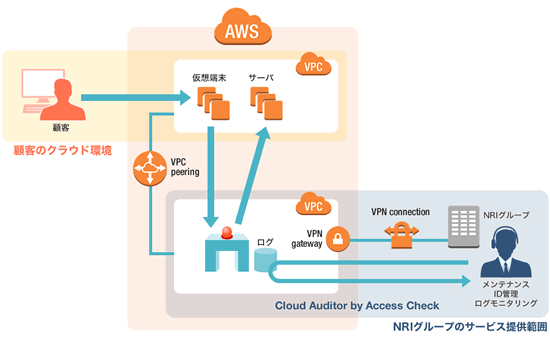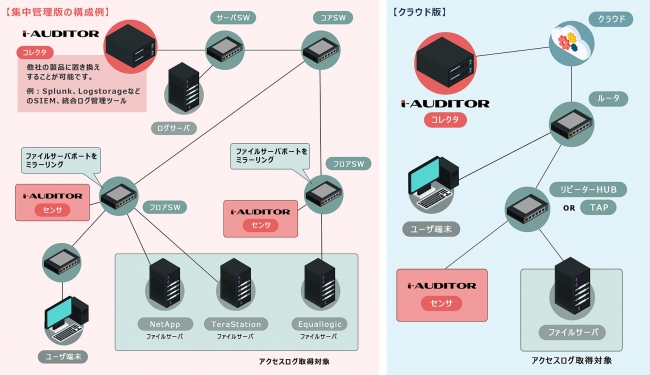
What is access auditor?
Access Auditor streamlines and automates the discovery, review, reporting, and alerting of user access rights with an easy-to-use web-based application. Forget the spreadsheets, and let Access Auditor simplify your user entitlement reviews. Access Auditor has connectors to nearly every major cloud provider and on-premise application.
How to audit remote access to third parties on your network?
By properly auditing remote access to the third parties on your network. The best way to do this is to enlist the help of a vendor management solution that can automatically track each vendor user’s activity with videos and logs of files transferred, commands entered, and services accessed. There is an old saying: “Trust, but verify.”
Why audit remote vendor access?
Proper auditing of remote vendor access achieves three vital goals: 1 An ongoing audit ensures accountability and compliance. 2 An audit trail and access notifications can set off alarms when unusual activity occurs. 3 Granular audit records provide forensic details in the event of a breach or mistake to help track down the root cause... More ...
Why do you need a remote support audit?
With its detailed audit functionality, organizations can ensure vendor accountability and compliance with industry regulations – and tech vendors can prove the “who, what, where, when, and why” of any remote support session.
What is a security audit platform?
A platform should offer network/IT security audit tools designed to give a total picture of all third-party remote access activity at the individual level. With its detailed audit functionality, organizations can ensure vendor accountability and compliance with industry regulations – and tech vendors can prove the “who, what, where, when, and why” of any remote support session.
How to mitigate remote vendor access?
In order to mitigate the risks of remote vendor access, and gain better network access control, your organization should take steps to monitor third-party activity in greater detail. In vendor risk assessment, a good first step would be to create a vendor risk assessment checklist, which might include actions such as:
What is vendor privileged access?
With the platform’s vendor privileged access features, enterprises can manage their vendors’ remote access efficiently and securely, while giving tech vendors just the right amount of access to the applications and systems needed to complete their job – and nothing more. You don’t have to be in the dark any longer. Now you can shine a light on who’s doing what on your network, at all times, to get a complete picture of all third-party activity.
What are the features of a secure audit?
Some features of a secure audit include: Real-time specific knowledge of each vendor connection, why they are connecting, and the activity associated with each individual user. Customizable, contextual labels and tags to identify ticket numbers, requestor, and other organization-specific data.
What is audit trail?
An audit trail and access notifications can set off alarms when unusual activity occurs. Granular audit records provide forensic details in the event of a breach or mistake to help track down the root cause and responsible party or parties.
Why is it important to implement internal audits?
For the sole purpose of risk management, it’s important to implement internal audits that identify and monitor all third-party vendors who have access to your network . Here’s how you can get started.