What are the different types of rat programs?
Besides the above examples, there are many other remote access trojan programs like CyberGate, Optix, ProRat, Shark, Turkojan, and VorteX. The full list of RAT tools is too long to be displayed here and it is still growing. How to tell if you have a RAT virus? It is kind of difficult.
What are some examples of remote access trojans?
Remote Access Trojan Examples. 1 1. Back Orifice. Back Orifice (BO) rootkit is one of the best-known examples of a RAT. It was made by a hacker group named the Cult of the Dead Cow ... 2 2. Sakula. 3 3. Sub7. 4 4. PoisonIvy. 5 5. DarkComet.
What is the njRAT rat and what are its weak points?
NjRat’s weak points include, in particular, a relatively high load on the victim’s system and, again, open-source code, which is both advantage and disadvantage. Open code implies antivirus tools can explore and detect the RAT by tracing it back to its source code, which is not the case with closed-source malware.
Is remote access Trojan a malware?
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
What is malware RAT?
RATs are malicious software that constitute a major cybersecurity threat. They usually infect computers, but they can also infect iOS and Android devices, as well as printers, routers, and other networked devices. RATs work by opening access to the device they're installed on to someone who's not supposed to be there.
What is the difference between RAT and backdoor?
The term “RAT” (Remote Access Tool) can be considered a synonym to “backdoor”, but it usually signifies a full bundle including a client application meant for installation on the target system, and a server component that allows administration and control of the individual 'bots' or compromised systems.
How are remote access Trojans delivered?
A remote access Trojan (RAT) is a malware program that includes a back door for administrative control over the target computer. RATs are usually downloaded invisibly with a user-requested program -- such as a game -- or sent as an email attachment.
Can RATs spread through WiFi?
Replies (6) Hi Ajay, RAT or remote access Trojan cannot attack other devices across the same WiFi network and as long as your devices are secured and have proper encryption, we believe that it will not affect your devices.
Can someone RAT an Iphone?
So someone would need direct physical access to your iOS device and a computer to install a RAT exploit into it. Even if you accessed a web site or email with a RAT package hidden in it, it cannot execute or do anything on a normal iOS installation.
Is remote access Trojan a backdoor?
Remote access Trojans are malware programs that use backdoors to control the target machine with administrative privilege. These type of Trojans are downloaded invisibly with a user request for a program such as a game or an email attachment.
Which connection is most commonly used in RATs?
RAT infections are typically carried out via spear phishing and social engineering attacks. Most are hidden inside heavily packed binaries that are dropped in the later stages of the malware's payload execution.
Is RAT a rootkit?
A rootkit is a special variant of a Trojan, a.k.a. a RAT (Remote Administration Tool).
How do I know if someone is accessing my computer remotely?
You can try any of these for confirmation.Way 1: Disconnect Your Computer From the Internet.Way 2. ... Way 3: Check Your Browser History on The Computer.Way 4: Check Recently Modified Files.Way 5: Check Your computer's Login Events.Way 6: Use the Task Manager to Detect Remote Access.Way 7: Check Your Firewall Settings.More items...•
Are remote access Trojans illegal?
Law enforcement officials say that simply possessing a remote-access tool isn't illegal. In fact, remote-access tools are often used for IT support purposes in corporate environments.
Is TeamViewer a RAT?
The JS script then launches the malware, which installs a version of TeamViewer, a remote administration tool (RAT), modified by the attackers. As in earlier attacks, the attackers use a malicious DLL library to hide the graphical user interface in order to control the infected system without the user's knowledge.
What does the RAT do?
Rats are rodents that do actually serve a purpose in the ecosystem. They are scavengers and opportunistic eaters. They will eat garbage and other things that people throw away. Plus, rats are important as part of the predatory ecosystem.
What do you mean by malware?
malicious softwareMalware is intrusive software that is designed to damage and destroy computers and computer systems. Malware is a contraction for “malicious software.” Examples of common malware includes viruses, worms, Trojan viruses, spyware, adware, and ransomware.
What is full form of RAT?
Introduction of Rapid Antigen Tests (RAT) in Telangana to detect coronavirus has left many questions in the minds of people, the most common being, what happens if someone with COVID-19 symptoms tests negative? Earlier, only reverse transcription-polymerase chain reaction (RT-PCR) tests were used to detect the virus.
What is RAT medical term?
Abbreviation for: radiation therapy. recombinant human antithrombin. Remuneration And Terms (of service committee)
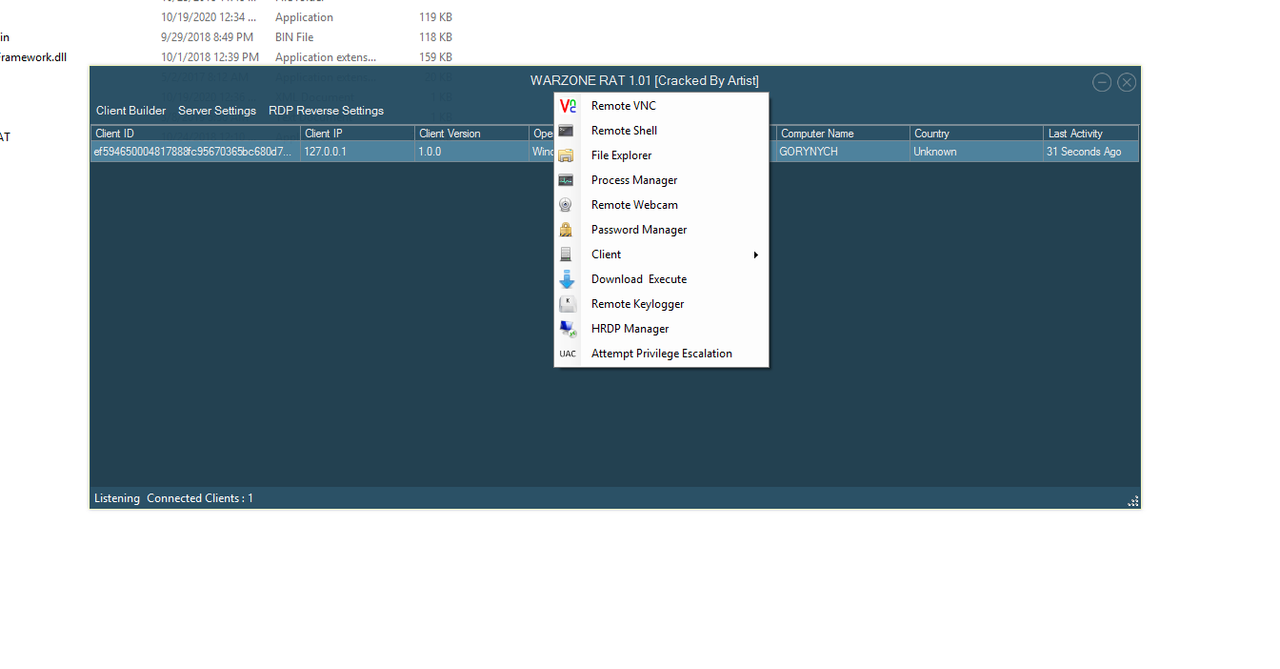
How are Remote Access Trojans Useful to Hackers?
Attackers using remote control malware cut power to 80,000 people by remotely accessing a computer authenticated into SCADA (supervisor y control and data acquisition) machines that controlled the country’s utility infrastructure. RAT software made it possible for the attacker to access sensitive resources through bypassing the authenticated user's elevated privileges on the network. Having access to critical machines that control city resources and infrastructure is one of the biggest dangers of RAT malware.
How to install a RAT?
An attacker must convince the user to install a RAT either by downloading malicious software from the web or running an executable from a malicious email attachment or message. RATs can also be installed using macros in Microsoft Word or Excel documents. When a user allows the macro to run on a device, the macro silently downloads RAT malware and installs it. With the RAT installed, an attacker can now remotely control the desktop, including mouse movement, mouse clicks, camera controls, keyboard actions, and any configured peripherals.
Why do attackers use RATs?
RATs have the same remote-control functionality as RDPs, but are used for malicious purposes. Attackers always code software to avoid detection, but attackers who use a RAT risk being caught when the user is in front of the device and the mouse moves across the screen. Therefore, RAT authors must create a hidden program and use it when the user is not in front of the device. To avoid detection, a RAT author will hide the program from view in Task Manager, a Windows tool that lists all the programs and processes running in memory. Attackers aim to stay hidden from detection because it gives them more time to extract data and explore network resources for critical components that could be used in future attacks.
How do RATs work?
To discover the way RATs work, users can remotely access a device in their home or on a work-related network. RATs work just like standard remote-control software, but a RAT is programmed to stay hidden to avoid detection either from anti-malware software or the device owner.
Why do attackers use remote devices?
Instead of storing the content on their own servers and cloud devices, attackers use targeted stolen devices so that they can avoid having accounts and servers shut down for illegal content.
What is remote control software?
Legitimate remote-control software exists to enable an administrator to control a device remotely. For example, administrators use Remote Desktop Protocol (RDP) configured on a Windows server to remotely manage a system physically located at another site such as a data center. Physical access to the data center isn’t available to administrators, so RDP gives them access to configure the server and manage it for corporate productivity.
What Is a Remote-Access Trojan?
A RAT is a piece of software that gives a stranger the ability to watch anything you do on a device. That stranger can also do anything on your device you're able to do.
Why do hackers use RAT malware?
Every hacker is different, and they all enter the work with different goals and objectives. But in general, people use a tool like this for a few specific purposes.
What are the Remote Access Trojans (RATs) and how they work?
Remote Access Trojans (RATs) also knowns as backdoor Trojans are type of malware that run invisibly on host computers and enable to the intruder remote access and control over the victims personal computer (PC). In general RATs have the nature of ordinary non-malicious remote control programs (i.e. Symantec pcAnywhere, TeamViewer etc. ) but they are designed for illegal installation and operation. RATs grant criminals unlimited access to the infected endpoints and make stealing information easily possible. Some of the RATs are so advanced that the cybercriminal is able to operate from distance the victims PC equally to the physical access to the machine. RATs are generally created by organized malware authors and their aim is to make money out of their efforts.
How do RATs get into a computer?
Usually RATs can get to the users computers through and executable file that person downloads somewhere ( i.e. file sharing environments) or through an e-mail attachment when the user clicks the infected attachment. Hackers tend to hide these Trojan horses in games and other smaller programs that users find harmless and execute them on their PCs.
How to prevent RATs?
As stated previously RATs are malicious programs that give an intruder remote access and control to invisibly act on host PCs. For typical antivirus scanners it is difficult to detect RATs because of binders and intruder encryption routines. Moreover, RATs tend to have the potential to cause significantly more damage than a worm or virus could cause. Finding and removing RATs should be a systems administrator's top priority.
What does RAT mean?
The “A” (for “Access”) in “RAT”, however, means more than simply access to data, which is the aim of many of these malware that can not be categorized as RAT. RAT does not only give access to information stored on the device, but to the functionality of the device as well.
Why do RATs come in client and server components?
Most of the RATs come in client and server components because the malware is hidden in the legitimate installer component. Hackers use a binding program to combine RATs with legitimate executables so that the user is not even aware that RAT is executed when the legitimate program/application is running.
What is a Trojan horse?
Introduction. Computer Trojans or Trojan Horses are named after the mythological Trojan Horse from the Trojan War. During the war Greeks gave a giant wooden horse to their Trojan enemies. As soon as Trojans dragged the horse inside their city walls, Greek soldiers sneaked out of the horse's hollow belly and opened the city gates, ...
Why are RATs so advanced?
Some of the RATs are so advanced that the cybercriminal is able to operate from distance the victims PC equally to the physical access to the machine. RATs are generally created by organized malware authors and their aim is to make money out of their efforts.
What is a RAT trojan?
RAT trojan is typically installed on a computer without its owner’s knowledge and often as a trojan horse or payload. For example, it is usually downloaded invisibly with an email attachment, torrent files, weblinks, or a user-desired program like a game. While targeted attacks by a motivated attacker may deceive desired targets into installing RAT ...
How to protect yourself from remote access trojans?
Just like protecting yourself from other network malware threats, for remote access trojan protection, in general, you need to avoid downloading unknown items; keep antimalware and firewall up to date, change your usernames and passwords regularly; (for administrative perspective) block unused ports, turn off unused services, and monitor outgoing traffic.
What Does a RAT Virus Do?
Since a remote access trojan enables administrative control , it is able to do almost everything on the victim machine.
How does RAT malware work?
Once get into the victim’s machine, RAT malware will hide its harmful operations from either the victim or the antivirus or firewall and use the infected host to spread itself to other vulnerable computers to build a botnet.
What is a RAT?
A remote access trojan (RAT), also called cree pware, is a kind of malware that controls a system via a remote network connection. It infects the target computer through specially configured communication protocols and enables the attacker to gain unauthorized remote access to the victim. RAT trojan is typically installed on a computer without its ...
What does RAT stand for?
RAT can also stand for remote administration tool, which is software giving a user full control of a tech device remotely. With it, the user can access your system just like he has physical access to your device. So, the user can access your files, use your camera, and even turn off or turn on your machine.
Why do RATs use a randomized filename?
It is kind of difficult. RATs are covert by nature and may make use of a randomized filename or file path structure to try to prevent identification of itself. Commonly, a RAT worm virus does not show up in the lists of running programs or tasks and its actions are similar to those of legal programs.
How to prevent remote access Trojans?
One way to prevent these remote access Trojans from being installed is to really examine the software that you’re installing on your computer. This is not a situation where you can trust anything that you download from the internet. You really need to make sure you know what’s being installed.
Where did the Trojan Horse come from?
The malware that we call a Trojan horse comes from the Trojan War where the Greeks used this fake horse to capture the City of Troy from the Trojans. This digital version of the Trojan horse is an application that pretends to be something other than malware in an effort to entice you into running this application.
Can Darkcomet RAT be installed on a production system?
I installed the DarkComet RAT onto a couple of tests systems that I have. I don’t recommend you doing this on a production system. I set up separate virtual machines in a completely isolated system to be able to install this malware. And as you can see, the DarkComet RAT allows the end user to look at the System Information on this computer. It can look and perform scripts, transfer files, look at stored passwords, or even listen to the microphone or view what’s happening on your web cam, all from this single administration front end.
Can anti-virus stop a Trojan horse?
If your anti-virus or your anti-malware software is already aware of this Trojan horse software, it will be able to then stop it from executing even though you’re the one that initiated the process. Once this Trojan horse software gets inside of your computer, it has as much access to your system as you do. So this is a very easy way for malware to find its way inside of your computer with as little effort as possible.
