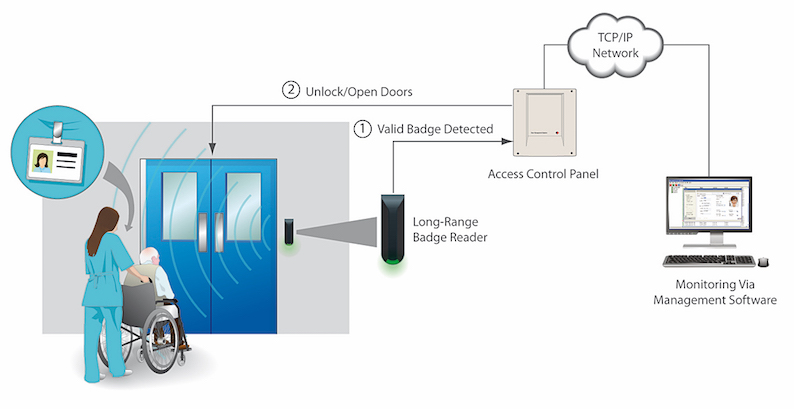
5 Steps to Secure Remote Access
- Assume Hostile Threats Will Occur. Laptops, wireless handheld devices and other portable digital gadgets are prone to loss or theft. ...
- Develop Policy Defining Telework, Remote Access. A telework security policy should define the form of remote access, types of telework devices allowed to use each form of remote access ...
- Configure Remote Access Servers to Enforce Policies. NIST cautions that compromised servers could be used to eavesdrop on remote access communications and manipulate them, as well as to provide ...
- Secure Telework Client Devices Against Common Threats. Teleworkers' PCs, laptops and handhelds should have the same local security controls as client devices for non-telework employees.
- Employ Strong Encryption, User Authentication. Information security managers can mitigate external security threats by encrypting data to protect the confidentiality and integrity of communications and authenticating endpoints to verify ...
- Use strong passwords. ...
- Use Two-factor authentication. ...
- Update your software. ...
- Restrict access using firewalls. ...
- Enable Network Level Authentication. ...
- Limit users who can log in using Remote Desktop. ...
- Set an account lockout policy.
How can I prevent remote access to my computer?
Scan your computer for viruses and malware.
- Malware is typically the easiest way for hackers to infiltrate your personal computer. ...
- If you don't have an antivirus, download an installer on another computer and transfer it to your computer via USB. ...
- A free, easy-to-use third-party anti-malware scanner available for both PCs and Macs is Malwarebytes Anti-Malware. ...
How to disable remote access in Windows 10?
To disable Remote Assistance on Windows 10, use these steps:
- Open Control Panel.
- Click on System and Security. …
- Under the “System” section, click the Allow remote access option. …
- Click the Remote tab.
- Under the “Remote Assistance” section, clear the Allow Remote Assistance connection to this computer option.
How do I turn off remote access in Windows 10?
Part 4: Disable Remote Desktop Service in Windows 10 with System Genius
- Get iSunshare System Genius downloaded and installed properly in your Windows 10 PC.
- Launch it and take the choice of System Service on the left menu column. Then it will display all the Windows services for you.
- Locate to Remote Desktop Service and click the Disable button to turn off this service on your PC.
How to remove remote access to computer?
Uninstall-Remote Access
- Syntax
- Description. The Unistall-RemoteAccess cmdlet uninstalls DirectAccess (DA) and VPN, both Remote Access (RA) VPN and site-to-site VPN.
- Examples. PS C:\>Uninstall-RemoteAccess Confirm If Remote Access is uninstalled, remote clients will not be able to connect to the corporate network via DirectAccess.
- Parameters. ...
- Inputs
- Outputs
Can remote access be monitored?
A: YES, your employer can and has the right to monitor your Citrix, Terminal, and Remote Desktop sessions.
Can remote access be hacked?
Remote desktop hacks become a common way for hackers to access valuable password and system information on networks that rely on RDP to function. Malicious actors are constantly developing more and more creative ways to access private data and secure information that they can use as leverage for ransom payments.
What are the security risks of remote access?
Many remote access security risks abound, but below is a list of the ones that jump out.Lack of information. ... Password sharing. ... Software. ... Personal devices. ... Patching. ... Vulnerable backups. ... Device hygiene. ... Phishing attacks.
Which method of remote access is the most secure?
Implement a Secure Connection for Remote Network AccessWired Connection: A wired connection is the most secure method for remote network access.Home Wi-Fi: The second most secure network connection is using a secured home Wi-Fi connection.More items...•
Can hackers see you through your phone camera?
Are hackers really spying on people through their phone cameras and webcams? The short answer: Yes. Webcams and phone cameras can be hacked, giving bad actors complete control over how they function. As a result, hackers can use a device's camera to both spy on individuals and search for personal information.
What happens if you give someone remote access to your computer?
This can be even worse than just conning you out of money, as undetected malware can allow hackers to steal your identity, including your passwords and financial information, over and over again, even if you get new passwords and account numbers.
Can someone remotely access my computer without my knowledge?
"Can someone access my computer remotely without me knowing?" The answer is "Yes!". This could happen when you are connected to the internet on your device.
What are security considerations for remote users examples?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
What is the insecure way to log in remotely to a system?
Remote access can be vulnerable to brute force and password- guessing attacks, particularly when authentication only requires a username and password. Improperly configured firewalls. In some cases, the POS system has a public IP address that is directly accessible from the Internet.
How do I create a secure remote access?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
Which protocol for remote access is more secure and why?
POINT-TO-POINT TUNNELING PROTOCOL (PPTP) It's used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network. PPTP is a great option because it's simple and secure.
What is a common way to help protect devices connected to the company network?
What is a common way to help protect devices connected to the company network? A. Only use laptops and other mobile devices with full-disk encryption. This is correct!
How do hackers hack remotely?
Remote hackers use various malware deployment methods; the most common (and probably the easiest) way for hackers to reach unsuspecting victims is through phishing campaigns. In this scenario, hackers will send emails with links or files, which unsuspecting recipients may click on.
Can someone access my computer without me knowing?
There are two ways someone can access your computer without your consent. Either a family member or work college is physically logging in to your computer or phone when you are not around, or someone is accessing your computer remotely.
What remote access methods could an attacker exploit?
Common remote access attacks An attacker could breach a system via remote access by: Scanning the Internet for vulnerable IP addresses. Running a password-cracking tool. Simulating a remote access session with cracked username and password information.
Comparing Windows Defender Remote Credential Guard With Other Remote Desktop Connection Options
The following diagram helps you to understand how a standard Remote Desktop session to a server without Windows Defender Remote Credential Guard wo...
Remote Desktop Connections and Helpdesk Support Scenarios
For helpdesk support scenarios in which personnel require administrative access to provide remote assistance to computer users via Remote Desktop s...
Remote Credential Guard Requirements
To use Windows Defender Remote Credential Guard, the Remote Desktop client and remote host must meet the following requirements: The Remote Desktop...
Enable Windows Defender Remote Credential Guard
You must enable Restricted Admin or Windows Defender Remote Credential Guard on the remote host by using the Registry. 1. Open Registry Editor on t...
Using Windows Defender Remote Credential Guard
Beginning with Windows 10 version 1703, you can enable Windows Defender Remote Credential Guard on the client device either by using Group Policy o...
Considerations When Using Windows Defender Remote Credential Guard
1. Windows Defender Remote Credential Guard does not support compound authentication. For example, if you’re trying to access a file server from a...
Why is it important to enforce access based on user identity?
Recommendation: It’s critical that companies enforce access based on user identity, allowing specific groups access to only what they need to get their jobs done, and expanding access from there on an as-needed basis.
What are the risks of using a VPN?
Here are five top security risks that teams must deal with, as well as technology and user education best practices to keep users and data safe: 1. Weak remote access policies. Once attackers get access to a virtual private network (VPN), they can often penetrate the rest of the network like a hot knife through butter.
Why do companies use VPNs?
Historically, many companies deployed VPNs primarily for technical people needing access to critical technology assets. Not so much the case anymore – VPNs are often encouraged for all users as a more secure connection than home or public networks.
Why is remote access important?
Secure remote access is important for three reasons: to safeguard and protect intellectual property; to increase employee productivity, and to enhance an organization’s competitive advantage. Organizations can confidently deliver on their current goals and innovate to achieve new ones when employees can work securely from everywhere.
What is remote desktop access?
Remote desktop access is an older and still popular method for accessing resources, typically on a corporate LAN. In this case, a user will connect to a physical or virtual computing instance located on the LAN. Popular examples include Remote Desktop Protocol (RDP) and Virtual Network Computing (VNC).
Is Google Chrome secure?
Most web browsers, like Google Chrome, provide some level of security for a secure web browsing experience. However, a successful secure remote access strategy provides organizations more control of the web browsing experience, eliminating reliance solely on web browser vendors for a secure web browsing experience.
What version of Windows Defender is used for remote credentials?
To use Windows Defender Remote Credential Guard, the Remote Desktop client and remote host must meet the following requirements: The Remote Desktop client device: Must be running at least Windows 10, version 1703 to be able to supply credentials, which is sent to the remote device.
What version of Windows can a remote computer run?
Version support. The remote computer can run any Windows operating system. Both the client and the remote computer must be running at least Windows 10, version 1607, or Windows Server 2016. The remote computer must be running at least patched Windows 7 or patched Windows Server 2008 R2.
Why does Windows Defender not allow NTLM fallback?
Windows Defender Remote Credential Guard does not allow NTLM fallback because this would expose credentials to risk. The Remote Desktop remote host: Must be running at least Windows 10, version 1607 or Windows Server 2016.
Why is Windows Defender not exposed?
By using Windows Defender Remote Credential Guard to connect during Remote Desktop sessions, if the target device is compromised, your credentials are not exposed because both credential and credential derivatives are never passed over the network to the target device.
Does Windows Defender support compound authentication?
Windows Defender Remote Credential Guard does not support compound authentication. For example, if you’re trying to access a file server from a remote host that requires a device claim, access will be denied.
Can you use Remote Credential Guard on Windows Defender?
For helpdesk support scenarios in which personnel require administrative access to provide remote assistance to computer users via Remote Desktop sessions, Microsoft recommends that Windows Defender Remote Credential Guard should not be used in that context. This is because if an RDP session is initiated to a compromised client that an attacker already controls, the attacker could use that open channel to create sessions on the user's behalf (without compromising credentials) to access any of the user’s resources for a limited time (a few hours) after the session disconnects.
Remote access security risks
Whether the network threats are intentional or not, they're still predictable. Hackers, malware and even users themselves routinely pose certain security hazards. Many remote access security risks abound, but below is a list of the ones that jump out.
How to prevent remote access security risks
The essence of an organization's network security challenge is users are now, more than ever, making security decisions on the network team's behalf. Teams should think about what they can do to minimize such decisions or at least minimize their effect on the business. Consider the following methods.
Find the security gaps
Unless and until technical staff, employees and management are working toward the same goals in terms of security standards, policies and expectations, there will be tangible risks. Most people have already established their baseline in this new normal.
How to allow remote access to a computer?
Open Control panel > click on System and Security. On the System and Security screen, click on Allow Remote Access option located under “System” section. On the next screen, uncheck Allow Remote Assistance connections to this computer option. Click on Apply and OK to save these new changes on your computer. 3.
What is remote attack?
A remote attack can be defined as a malicious act, designed to target vulnerable points in a computer or a network connecting multiple computers. In general, remote attacks are carried out to steal data, take control of the PC, cause damage or infect the computer with malware, adware and viruses. So, let us go ahead and take a look at some ...
How to disable remote desktop on Windows 10?
In case you are using the Professional Edition of Windows 10, make sure that you disable Remote Desktop on your computer while it is not being used. Open Control panel > click on System and Security > Allow Remote Access. On the next screen, select Don’t Allow Remote Assistance connections to this computer option.
How to clean up a computer with malware?
Open Chrome Browser, click on the 3-dots menu > Settings. On the next screen, scroll down to the bottom and click on Advanced. Scroll down further to “Reset and Clean Up” section and click on Clean up computer. Next, click on Find and Chrome will start searching for harmful software installed on your computer.
How to detect harmful programs on my computer?
An easy way to detect the presence of harmful programs on your Windows computer is to periodically scan your PC for malware using Windows Defender or any other third party antivirus program installed on your computer.
Where is the save password button in Chrome?
The option to save Passwords is enabled by default in Chrome browser, but you can easily disable this option in Chrome Advanced Settings screen. Click on the 3-dots Chrome Menu icon located at the top-right corner of your screen and click on Settings in the drop-down menu. Next, scroll down and click on Advanced .
How to secure data in Windows 10?
In case you are using the Professional edition of Windows 10, you can simply right-click on the Folder > Click on Properties > Advanced and check Encrypt Contents to Secure Data option. Windows 10 Home Edition users can make use of various third party tools that are available in the market.
How to secure RDP?
Ananth: There are some built-in, no-cost defenses that can secure RDP. These include: 1 Patching: Keep servers especially up to date. 2 Complex passwords: Also use two-factor authentication, and implement lockout policies. 3 Default port: Change the default port used by RDP from 3389 to something else via the Registry. 4 Windows firewall: Use the built-in Windows firewall to restrict RDP sessions by IP address. 5 Network Level Authentication (NLA): Enable NLA, which is non-default on older versions. 6 Limit RDP access: Limit RDP access to a specific user group. Don't allow any domain admin to access RDP. 7 Tunnel RDP access: Tunnel access via IPSec or Secure Shell (SSH).
What are some built-in, no-cost defenses that can secure RDP?
Ananth: There are some built-in, no-cost defenses that can secure RDP. These include: Patching: Keep servers especially up to date. Complex passwords: Also use two-factor authentication, and implement lockout policies. Default port: Change the default port used by RDP from 3389 to something else via the Registry.
What is the RDP vulnerability?
Most notably, 2019 gave rise to a vulnerability known as BlueKeep that could allow cybercriminals to remotely take over a connected PC that's not properly patched.
How many systems are exposed to the internet via RDP?
Web crawlers like shodan.io make it easy for attackers to quickly identify vulnerable public-facing machines. Worldwide, more than two million systems are exposed to the internet via RDP, of which more than 500,000 are in the US.
Do all RDP instances need a VPN?
Gamblin: Without many exceptions, all RDP instances should require multiple levels of access and authentication controls. This would include the use of a VPN to access an RDP instance and requiring a second factor (like Duo) for authentication.
Can RDP be placed on the internet?
Some major organizations place RDP directly on the internet, but most (hopefully) are doing this unknowingly. Checking on this is pretty simple; just fire up your favorite internet-wide scanner and look at all the RDP instances directly exposed. Ananth: There are some built-in, no-cost defenses that can secure RDP.