points within the enterprise, including employees, vendors, third-parties, and more.
What is privileged access management?
Privileged access management, or PAM, is a security measure that allows organizations to control and monitor the activity of privileged users, including their access to key business systems and what they’re able to do once logged in. Most organizations order their systems in tiers according to the severity of the consequences should ...
What is a privilege account?
Privileged accounts, such as domain admin and networking equipment accounts, provide administrative levels of access to high-tier systems, based on higher levels of permissions.
What is advanced session monitoring?
Advanced session monitoring allows admins complete insight as to who is using the privileged access environment and why, which enables faster risk mitigation. ARCON | PAM also provides a complete audit trail of privileged activities, as well as reports and analytics of the results, via the solution’s reporting engine. This allows managers and auditors to assess the organization’s compliance status as needed.
What is an ARCON password vault?
ARCON | PAM features a secure password vault that automates frequent password changes. The vault generates and stores strong, dynamic passwords, which can only be accessed by authorized users. Users must go through multi-factor authentication (MFA) in order to access the vault. ARCON offers native software-based one-time-password (OTP) validation to verify users’ identities, and this tool integrates with third-party authentication solutions should an organization want to build layers of authentication around the vault. The security of MFA allows ARCON | PAM to run single sign-on (SSO) access to all critical systems without users having to share their credentials. This makes the sign-on process more efficient, whilst protecting critical data from the threat of password breaches. Finally, all privileged access is just-in-time, which reduces the threat surface by favouring access as needed over standing privileges.
How does Secret Server work?
Secret Server stores all privileged credentials in an encrypted, centralized vault that users can only access via a two-factor authentication process. Once verified, users can only view the passwords they need to be able to do their job. From a centralized management portal, admins can provision and deprovision privileges for just-in-time access, as well as configure policies for password complexity and credential rotation. This eliminates weak and static passwords, reducing the risk of password theft. Admins can also set up a custom workflow to delegate access requests, including for third parties. Powerful session recording capabilities enable organizations to monitor privileged activities, both to ensure compliance and to detect the source of any fraudulent or suspicious activity.
What is JumpCloud user management?
JumpCloud User Management with Cloud Directory Services securely connects privileged users to critical systems, applications, files and networks. It integrates seamlessly with Google Workload, MS O365 and on-premises Active Directories. JumpCloud User Management leverages cloud-based directory services, which reduces strain on system resources whilst providing the scalability of the cloud.
How does one identity safeguard work?
With One Identity’s Safeguard solution, users can access their privileged and non-privileged resources from a single account, which removes the risk of error in provisioning access. This also reduces the strain on help desk workloads, automating the process of granting privileged credentials according to the user’s role. Privileged accounts are stored in a secure vault for enhanced security, with centralized authentication and SSO for added protection and increased efficiency. Safeguard uses machine learning to analyze user activity both at the time of access and throughout the session. It also records keystrokes, mouse movement and windows viewed in order to detect unauthorized use of critical business systems and increase accountability. Admins can review these recordings remotely and search them like a database for specific events across sessions. They can also be used for governance and compliance purposes.
What is Privileged Access Management?
Privileged access management (PAM) is a type of software that reviews access levels for all of a business’s data and software to limit the number of employees with high-level permissions. It does this through least privileged access — users only have permission for information they absolutely need to do their job. Users can include both people and applications that may need to access data in order to function properly.
What is PAM security?
Sometimes, PAM is also called privileged identity management (PIM) or privileged access security (PAS). By keeping valuable information under tight control, organizations can minimize the impact of any data breaches that do occur.
What is a PAM password?
Instead of giving users credentials to sensitive data, privileged access management software automatically generates a new password for authorized users. This prevents manual overrides of the system, while still providing easy access for the people and applications that need it. PAM software also protects the actual credentials in a secure environment to keep attackers from finding them.
What is a PAM system?
PAM software enables a company’s IT team to monitor users’ sessions with valuable information, allowing them to verify access levels and remotely end sessions if necessary. The system should also record all privileged sessions and make them searchable, so IT administrators can review them later.
Does Thycotic have a password manager?
It’s very customizable, and businesses can use their own developers or work with Thycotic’s team. Thycotic automatically handles password changes for network accounts to keep them secure and includes a secure vault and password manager. There are also options for approval workflows and disaster recovery.
License requirements
The concepts covered in this guide assume you have Microsoft 365 Enterprise E5 or an equivalent SKU. Some of the recommendations in this guide can be implemented with lower SKUs. For more information, see Microsoft 365 Enterprise licensing.
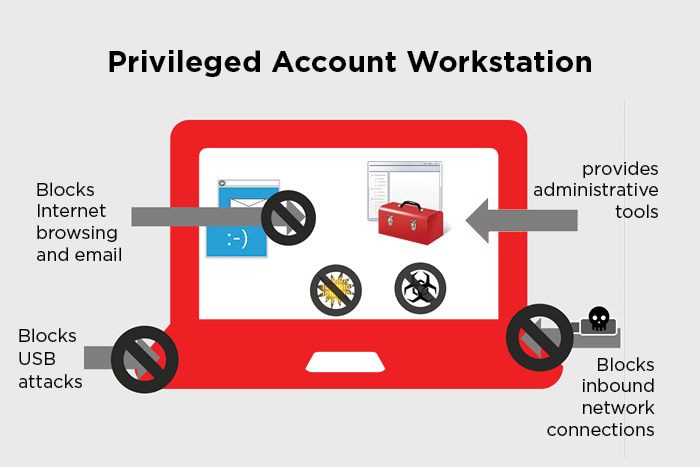
Azure Active Directory configuration
Azure Active Directory (Azure AD) manages users, groups, and devices for your administrator workstations. Enable identity services and features with an administrator account.
Microsoft Intune configuration
In our sample, we recommend that BYOD devices not be permitted. Using Intune BYOD enrollment allows users to enroll devices that are less, or not trusted.
Set rules in the Endpoint Protection Configuration Profile for Microsoft Defender Firewall
Windows Defender Firewall policy settings are included in the Endpoint Protection Configuration Profile. The behavior of the policy applied in described in the table below.
Enable Microsoft Cloud Application Security, URLs restricted list to approved URLs (Allow most)
In our roles deployment it is recommended that for Enterprise, and Specialized deployments, where a strict deny all web browsing is not desirable, that using the capabilities of a cloud access security broker (CASB) such as Microsoft Defender for Cloud Apps be utilized to block access to risky, and questionable web sites.
Manage local applications
The secure workstation moves to a truly hardened state when local applications are removed, including productivity applications. Here, you add Visual Studio Code to allow connection to Azure DevOps for GitHub to manage code repositories.
Validate and test your deployment with your first device
This enrollment assumes that you will use a physical computing device. It is recommended that as part of the procurement process that the OEM, Reseller, distributor, or partner register devices in Windows Autopilot.
What directories can you leverage?
With our solutions, you can leverage your existing directories (LDAPS, Kerberos, Smart Card, RADIUS) so that changes to a user’s account in Active Directory are automatically reflected.
What are some security investments that can be leveraged?
And you can leverage existing security investments such as password solutions, information and event management (SIEM) tools, and Change Management solutions to increase productivity.
What is session logging?
Session logging allows for the review of all end system and network interactions. This log includes users involved, which endpoints they connected to, and system information. In addition to log reports, BeyondTrust also records videos of each session. These video recordings capture every action taken in each remote desktop, SSH, or Telnet session.
What is a group policy?
Policies can be set for vendors, users, groups, or sessions, giving administrators significant flexibility and control. Group policies integrate easily with external directory stores to assign permissions based on your existing structures.
Can privileged users connect to mobile devices?
Since we allow privileged users to connect from mobile devices, you can create a list of authenticated devices and determine the network locations from which they can connect.
Common Remote Access Technologies Run Counter to Zero Trust
The urgency to “go remote” in response to the COVID-19 pandemic compelled organizations to lean into VPNs and remote access technologies, like remote desktop protocol (RDP), more heavily than ever. This seismic workplace shift magnified the considerable, pre-existing security faults inherent to many remote access technologies.
How to Align Remote Access with Zero Trust
A zero trust architecture (ZTA) treats all access requests as potentially malicious—a stark departure from the all-or-nothing access allowed by VPNs.
What is privileged remote access?
Privileged Remote Access gives you the ability to centrally secure and manage access across all of your environments, even sensitive systems in the Cloud.
What is advanced web access?
Advanced Web Access can be configured to work across any solution that leverages a web interface for management including; Amazon Web Services, Google Cloud, VMware vSphere, Citrix XenServer, Microsoft Hyper-V, Microsoft Azure, IBM Softlayer, and Rackspace.
