
What is transactional remote receive?
Transactional remote receive is defined as a transactional receive of a message from a remote queue. Previously, this feature was not available in Message Queuing (MSMQ), and Microsoft also recommended avoiding nontransactional remote receives unless absolutely necessary.
What is remote access and how it works?
Remote access is generally obtained with the combined working of hardware and software with robust network connectivity. For example, standard remote access is available before the widespread internet connection. It is attained by terminal simulation which is managed using a hardware modem linked to a telephonic network.
How do I configure DTC for transactional remote receive?
To use transactional remote receive, you need to configure both the queue computer and the client computer to enable network DTC access. The steps to do this are as follows: Open the Control Panel, open Administrative Tools, and open Component Services.
What is remote transaction in CICS?
A remote transaction is a Customer Information Control System (CICS) asynchronous processing transaction that is owned by other system and is invoked from local CICS system only by SMART command. This definition is also subject to variation.
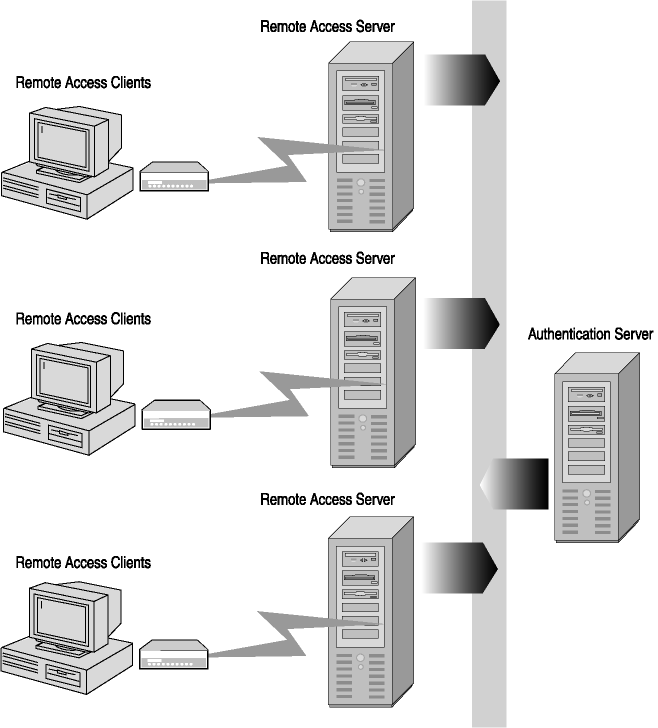
What is remote accessing?
Remote access is the act of connecting to IT services, applications, or data from a location other than headquarters. This connection allows users to access a network or computer remotely via the internet.
What is remote access examples?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
What is remote access in business?
Secure remote access allows employees and IT personnel to safely connect to and manage another user's desktop from a different location. With more people than ever now working from home, secure remote access has become an important IT tool for many organizations.
What happens if you give someone remote access to your computer?
This can be even worse than just conning you out of money, as undetected malware can allow hackers to steal your identity, including your passwords and financial information, over and over again, even if you get new passwords and account numbers.
What are the three main types of remote connections?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What is remote access and its advantages?
Remote access technology gives users the ability to access a computer, device or network from a remote location. Remote access is now commonly used for corporate networks that give their employees the ability to remote access a computer and perform their tasks even without being physically present in the office.
What is the greatest benefit of remote access to an organization?
Flexibility. By allowing your staff to perform tasks outside the office using remote access, you can facilitate more flexible work arrangements and help employees create a better work/life balance.
How do you take remote access?
Use Remote Desktop to connect to the PC you set up: On your local Windows PC: In the search box on the taskbar, type Remote Desktop Connection, and then select Remote Desktop Connection. In Remote Desktop Connection, type the name of the PC you want to connect to (from Step 1), and then select Connect.
How do you secure remote access?
Basic Security Tips for Remote DesktopUse strong passwords. ... Use Two-factor authentication. ... Update your software. ... Restrict access using firewalls. ... Enable Network Level Authentication. ... Limit users who can log in using Remote Desktop. ... Set an account lockout policy.
Can someone remotely access my computer without my knowledge?
There are two ways someone can access your computer without your consent. Either a family member or work college is physically logging in to your computer or phone when you are not around, or someone is accessing your computer remotely.
Is it safe to allow remote access?
Remote access solutions could leave you vulnerable. If you don't have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data. Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular.
Can someone see me through my computer screen?
But, just like any other tech devices, webcams are prone to hacking, which can lead to a serious, unprecedented privacy breach. Think of a case where an authorized person accesses and illegally takes control of your webcam, without your knowledge. Such a person will effortlessly spy on you and the people around you.
What are the types of remote?
In today's electronic market, there are three primary types of remote control systems available to consumers, IR based systems, RD based systems and BT based systems. IR stands for Infrared. Means the remote must be pointed directly at the receiver.
What is remote access equipment?
Remote computer access is the ability to access another computer or network that isn't in your physical presence. Remote computer access allows an employee to access a computer desktop and its files from a remote location. This helps enable an employee who is working from home, for instance, to work effectively.
What is remote access?
The remote access is a method to establish a connection over the server, and it extends the ability to access the network. It allows the user to manage and view the system to fix any faults or requirements when it is not able to connect physically. In other terms, the user can access the system with an internet connection or telecommunication method. IT employees and company chief who are traveling to a different location should need to access the computer networks by using remote access control.
How does Remote Access work?
Remote access is generally obtained with the combined working of hardware and software with robust network connectivity. For example, standard remote access is available before the widespread internet connection. It is attained by terminal simulation which is managed using a hardware modem linked to a telephonic network. The secured remote access is provided by secure software called VPN. It is used to communicate all the hosts by a wired interface network or via internet connection or means of Wi-Fi network interface. The VPN is used to link every individual network to the allotted private networks.
Why should remote desktop services have centralized RDS?
Because the remote desktop service should have the centralized RDS and hence the ability of RDS should be powerful enough to withstand the functional load of the several computer systems. The network should be reliable and adjusted to fit into the properly aligned network.
Why do organizations use remote desktop?
The organization can use remote desktop to allow the user to link the network and applications remotely. The application software that is used in remote desktop is integrated into the operating system of the remote host. It allows the applications to execute in a remote method on a network server which is viewed temporarily at the remote establishment of the remote connection. The user can access safely on the cloud applications from any location on any device by using different authentication techniques that include remote sign on for one time that enables the user secure and easy control to the application without any need of VPN configuration or modification of firewall strategies.
What is a direct remote access line?
It is the direct remote access which is integrated as the direct line from the organization’s LAN to the employee laptop or desktop. The same line is also used to link both the home and the company’s LAN. The direct connection offers robust speed, but the maintenance and cost are expensive. The LAN cable leads to an improper connection, which is prone to data loss and loose connection that affects productivity. So the damage causes the failure of cables because of the external conditions such as construction work and weather conditions.
What is multifactor authentication?
The organization can work on authentication of multifactor attributes to check the identity of users which combines the multiple credentials of a single person who has the chance to build a unique password.
Where is the gateway located?
The gateway or VPN server is situated at every target network and then decrypted the information and then transmit to the concerned host located in the private network. A computer should possess the software which should enable it to associate the system which is hosted in remote access service of the organization.
What is remote access in SQL Server?
The remote access option in SQL Server controls the execution of stored procedures from local or remote servers on which instances of SQL Server are running. And default value of remote access option is 1, which grants permission to run local procedures from remote servers or remote procedures from the local server. If you want to prevent this, set the option to 0.
How to login to SQL Server?
Please login into SQL Server with Windows Authentication mode or SQL Server Authentication mode. 1. In Object Explorer, right-click a server and select Properties. 2. Click the Connections node. 3. Under Remote server connections, select or clear the All remote connections to this server check box.
Allowing Remote Access to your Computer
To use Remote Access, the remote computer must be configured first to accept remote connections. This setting is turned off by default to avoid unwanted connections, but to turn it on, follow these steps −
Use Remote Desktop to access another Computer
Now that you’ve ensured that the remote computer will allow your connection, follow these steps to access it remotely.
