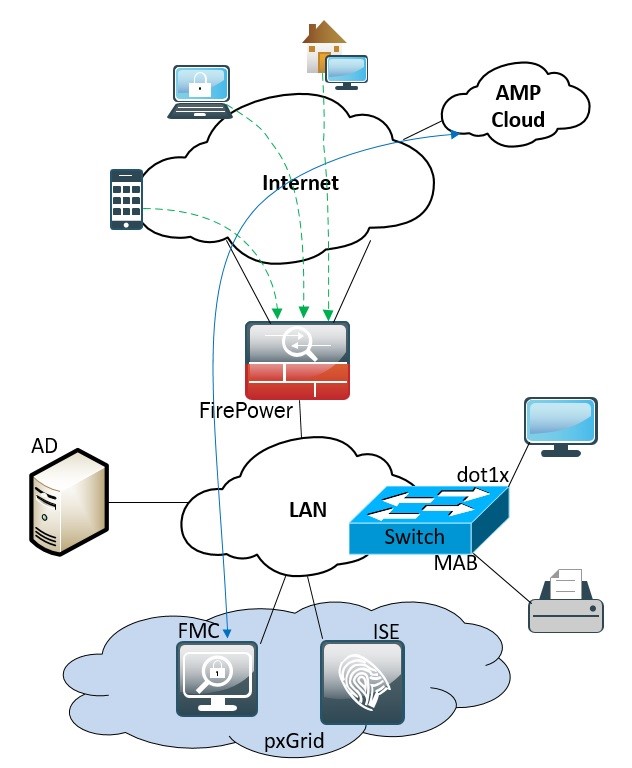
remote access servers support the following set of authentication methods:
- Password Authentication Protocol (PAP)
- Challenge Handshake Authentication Protocol (CHAP)
- Microsoft’s implementation of CHAP (MS-CHAP)
- Updated version of MS-CHAP (MS-CHAP2)
- Extensible Authentication Protocol/Transport Layer Security (EAP/TLS)
Full Answer
What is used by remote access protocols for authentication?
Authentication is the process of proving identity. Common protocols used for remote access authentication include PAP, CHAP, MS-CHAP, or EAP. Usernames and passwords are used during identification and authentication as authentication credentials. SLIP and PPP are remote access connection protocols that are used to establish and negotiate ...
How to setup remote access?
Once installed, you can now connect to remote endpoints by following the steps below:
- The software needs to be downloaded on both the local and remote computers.
- Open the software on both the local and remote computers.
- Write down the ITarian ID number and password of the remote computer.
- Click “Start Connection.”
- Enter the ID number and password of the remote computer.
- Click “Connect.”
How to protect remote access?
To enable Remote Access in your UniFi Protect application:
- Access the UniFi OS Console hosting Protect via its IP address. ...
- Log in to your Ubiquiti SSO account.
- Go to the System Settings > Advanced menu, and enable the Remote Access toggle.
How to authenticate remote users?
Using a personal authentication token or password Using an SSH key Using your GitHub password with 2-factor authentication; With either of the first two approaches you can avoid entering a username and password each time you interact with the remote repository, as discussed below.
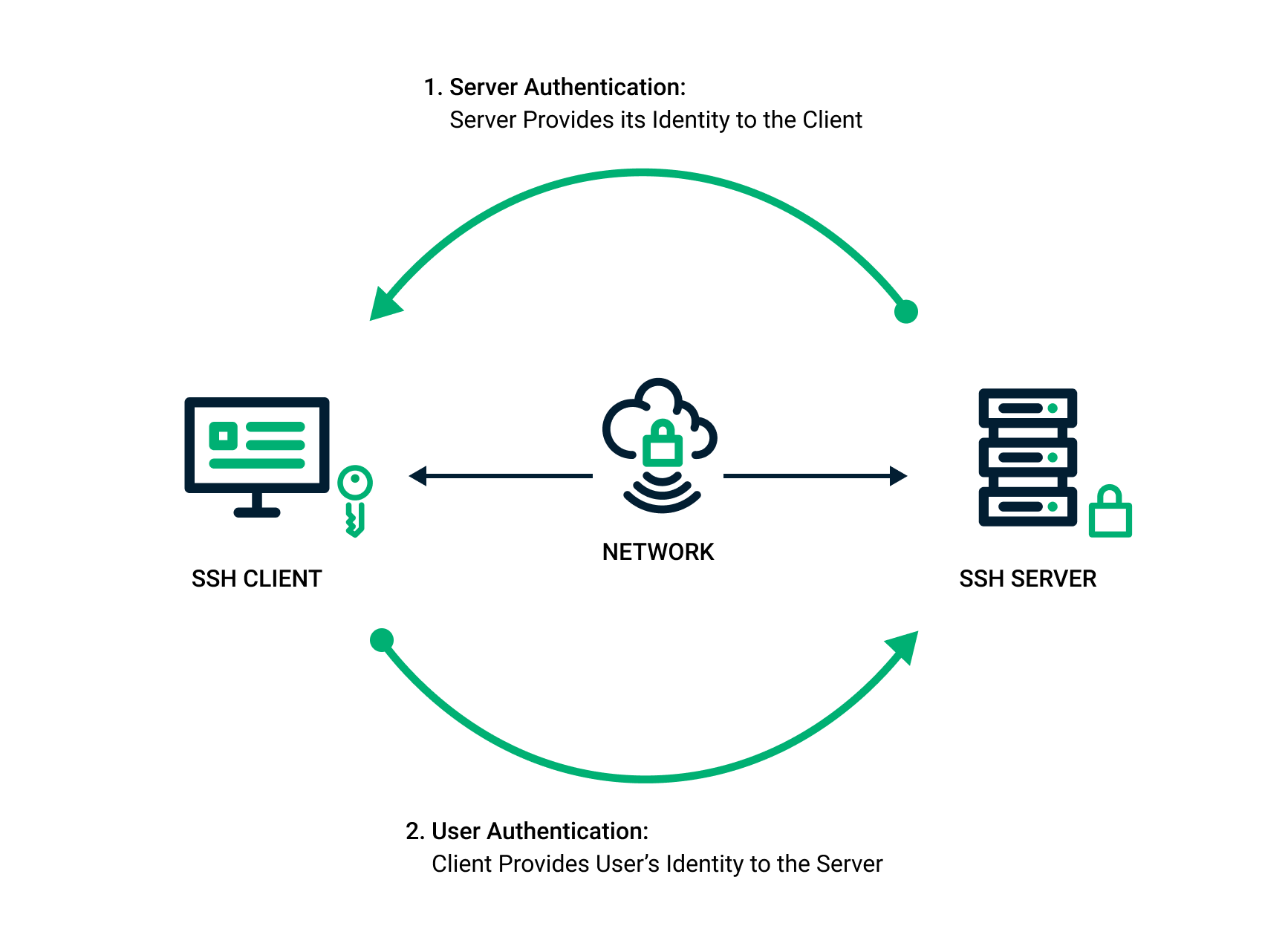
Which 2 methods of authentication can be used for remote access connections?
remote access servers support the following set of authentication methods:Password. Authentication Protocol (PAP)Challenge. Handshake Authentication Protocol (CHAP)Microsoft's. implementation of CHAP (MS-CHAP)Updated. version of MS-CHAP (MS-CHAP2)Extensible. Authentication Protocol/Transport Layer Security (EAP/TLS)
What are the 3 user authentication mechanisms?
Multi-factor authentication Examples include codes generated from the user's smartphone, Captcha tests, fingerprints, voice biometrics or facial recognition. MFA authentication methods and technologies increase the confidence of users by adding multiple layers of security.
How does remote user authentication work?
In remote user authentication scheme, the user is assigned a smart card, which is being personalized by some parameters and provide the legal users to use the resources of the remote system.
What is remote network authentication?
Authentication is a way to restrict access to specific users when these users access a remote machine. Authentication can be set up at both the machine level and the network level.
What are the 4 general forms of authentication?
Four-factor authentication (4FA) is the use of four types of identity-confirming credentials, typically categorized as knowledge, possession, inherence and location factors.
What are the 3 types of authentication?
The three authentication factors are: Knowledge Factor – something you know, e.g., password. Possession Factor – something you have, e.g., mobile phone. Inherence Factor – something you are, e.g., fingerprint.
What is the best remote access authentication?
Extensible Authentication Protocol-Transport Level Security is the most secure remote authentication protocol. It uses certificates on both the client and the server to provide mutual authentication, data integrity, and data confidentiality.
Why is remote authentication important?
MFA is important for remote workers for not only preventing unauthorized access, but in improving your organization's overall security posture. This is thanks to one of the great features of MFA: when an attempt is made to get into someone's account from an unauthorized device, the user will get a notification.
What does Ntlm stand for?
(New Technology) LAN ManagerIn a Windows network, NT (New Technology) LAN Manager (NTLM) is a suite of Microsoft security protocols intended to provide authentication, integrity, and confidentiality to users. NTLM is the successor to the authentication protocol in Microsoft LAN Manager (LANMAN), an older Microsoft product.
What is remote access examples?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
What is remote access requirements?
Remote computer access requires a reliable internet connection. You'll need to activate or install software on the device you want to access, as well as on the device — or devices — you want to use to get that access.
What is remote access control?
Remote access control refers to the ability to monitor and control access to a computer or network (such as a home computer or office network computer) anywhere and anytime. Employees can leverage this ability to work remotely away from the office while retaining access to a distant computer or network.
What is the most common authentication mechanism?
Password-based authentication Also known as knowledge-based authentication, password-based authentication relies on a username and password or PIN. The most common authentication method, anyone who has logged in to a computer knows how to use a password.
What is a user authentication?
User authentication verifies the identity of a user attempting to gain access to a network or computing resource by authorizing a human-to-machine transfer of credentials during interactions on a network to confirm a user's authenticity.
What are the user authentication mechanism in ecommerce?
Two-factor authentication requires using two different methods to authenticate that the customer is who they claim to be. The first factor used in ecommerce is usually a name and password. The second factor can be any number of things, including a PIN or a code sent via text message.
What are the different types of authentication factors?
The five main authentication factor categories are knowledge factors, possession factors, inherence factors, location factors, and behavior factors.
What is remote access server?
Remote access servers can be configured as dial-in servers or VPN servers. Dial-in servers use the Point-to-Point Protocol (PPP) or in the case of some older servers, the Serial Line Internet Protocol (SLIP) as the link layer protocol. VPN servers can use the Point-to-Point Tunneling Protocol (PPTP), Layer 2 Tunneling Protocol (L2TP), or IPSec tunnel mode to establish a secure "tunnel" over the Internet. Windows remote access servers support the following set of authentication methods: 1 Password Authentication Protocol (PAP) 2 Challenge Handshake Authentication Protocol (CHAP) 3 Microsoft's implementation of CHAP (MS-CHAP) 4 Updated version of MS-CHAP (MS-CHAP2) 5 Extensible Authentication Protocol/Transport Layer Security (EAP/TLS)
What does authenticator do?
The authenticator also calculates the hash value and compares the client's response with its own calculation. If the values match, the connection is established.
What is EAP TLS?
EAP/TLS provides for use of more secure authentication methods such as smart cards, Kerberos, and digital certificates, which are much more secure than the user name/password authentication methods above. It's defined in RFC 2716.
What is a RADIUS authorization?
Authorization refers to granting specific services to users based on their authenticated identity; restrictions can be imposed on certain users. Accounting refers to tracking the use of the network by users and can be done for billing, management, or security purposes. RADIUS is defined in RFCs 2865 and 2866.
Is MS-CHAP v2 secure?
Version 2 adds such features as mutual (two-way) authentication of both client and server, as well as stronger encryption keys. MS-CHAP v2 is more secure than CHAP for Windows systems.
Can you have multiple remote access servers on Windows 2003?
Windows 2003 Server Enterprise Edition's IAS implementation puts no limits on the number of RADIUS clients you can configure or on the number of RADIUS server groups you can have. Even more importantly, a single RADIUS server can support many remote access servers, so that as you add additional dial-in and/or VPN servers, their users are all still authenticated through one central point: the RADIUS server. The fact that the authentication server is separate from the access server (s) makes this both more secure and more scalable than other authentication methods.
Which service can provide both authentication and authorization at the network level?
The LDAP directory service and the NIS+ name service can provide both authentication and authorization at the network level.
What is remote login?
The remote login commands enable users to log in to a remote machine over the network and use its resources. The remote login commands are rlogin, rcp, ftp. If you are a “trusted host,” authentication is automatic. Otherwise, you are asked to authenticate yourself.
What encryption does Kerberos use?
Kerberos uses DES encryption to authenticate a user when logging in to the system.
What is remote access authentication protocol?
A remote access authentication protocol is the method by which remote users will be authenticated when they log on the network. One (unwise) choice is to allow users to log on without authentication.
What is EAP authentication?
EAP allows for authentication of a remote access connection through the use of authentication schemes, known as EAP types. EAP offers the strongest security by providing the most flexibility in authentication variations. EAP can support authentication mechanisms, such as token cards, smart cards, certificates, and public key encryption authentication.
What is secure authentication?
Secure authentication (i.e., for higher levels of assurance) requires a multi-factor approach. In general, the combination of authentication factors should include some or all of the three above categories.
When identity data shared by the ID system and stored by the relying party as part of the authentication mechanism, what?
When identity data shared by the ID system and stored by the relying party as part of the authentication mechanism, ensure that information is secured in order to prevent loss or compromise.
What is federation in identity?
Federation is the ability of one organization to accept another organization’s identity credentials for authentication based on inter-organizational trust. The trusting organization must be comfortable that the other identity provider has acceptable policies, and that those policies are being followed. Federation protocols and assurance and trust frameworks facilitate federation of digital identity between organizations. For federation to be effectively used globally, agreement and mapping with the ISO defined assurance framework and the adoption of standards are critical (Source: Catalog of Technical Standards ).
Why is online authentication important?
Ultimately, online authentication provides a higher level of assurance because it offers more potential authentication factors and a “live” source. At the same time, it may also bring greater data protection and cybersecurity risks.
What is the purpose of establishing a secure communication channel between the relying parting (service provider) and?
Establish a secure communication channel between the relying parting (service provider) and the identity provider to enable an authentication workflow between the service provider and identity provider application. This is typically done using digital certificates to secure communication and may also involve passwords (a shared secret) to authenticate the application.
What is the level of assurance provided by online mechanisms?
The authentication level of assurance provided by online mechanisms varies according to the specific credentials, authenticators, and protocols used. In addition to choosing authentication methods with levels of assurance appropriate to the transaction, practitioners must consider their accessibility and convenience, particularly for vulnerable persons (e.g., low literacy, the elderly, and people with disabilities), and those with unreliable internet or mobile connections. For example, card-based authentication for remote transactions (e.g., e-services) would require the purchase and distribution of card and/or biometric readers to each person, which may be a barrier to adoption.
What is manual verification of ID?
Manual (non-digital) comparison (i.e., taking an ID card at face value): Traditionally, authentication processes have involved the manual inspection of credentials (commonly ID cards) to determine that they are genuine ( e.g., via embedded security features) and assess whether the person or their physical signature resembles the photo or signature included on the credential. While this method is intuitive and requires less infrastructure (beyond providing the credentials themselves), it provides a lower level of assurance and more opportunities for corruption than digital authentication due to the potential for human error and/or discretion in applying the procedure. At the same time, this may be appropriate for certain low-risk transactions and/or the only viable solution in areas with no connectivity or electricity. If security features are to be a viable method of improving the reliability of authentication, relying parties need to be aware and appropriately equipped—e.g., I the case of level 2 (covert) security features, this might require a UV light.
How does secure remote access work?
Every remote worker needs a way to connect with remote desktop services and applications that won't slow down their workflows. At the same time, IT administrators must manage those connections to ensure they don't leave the network open to threats.
Why is secure remote access important to remote work security?
Secure remote access approaches are so vital because it’s now impossible to control security at the endpoint. Each user in a remote or hybrid workforce is connecting to the network from a different type of computer or smartphone, and they’re using a variety of internet connections to log in.
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
Why use two factor authentication for VPN?
Adopting two-factor authentication for remote access through VPN further boosts your network security. Now let’s take a look at why you should choose a particular VPN type as a secure connection methodology instead of the alternatives.
What are the implications of IPSec connections for corporations?
What are the implications of IPSec connections for corporations, considering the very nature of this connection? Well, your employee will only be able to access the network from a single, authorized device. Security is further boosted by the enforcement of antivirus and firewall policies.
What is IPSEC encryption?
IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect data flows between hosts and security gateways.
What is the first thing that’s required to ensure smooth remote access via a VPN?
The first thing that’s required to ensure smooth remote access via a VPN is to plan out a comprehensive network security policy.
What is the line of defense for remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly.
Why do devices have administrator rights?
To ensure that no unauthorized software is able to install itself, or by a user, and cause a virus, worm, Trojan or malware infection on a device, each device must deny administrator rights to the user of that particular device or all the employees in general. This ensures protection against Distributed Denial of Service (DDoS) attacks.
What is access control?
Access control makes sure that only authenticated and authorized users can access resources. Sometimes there is a bit of confusion between access control and authorization, or between authentication and identification. Let’s clarify all of them and give some examples.
What is the third step of access control?
Authorization is the third step of access control.
Why is access control important?
Access control is paramount for security and fatal for companies failing to design it and implement it correctly.
