Windows remote access servers support the following set of authentication methods:
- Password Authentication Protocol (PAP)
- Challenge Handshake Authentication Protocol (CHAP)
- Microsoft’s implementation of CHAP (MS-CHAP)
- Updated version of MS-CHAP (MS-CHAP2)
- Extensible Authentication Protocol/Transport Layer Security (EAP/TLS)
- Password. Authentication Protocol (PAP)
- Challenge. Handshake Authentication Protocol (CHAP)
- Microsoft's. implementation of CHAP (MS-CHAP)
- Updated. version of MS-CHAP (MS-CHAP2)
- Extensible. Authentication Protocol/Transport Layer Security (EAP/TLS)
What is a remote authentication protocol?
The acronym is actually fairly descriptive of what it does: The worker will remotely authenticate for access to that remote network. I have previously mentioned that I like to map protocols before to the OSI Reference Model. This helps one visualize just what protocols belong where in the grand scheme of things.
What are the different types of remote access authentication?
Remote access authentication options. Remote access servers can be configured as dial-in servers or VPN servers. Dial-in servers use the Point-to-Point Protocol (PPP) or in the case of some older servers, the Serial Line Internet Protocol (SLIP) as the link layer protocol.
What authentication methods are supported by OpenWindows remote access servers?
Windows remote access servers support the following set of authentication methods: Extensible Authentication Protocol/Transport Layer Security (EAP/TLS) For security purposes, PAP can be excluded as a viable option for most businesses because it sends passwords across the phone line or Internet in plain text.
What is the use of authentication?
Authentication is a way to restrict access to specific users when these users access a remote machine. Authentication can be set up at both the machine level and the network level.
What is SMS code?
What is iproov verification?
Why is authentication important?
Why is SMS code so frustrating?
What happens if your authentication process takes too long?
What is face authentication?
Why are passwords not secure?
See more
About this website

What is the best remote access authentication?
Extensible Authentication Protocol-Transport Level Security is the most secure remote authentication protocol. It uses certificates on both the client and the server to provide mutual authentication, data integrity, and data confidentiality.
What are 4 methods of authentication?
The most common authentication methods are Password Authentication Protocol (PAP), Authentication Token, Symmetric-Key Authentication, and Biometric Authentication.
How do I authenticate remote users?
In the management GUI, select Settings > Security > Remote Authentication. Select Configure Remote Authentication. Select LDAP. Select the type of LDAP server that is used for authentication.
What are the 3 authentication methods?
Authentication factors can be classified into three groups: something you know: a password or personal identification number (PIN); something you have: a token, such as bank card; something you are: biometrics, such as fingerprints and voice recognition.
What are the five 5 authentication methods?
5 Common Authentication TypesPassword-based authentication. Passwords are the most common methods of authentication. ... Multi-factor authentication. ... Certificate-based authentication. ... Biometric authentication. ... Token-based authentication.
Which methods are used in authentication?
Password-based authentication. Also known as knowledge-based authentication, password-based authentication relies on a username and password or PIN. ... Two-factor/multifactor authentication. ... Biometric authentication. ... Single sign-on. ... Token-based authentication. ... Certificate-based authentication.
What is Kerberos authentication?
Kerberos authentication is a multistep process that consists of the following components:The client who initiates the need for a service request on the user's behalf.The server, which hosts the service that the user needs access to.The AS, which performs client authentication.More items...
How many types of authentication protocols are there?
EAP - Extensible Authentication Protocol More than 40 EAP-methods exist, the most common are: EAP-MD5. EAP-TLS. EAP-TTLS.
What are the common methods of authentication for network security?
6 Common network authentication methodsPassword-based authentication. Passwords are the most common network authentication method. ... Two-factor authentication. ... Multi-factor authentication. ... CAPTCHAs. ... Biometrics authentication. ... Certificate-based authentication.
How many types of authentication are there?
There are three basic types of authentication. The first is knowledge-based — something like a password or PIN code that only the identified user would know. The second is property-based, meaning the user possesses an access card, key, key fob or authorized device unique to them. The third is biologically based.
What is authentication What are the types of authentication?
What are the types of authentication? Authentication keeps invalid users out of databases, networks, and other resources. These types of authentication use factors, a category of credential for verification, to confirm user identity.
What is the most common form of authentication?
Password - The use of a user name and password provides the most common form of authentication. You enter your name and password when prompted by the computer. It checks the pair against a secure file to confirm.
What is an example of authentication?
In computing, authentication is the process of verifying the identity of a person or device. A common example is entering a username and password when you log in to a website.
How to configure WinRM client?
To set the configuration for the WinRM client, use the Winrm Setcommand and specify the client. For example, the following command disables digest authentication for the client.
How to enable certificate authentication on WinRM?
You must first enable certificate authentication on both the client and service by using the Winrm command line tool. For more information, see Enabling Authentication Options. You must also create an entry in the CertMapping table on the WinRM server computer. This establishes a mapping between one or more certificates and a local account. After the certificate has been used for authentication and authorization, the corresponding local account is used for operations performed by the WinRM service.
What is the default method for a remote computer?
If you supply explicit credentials with a ConnectionOptionsobject, Negotiate is the default method. Negotiate authentication determines whether the ongoing authentication method is Kerberos or NTLM, depending on whether the computers are in a domain or workgroup. If connecting to a remote target computer using a local account, then the account should be prefixed with the computer name. For example, myComputermyUsername.
What is the default method of authentication when the client is in a domain and the remote destination string is not one of?
Kerberosis the default method of authentication when the client is in a domain and the remote destination string is not one of the following: localhost, 127.0.0.1, or [::1].
What is UAC in WinRM?
User Account Control (UAC)affects access to the WinRM service. When Negotiate authentication is used in a workgroup, only the built-in Administrator account can access the service. To allow all accounts in the Administrators group to access the service, set the following registry value:
How to add a user to WinRM?
You can add a local user, domain user, or domain group to WinRMRemoteWMIUsers__by typing net localgroup WinRMRemoteWMIUsers__ /add <domain><username>at the command prompt. Optionally, you can use the Group Policy to add a user to the group.
What is remote management?
Windows Remote Management maintains security for communication between computers by supporting several standard methods of authentication and message encryption.
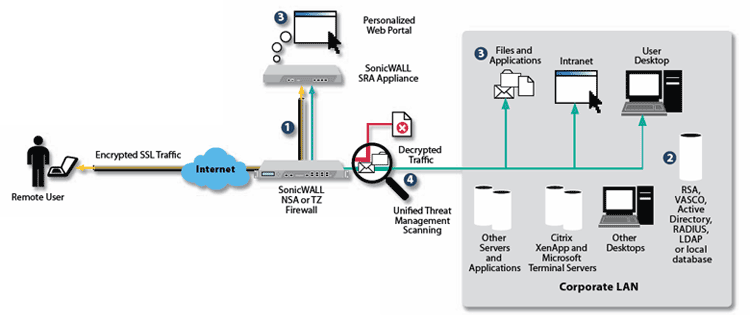
What is remote access server?
Remote access servers can be configured as dial-in servers or VPN servers. Dial-in servers use the Point-to-Point Protocol (PPP) or in the case of some older servers, the Serial Line Internet Protocol (SLIP) as the link layer protocol. VPN servers can use the Point-to-Point Tunneling Protocol (PPTP), Layer 2 Tunneling Protocol (L2TP), or IPSec tunnel mode to establish a secure "tunnel" over the Internet. Windows remote access servers support the following set of authentication methods: 1 Password Authentication Protocol (PAP) 2 Challenge Handshake Authentication Protocol (CHAP) 3 Microsoft's implementation of CHAP (MS-CHAP) 4 Updated version of MS-CHAP (MS-CHAP2) 5 Extensible Authentication Protocol/Transport Layer Security (EAP/TLS)
Why is PAP not supported?
For security purposes, PAP can be excluded as a viable option for most businesses because it sends passwords across the phone line or Internet in plain text. The only reason to use PAP is if the remote access client and remote access server are not able to negotiate a more secure authentication method. Many VPN/firewall products do not support PAP because of the security issue.
What is EAP TLS?
EAP/TLS provides for use of more secure authentication methods such as smart cards, Kerberos, and digital certificates, which are much more secure than the user name/password authentication methods above. It's defined in RFC 2716.
What is a radian?
RADIUS provides for a centralized authentication database and can handle authorization and accounting in addition to authentication. Authorization refers to granting specific services to users based on their authenticated identity; restrictions can be imposed on certain users. Accounting refers to tracking the use of the network by users and can be done for billing, management, or security purposes. RADIUS is defined in RFCs 2865 and 2866.
Why is it important to verify identity?
The ability to verify identity (authentication) is even more important for remote users than for those who are on-site, since without a secure authentication scheme anyone could get into the network and view, copy, change or even destroy important data. The choices you make have implications for ease of administration and security as your network ...
What does authenticator do?
The authenticator also calculates the hash value and compares the client's response with its own calculation. If the values match, the connection is established.
What is the protocol used for dial in VPN?
Dial-in servers use the Point-to-Point Protocol (PPP) or in the case of some older servers, the Serial Line Internet Protocol (SLIP) as the link layer protocol. VPN servers can use the Point-to-Point Tunneling Protocol (PPTP), Layer 2 Tunneling Protocol (L2TP), or IPSec tunnel mode to establish a secure "tunnel" over the Internet. ...
What port does XTACACS use?
This protocol is also an application layer protocol and observes the client/server model. Since TACACS+ is also a well known protocol, it stands to reason that there is also a well known port associated with this activity, which is TCP Port 49. That being said, XTACACS uses UDP. There is always the exception to the rule!
What is a tacs?
Terminal Access Controller Access Control System , or TACACS, is similar to RADIUS and is used to regulate access to the network. One of the biggest differences between TACACS and RADIUS is that TACACS primarily uses TCP for its transport protocol needs vs. the UDP that RADIUS will use. There are also three versions of TACACS with TACACS+ being the most recent. It is important to note that TACACS+ is not backwards compatible with the other earlier versions. This protocol is also an application layer protocol and observes the client/server model. Since TACACS+ is also a well known protocol, it stands to reason that there is also a well known port associated with this activity, which is TCP Port 49. That being said, XTACACS uses UDP. There is always the exception to the rule!
Why is telecommuting important?
One of the most desired advantages has been for some workers to have the ability to work from home. These telecommuters are one of the recent changes that have affected the workforce and much to the benefit of the worker. The ability to telecommute has greatly affected employee morale for the better. The problem is that these workers must also be able to communicate with the corporate network both remotely and securely. It is of little surprise that these concerns have been addressed in a variety of ways that all work quite well.
What is an access challenge?
Access-Challenge: where the server sends a challenge and the user must respond.
What port is used for a rudius?
Like many well-known protocols, RADIUS has some well-known ports that it is normally configured to be listening on. They are Port 1812 and Port 1813, which is used for RADIUS accounting.
What happens every time you involve another layer or program in your network?
The bottom line is that every time you involve another layer or program in your network, you are introducing another possible attack vector. You would be well advised to go with a mature technology for your remote authentication solution.
How does telecommuting affect morale?
The problem is that these workers must also be able to communicate with the corporate network both remotely and securely . It is of little surprise that these concerns have been addressed in a variety of ways that all work quite well.
What encryption does Kerberos use?
Kerberos uses DES encryption to authenticate a user when logging in to the system.
Which service can provide both authentication and authorization at the network level?
The LDAP directory service and the NIS+ name service can provide both authentication and authorization at the network level.
What is remote login?
The remote login commands enable users to log in to a remote machine over the network and use its resources. The remote login commands are rlogin, rcp, ftp. If you are a “trusted host,” authentication is automatic. Otherwise, you are asked to authenticate yourself.
How many bits does DES use?
The Data Encryption Standard (DES) encryption functions use a 56-bit key to encrypt a secret key.
Why is authentication important?
Imagine it as the first line of defence, allowing access to data only to users who are approved to get this information. In order to make this defence stronger, organisations add new layers to protect the information even more.
What is the most commonly used authentication method to validate identity?
The most commonly used authentication method to validate identity is still Biometric Authentication. Think of the Face ID technology in smartphones, or Touch ID. These are the most popular examples of biometrics.
What is Face Match?
Face Match is Veriff's authentication and reverification method that allows users to validate themselves using their biometric features. The technology confirms that a returning customer is who they claim to be using biometric analysis.
How does biometric authentication work?
Biometric authentication verifies an individual based on their unique biological characteristics. The system can help you verify people in a matter of seconds. It stores authentic data and then compares it with the user's physical traits. There are different forms of Biometric Authentication. Let's go through some of them:
What is the most effective authentication method?
Both of these components are crucial for every individual case. This is why we consider Biometric and Public-Key Cryptography (PKC) authentication methods as the most effective and secure from the given options. Both of them eliminate passwords and protect highly secure information. Usability is also a big component for these two methods - there is no need to create or remember a password.
What is the most popular form of biometric authentication?
Fingerprints are the most popular form of biometric authentication. The system to verify users with them mainly relies on mobile native sensing technology. Fingerprints are easy to capture, and the verification happens by comparing the unique biometric loop patterns.
How often does identity verification happen?
Most of the time, identity confirmation happens at least twice, or more. The most common methods are 3D secure, Card Verification Value, and Address Verification.
Why is IPSEC used?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
What are the implications of IPSec connections for corporations?
What are the implications of IPSec connections for corporations, considering the very nature of this connection? Well, your employee will only be able to access the network from a single, authorized device. Security is further boosted by the enforcement of antivirus and firewall policies.
What is IPSEC encryption?
IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect data flows between hosts and security gateways.
Why use two factor authentication for VPN?
Adopting two-factor authentication for remote access through VPN further boosts your network security. Now let’s take a look at why you should choose a particular VPN type as a secure connection methodology instead of the alternatives.
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
What is the first thing that’s required to ensure smooth remote access via a VPN?
The first thing that’s required to ensure smooth remote access via a VPN is to plan out a comprehensive network security policy.
What is client-side software?
The client-side software is responsible for establishing a tunneling connection to the RAS and for the encryption of data.
What happens if your password is compromised?
In the event your password is compromised, your account can remain secure as the cybercriminal is unable to authenticate the secondary requirement.
What is biometric authentication?
Common biometric authentication methods include fingerprint identification, voice recognition, retinal and iris scans, and face scanning and recognition.
What are the advantages and disadvantages of MFA?
Disadvantage: As with token authentication, a lost phone can quickly circumvent the security offered by MFA.
What is the advantage of MFA?
Advantage: MFA is common and low-cost to implement. As one of the most popular methods of authentication for anything from email accounts to online banking, MFA would be relatively easy to roll out with staff members.
What are the disadvantages of using tokens?
Disadvantage: Unfortunately, this authentication method can be easily undermined by the user. Put simply, a token is something you can lose. Whether it’s on a key ring or kept in a briefcase, even the most mindful of people can forget it in a car that’s then stolen, or have it fall out of their pocket at dinner.
What is a token for a hacker?
Common forms include a dongle, card, or RFID chip. A token makes it more difficult for a hacker to access an account since they must have long credentials and the tangible device itself, which is much harder for a hacker to obtain. Advantage: Similar to a biometric, a token is difficult to fake. The specific digital identity ...
Can hackers hack passwords?
It’s commonly accepted that conventional authentication protocols and password protection are too weak, with today’s hackers easily using sophisticated tools that can hack passwords and get into your system and the data stored on it.
What is SMS code?
SMS codes are in-band authentication, which offers less security than you might expect . If a user is buying something via a mobile app and the app provider sends an SMS code to that mobile device to verify the purchase, the SMS code is not actually providing any additional security—the code is being sent to the same device and is, therefore ‘in-band’. If the device has been compromised, the OTP is worthless. iProov face authentication is out of band: it assumes that the device has been compromised and so the authentication is processed securely and privately in the cloud. Even if a bad actor had full access to another’s device, the authentication process remains secure.
What is iproov verification?
Here at iProov, we provide biometric face verification to some of the world’s most secure organizations to enable them to authenticate online users.
Why is authentication important?
Ultimately, authentication is needed to restrict and allow access to personal information and accounts.
Why is SMS code so frustrating?
SMS codes can add complexity and additional steps to the authentication process. If customers are using a computer to complete a task online and are asked to find their mobile device to retrieve an SMS code, it can be frustrating and potentially cause the user to drop off and abandon the transaction.
What happens if your authentication process takes too long?
Completion rates: If your authentication process asks the user to follow too many instructions, or if it takes too long, or it needs repeated attempts before it succeeds, there’s a high risk of drop-offs and lost business. This impacts any organization, whether it’s a retailer dealing with abandoned baskets or citizens failing to return to access online government services.
What is face authentication?
Facial authentication uses a face scan done by a human on any device with a front-facing camera to prove they are who they say they are. For face authentication to be secure, it needs to verify that the user is the right person, a real person, and that they are authenticating right now. This is what iProov’s Genuine Presence Assurance technology delivers.
Why are passwords not secure?
In recent years organizations have started to move away from knowledge-based authentication. Passwords are not secure, because they can be shared, guessed or stolen. Passwords also cause user frustration, because they are easily forgotten. This ultimately leads to drop-off and poor completion rates.