What is Quasar? The Quasar tool allows users to remotely control other computers over a network. Software programs of this type are known as remote access tools (RATs).
Full Answer
What is the quasar tool?
The Quasar tool allows users to remotely control other computers over a network. Software programs of this type are known as remote access tools (RATs). There both are legitimate and illegal RATs. Quasar is a legitimate tool, however, cyber criminals often use these tools for malicious purposes.
Is Quasar remote access tool legit?
Remote access tools can be either legitimate or malicious, depending on their usage. Quasar was licensed under the MIT License, which means that it can be used for personal and commercial use, as well as code modification. Employers can use the RAT for day-to-day administrative tasks in a workplace, and even help to spy on employees if so desired.
Does quasar work on Windows 10?
While functions of Quasar are quite typical for a Remote Administration Tool, there is one trait that makes it a more attractive choice for cybercriminals rather than other RATs – it works on Windows 10. Many other tools of this kind do not support the latest version of Windows, limiting the number of machines that can be infected with malware.
How do I run Quasar client?
You can execute the client directly with the specified settings. Start Quasar.exe and use the client builder. See the wiki for usage instructions and other documentation. Quasar is distributed under the MIT License. Third-party licenses are located here. Thank you! I really appreciate all kinds of feedback and contributions.

What is Quasar tool?
Quasar is a fast and light-weight remote administration tool coded in C#. The usage ranges from user support through day-to-day administrative work to employee monitoring. Providing high stability and an easy-to-use user interface, Quasar is the perfect remote administration solution for you.
Is Quasar RAT open-source?
Description. Quasar is a publically available, open-source RAT for Microsoft Windows operating systems (OSs) written in the C# programming language.
What is Quasarrat?
Quasar RAT is a . NET framework open-source remote access trojan family used in cyber-criminal and cyber-espionage campaigns to target Windows operating system devices. It is often delivered via malicious attachments in phishing and spear-phishing emails. Some of its features include: TCP network stream.
What is Quasar malware?
Quasar is a remote access trojan is used by attackers to take remote control of infected machines. It is written using the . NET programming language and is available to a wide public as an open-source project for Microsoft Windows operating systems, making it a popular RAT featured in many attacks.
Who created Quasar RAT?
GitHub user MaxXorQuasar was developed by GitHub user MaxXor to be used for legitimate purposes. However, the RAT has been used by bad actors in cyber-espionage campaigns. Quasar RAT was first released in July 2014 as “xRAT 2.0.” and was later renamed as “Quasar” in August 2015.
What is RAT remote administration tool?
A remote administration tool (RAT) is a software program that gives you the ability to control another device remotely. You then have access to the device's system as if you had physical access to the device itself.
What is async RAT?
AsyncRAT is a Remote Access Tool (RAT) designed to remotely monitor and control other computers through a secure encrypted connection.
What can NanoCore do?
NanoCore can provide the threat actor with information such as computer name and OS of the affected system. It also opens a backdoor that allows the threat actors to access the webcam and microphone, view the desktop, create internet message windows and offers other options.
What is orcus RAT?
Orcus RAT is a remote access trojan discovered by Cisco Talos researchers using both this RAT and Revenge RAT as malware distribution campaigns targeting organizations including government entities, financial services organizations, information technology service providers and consultancies.
Summary
Quasar, a legitimate open-source remote administration tool (RAT), has been observed being used maliciously by Advanced Persistent Threat (APT) actors to facilitate network exploitation.
Description
Quasar is a publically available, open-source RAT for Microsoft Windows operating systems (OSs) written in the C# programming language. Quasar is authored by GitHub user MaxXor and publicly hosted as a GitHub repository.
Solution
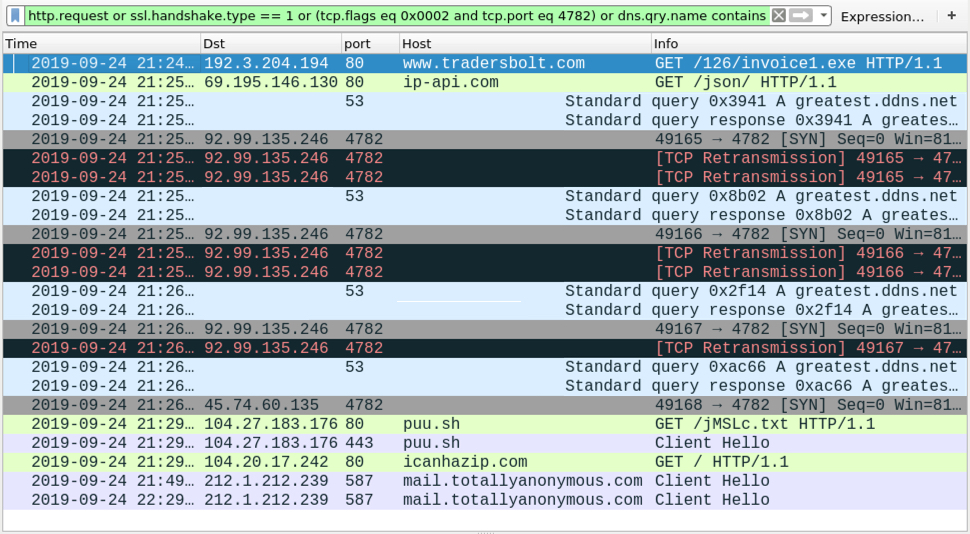
Network defenders can detect Quasar activity by monitoring network traffic for its unique pattern, the registry key it edits for persistence, mutexes for strings that follow the default Quasar pattern, and the directories where Quasar installs itself. Commercial antivirus programs detect most Quasar client binary builds as malicious.
Revisions
This product is provided subject to this Notification and this Privacy & Use policy.
What is a Quasar server?
Quasar uses a client-server architecture that enables one user to remotely access many clients. The server is responsible for creating client binaries and managing client connections. Users then interact with connected clients through the server’s graphical user interface (GUI).
What is a quasar?
Quasar is a publically available, open-source RAT for Microsoft Windows operating systems (OSs) written in the C# programming language. Quasar is authored by GitHub user MaxXor and publicly hosted as a GitHub repository. While the tool can be used for legitimate purposes (e.g., an organization’s helpdesk technician remotely accessing an employee’s laptop), the Cybersecurity and Infrastructure Security Agency (CISA), is aware of APT actors using Quasar for cybercrime and cyber-espionage campaigns.
Can Quasar be hidden?
Quasar users can also specify the name of the executable. Both the client executable and the subdirectory can be hidden from the target host user during installation by a Windows application programming interface call that sets one of the file’s attributes to “hidden.” The “hidden” setting only hides files from the target host user’s view in Windows File Explorer.