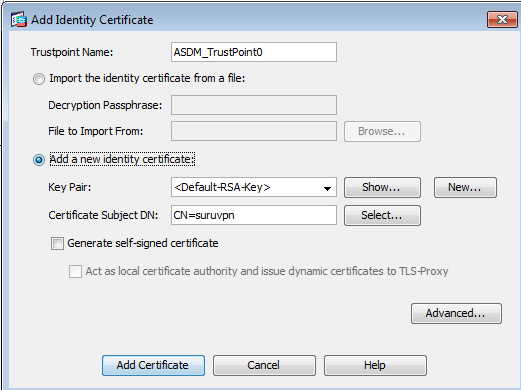
Eight easy steps to Cisco ASA remote access setup
- Step 1. Configure an Identity Certificate. Here I am creating a general purpose, self-signed, identity certificate named...
- Step 2. Upload the SSL VPN Client Image to the ASA. You can obtain the client image at Cisco.com. As you choose which...
- Step 3. Enable AnyConnect VPN Access.
- Step 4. Create a Group Policy. Group Po...
Full Answer
How do you enable remote access?
Steps to enable allow remote connection in Windows 10:
- Open System using Windows+Pause Break.
- Choose Remote settings in the System window.
- Select Allow remote connections to this computer and tap OK in the System Properties dialog.
How to secure your remote access?
- In-session file transfer
- Out-of-session file transfer
- Remote print
- Text copy/paste
- Remote wake
- Remote Reboot
- Out-of-session chat
- Session recording
- Concurrent remote sessions
- Remote command
How do you program a Cisco remote?
Cisco Remote Programming
- Turn on the TV
- On the Remote, press and hold the TV button
- On the Remote, press and hold the OK button
- Release both keys at the same time a. ...
- Press the Numbers 922 on the Number Pad a. ...
- Point the remote at your TV and slowly press and release the Play button arrow button (just to the right of the yellow Pause button)
Can someone help me with remote access?
Windows Remote Assistance lets someone you trust take over your PC and fix a problem from wherever they are. Before you can use it, you'll need to enable access. In the search box on the taskbar, type remote assistance, and then select Allow Remote Assistance invitations to be sent from this computer from the list of results.
How do I configure my router for remote access?
All you need to do is type the router IP or default gateway address in the web browser. Next, enter your username and password. Now, once you are in the router's web portal, look for the Remote Management option. Some routers called it Remote Access and it's usually found under Advanced Settings.
How do I connect my Cisco Remote?
Cisco Remote ProgrammingLocate the Manufacturer and codes from the list provided.Turn on the TV.On the Remote, press and hold the TV button.On the Remote, press and hold the OK button.Release both keys at the same time. ... Enter a four digit number matching the TV Manufacturer from the list provided. ... Test remote functions.More items...•
Is Vty Telnet or SSH?
An efficient way to manage remote devices is to use VTY access, which is CLI-based remote access using Telnet or SSH. Telnet uses TCP port number 23. Telnet is a simple protocol and does not encrypt communications.
What do you need to configure on a switch to allow remote management?
To prepare a switch for remote management access, the switch must be configured with an IP address and a subnet mask. Keep in mind that to manage the switch from a remote network, the switch must be configured with a default gateway. This is very similar to configuring the IP address information on host devices.
How do I remotely control a Cisco switch?
0:4012:19Cisco router and switch configure remote access (telnet/ssh) - YouTubeYouTubeStart of suggested clipEnd of suggested clipSo you type telnet in the IP address and then you put in the password of Cisco. And hey check it outMoreSo you type telnet in the IP address and then you put in the password of Cisco. And hey check it out I'm on the router. Before you can do anything useful though you need to type enable.
How do you program DTA C?
0:552:40Programming Your DTA Remote Control - YouTubeYouTubeStart of suggested clipEnd of suggested clipTurn on your TV by pressing the power button on the TV. Itself. Now on the remote hold down the muteMoreTurn on your TV by pressing the power button on the TV. Itself. Now on the remote hold down the mute. And ok buttons at the same time until the LED on the remote stays illuminated.
What Vty means?
Virtual TeletypeWhat Does Virtual Teletype (VTY) Mean? Virtual teletype (VTY) is a command line interface (CLI) created in a router and used to facilitate a connection to the daemon via Telnet, a network protocol used in local area networks. To connect to a VTY, users must present a valid password.
What is Vty password?
The term “vty” stands for Virtual teletype. VTY is a virtual port and used to get Telnet or SSH access to the device. VTY is solely used for inbound connections to the device. These connections are all virtual with no hardware associated with them. Related Blog – VTY Password.
How many Vty lines are on a router?
five VTY portsVTY ports are virtual TTY ports, used to Telnet or SSH into the router over the network. You can use them to connect to the router to make configuration changes or check the status. Most routers have five VTY ports, numbered 0 to 4.
Which protocol should be used to manage a switch remotely?
Secure Shell (SSH) is a protocol that provides a secure (encrypted) management connection to a remote device.
What is login local Vty?
login is used on vty and console and means that the password that is user for its authentication, is configured under vty and console as well. Login local, means that authentication uses locally configured credentials using the. username
What is basic switch configuration?
Basic switch configuration can be thought of as the minimum network, port, and security provisioning required for the production deployment of a switch. In practice, your exact needs will vary from environment to environment. And overall, effective switch management is a detailed topic in its own right.
What is the meaning of line Vty 0 15?
Lines 0 15 is vty lines 0, 1, 2 ,3 ,4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14 and 15. for example if you were type in global configuration mode, line vty 0 15 you will enter configuration for lines 0-15.
What is login local Vty?
login is used on vty and console and means that the password that is user for its authentication, is configured under vty and console as well. Login local, means that authentication uses locally configured credentials using the. username
What is the difference between line Vty 0 4 and line Vty 5 15?
VTY lines are usually used for creating out-of-band management sessions to devices. If a password is not supplied on a vty line, that line cannot be used for managing the device. In some cases administrators may decide to let junior staff to use lines 0 - 4 and senior staff to use lines 5 - 15.
What is Vty ACL?
Remote access via virtual terminal or virtual tty (vty) lines can also be secured by configuring inbound and outbound Access Control Lists (ACLs). Inbound ACLs enable inbound connections to a Cisco device, router or switch, from a restricted list of IP addresses.
What is VPN on Cisco router?
This chapter explains the basic tasks for configuring an IP-based, remote access Virtual Private Network (VPN) on a Cisco 7200 series router. In the remote access VPN business scenario, a remote user running VPN client software on a PC establishes a connection to the headquarters Cisco 7200 series router.
How to verify that authentication proxy is successfully configured on the router?
To verify that the authentication proxy is successfully configured on the router, ask a user to initiate an HTTP connection through the router. The user must have authentication and authorization configured at the AAA server. If the user authentication is successful, the firewall completes the HTTP connection for the user. If the authentication is unsuccessful, check the access list and the AAA server configurations.
What command to use to verify PPTP?
After you complete a connection, enter the show vpdn tunnel command or the show vpdn session command to verify your PPTP and MPPE configuration.The following example contains typical output:
What is Cisco IOS firewall proxy?
Using the Cisco IOS firewall authentication proxy feature , network administrators can apply specific security policies on a per-user basis. Users can be identified and authorized on the basis of their per-user policy, and access privileges tailored on an individual basis are possible, in contrast with general policy applied across multiple users.
What is the radiusserverkey command?
Sets the authentication and encryption key for communications between the router and the AAA server. For RADIUS servers use the radiusserverkey command.
What is authentication proxy?
With the authentication proxy feature, users can log into the network or access the Internet via HTTP, and their specific access profiles are automatically retrieved and applied from an authentication server. The user profiles are active only when there is active traffic from the authenticated users.
How to display user authentication entries?
Display the user authentication entries using the show ip auth-proxy cache command in privileged EXEC mode. The authentication proxy cache lists the host IP address, the source port number, the timeout value for the authentication proxy, and the state of the connection. If the authentication proxy state is HTTP_ESTAB, the user authentication was successful.
What is Cisco Secure Endpoint?
Cisco Secure Endpoint New packages fit for every organization Every Cisco Secure Endpoint (formerly AMP for Endpoints) package comes with Cisco SecureX built-in. It’s our cloud-native platform that integrates all your security solutions into one view wit... view more
Do you need to set IP domain name for generating key?
Apart from those commands as sandeep stated here... you need to set ip domain-name as well for generating the key. Because you key will get generated based on your hostname... i.e. .
Is Cisco 1841 compatible with Cisco 1841?
Those advanced IP Services are compatible with cisco 1841 routers..... current IOS is in specific to broadband which has some limited facilities..... for eg advip ios has much more features of IP SLA but broadband IOS has only IP SLA Responder feature.... Like this way you have many other differences mate....
Is Cisco Secure a partner of IBM?
This month, we're excited to bring awareness to a newly formed partnership between Cisco Secure and IBM. Securing today's dynamic enterprise applications is critical. With hybrid and multi-cloud adoption, traditional network-based security ran into limita... view more
Does Cisco IOS support SSH?
You will need an image that supports SSH (images with k9) Yes. Starting with Cisco IOS Software Release 12.4 (1), SSH is supported in all images with the following exceptions: IP Base without Crypto and Enterprise Base without Crypto. Use this command: Router (config)# crypto key generate rsa.
What is off-premises access?
Off-premises access: a consistent experience outside the network for Jabber and EX/MX/SX Series clients
What is MRA access policy?
For Cisco Jabber users, the MRA access policy that you configured must be associated to your Cisco Jabber users during the LDAP sync. For information on how to provision end users, see the End User Configuration .
Does Cisco Expressway use Unified Communications Manager?
This feature requires you to integrate Unified Communications Manager with Cisco Expressway. For Cisco Expressway configuration details for Mobile and Remote Access, refer to the Mobile and Remote Access Through Cisco Expressway Deployment Guide .
Do you need to exchange certificates between Cisco Expressway and Unified Communications Manager?
Cisco recommends that you use CA-signed certificates with the same CA for each system. In this case:
Do you need NTP for mobile access?
Mobile and Remote Access requires that you set up NTP servers for your deployment. Make sure that you have NTP servers deployed for your network and Phone NTP References for SIPendpoints.
Does Expressway C use forward and reverse DNS?
You must create internal DNS records, for both forward and reverse lookups, for all Unified Communications nodes used with Mobile and Remote Access. This allows Expressway-C to find the nodes when IP addresses or hostnames are used instead of FQDNs. Make sure that the SRV record is not resolvable outside of the local network.
Does Cisco Expressway require mobile access?
In addition, you must configure Cisco Expressway with Mobile and Remote Access. For details, see Mobile and Remote Access via Cisco Expressway Deployment Guide .
What is off-premises access?
Off-premises access: a consistent experience outside the network for Jabber and EX/MX/SX Series clients
Does Expressway C use forward and reverse DNS?
You must create internal DNS records, for both forward and reverse lookups, for all Unified Communications nodes used with Mobile and Remote Access. This allows Expressway-C to find the nodes when IP addresses or hostnames are used instead of FQDNs. Make sure that the SRV record is not resolvable outside of the local network.
Does Cisco Expressway require mobile access?
In addition, you must configure Cisco Expressway with Mobile and Remote Access. For details, see Mobile and Remote Access via Cisco Expressway Deployment Guide .
Does Cisco Expressway use Unified Communications Manager?
This feature requires you to integrate Unified Communications Manager with Cisco Expressway. For Cisco Expressway configuration details for Mobile and Remote Access, refer to the Mobile and Remote Access Through Cisco Expressway Deployment Guide .
Do you need to exchange certificates between Cisco Expressway and Unified Communications Manager?
Cisco recommends that you use CA-signed certificates with the same CA for each system. In this case:
Do you need NTP for mobile access?
Mobile and Remote Access requires that you set up NTP servers for your deployment. Make sure that you have NTP servers deployed for your network and Phone NTP References for SIPendpoints.
Does Cisco support registration failover?
The Cisco IP Phones do not support registration failover.