How do I enable remote access in Windows 10?
Windows 10 Fall Creator Update (1709) or later
- On the device you want to connect to, select Start and then click the Settings icon on the left.
- Select the System group followed by the Remote Desktop item.
- Use the slider to enable Remote Desktop.
- It is also recommended to keep the PC awake and discoverable to facilitate connections. ...
How do I setup my computer for remote access?
To enable remote connections on Windows 10, use these steps:
- Open Control Panel.
- Click on System and Security.
- Under the “System” section, click the Allow remote access option ...
- Click the Remote tab.
- Under the “Remote Desktop” section, check the Allow remote connections to this computer option.
How to setup remote access for a computer?
- Log in to your RemotePC account with your registered email address and password. Note: If you do not have an existing account, sign up for a RemotePC account.
- On the RemotePC homescreen, click Configure Now!
- Set Computer Name and Personal Key for your computer.
- Click Enable Now!
How to set up secure remote access?
- Windows or Mac login when connecting remotely
- Request permission to connect to the user’s computer
- Automatically blank the remote screen when connected
- Automatically lock remote computer when disconnected
- Lock the remote computer’s keyboard and mouse while in session
- Lock the streamer settings using Splashtop admin credentials

Which is the fastest remote access software?
Top 7 fastest remote desktop software you can use:TeamViewer Remote Desktop.AnyDesk.Chrome Remote Desktop.RealVNC Connect.Splashtop.LogMeIn Remote Access.Remote Utilities.
How do I speed up remote access?
Speed Up Your Remote Connection1) Lower the resolution of both of your computers. ... 2) Change your connection and remote connection experience. ... 3) Change the resources you are connecting to. ... 4) Ensure wherever the remote computer is located has a high Internet upload speed.
How do I get remote access to my computer?
On your Windows, Android, or iOS device: Open the Remote Desktop app (available for free from Microsoft Store, Google Play, and the Mac App Store), and add the name of the PC that you want to connect to (from Step 1). Select the remote PC name that you added, and then wait for the connection to complete.
What is the shortcut to open Remote Desktop Connection?
Press CTRL+ALT+HOME, TAB, TAB, TAB, TAB, TAB, ENTER. This activates the connection bar, and then presses the Restore down button.
Why is remote access so slow?
This is generally caused by a slow network connection on the client computer. Navigate to the Experience tab of the Remote Desktop client and choose a different option under Performance to reduce the bandwidth used by Remote Desktop.
Is VPN faster than Remote Desktop?
Although RDP does require more time and effort to install and configure than VPN, the RDP environment will feel more natural to remote workers while requiring less bandwidth and minimal premises-based hardware. With RDP, remote workers can operate exactly as they would in the office without limitations.
How can I remotely access my computer for free?
10 Best Free Remote Desktop Tools You Should KnowTeamViewer. Available in premium and free versions, TeamViewer is quite an impressive online collaboration tool used for virtual meetings and sharing presentations. ... Splashtop. ... Chrome Remote Desktop. ... Microsoft Remote Desktop. ... TightVNC. ... Mikogo. ... LogMeIn. ... pcAnywhere.More items...
Can someone remotely access my computer when it's off?
Without appropriate security software installed, such as anti-malware tools like Auslogics Anti-Malware, it is possible for hackers to access the computer remotely even if it is turned off.
How can I remotely access another computer using IP address?
Once you've set up the target PC to allow access and have the IP address, you can move to the remote computer. On it, open the Start Menu, start typing “Remote Desktop” and select Remote Desktop Connection when it appears in the search results. Then in the box that appears type the IP address and click Connect.
How do you do Ctrl Alt Del on Remote Desktop?
Press the "CTRL," "ALT" and "END" keys at the same time while you are viewing the Remote Desktop window. This command executes the traditional CTRL+ALT+DEL command on the remote computer instead of on your local computer.
How do I open Remote Desktop in Windows 10?
To launch the saved session, open File Explorer and go to the folder where you store your RDP file. Double click it to establish the connection. Alternatively, you can launch mstsc.exe again and select on the Open button on the General tab. Browse for your RDP file and you are done.
How do I open Remote Desktop on Windows 10?
Windows 10: Allow Access to Use Remote DesktopClick the Start menu from your desktop, and then click Control Panel.Click System and Security once the Control Panel opens.Click Allow remote access, located under the System tab.Click Select Users, located in the Remote Desktop section of the Remote tab.More items...•
How can I improve my RDP performance?
System Performance SettingOpen system Properties (right click 'My Computer' Properties)Navigate "Advanced system settings"->"Advanced Tab"->"Settings Button"->"Visual Effect Tab".Select the radio button name 'Adjust for best performance'.
How can I improve my Google Remote Desktop speed?
Remove and reinstall CRD. Generally speaking, removing and then reinstalling Chrome Remote Desktop could help fix a lot of problems. Therefore, it may also be a Chrome Remote Desktop lag fix.
Why is TeamViewer so laggy?
TeamViewer uses your Internet connection to transmit data from the remote computer. A fast download speed is recommended, or you will experience lag. The remote computer is uploading at the same time. Therefore, your computer can only receive information as fast as the other computer can send it.
Why is my Google Remote Desktop so slow?
Believe it or not, your CPU might be the cause of slow Chrome Remote Desktop connection. Namely, it takes some computing to compress video before it's sent over the network. If your CPU is busy doing something else (like running a simulation of some sort), it will postpone the processing for… quite a while.
What Is Remote Access Software?
Remote access software lets one computer view or control another computer, not merely across a network, but from anywhere in the world. You might use it to log into your customers' computers and show them how to run a program, or sort out their technical troubles. Or you can even use it to invite friends or clients to view your desktop while you run a demo for them. You can use the screen as a temporary whiteboard, drawing lines and circles that help friends or clients understand what you're doing on your machine or theirs.
What is remote PC?
RemotePC is one of the best low-frills remote-access apps, offering identical features on PCs and Macs, fast performance, and a minimal, but intuitive, interface .
What is GoToMyPC?
GoToMyPC is a mature, easy-to-use remote access software with the best available balance between features and ease of use. Unless you need support for Linux or enterprise-level operating systems, this is the app you want.
Is VNC Connect secure?
VNC Connect is solid, secure, and simple to use, once you get the hang of it. It has fewer features than other corporate-level remote access software, but it's also a lot less expensive.
Does GoToMyPC work with TeamViewer?
GoToMyPC and LogMeIn add the ability to drag and drop files between the local desktop and the viewer window that displays the desktop of the remote machine, but this feature works only when connecting to and from Windows computers. TeamViewer has a FileBox window into which you can drag files that will be accessible to both machines. LogMeIn, TeamViewer, and VNC Connect include whiteboard features for drawing lines in the viewer. For more on each remote access apps individual features, see the individual reviews, which are linked to below.
Why is remote access important?
It is essential for these individuals to have safe, anytime, anywhere access to corporate networks and services.
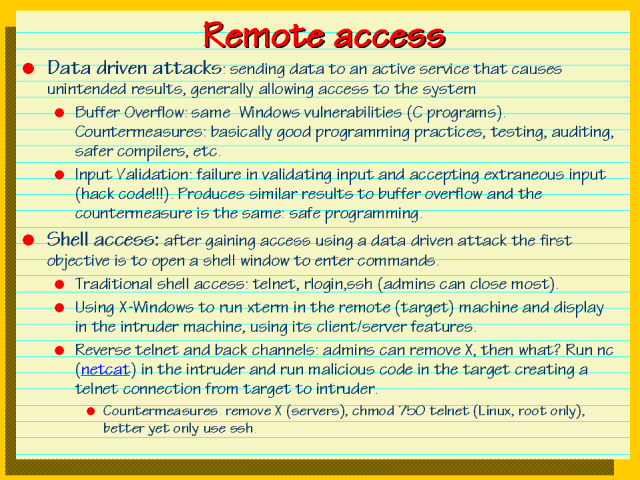
What are the risks of remote access?
Many potential risks accompany vendor remote access —from introducing malware into your systems to technical and business dangers.
What percentage of Verizon network intrusions exploited weak or stolen credentials?
According to Verizon’s Data Breach Investigation Report, “76 percent of network intrusions exploited weak or stolen credentials.” Since vendors don’t need constant access to your network, they often use one remote access tool license and share generic logins and passwords across technicians. This makes the credentials easy for hackers to guess. What’s more, the vendor’s ex-employees often retain remote access to your systems.
What happens if you give access to an outsider?
Recognize that granting system access to an outsider lowers your security level to that of the external provider. If they lack strong security controls, they become your weakest link. If a hacker compromises their system, that partner can become a backdoor into your environment .
Why is reducing network entry points important?
By reducing network entry points to the least amount that are necessary, you increase your ability to monitor and block unwanted activity on your network.
Where should a server be placed?
Because of this, NIST recommends; in most cases, that a server should be placed at an enterprise's network perimeter so it serves as a single point of entry to the network and enforces the remote work security policy before any remote access traffic is permitted into the enterprise's internal networks.
Can compromised servers be used to eavesdrop?
The National Institute of Standards and Technology (NIST) advises that compromised servers could be wielded to eavesdrop on and manipulate remote access communications. They can also provide a starting point for attacking other hosts within your organization.
When is a website created for remote access?
If the network location server website is located on the Remote Access server, a website will be created automatically when you configure Remote Access and it is bound to the server certificate that you provide.
What certificate is needed for remote access?
Remote Access requires an IP-HTTPS certificate to authenticate IP-HTTPS connections to the Remote Access server. There are three certificate options for the IP-HTTPS certificate:
How to join a remote server to a domain?
To join the Remote Access server to a domain. In Server Manager, click Local Server. In the details pane, click the link next to Computer name. In the System Properties dialog box, click the Computer Name tab, and then click Change.
How many Group Policy Objects are required for remote access?
To deploy Remote Access, you require a minimum of two Group Policy Objects. One Group Policy Object contains settings for the Remote Access server, and one contains settings for DirectAccess client computers. When you configure Remote Access, the wizard automatically creates the required Group Policy Objects.
What domain is Remote Access Server?
The Remote Access server and all DirectAccess client computers must be joined to an Active Directory domain . DirectAccess client computers must be a member of one of the following domain types:
How to change the name of my computer?
On the Start screen, type explorer.exe, and then press ENTER. Right-click the Computer icon, and then click Properties. On the System page, click Advanced system settings. In the System Properties dialog box, on the Computer Name tab, click Change.
How to add a new host in DNS?
In the left pane of the DNS Manager console, expand the forward lookup zone for your domain. Right-click the domain, and click New Host (A or AAAA).
What is remote access technology?
A common remote access technology in use today is the IPsec VPN. A piece of software called a VPN client is installed on the end user’s computer and is configured with details about the target network, such as the gateway IP address and a pre-shared security key. Each time the user wants to connect to the corporate network, they start the VPN client, which creates a secure connection to the corporate firewall.
Is VPN required for telecommuting?
Being able to connect securely to your corporate network from a remote location using a Virtual Private Network (VPN) is important, and it may be required by your job if you are a telecommuter. There are some remote access technologies that are widely used, but some new methods have recently emerged that have the ability to change how we work.
Is DirectAccess going to be widespread?
DirectAccess is not going to gain widespread adoption until the OS licensing requirements are revised and the networking is reworked to be more straightforward. While IPv6 is the future of networking, we currently live and work in an IPv4 world, especially on the LAN (as of May 2014, IPv4 still carried more than 96% of Internet traffic worldwide, according to Google ). Setting up a new remote access technology should not require one or more potentially expensive projects before it can be deployed.
What Is Remote Access?
Remote access is any connection made to an organization's internal network and systems from an external source by a device or host. Remote locations can be almost anywhere in the world, from the employee’s home to an off-site office, hotels, transportation hubs, and cafes.
Why is remote access important?
Software organizations where development engineers need to connect across multiple locations, small organizations lacking office-space, and large, enterprise organizations all want to offer the most flexible work options in order to attract high-ranking candidates and reap the rewards of having such a policy.
Why Is a Remote Access Policy Necessary?
The numerous types of mobile devices and the different ways to connect pose challenges for the IT department. Devices can include cell phones, tablets, laptops, and any other device a remote worker relies on to conduct business. They can be company owned and secured, personally owned and authorized by a Bring Your Own Device (BYOD) policy, or a combination. Each class of device has its own set of security challenges. According to the National Institute for Standards and Technology’s Guidelines for Managing the Security of Mobile Devices in the Enterprise, “…Security controls available for laptops today are quite different than those available for smartphones, tablets, and other mobile device types.” Since different devices demand different controls, the policy has to detail what is allowed, compliant, and secure. The policy should answer the following questions:
What Problems Arise Without a Remote Access Policy?
Therefore, consequences for misuse can also be clearly outlined to compel compliance and appropriate precautions for data use and access. Elements such as firewalls, connectivity guidelines, personal use restrictions, and antivirus updates can help IT prevent both malicious and accidental loss and disruption of corporate information assets. The remote access control policies also provide protections for confidentiality, intellectual property, and information compliance.
What is telecommuting?
“Telecommuting,” a term coined in the 1970s, has experienced explosive growth in today’s era of mobile connectivity. Now called distributed offices, remote work, telework, mobile work, smart work, and work shifting, many people are finding flexibility and increased productivity conducting business away from a centralized office environment. Researchers have long studied the benefits of remote work - from the successes that remote work had on traffic reduction during the 1984 Los Angeles Olympics to the 2016 findings by a Gallup survey on the increased hours for remote work.
What percentage of people work remotely?
According to research conducted by Gallup, 43 percent of workers in the U.S. worked remotely at least some of the time in 2016. Remote workers report higher job satisfaction and flexibility, experience fewer distractions and interruptions, and are more productive. Companies experience less absenteeism, less stress on office accommodations, and realize greater employee retention. A recent New York Times article found that finance, insurance, real estate, and transportation were most likely to have and support remote work (retail and education were least likely candidates). The trend is only increasing: the 2016 Gallup poll also found that those who work remotely log more hours away from the office than was reported in their 2012 findings. Not only are people logging more hours, but remote workers are saving money when it comes to commuting costs and businesses are saving on office space expenses.
What is unauthorized access policy?
Even if the employee provides their own equipment, laptop, or mobile device, the policy dictates and enforces the minimum-security requirements necessary. The policy can also provide determinations on who is allowed remote access, the level of access, and penalties for misuse.
How to stop someone from accessing my computer?
This includes removing any Ethernet cables and turning off your Wi-Fi connections.
How to install antivirus on another computer?
If you don't have an antivirus, download an installer on another computer and transfer it to your computer via USB. Install the antivirus and then run a scan with it.
What to do if your computer is compromised?
Change all of your passwords . If your computer was compromised, then there’s a possibility that all of your passwords have been recorded with a keylogger. If you’re sure the infection is gone, change the passwords for all of your various accounts. You should avoid using the same password for multiple services.
What to do if you can't get rid of intrusion?
If you're still experiencing intrusions, or are concerned that you may still be infected, the only way to be sure is to completely wipe your system and reinstall your operating system.
How to get rid of rootkits?
Download and run the Malwarebyte s Anti-Rootkit Beta. You can get this program for free from https://www.malwarebytes.com/antirootkit. This will detect and remove "rootkits," which are malicious programs that exist deep in your system files. The program will scan your computer, which may take a while to complete.
How to find out what is running on my computer?
Open your Task Manager or Activity Monitor. These utilities can help you determine what is currently running on your computer.
Can a computer be remotely accessed?
The chances of your specific computer being remotely accessed, while not impossible, are very low. You can take steps to help prevent intrusions.
What is the most basic method by which to can access someone’s phone without their knowledge?
Password peeking is the most basic method by which to can access someone’s phone without their knowledge. This involves watching when they unlock their phone or asking them to open their phone for some reason while making sure you can view their password.
What is the hacking method?
An unconventional method for the average person is hacking someone’s cell phone to gain access to it. If you do not know how to do this, there are experts for hire online that can accomplish such tasks (which we do not recommend doing). Methods they may use to hack the target user include Wi-Fi networks, phishing, and malware.
Can you crack open a phone?
This process is more complicated and involves needing a clear understanding of how phone operating systems work. Many applications allow direct backdoor access and if you have the right computer software, you can crack open and access all data on the target phone.
