Pros. Remote access VPN reduces deployment costs, complexity, and need for extra administration. Protects from unwanted cyber attacks. Cons. Remote access VPN, if not properly configured, can cause security problems.
Full Answer
What are the advantages and disadvantages of VPN?
Another major advantage of using a VPN is that it grants the ability to unblock various websites and streaming services. Good VPNs manage to circumvent any web filter reliably every time the user needs to access content that is not available in their region.
What are the different modes of remote access VPN deployment?
When you want to deploy a remote access VPN, there are two major modes to that end, which are the Secure Sockets Layer (SSL) and IP Security ( IPsec ). Each of these modes has its own pros and cons depending on the access requirements of the users or the organization.
Do I need a VPN if I am a telecommuter?
Being able to connect securely to your corporate network from a remote location using a Virtual Private Network (VPN) is important, and it may be required by your job if you are a telecommuter. There are some remote access technologies that are widely used, but some new methods have recently emerged that have the ability to change how we work.
What are the advantages of a virtual private network?
With a Virtual Private Network, people in two remote locations, can connect to each other, and communicate over the network, as if they were sitting in the same building, communicating over a Local Area Network. 2. Bypass Geo-restrictions on Websites and Content

What are the advantages and disadvantages of remote access?
Advantages of Remote Access1) Flexible Access. ... 2) Flexible Set-Up and Costs. ... 3) Full Control on Authorization and Access. ... 4) Centralized Storage and Backups. ... 5) Shared Resources; Greater Efficiency and Collaboration. ... 1) Security Issues. ... 2) Version Problems and Data Liabilities. ... 3) Hardware Issues Still Need On-Site Work.More items...•
What are the advantages and disadvantages of a VPN?
VPN Pros & Cons SummaryVPN Advantages. VPNs allow users to hide their network information and safely browse the web no matter their location. ... VPN Disadvantages. Specific activities that require high bandwidth, such as gaming, might not be able to function using a VPN, but they are easily enabled and disabled.
What are some of the advantages of using VPNs for remote access?
VPN BenefitsRemote Access to Information Anytime. Regardless of location, VPNs can be used by employees anytime and anywhere, as long as there's internet and an approved device being used.Data Security. ... Access to Blocked Websites. ... Affordable for Business. ... Boost Productivity. ... Better Work Life Balance.
What are the advantages and disadvantages of using remote desktop instead of a VPN?
Unlike VPN, RDP typically enables users to access applications and files on any device, at any time, over any type of connection. The biggest advantage of RDP is that you have access to network resources, databases, and line-of-business software applications without the limitations and high bandwidth demands of VPN.
Is there any disadvantages of using VPN?
The 10 biggest VPN disadvantages are: A safe, top-quality VPN will cost you money: Read more. VPNs almost always slow your connection speed: Read more. Using a VPN on mobile increases data usage: Read more. Some online services try to ban VPN users: Read more.
What are the risks of using a VPN?
VPNs are insecure because they expose entire networks to threats like malware, DDoS attacks, and spoofing attacks. Once an attacker has breached the network through a compromised device, the entire network can be brought down.
What is the difference between remote access and a VPN?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
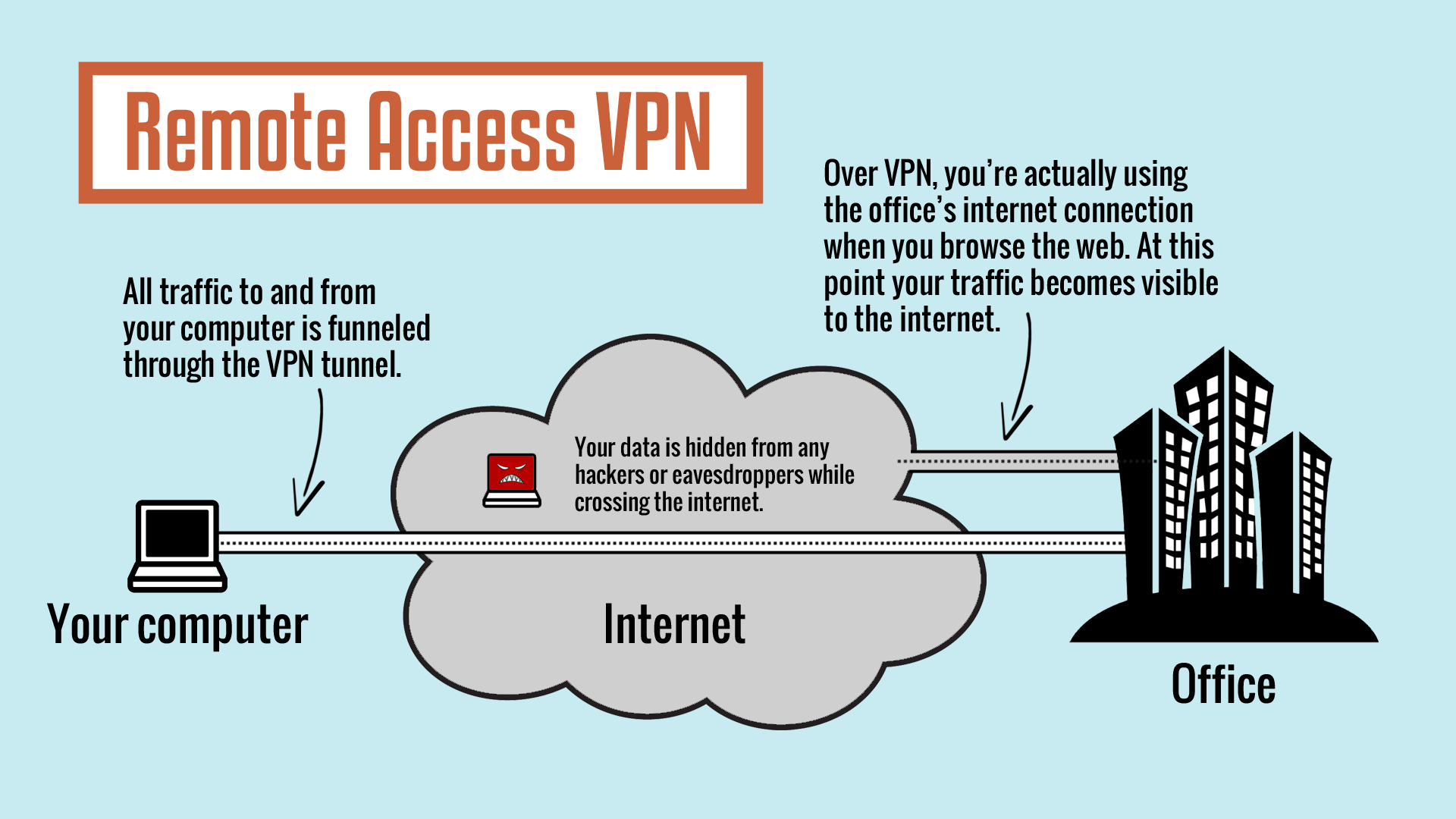
What is remote access VPN?
A remote access Virtual Private Network (VPN) allows users working remotely to access and use applications and data residing in the corporate data center,headquarter offices, and cloud locations, often encrypting all user traffic.
What are the main benefits of using a VPN?
Pros of VPN: What are the advantages of using a VPN?Secure Your Network. The benefits of using a VPN are vast. ... Hide Your Private Information. ... Prevent Data Throttling. ... Avoid Bandwidth Throttling. ... Get Access to Geo-blocked Services. ... Network Scalability.
Which is more secure VPN or remote desktop?
Security. Although both VPN and RDP are encrypted through internet connection, a VPN connection is less accessible to threats than a remote desktop connection. For this reason, VPN is often considered more secure than RDP.
What are the disadvantages of using remote desktop?
Reliable Network Required: For a client computer to connect successfully to a host computer, you need a working and reliable network connection. Otherwise, the entire remote desktop service may break down.
Should I use a VPN for remote desktop?
In order to fully secure a remote desktop, a VPN is the best option. With a VPN like Access Server, you have secure access to the network, and then the VPN server has least a privilege access policy setup that would limit an employee to using a remote desktop to connect only to his or her computer's IP address.
What are the main two advantages of using VPN?
A VPN can prevent web browsers and others from accessing your connection, helping to keep information you send and receive anonymous and secure. Some VPNs also offer military-grade 256-bit encryption of your data.
What are the main benefits of using a VPN?
Pros of VPN: What are the advantages of using a VPN?Secure Your Network. The benefits of using a VPN are vast. ... Hide Your Private Information. ... Prevent Data Throttling. ... Avoid Bandwidth Throttling. ... Get Access to Geo-blocked Services. ... Network Scalability.
Should I keep my VPN on all the time?
The answer to “should I leave a VPN on?” is yes. VPNs offer the best online security, so you should leave your VPN on at all times to protect yourself against data leaks and cyberattacks, while you're using public W-Fi, and against intrusive snoopers such as ISPs or advertisers. So always keep your VPN on.
What does a VPN on my phone do?
What is a VPN? A virtual private network (VPN) conceals internet data traveling to and from your device. VPN software lives on your devices — whether that's a computer, tablet, or smartphone. It sends your data in a scrambled format (this is known as encryption) that's unreadable to anyone who may want to intercept it.
Why do companies use VPNs?
For all these reasons, VPNs have become a popular option for companies who need to give their employees remote access, but want to provide online security and privacy.
Why is VPN important?
To fully achieve its goals, a VPN must accomplish two important tasks: Protect that connection, so that your files (and your company’s network) won’t be compromised. VPNs achieve this second step by encrypting data, these encryption and masking features help protect your online activities and keep them anonymous.
What is VPN for employees?
1. VPNs: Virtual Private Networks . When employees need to remotely access their company files, a virtual private network (VPN) is often the tool of choice. VPNs are designed to give employees the online privacy and anonymity they (and their company) require, by turning a public internet connection into a private network.
What are the two types of users that need privileged accounts?
Many organizations need to provide privileged accounts to two types of users: internal users (employees) and external users (technology vendors and contractors). However, organizations that use vendors or contractors must protect themselves against potential threats from these sources.
Can hackers use VPNs?
Hackers have also exploited VPNs in prolonged multi-stage cyberattacks. As detailed in a 2018 US government alert, Russian cyber activity targeted “trusted third-party suppliers with less secure networks”, “leveraging remote access services … such as VPN, RDP, and Outlook Web Access (OWA)” to exploit the insecure infrastructure of those third-party suppliers and gain access to other, final targets. VPNs are specifically mentioned by name in the alert as a major initial access point for hackers.
Can VPNs be exploited?
VPNs are exploited in major data breaches. A note of caution for those thinking of using VPNs: their reputation has suffered a major blow due to their implication in a number of serious data breaches. National news stories have reported on how hackers exploited VPNs to cause data breaches at several major companies .
Is desktop sharing good for enterprise?
Second, desktop sharing tools are not the best solution for supporting enterprise environments. While these tools can be utilized to provide desktop support and handle helpdesk tasks, they typically don’t have the security and functionality required for complex enterprise remote support such as server or application maintenance. They often lack the strict security controls ( logging and audit) that enterprises in highly-regulated industries need. Also, while desktop sharing can be useful for end-user support, there are additional tools and protocols needed when supporting servers, databases, and other enterprise applications.
What Is a VPN?
VPN or Virtual Private Network is a networking technology that allows you to browse securely over the Internet. It does so by creating an encrypted data tunnel and hides your public IP address from the public.
What is ClearVPN?
Advanced technology can be easy and fun. ClearVPN is the first personalized VPN solution that focuses on user experience and user's actual needs. It's hassle-free, intuitive, and beautifully designed.
How to bypass ISP throttling?
Bypass ISP throttling - It gets frustrating when your ISP decides to limit your bandwidth when you’re gaming, streaming, or torrenting. This can be easily overcome by using a VPN with obfuscated servers. Not only does it hide your online activities from ISPs, but it also prevents them from knowing that you’re using a VPN.
Is VPN secure?
Security matters when evaluating the pros and cons of using a VPN. Ideally, you’ll want a VPN built with highly secure VPN security features such as the AES -256. It is used by the military and banks. Any attempts to crack an AES-256 encrypted communication will be futile as it takes billions of years to do that.
Is premium VPN good?
Now that we’ve evaluated the VPN pros and cons, it’s evident that using a premium VPN is the right choice if you want to stay protected online.
Does VPN slow down internet connection?
May slow down the internet connection - VPNs are like an intermediate relay between your device and the internet. If you’ve chosen a mediocre VPN that’s not optimized for speed, it could hurt your browsing experience.
Is VPN safe for hacking?
Ensure a safe and secure browsing environment. You’re guaranteed a secure data transmission channel when using a VPN. Any hacking attempts are thwarted by secure encryptions and protocol. Furthermore, you’ll be on stealth mode when going online as your device’s IP address will be masked by a VPN server’s IP.
How to choose a VPN?
Here are a few things to keep in mind when choosing a VPN provider: 1 Server infrastructure. Make sure it has extensive server infrastructure, as it will give you a lot of IP addresses to choose from; 2 Strong encryption algorithms. This is one of the essential components of a VPN. 256-bit AES encryption is the strongest on the market, so always check if the VPN service offers it; 3 Customer service. A good VPN provider should have a reliable and professional customer support in case you encounter any problems (to find out how satisfied our customers are with their service, check out these NordVPN reviews ); 4 No-logs policy. Make sure the provider has an audited no-logs policy, which means that they do not store any data about you; 5 Country of operation. Check whether the service is not based in a country notorious for surveillance and privacy violations.
What happens if your internet is not encrypted?
If it's not encrypted, third parties, like your internet service provider, government officials, or cybercriminals, can access it and use it against you. The risk is especially high when you use unsecured public Wi-Fi networks, which are fertile grounds for hackers.
How long is NordVPN money back guarantee?
Powerful encryption, a global infrastructure, and a 30-day money-back guarantee, makes NordVPN a go-to security app for millions around the world.
Why are some websites unavailable?
Some websites or online services may be unavailable in specific locations for ethical, commercial, or political reasons. Internet service providers impose these restrictions by inspecting users' IP addresses, which show users' locations. Providers can then deny content or services to specific locales.
Does VPN protect you?
VPN can help you with that. It encrypts your traffic so no one can see what you do or access online. Premium VPN providers use top-notch encryption algorithms, which are practically indecipherable and guarantee 100% protection, making you almost invisible online.
Can ISPs snoop on my data?
ISPs often snoop on their customers' data and can even pass it to third parties. For example, they can sell it to a governmental institution interested in what you do online or a commercial entity that may use it for marketing purposes or ad targeting. A VPN will mitigate this issue.
Can a VPN see your IP address?
However, if you use a VPN, you'll be routing your data through a VPN server with its own IP address. Websites you interact with will only be able to view the VPN's IP address, and not your own.
What happens if your VPN isn't configured properly?
If your VPN isn’t configured properly, you could experience IP and DNS leaks which make your private data vulnerable to hackers and other online threats. If you’ve been reading about VPN features and you’re feeling overwhelmed, have no fear.
What is a good VPN?
A good VPN – short for Virtual Private Network – comes with plenty of benefits. It will let you access geoblocked websites and content from all around the world, including your favorite streaming services, such as Netflix, Hulu, and BBC. You can use it to change your IP address and appear as though you’re in a different country, and get better prices on flights, hotel rooms and more.
What is the best VPN for protecting your privacy?
VPNs can help you hide this information from websites so that you are protected at all times. We recommend ExpressVPN — the #1 VPN out of over 350 providers we've tested. It has military-grade encryption and privacy features that will ensure your digital security, plus — it's currently offering 49% off.
How does a VPN work?
A VPN encrypts your data and keeps your private activity really private, whether you’re browsing the web at home, at the office or through public wi-fi. You always remain anonymous and nobody – from hackers to government officials – can see what you’re doing online.
What happens when your encrypted connection drops?
It’s that the moment your encrypted connection drops, your real IP address is exposed, and you are no longer anonymous. A kill switch feature, which instantly disconnects you from the internet in case of a server drop, can prevent this from happening.
Is a VPN good for privacy?
A good VPN will also secure your internet connection, protect your privacy and conceal your identity , keeping you safe from hackers or anyone else who might be trying to keep tabs on your online activity . It’s important to remember that not all VPNs are created equal, and each one comes with its own set of pros and cons.
Is ExpressVPN safe?
ExpressVPN not only keeps you safe with military-grade encryption, it also offers lightning-fast speeds.
What is remote access technology?
A common remote access technology in use today is the IPsec VPN. A piece of software called a VPN client is installed on the end user’s computer and is configured with details about the target network, such as the gateway IP address and a pre-shared security key. Each time the user wants to connect to the corporate network, they start the VPN client, which creates a secure connection to the corporate firewall.
How does SSL VPN work?
When setting up an SSL VPN, the network administrator publishes the VPN client to the firewall, providing it for download via the firewall's public connection. To access the corporate network, end users visit a public web page, from which they can install the SSL VPN client and download the configuration details.
What is SSL VPN?
SSL, which stands for Secure Sockets Layer, is a common encryption technology that is widely used to provide secure communication on the Internet. When setting up an SSL VPN, the network administrator publishes the VPN client to the firewall, providing it for download via the firewall's public connection. To access the corporate network, end users visit a public web page, from which they can install the SSL VPN client and download the configuration details.
Does a firewall include VPN?
When a firewall is purchased, it typically includes plenty of licenses for IPsec VPN connections.
Is DirectAccess going to be widespread?
DirectAccess is not going to gain widespread adoption until the OS licensing requirements are revised and the networking is reworked to be more straightforward. While IPv6 is the future of networking, we currently live and work in an IPv4 world, especially on the LAN (as of May 2014, IPv4 still carried more than 96% of Internet traffic worldwide, according to Google ). Setting up a new remote access technology should not require one or more potentially expensive projects before it can be deployed.
Is VPN required for telecommuting?
Being able to connect securely to your corporate network from a remote location using a Virtual Private Network (VPN) is important, and it may be required by your job if you are a telecommuter. There are some remote access technologies that are widely used, but some new methods have recently emerged that have the ability to change how we work.
Is SSL VPN better than IPsec?
Many organizations will find that SSL VPN provides advantages over IPsec VPN. Firewall manufacturers could speed up the adoption of SSL VPN by bundling more licenses with the firewall instead of selling them as add-ons.
Check Point Remote Access VPN Pros
It allows everyone to work from home. If no one could work from home, then we wouldn't have a company, especially now during COVID-19. It's mission-critical, especially since it's currently being used. If there is a problem with it, we would really be screwed.
Check Point Remote Access VPN Cons
When you want to deploy a new Check Point agent, it is really a pain in the butt. For example, Windows 10 now has updates almost every couple of months. It changes the versioning and things under the hood. These are things that I don't understand, because I'm not a Windows person.
Why use a VPN?
Since VPNs basically route all your network traffic through a “tunnel”, and makes it appear as if you’re accessing the Internet from another location, you can easily use a VPN to get around most geo-restrictions placed on websites and content .
Why is VPN weak?
A Virtual Private Network’s strongest point, is also usually it’s weakest: a VPN encrypts all of your network traffic, to ensure anonymity, and security. However, stronger encryption naturally takes more time, and resources.
Why is it important to choose a VPN provider?
This is important for a variety of reasons: If a VPN provider has a larger number of servers, the chances of servers being nearby are higher, which will directly result in faster speeds.
What is VPN network?
By definition, Virtual Private Networks act such that any users connected to the VPN will be able to access the entire network as if they were on a local network. This provides enterprises with a huge advantage, as remote clients can connect to the private network, and access relevant data, and even share files with each other as if they were sitting in the same building. This makes it incredibly easy for large multinational companies manage multiple remote locations, and provide easy access to important data to remote employees.
What is VPN security?
These may be SSL/TLS, PPTP, IPSec, and others. These are the protocols that the VPN service will use to encrypt, and protect your network traffic.
Why use VPN for enterprise?
If we talk about Virtual Private Networks being used by enterprises, the main use case is to allow remote employees, and users to be able to connect to the company’s network, as if they were physically present there . This allows for ease of use, but also brings with it many security concerns. Since the devices being used to access the VPN aren’t all present at the company’s buildings, the network admins have little to no control over the devices that remote users are using to connect. They have to trust the users to use secure methods to access the network. This means that the security of the company’s network depends on a number of remote users, and can’t be completely controlled by the network admins themselves, which is quite a big issue when it comes to enterprise security.
Why do people use VPNs?
VPNs are used by enterprises to create secure private networks, allow remote employees access to company data hosted on private servers, and a lot more. Individuals, on the other hand, usually use VPNs to remain anonymous while browsing, and secure their data on networks with little (or no) security. So, if you’ve ever wondered about whether you ...
What are the disadvantages of VPN?
The disadvantages of a VPN service have more to do with potential risks, incorrect implementation and bad habits rather than problems with VPNs themselves. Some of the main problems with VPNs, especially for businesses, are scalability, protection against advanced cyberattacks and performance.
What are the advantages of using a VPN?
Another major advantage of using a VPN is that it grants the ability to unblock various websites and streaming services. Good VPNs manage to circumvent any web filter reliably every time the user needs to access content that is not available in their region.
Why are VPNs effective?
VPNs are very effective against bandwidth throttling where users may experience buffering or long load times on specific websites especially during the end of the month . Internet service providers along with network administrators usually throttle bandwidth to keep certain users within their download limits. Hence they limit the amount of data users can transfer in a certain period.
Why is it important to use a VPN?
Since it violates their agreements, streaming services and content providers actively fight against VPNs that attempt to circumvent geo-restrictions. This is why it is important to use a high-quality VPN because they regularly update their anonymity tools and servers to unblock content.
How does VPN help?
VPNs can help users save money on various products that are sold online. If the user deploys VPNs to purchase the right products, discounts can go up to thousands of dollars. Different companies set different prices in different regions for the same services and products. With the help of a VPN, users can switch their locations to the region with the lowest price and make their purchases.
Why is VPN important?
The two most important reasons for VPN use are privacy and anonymity. VPN services secure public internet connections via encryption. They also hide online activity from bad actors such as hackers and other cybercriminals.
How does a VPN work?
VPNs do this by masking the user’s traffic and passing it through the encrypted tunnel. When the user connects to a VPN server to change their IP address websites, ISPs and government agencies get the impression that the user is from a different country. Additionally, there is no way for the firewall to know if the incoming encrypted traffic should be blocked because its content cannot be seen.