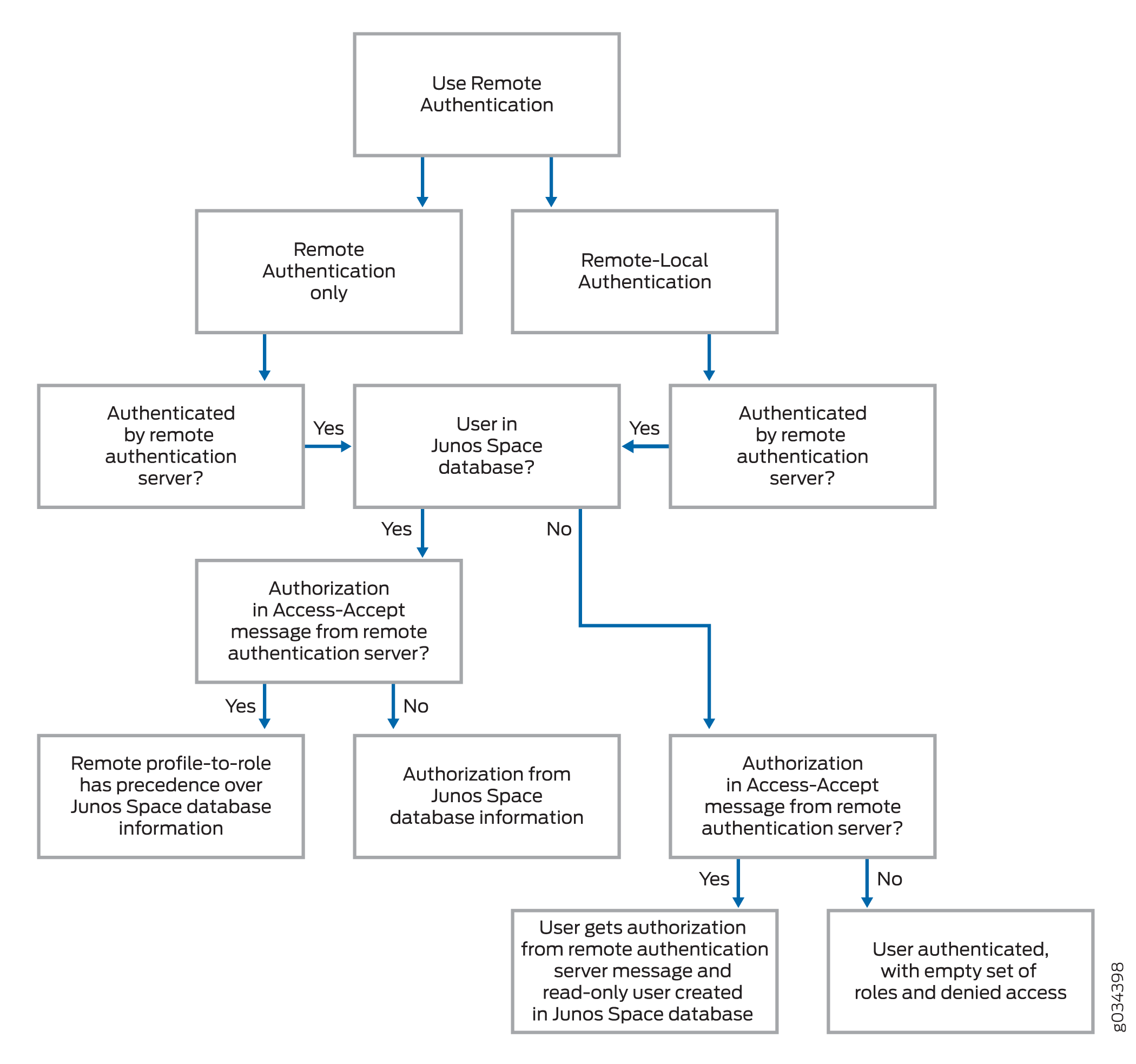
Windows remote access servers support the following set of authentication methods:
- Password Authentication Protocol (PAP)
- Challenge Handshake Authentication Protocol (CHAP)
- Microsoft's implementation of CHAP (MS-CHAP)
- Updated version of MS-CHAP (MS-CHAP2)
- Extensible Authentication Protocol/Transport Layer Security (EAP/TLS)
Full Answer
What is used by remote access protocols for authentication?
Authentication is the process of proving identity. Common protocols used for remote access authentication include PAP, CHAP, MS-CHAP, or EAP. Usernames and passwords are used during identification and authentication as authentication credentials. SLIP and PPP are remote access connection protocols that are used to establish and negotiate ...
How to setup remote access?
Once installed, you can now connect to remote endpoints by following the steps below:
- The software needs to be downloaded on both the local and remote computers.
- Open the software on both the local and remote computers.
- Write down the ITarian ID number and password of the remote computer.
- Click “Start Connection.”
- Enter the ID number and password of the remote computer.
- Click “Connect.”
How to protect remote access?
To enable Remote Access in your UniFi Protect application:
- Access the UniFi OS Console hosting Protect via its IP address. ...
- Log in to your Ubiquiti SSO account.
- Go to the System Settings > Advanced menu, and enable the Remote Access toggle.
How to authenticate remote users?
Using a personal authentication token or password Using an SSH key Using your GitHub password with 2-factor authentication; With either of the first two approaches you can avoid entering a username and password each time you interact with the remote repository, as discussed below.

What is the best remote access authentication?
Extensible Authentication Protocol-Transport Level Security is the most secure remote authentication protocol. It uses certificates on both the client and the server to provide mutual authentication, data integrity, and data confidentiality.
What is remote network authentication?
Authentication is a way to restrict access to specific users when these users access a remote machine. Authentication can be set up at both the machine level and the network level.
Which 2 methods of authentication can be used for remote access connections?
remote access servers support the following set of authentication methods:Password. Authentication Protocol (PAP)Challenge. Handshake Authentication Protocol (CHAP)Microsoft's. implementation of CHAP (MS-CHAP)Updated. version of MS-CHAP (MS-CHAP2)Extensible. Authentication Protocol/Transport Layer Security (EAP/TLS)
What are the 3 types authentication methods?
5 Common Authentication TypesMulti-factor authentication.Certificate-based authentication.Biometric authentication.
What is remote access examples?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
Why is remote authentication important?
MFA is important for remote workers for not only preventing unauthorized access, but in improving your organization's overall security posture. This is thanks to one of the great features of MFA: when an attempt is made to get into someone's account from an unauthorized device, the user will get a notification.
What are the 4 general forms of authentication?
Four-factor authentication (4FA) is the use of four types of identity-confirming credentials, typically categorized as knowledge, possession, inherence and location factors.
How many types of authentication are there?
There are three basic types of authentication. The first is knowledge-based — something like a password or PIN code that only the identified user would know. The second is property-based, meaning the user possesses an access card, key, key fob or authorized device unique to them. The third is biologically based.
What are different authentication methods?
Common types of biometrics include the following: Fingerprint scanning verifies authentication based on a user's fingerprints. Facial recognition uses the person's facial characteristics for verification. Iris recognition scans the user's eye with infrared to compare patterns against a saved profile.
What are the 5 factors of authentication?
The five main authentication factor categories are knowledge factors, possession factors, inherence factors, location factors, and behavior factors.
What is the most common type of authentication system that we used today?
Single-Factor/Primary Authentication Historically the most common form of authentication, Single-Factor Authentication, is also the least secure, as it only requires one factor to gain full system access. It could be a username and password, pin-number or another simple code.
What are the 3 factors of authentication?
Three-factor authentication (3FA) is the use of identity-confirming credentials from three separate categories of authentication factors – typically, the knowledge, possession and inherence categories. Multifactor authentication dramatically improves security.
Should I enable NLA?
Network Level Authentication is critical for secure RDP connections. Don't turn it off. No! Network Level Authentication is how Windows authenticates remote desktop clients and servers before sending your credentials over to a remote machine.
How does RDP NLA work?
When Duo Authentication for Windows Logon (RDP) is installed on a system where NLA is enabled, the RDP client prompts for the Windows username and password in a local system dialog. That information is used to connect to the remote system and passed through to the Remote Desktop manager.
Why is NLA important?
The advantages of Network Level Authentication are: It requires fewer remote computer resources initially, by preventing the initiation of a full remote desktop connection until the user is authenticated, reducing the risk of denial-of-service attacks.
How do I connect to Remote Desktop with Network Level Authentication?
Settings app > System > Remote Desktop > toggle Enable Remote Desktop ON > click Confirm at the window that appears > Advanced Settings > select Require computers to use Network Level Authentication to connect (recommended)
How to Enable Remote Desktop
The simplest way to allow access to your PC from a remote device is using the Remote Desktop options under Settings. Since this functionality was a...
Should I Enable Remote Desktop?
If you only want to access your PC when you are physically sitting in front of it, you don't need to enable Remote Desktop. Enabling Remote Desktop...
Why Allow Connections only With Network Level Authentication?
If you want to restrict who can access your PC, choose to allow access only with Network Level Authentication (NLA). When you enable this option, u...
Which service can provide both authentication and authorization at the network level?
The LDAP directory service and the NIS+ name service can provide both authentication and authorization at the network level.
What is remote login?
The remote login commands enable users to log in to a remote machine over the network and use its resources. The remote login commands are rlogin, rcp, ftp. If you are a “trusted host,” authentication is automatic. Otherwise, you are asked to authenticate yourself.
What encryption does Kerberos use?
Kerberos uses DES encryption to authenticate a user when logging in to the system.
How to allow remote access to PC?
The simplest way to allow access to your PC from a remote device is using the Remote Desktop options under Settings. Since this functionality was added in the Windows 10 Fall Creators update (1709), a separate downloadable app is also available that provides similar functionality for earlier versions of Windows. You can also use the legacy way of enabling Remote Desktop, however this method provides less functionality and validation.
How to connect to a remote computer?
To connect to a remote PC, that computer must be turned on, it must have a network connection, Remote Desktop must be enabled, you must have network access to the remote computer (this could be through the Internet), and you must have permission to connect. For permission to connect, you must be on the list of users. Before you start a connection, it's a good idea to look up the name of the computer you're connecting to and to make sure Remote Desktop connections are allowed through its firewall.
How to remotely connect to Windows 10?
Windows 10 Fall Creator Update (1709) or later 1 On the device you want to connect to, select Start and then click the Settings icon on the left. 2 Select the System group followed by the Remote Desktop item. 3 Use the slider to enable Remote Desktop. 4 It is also recommended to keep the PC awake and discoverable to facilitate connections. Click Show settings to enable. 5 As needed, add users who can connect remotely by clicking Select users that can remotely access this PC .#N#Members of the Administrators group automatically have access. 6 Make note of the name of this PC under How to connect to this PC. You'll need this to configure the clients.
Should I enable Remote Desktop?
If you only want to access your PC when you are physically using it, you don't need to enable Remote Desktop. Enabling Remote Desktop opens a port on your PC that is visible to your local network. You should only enable Remote Desktop in trusted networks, such as your home. You also don't want to enable Remote Desktop on any PC where access is tightly controlled.
What is an access challenge?
Access-Challenge: where the server sends a challenge and the user must respond.
What port does XTACACS use?
This protocol is also an application layer protocol and observes the client/server model. Since TACACS+ is also a well known protocol, it stands to reason that there is also a well known port associated with this activity, which is TCP Port 49. That being said, XTACACS uses UDP. There is always the exception to the rule!
What is a tacs?
Terminal Access Controller Access Control System , or TACACS, is similar to RADIUS and is used to regulate access to the network. One of the biggest differences between TACACS and RADIUS is that TACACS primarily uses TCP for its transport protocol needs vs. the UDP that RADIUS will use. There are also three versions of TACACS with TACACS+ being the most recent. It is important to note that TACACS+ is not backwards compatible with the other earlier versions. This protocol is also an application layer protocol and observes the client/server model. Since TACACS+ is also a well known protocol, it stands to reason that there is also a well known port associated with this activity, which is TCP Port 49. That being said, XTACACS uses UDP. There is always the exception to the rule!
Can you use PPP on a Radius router?
Notably, you can use PPP, PAP, and CHAP to name most of them. If you are familiar with Cisco Systems gear or are in charge of supporting the routers and switches from them, then you are no doubt familiar with the various authentication methods offered by RADIUS.
What are Authentication Systems?
Authentication systems are security measures put in place to secure data and systems by requiring additional input beyond username and password for users to access a system. By providing this additional input, authentication systems help ensure that users are who they say they are. Authentication systems can require one other form of user input or more. These systems are sometimes called multiple-factor authentication, or MFA.
What is Auth0 authentication?
Auth0 is an identity management platform for developers and application teams. It gives users a platform to authenticate and authorize, providing secure access to applications, devices, and users. Auth0 aims to provide the simplicity, extensibility, and expertise to scale and protect…. Hide Details.
What are the different types of authentication?
Most modern authentication systems offer a wider range of authentication methods than passwords alone. The most common approach for advanced authentication, such as two-factor authentication or multi-factor authentication, is to pair a password with some sort of external verification. Other common authentication methods include: 1 Challenge questions 2 Unique identifying items, such as physical devices or external applications 3 Biometric identifies, such as retina and fingerprint scans or facial recognition 4 Location-based authentication
Why is multifactor authentication important?
These systems are sometimes called multiple-factor authentication, or MFA. Using authentication improves data security and prevents potential breaches. When multi-factor authentication is required to access a system, the system is less vulnerable to security issues like weak passwords or attacks like phishing.
How many authentication checks does two factor authentication use?
Two-factor authentication only uses 2 authentication checks, usually a password and another method. MFA uses 2 or more authentication methods, with each additional method designed to increase security.
What is the most common method of authentication?
The most common approach for advanced authentication, such as two-factor authentication or multi-factor authentication, is to pair a password with some sort of external verification . Other common authentication methods include:
What is Watchguard AuthPoint?
WatchGuard AuthPoint is a multi-factor authentication (MFA) service that helps companies keep their assets, information, and user identities secure. Multi-factor authentication solutions can enable organizations to close security gaps that leave companies vulnerable to breaches by…
What is 2FA authentication?
Today there are a series of tasks, such as the update of software, maintenance work or changes to configuration, which are carried out periodically and are necessary for the system to function correctly. On occasions it is possible for these tasks to be carried out remotely and by individuals external to the organisation (e.g. manufacturers or engineers). This access may be performed in a non-secure way or from an environment that may have been compromised and it is particularly in these cases where it is recommended to implement two-factor authentication (2FA).
What are tokens based on?
Token Based on Software or Hardware 1 Google Authenticator :is a mobile application based on two-factor authentication which uses the Time-based One-Time Password algorithm (TOTP) and the HMAC-based One-time Password algorithm (HOTP) to authenticate the users. There is a PAM module for installation on Linux systems and authentication against RADIUS systems. 2 Authy: Open Source multi-platform application: iPhone, Android, or desktop and offers three authentication combinations: Authy SoftToken, Authy OneCode and Authy OneTouch. 3 Yubiko: solution based on hardware called YubiKey. It is a small hardware device that activates two-factor authentication with the simple touch of a button. 4 DUO: allows users to protect their logins and transactions through smartphones and the application can be used offline. It is compatible with Linux and Windows systems. For example, in Windows it would be possible for RDP connections.
What is a remote authentication dial in user service?
The remote authentication dial in user service (RADIUS) protocol is a third-party authentication system. RADIUS is described in RFCs 2865 and 2866, and it uses the UDP ports 1812 (authentication) and 1813 (accounting). RADIUS formerly used the unofficially assigned ports of 1645 and 1646 for the same respective purposes, and some implementations continue to use those ports.
How does trust pass authentication requests?
How a specific trust passes authentication requests depends on how it is configured; trust relationships can be one way, providing access from the trusted domain to resources in the trusting domain, or two way, providing access from each domain to resources in the other domain . Trusts are also either nontransitive, in which case trust exists only between the two trust partner domains, or transitive, in which case trust automatically extends to any other domains that either of the partners trusts.
What is the purpose of the Radius system?
RADIUS is considered an “AAA” system, comprised of three components: authentication, authorization, and accounting. It authenticates a subject's credentials against an authentication database. It authorizes users by allowing specific users' access to specific data objects.
What is authentication in NAS?
Authentication The server seeking access sends a request to NAS. The NAS then creates and sends a RADIUS Access Request to the RADIUS Server. This request acts as an authorization to grant access. Typically, a user name and password or some other means of establishing identity is requested for this process, which must then be provided by the user seeking access. The request will also contain other means of verification that the NAS collected, such as physical location of the user and/or the phone number or network address of the user.
What is domain in Active Directory?
Microsoft Windows Active Directory uses the concept of domains as the primary means to control access. For authentication purposes, Microsoft bases their authentication of trust relationships on RFC 1510, the Kerberos Authentication Protocol, and it has been integrated into Microsoft Windows operating systems since Windows 2000. Each domain has a separate authentication process and space. Each domain may contain different users and different network assets and data objects. Because Microsoft Windows also uses the concept of groups to control access by users to data objects, each group may be granted access to various domains within the system. If a two-way trust between domains is created, then groups belonging to either domain may access data objects from each domain.
What is a PAP server?
The Password Authentication Protocol (PAP) is defined by RFC 1334 ( http://tools.ietf.org/html/rfc1334#section-2) and is referred to as being, “not a strong authentication method.” [17] A user enters a password and it is sent across the network in clear text. When received by the PAP server, it is authenticated and validated. Sniffing the network may disclose the plaintext passwords. Sniffing refers to monitoring network communications and capturing the raw TCP/IP traffic.
What is PAP authentication?
The Password Authentication Protocol (PAP) is defined by RFC 1334 and is referred to as being, “not a strong authentication method.” [ 7] A user enters a password, and it is sent across the network in clear text. When received by the PAP server, it is authenticated and validated. Sniffing the network may disclose the plaintext passwords. Sniffing refers to monitoring network communications and capturing the raw TCP/IP traffic. Two tools, Snort ( http://www.snort.org) and Cain & Abel ( http://www.oxid.it/cain ), are particularly good at sniffing networks.
What is DirectAccess client?
The DirectAccess client computer forwards the signed certificate request to the CA and stores the enrolled certificate for use by the Kerberos SSP/AP.
When configuring OTP in a Remote Access multi-forest environment, should OTP CAs be from the?
When configuring OTP in a Remote Access multi-forest environment, OTP CAs should be from the resource forest only , and certificate enrollment should be configured across forest trusts. For more information, see AD CS: Cross-forest Certificate Enrollment with Windows Server 2008 R2.
What is an OTP server?
An OTP server that supports PAP over RADIUS.
How to use a key fob OTP?
Users who are using a KEY FOB OTP token should insert the PIN followed by the tokencode (without any separators) in the DirectAccess OTP dialog. Users who are using PIN PAD OTP token should insert only the tokencode in the dialog.
What is a RRAS?
1. DirectAccess and Routing and Remote Access Services (RRAS) VPN-DirectAccess and VPN are managed together in the Remote Access Management console. 2. RRAS Routing-RRAS routing features are managed in the legacy Routing and Remote Access console. The Remote Access role is dependent on the following server features:
What is OTP in remote access?
In a Remote Access multisite deployment, OTP settings are global and identify for all entry points. If multiple RADIUS or CA servers are configured for OTP, they are sorted by each Remote Access server according to availability and proximity.
What is the NCA service?
Client-side requirements-For Windows 10 and Windows 8 client computers, the Network Connectivity Assistant (NCA) service is used to detect whether OTP credentials are required. If they are, the DirectAccess Media Manager prompts for credentials. NCA is included in the operating system, and no installation or deployment is required. For Windows 7 client computers, DirectAccess Connectivity Assistant (DCA) 2.0 is required. This is available as a download on the Microsoft Download Center.
