In the Remote Access MMC, right-click the VPN
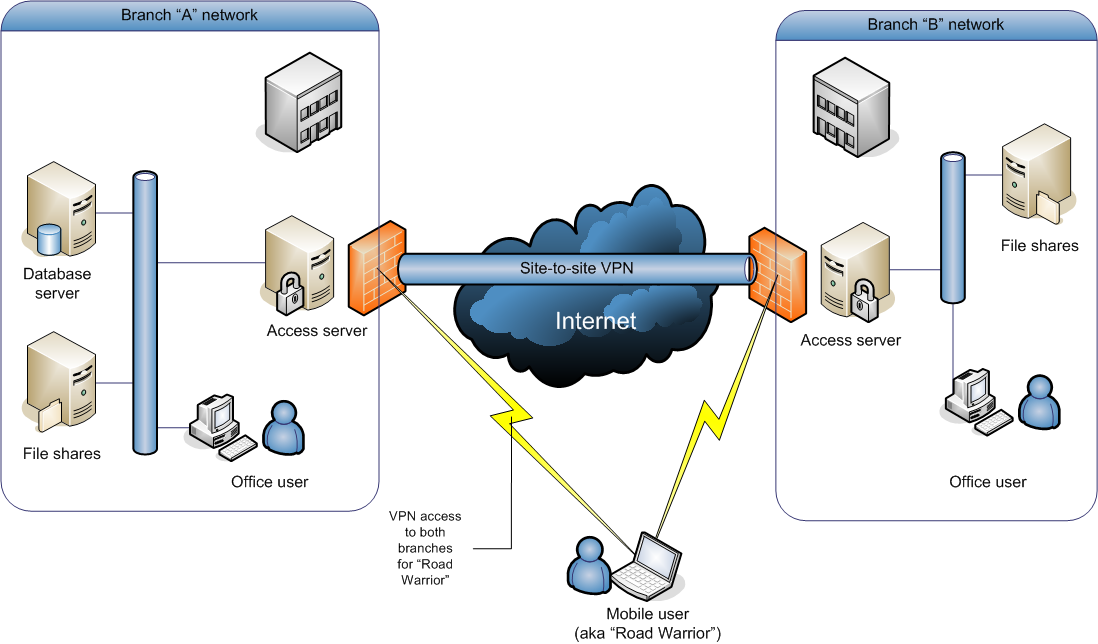
Virtual private network
A virtual private network extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running on a computing device, e.g. …
How to secure your VPNs?
The best solution for securing VPNs, especially in a work-from-anywhere environment, is through multi-factor authentication using biometrics. Biometric authentication is the only true method of multi-factor authentication that goes beyond a device or certificate to identify the individual who is requesting access.
Is it safe to use IPSec VPN for remote access?
A word of warning: If you are using IPSec VPN for remote access, but you are not deploying Internet Key Exchange (IKE, certificates) as an authentication method, the connection will be vulnerable. For many use cases, XAUTH and L2TP methods of IPSec authentication are prone to security lapses.
What are the built-in VPN authentication options?
VPN authentication options. In addition to older and less-secure password-based authentication methods (which should be avoided), the built-in VPN solution uses Extensible Authentication Protocol (EAP) to provide secure authentication using both user name and password, and certificate-based methods.
What are the best practices for securing remote access?
Best Practices for Securing Remote Access. RAS: The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network ... IPSec: IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect ...
Can I use a VPN for remote access?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
Is VPN an authentication method?
In addition to older and less-secure password-based authentication methods (which should be avoided), the built-in VPN solution uses Extensible Authentication Protocol (EAP) to provide secure authentication using both user name and password, and certificate-based methods.
Which 2 methods of authentication can be used for remote access connections?
remote access servers support the following set of authentication methods:Password. Authentication Protocol (PAP)Challenge. Handshake Authentication Protocol (CHAP)Microsoft's. implementation of CHAP (MS-CHAP)Updated. version of MS-CHAP (MS-CHAP2)Extensible. Authentication Protocol/Transport Layer Security (EAP/TLS)
How do I get VPN authentication?
To connect to your VPN, go back to Settings > Network & Internet > VPN. Click on your VPN name. If you want, at this point you can select Advanced Options to edit the connection properties, clear your sign-in info, or set up a VPN proxy. Select Connect and enter a password if you've set one.
What is a VPN authentication?
A virtual private network (VPN) gives you online privacy and anonymity to secure user authentication by creating a private network from a public internet connection. VPNs mask your IP (Internet Protocol) address and establish a secure and encrypted connection to provide greater privacy than even a secure Wi-Fi spot.
Which 3 types of authentication can be used for IPsec site to site VPNs?
Authentication in IPsec VPNsSupported authentication methods for IPsec VPNs. Authentication verifies that the remote party is who they claim they are.Using pre-shared key (PSK) authentication. A pre-shared key is a string of characters that is used as an authentication key. ... Using certificate-based authentication.
What are the 3 types of authentication?
The three authentication factors are: Knowledge Factor – something you know, e.g., password. Possession Factor – something you have, e.g., mobile phone. Inherence Factor – something you are, e.g., fingerprint.
What is the best remote access authentication?
Extensible Authentication Protocol-Transport Level Security is the most secure remote authentication protocol. It uses certificates on both the client and the server to provide mutual authentication, data integrity, and data confidentiality.
What is the most secure authentication method?
Experts believe that U2F/WebAuthn Security Keys are the most secure method of authentication. Security keys that support biometrics combine the Possession Factor (what you have) with the Inherence Factor (who you are) to create a very secure method of verifying user identities.
How do I setup my own VPN?
To setup your home router as a VPN server:Open up your preferred browser.Enter your router's LAN (internal) IP address into the search bar. ... Enter the router's username and password. ... Go into Settings (or Advanced Settings) > VPN Service.Enable the VPN Service.More items...•
Is VPN considered Two-Factor Authentication?
1. VPN Two-Factor Authentication Protects Against Phishing Attacks. Among the main reasons you should ensure additional VPN security is the trend of phishing attacks, which are successfully performed by criminals in up to 17% of cases, according to the Duo report.
Why is my VPN authentication failed?
A corrupt installation of your VPN can cause the “VPN Authentication Failed” error. If you suspect this may be the problem, try uninstalling and reinstalling your VPN client. Avoid running into other errors by using an uninstaller software to remove all registry entries and files from the first installation.
Why is my VPN authentication failed?
A corrupt installation of your VPN can cause the “VPN Authentication Failed” error. If you suspect this may be the problem, try uninstalling and reinstalling your VPN client. Avoid running into other errors by using an uninstaller software to remove all registry entries and files from the first installation.
What is authentication information for VPN on Mac?
When trying to connect to your VPN provider's servers on Mac, you may see a prompt, asking you to enter your authentication information. This authentication information for the VPN connection implies your Mac password. If you click Cancel, the window just pops up again directly.
When you connect to Azure by using a VPN which connection method would you use?
Azure supports three types of Point-to-site VPN options:Secure Socket Tunneling Protocol (SSTP). SSTP is a Microsoft proprietary SSL-based solution that can penetrate firewalls since most firewalls open the outbound TCP port that 443 SSL uses.OpenVPN. ... IKEv2 VPN.
What is IP security in network security?
What is IPsec? IPsec (Internet Protocol Security) is a suite of protocols that secure network communication across IP networks. It provides security services for IP network traffic such as encrypting sensitive data, authentication, protection against replay and data confidentiality.
Why is VPN authentication important?
While increasing security for remote VPN authentication access is a critical priority, especially during a time when cyberattacks are specifically targeting remote workers, just as important is making sure it remains convenient for your users.
What is a VPN 2021?
March 15, 2021 by BIO-key Team 0 Comments. A virtual private network (VPN) gives you online privacy and anonymity to secure user authentication by creating a private network from a public internet connection. VPNs mask your IP (Internet Protocol) address and establish a secure and encrypted connection to provide greater privacy ...
What is biometric authentication?
Biometric authentication is the only true method of multi-factor authentication that goes beyond a device or certificate to identify the individual who is requesting access. Instead of knowing that the user’s phone is present at the time the access request is made for example, you can be sure that the user themselves are present.
Is biometric authentication secure?
Biometric authentication is quickly taking over as the fastest, most secure and convenient method of authentication and is ideal for remote access, when users are not visible to the organization, and home networks leave much to be desired when it comes to security best practices .
Is a VPN a single factor?
Single factor ( password only) is not enough to prevent unauthorized access to your VPN. The best solution for securing VPNs, especially in ...
Can I use a hardware token for VPN?
In contrast, if the IT admin has configured the security policy to allow the user to use a hardware token or biometric authentication, if the hardware token is missing the user can easily switch to using the biometric authentication option and gain access to the VPN. Flexibility and options are essential when implementing multi-factor authentication for VPN access successfully.
What does portal authentication mean?
For portal authentication, this means that certificates must be pre-deployed on the endpoints before their initial portal connection. Additionally, the client certificate presented by a user must match what is defined in the certificate profile. If the certificate profile does not specify a username field (.
What is a server profile?
The server profile instructs the firewall on how to connect to the authentication service. Local, RADIUS, Kerberos, SAML, and LDAP authentication methods are supported. This example shows an LDAP authentication profile for authenticating users against the Active Directory.
How to manage a certificate?
Select#N#Device#N#Certificate Management#N#Certificates#N#to manage certificates as follows: 1 Obtain a server certificate. Because the portal and gateway are on the same interface, the same server certificate can be used for both components. 2 The CN of the certificate must match the FQDN,#N#gp.acme.com#N#. 3 To enable users to connect to the portal without receiving certificate errors, use a server certificate from a public CA.
Can you use GlobalProtect with two factor authentication?
If you configure a GlobalProtect portal or gateway with an authentication profile and a certificate profile (which together can provide two-factor authentication), the end user must authentication through both profiles successfully before gaining access. For portal authentication, this means that certificates must be pre-deployed on ...
Does a client certificate require a username?
None. ), the client certificate does not require a username. In this case, the user must provide the username when authenticating against the authentication profile. If the certificate profile specifies a username field, the certificate that the user presents must contain a username in the corresponding field.
Can you configure app settings from the portal?
As an alternative to deploying app settings from the portal configuration, you can define settings directly from the Windows registry or global macOS plist. Examples of settings that you can deploy include specifying the portal IP address or enabling GlobalProtect to initiate a VPN tunnel before a user logs in to the endpoint and connects to the GlobalProtect portal. On Windows endpoints only, you can also configure settings using the MSIEXEC installer. For additional information, see Customizable App Settings.
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
What is the first thing that’s required to ensure smooth remote access via a VPN?
The first thing that’s required to ensure smooth remote access via a VPN is to plan out a comprehensive network security policy.
Why is IPSEC used?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
What are the implications of IPSec connections for corporations?
What are the implications of IPSec connections for corporations, considering the very nature of this connection? Well, your employee will only be able to access the network from a single, authorized device. Security is further boosted by the enforcement of antivirus and firewall policies.
What is IPSEC encryption?
IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect data flows between hosts and security gateways.
Why use two factor authentication for VPN?
Adopting two-factor authentication for remote access through VPN further boosts your network security. Now let’s take a look at why you should choose a particular VPN type as a secure connection methodology instead of the alternatives.
What is the line of defense for remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly.