
On demand audit logs provide detailed, cumulative review of access history. Management of remote access to medical devices/systems is critical to addressing security and privacy requirements and minimizing the risk of breaches. Authorized access must be tightly controlled and unauthorized access mitigated.
Full Answer
What is auditlog object in cloud logging?
Every audit log entry in Cloud Logging is an object of type LogEntry. What distinguishes an audit log entry from other log entries is the protoPayload field; this field contains an AuditLog object that stores the audit logging data. To understand how to read and interpret audit log entries, review Understanding audit logs.
How do I access the audit logs?
To access the audit logs, you need to be in one of the following roles: Security Administrator Security Reader Report Reader Global Reader Global Administrator Where can I find it? The Azure portal provides you with several options to access the log. For example, on the Azure Active Directory menu, you can open the log in the Monitoringsection.
How to audit remote access to third parties on your network?
By properly auditing remote access to the third parties on your network. The best way to do this is to enlist the help of a vendor management solution that can automatically track each vendor user’s activity with videos and logs of files transferred, commands entered, and services accessed. There is an old saying: “Trust, but verify.”
What is remote access monitoring and accounting?
Use Remote Access Monitoring and Accounting. Remote Access monitoring reports remote user activity and status for DirectAccess and VPN connections. It tracks the number and duration of client connections (among other statistics), and monitors the operations status of the server.
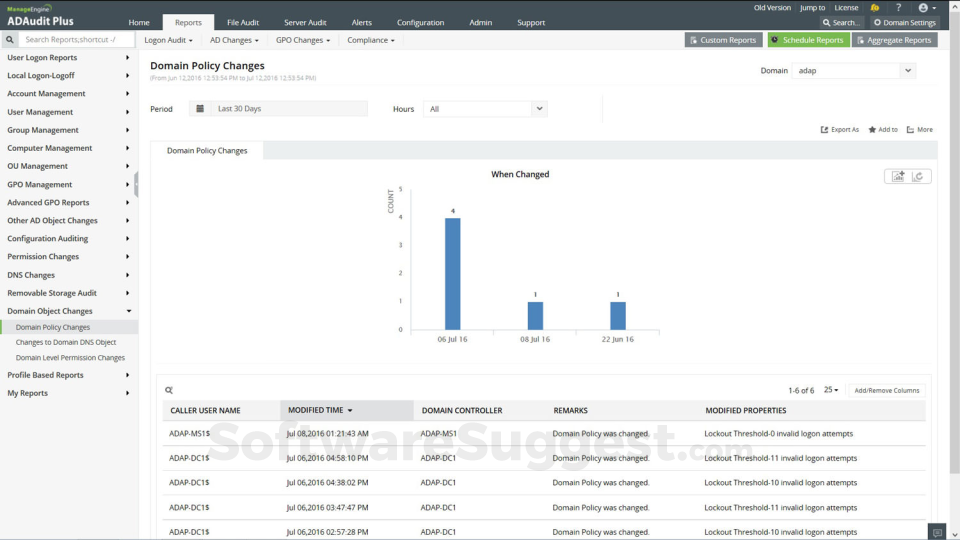
How do I find remote access logs?
To view this remote desktop activity log, go to the Event Viewer. Under Applications and Services Logs -> Microsoft -> Windows -> Terminal-Services-RemoteConnectionManager > Operational.
What is a remote access audit?
Remote Desktop Audit is designed for monitoring the activity of users who access your servers via remote desktop. All information about remote desktop sessions across your servers will be collected in one place, thereby allowing for in-depth data analysis and providing valuable new insights.
How do I find audit logs?
Use the EAC to view the admin audit log In the EAC, go to Compliance management > Auditing, and then choose Run the admin audit log report. In the Search for changes to administrator role groups page that opens, choose a Start date and End date (the default range is the past two weeks), and then choose Search.
How do I check remote history?
In the Windows Tools section, click Remote Control. Click. against the name of a computer to view its remote-control history.
What are the security requirements for remote access?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
What are potential risks associated with remote access?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
What do audit logs show?
Audit logs record the occurrence of an event, the time at which it occurred, the responsible user or service, and the impacted entity. All of the devices in your network, your cloud services, and your applications emit logs that may be used for auditing purposes.
What data can you track using the login audit log?
The audit log provides you an event name and description of the change. It also logs the user who performed the action, the IP address showing where the change was made, and the exact date/time the change was made.
Which activities are recorded by audit logs?
In general, application-level audit trails monitor and log user activities, including data files opened and closed, specific actions, such as reading, editing, and deleting records or fields, and printing reports.
Can you tell if someone is remotely accessing your computer?
To see all the login activities on your PC, use Windows Event Viewer. This tool will show you all Windows services that have been accessed and logins, errors and warnings. To access the Windows Event Viewer, click the search icon and type in Event Viewer. Click Windows Logs, then choose Security.
Can Remote Desktop be monitored?
A: YES, your employer can and has the right to monitor your Citrix, Terminal, and Remote Desktop sessions.
Is there a log file for RDP connections?
Outgoing RDP Connection Logs in Windows You can also view outgoing RDP connection logs on the client side. They are available in the following event log: Application and Services Logs -> Microsoft -> Windows -> TerminalServices-ClientActiveXCore -> Microsoft-Windows-TerminalServices-RDPClient -> Operational.
What are the advantages of a remote audit?
Remote audit benefits range from:Improving the efficiency of the audit: Reduced travel-time. ... Enabling wider access to and sharing of competence: Additional competence or auditor(s) can be added to any audit team in cost-efficient ways. ... Increase your reach & mitigate risk:
What is remote access control?
Remote access control refers to the ability to monitor and control access to a computer or network (such as a home computer or office network computer) anywhere and anytime. Employees can leverage this ability to work remotely away from the office while retaining access to a distant computer or network.
Which is more secure to use when connecting to a device virtually?
VPNs allow employees working remotely to connect to a corporate network by routing their activity through a secure server. VPN systems encrypt data transmitted over the network, so that data is unusable to an attacker eavesdropping on the connection.
What is remote access monitoring?
Remote Access monitoring reports remote user activity and status for DirectAccess and VPN connections. It tracks the number and duration of client connections (among other statistics), and monitors the operations status of the server. An easy-to-use monitoring console provides a view of your entire Remote Access infrastructure. Monitoring views are available for single server, cluster, and multisite configurations.
What is direct access connection?
For DirectAccess, a connection is uniquely identified by the IP address of the remote client. For example, if a machine tunnel is open for a client computer, and a user is connected from that computer, these would be using the same connection. In a situation where the user disconnects and connects again while the machine tunnel is still active, it is a single connection.
What is monitoring in a network?
Monitoring shows actively connected users at a given point in time.
How to mitigate remote vendor access?
In order to mitigate the risks of remote vendor access, and gain better network access control, your organization should take steps to monitor third-party activity in greater detail. In vendor risk assessment, a good first step would be to create a vendor risk assessment checklist, which might include actions such as:
What is audit trail?
An audit trail and access notifications can set off alarms when unusual activity occurs. Granular audit records provide forensic details in the event of a breach or mistake to help track down the root cause and responsible party or parties.
What is vendor privileged access?
With the platform’s vendor privileged access features, enterprises can manage their vendors’ remote access efficiently and securely, while giving tech vendors just the right amount of access to the applications and systems needed to complete their job – and nothing more. You don’t have to be in the dark any longer. Now you can shine a light on who’s doing what on your network, at all times, to get a complete picture of all third-party activity.
What is a security audit platform?
A platform should offer network/IT security audit tools designed to give a total picture of all third-party remote access activity at the individual level. With its detailed audit functionality, organizations can ensure vendor accountability and compliance with industry regulations – and tech vendors can prove the “who, what, where, when, and why” of any remote support session.
What are the features of a secure audit?
Some features of a secure audit include: Real-time specific knowledge of each vendor connection, why they are connecting, and the activity associated with each individual user. Customizable, contextual labels and tags to identify ticket numbers, requestor, and other organization-specific data.
Why use outside vendors?
These third parties provide the ability to scale a business, bring new and vital expertise to bear on problems, and let you concentrate on core competencies . However, vendors can also bring a great deal of risk, especially when it comes to how they access your network and sensitive data.
Why is it important to implement internal audits?
For the sole purpose of risk management, it’s important to implement internal audits that identify and monitor all third-party vendors who have access to your network . Here’s how you can get started.
What is SSOT in log audit?
In order for your log audits to be effective and efficient, strive to create a Single Source of Truth (SSOT) for all vendor activity. Whether you use a Syslog server just for this information or one of the VPAM systems mentioned previously, this will allow your reviewers to see the whole story in one place.
Why is remote access important?
Proper remote access audit processes are important to any information security program . User accounts and rights should regularly be audited against employment records. Logs of router, firewall, and Intrusion Detection Systems (IDS) should be reviewed on a regular basis. Not so surprisingly, all of these reviews should be documented. Access to your networks and systems by third parties should be audited as well, even closer than internal employee activities since this type of access represents an outsized risk to your security. The security of vendors and other third parties may not be as high as your companies and unfortunately, if they are connected to your systems, their vulnerabilities become yours. Also, you don’t have as much information about their employees as you have on your own. Third-party data breaches are on the rise and many regulations now require covered entities to document and secure third-party remote access. For all these reasons, you should keep granular audit records on all third-party access and have a regular process to review them. Only by doing this can you catch a vendor who is breached or who has a malicious current or former employee.
Why use SSOT in vendor audit?
Having an SSOT for vendor audit information will allow you to view the whole story of each session in one place and even connect multiple sessions. This is key to being able to “see the forest for the trees” in audit data.
Why is it important to audit third party access?
Doing audits of third-party remote access is important, but doing them right makes all the difference. If you have only cursory access reviews or only go to your logs when there is an issue, you stand little chance of stopping a breach in progress or before it starts. Get your third party review processes, procedures, and technology up to par, because if you are only using audits sporadically or after an issue crops up, it is probably too late. To learn more about the importance of auditing correctly, check out our blog that highlights how you can survive your next cybersecurity audit.
Can a third party remote access be a hacker?
This is especially true of third-party remote access since it’s coming from an external source that is often not easily identifiable. Strange IP addresses could be a remote contractor or a hacker bent on destruction, but it’s hard to tell that from typical firewall or router logs that contain little else.
Do you need to keep granular audit records for third party access?
Third-party data breaches are on the rise and many regulations now require covered entities to document and secure third-party remote access. For all these reasons, you should keep granular audit records on all third-party access and have a regular process to review them.
How to check RDP logs?
You can check the RDP connection logs using Windows Event Viewer ( eventvwr.msc ). Windows logs contain a lot of data, and it is quite difficult to find the event you need. When a user remotely connects to the remote desktop of RDS (RDP), a whole number of events appears in the Windows Event Viewer. There are several different logs where you can find the information about Remote Desktop connections. We’ll look at the logs and events on the main stages of an RDP connection that may be of interest to the administrator:
Where is the RDP authentication log?
Authentication shows whether an RDP user has been successfully authenticated on the server or not. The log is located in “Windows -> Security”. So you may be interested in the events with the EventID 4624 ( An account was successfully logged on) or 4625 ( An account failed to log on ). Please, pay attention to the LogonType value in the event description. If the Remote Desktop service has been use to create new session during log on, LogonType = 10. If the LogonType = 7, it means that a user has reconnected to the existing RDP session.
What does 9009 mean in RDP?
The event with the EventID 9009 ( The Desktop Window Manager has exited with code <X>) in the System log means that a user has initiated logoff from the RDP session with both the window and the graphic shell of the user have been terminated.
What is logoff in Windows?
Logoff refers to the user logoff from the system. It is logged as the event with the EventID 23 ( Remote Desktop Services: Session logoff succeeded) in “Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-LocalSessionManager -> Operational”.
What is EventID 4778?
The event with the EventID 4778 in Windows -> Security log (A session was reconnected to a Window Station). A user has reconnected to an RDP session (a user is assigned a new LogonID).
What does the RDP session ID return?
The command returns the session ID (ID), the name of user (USERNAME) and the session state (Active/Disconnect). It is convenient to use this command when you need to get the ID of the user RDP session in case shadow connection is used.
What does the logs do on a RDP server?
Then you will get an event list with the history of all RDP connections to this server. As you can see, the logs provide a username, a domain (in this case the Network Level Authentication is used; if NLA is disabled, the event text looks differently) and the IP address of the computer, from which the RDP connection has been initiated.
What is audit log in Azure AD?
With the audit logs in Azure AD, you get access to records of system activities for compliance. The most common views of this log are based on the following categories:
Who can access it?
To access the audit logs, you need to be in one of the following roles:
What is the service filter in audit?
You can filter the audit data on the following fields: The Service filter allows you to select from a drop-down list of the following services: The Category filter enables you to select one of the following filters: The Activity filter is based on the category and activity resource type selection you make.
What does IT administrator do?
The information about your system’s health enables you to assess whether and how you need to respond to potential issues.
How to find audit logs?
To find and view audit logs, you need to know the identifier of the Cloud project, folder, or organization for which you want to view audit logging information. You can further specify other indexed LogEntry fields, like resource.type; for details, review Finding log entries quickly.
What is data access audit log?
Data Access audit logs contain API calls that read the configuration or metadata of resources, as well as user-driven API calls that create, modify, or read user-provided resource data.
What is IAM permissions?
IAM permissions and roles determine your ability to access audit logs data in the Logging API, the Logs Explorer, and the gcloud command-line tool.
What is cloud logging?
Cloud Logging uses log buckets as containers that store and organize your logs data. For each Cloud project, folder, and organization Logging automatically creates two log buckets, _Required and _Default, and correspondingly named sinks.
How to view audit logs in Cloud?
To view abbreviated audit log entries in the Cloud Console, do the following: Go to the Activity page: Go to the Activity page. In the project selector, select the Cloud project or organization for which you want to view audit logs entries. In the Filter panel, select the entries you want to view.
What is gcloud command line?
The gcloud command-line tool provides a command-line interface to the Cloud Logging API. Supply a valid PROJECT_ID, FOLDER_ID , or ORGANIZATION_ID in each of the log names.
What is system event audit?
System Event audit logs contain log entries for Google Cloud actions that modify the configuration of resources. System Event audit logs are generated by Google systems; they aren't driven by direct user action.
