What is remote access monitoring and accounting?
Use Remote Access Monitoring and Accounting. Remote Access monitoring reports remote user activity and status for DirectAccess and VPN connections. It tracks the number and duration of client connections (among other statistics), and monitors the operations status of the server.
Is remote work impacting the internal audit profession?
… This new report, “The Remote Auditor: Challenges, opportunities, and new ways of working,” by the Internal Audit Foundation and AuditBoard presents poll and survey results that help assess the impact of remote work in the internal audit profession. It also offers options for sustaining a positive workplace culture in a virtual setting.
What is remote access monitoring in Windows Server 2016?
Applies To: Windows Server (Semi-Annual Channel), Windows Server 2016. Remote Access monitoring reports remote user activity and status for DirectAccess and VPN connections. It tracks the number and duration of client connections (among other statistics), and monitors the operations status of the server.
What is the remote access monitoring console?
An easy-to-use monitoring console provides a view of your entire Remote Access infrastructure. Monitoring views are available for single server, cluster, and multisite configurations. Note: Windows Server 2012 combines DirectAccess and Routing and Remote Access Service (RRAS) into a single Remote Access role.
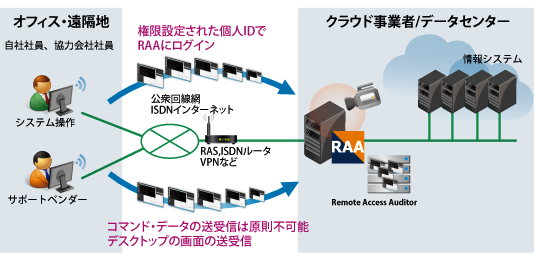
What is remote access monitoring?
Remote Access monitoring reports remote user activity and status for DirectAccess and VPN connections. It tracks the number and duration of client connections (among other statistics), and monitors the operations status of the server. An easy-to-use monitoring console provides a view of your entire Remote Access infrastructure. Monitoring views are available for single server, cluster, and multisite configurations.
What is direct access connection?
For DirectAccess, a connection is uniquely identified by the IP address of the remote client. For example, if a machine tunnel is open for a client computer, and a user is connected from that computer, these would be using the same connection. In a situation where the user disconnects and connects again while the machine tunnel is still active, it is a single connection.
Why is it important to audit third party access?
Doing audits of third-party remote access is important, but doing them right makes all the difference. If you have only cursory access reviews or only go to your logs when there is an issue, you stand little chance of stopping a breach in progress or before it starts. Get your third party review processes, procedures, and technology up to par, because if you are only using audits sporadically or after an issue crops up, it is probably too late. To learn more about the importance of auditing correctly, check out our blog that highlights how you can survive your next cybersecurity audit.
Why is remote access important?
Proper remote access audit processes are important to any information security program . User accounts and rights should regularly be audited against employment records. Logs of router, firewall, and Intrusion Detection Systems (IDS) should be reviewed on a regular basis. Not so surprisingly, all of these reviews should be documented. Access to your networks and systems by third parties should be audited as well, even closer than internal employee activities since this type of access represents an outsized risk to your security. The security of vendors and other third parties may not be as high as your companies and unfortunately, if they are connected to your systems, their vulnerabilities become yours. Also, you don’t have as much information about their employees as you have on your own. Third-party data breaches are on the rise and many regulations now require covered entities to document and secure third-party remote access. For all these reasons, you should keep granular audit records on all third-party access and have a regular process to review them. Only by doing this can you catch a vendor who is breached or who has a malicious current or former employee.
Why use SSOT in vendor audit?
Having an SSOT for vendor audit information will allow you to view the whole story of each session in one place and even connect multiple sessions. This is key to being able to “see the forest for the trees” in audit data.
What is SSOT in log audit?
In order for your log audits to be effective and efficient, strive to create a Single Source of Truth (SSOT) for all vendor activity. Whether you use a Syslog server just for this information or one of the VPAM systems mentioned previously, this will allow your reviewers to see the whole story in one place.
Can a third party remote access be a hacker?
This is especially true of third-party remote access since it’s coming from an external source that is often not easily identifiable. Strange IP addresses could be a remote contractor or a hacker bent on destruction, but it’s hard to tell that from typical firewall or router logs that contain little else.
Do you need to keep granular audit records for third party access?
Third-party data breaches are on the rise and many regulations now require covered entities to document and secure third-party remote access. For all these reasons, you should keep granular audit records on all third-party access and have a regular process to review them.
When incorporating remote facility review into a larger remote auditing plan, should auditors note the areas they feel need?
When incorporating remote facility review into a larger remote auditing plan, auditors should note the areas they feel need to be captured through visual media like photos and video during document review. As part of this document review, auditors should note known or possible process problems, such as complaints, CAPAs, and deviations, so that they can be evaluated remotely.
Why are firms turning to remote audits?
For quality and compliance teams, the sudden workforce disruption is complicating—and often preventing— in-person quality audits led by qualified third parties. To avoid compounding delays due to canceled or deferred audits, firms are increasingly turning to remote or “virtual” audits to maintain their assurance activities until normal operations can resume.
What should be checked during a Wi-Fi audit?
Connectivity and A/V checks: If a live facility walkthrough is included in the audit, the route should be checked with devices that will be used to livestream the audit prior to audit day to ensure wi-fi dead spots don’t threaten the process. This guide offers more detail on this point during its discussion of facility reviews.
How long should an audit be completed?
If an audit is typically completed in two days, for example, an additional half day may be needed to conduct the same activities remotely.
What is a legal document that prohibits recording?
Legal agreements barring electronic recordings: A legal document should be produced and signed by both parties to prohibit any recording of screen-shares, livestreams, or other media transmitted remotely. The risks of recording in a remote project will likely not be mitigated by existing contractual clauses.
Is remote auditing as efficient as on-site auditing?
Remote auditing is rarely as efficient as on-site auditing, so consider whether sampling may be necessary. Especially in areas where a full data review is traditionally conducted, be sure to coordinate a sampling strategy with the auditor and review the strategy with audit participants so sampling can be done accurately and appropriately.
Is remote auditing more difficult than in person?
However, since making a contemporaneous change in a remote setting is typically more difficult than it is in person, and each audit activity may demand more time due to technical limitations, a remote audit should be fully choreographed in as much detail as possible from the start.