
Do you have a template for implementing remote access policies?
Below, we’ve outlined some strong practices for implementing remote access policies and processes at your organization and included a remote access policy template that can serve as a solid foundation for your own.
What is the group’s Remote Access Policy?
This policy applies to remote access connections used to do work on behalf of the Group, including reading or sending email, viewing intranet web resources and network/system/application support. Remote access implementations that are covered by this policy include, but are not limited to, dial-in modems, Internet, ISDN, ADSL, VPN, and SSH etc.
What is restricted use of remote access?
Restricted use. Remote access privileges shouldn’t be given out in the office like candy, but rather on an as-needed basis. Only users who require remote access when traveling or working away from the office should be granted remote access. Remote access should be revoked when no longer needed.
What are the requirements for users with remote access privileges?
Users with remote access privileges must ensure that all authentication devices (e.g. hardware tokens or smart cards) must return to IT Security once task completed or the privileges has been revoked. IT Security must ensure that all returned devices are recorded before reassigned the devices to others.
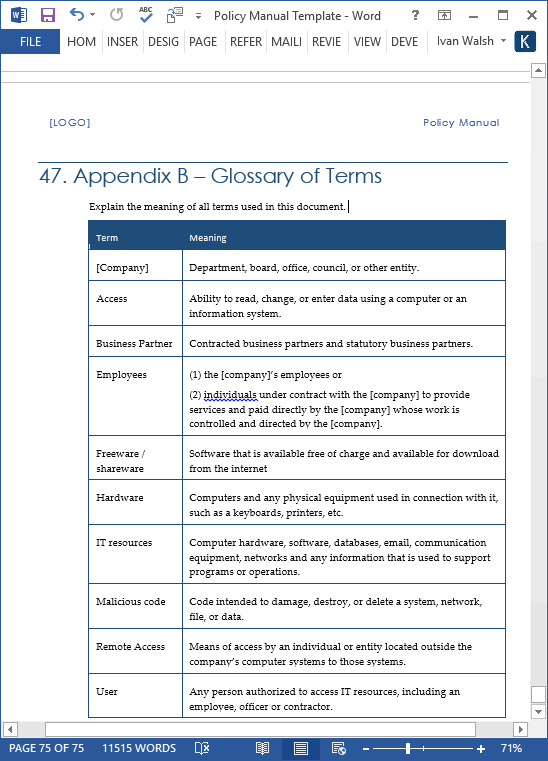
What should be included in a remote access policy?
What Should You Address in a Remote Access Policy?Standardized hardware and software, including firewalls and antivirus/antimalware programs.Data and network encryption standards.Information security and confidentiality.Email usage.Physical and virtual device security.Network connectivity, e.g., VPN access.More items...•
What is a remote access plan?
A well-designed remote access plan provides access to the required corporate data and applications for users when they're off-premises.
How do I create a network security policy?
How To Develop & Implement A Network Security PlanArticle Navigation.Step 1: Understand Your Business Model.Step 2: Perform A Threat Assessment.Step 3: Develop IT Security Policies & Procedures.Step 4: Create A “Security-First” Company Culture.Step 5: Define Incident Response.Step 6: Implement Security Controls.More items...•
What are the five elements of a remote access security readiness review?
The review examined cybersecurity at the governance layer and identified five critical pillars key to cybersecurity readiness: culture, people, structure, processes, and resources.
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What are three examples of remote access locations?
What Is Remote Access?Queens College.Harvard University Extension School.
What are the 5 network policies?
They include Acceptable Use, Disaster Recovery, Back-up, Archiving and Failover policies. People who need access to a network to do their job are usually asked to sign an agreement that they will only use it for legitimate reasons related to doing their job before they are allowed access.
What are the types of network security policies?
Types of Network Security ProtectionsFirewall. Firewalls control incoming and outgoing traffic on networks, with predetermined security rules. ... Network Segmentation. ... Remote Access VPN. ... Email Security. ... Data Loss Prevention (DLP) ... Intrusion Prevention Systems (IPS) ... Sandboxing. ... Hyperscale Network Security.
What are the common policies used in the modern network?
Terms in this set (17)What are common Policies used in the Modern Network. password policy. ... NDA (Non-Disclosure Agreement) Non-disclosure agreement. ... Password Policy. ... DLP (Data Loss Prevention) ... Remote-Access Policy. ... Incident Response Policy. ... bring your own device (BYOD) policy. ... AUP (Acceptable Use Policy)More items...
What is a Security Readiness Review?
A Readiness Review is a critical factor in the development and maintenance of a comprehensive risk and compliance-focused Information Security program. TrustedSec reviews an organization's control structure against the CMMC requirements and assists in the development of a strategy to become compliant or certified.
What is Cmmc readiness assessment?
The Cybersecurity Model Maturity Certification (CMMC) framework measures a company's aptitude to fully secure data critical to military safety, which, in turn, impacts all Americans' safety. To prepare for an official CMMC audit, many companies elect to execute a CMMC readiness assessment.
What is remote access and its advantages?
With remote access, employees can safely work from any device, platform, or network at their home office or abroad. Remote desktop functions allow them to remotely access important files and share their screen for meetings and troubleshooting.
What is the greatest benefit of remote access to an organization?
Flexibility. By allowing your staff to perform tasks outside the office using remote access, you can facilitate more flexible work arrangements and help employees create a better work/life balance.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
Why is remote access important?
With remote access, you can still accomplish tasks even outside of office hours. Since you have access to your office computer and network, you can still acquire necessary files and data you need to finish any time-sensitive demands that get in your way.
Why you need a remote access policy
Access to IT and business resources -- data, databases, systems and networks -- must be protected from unauthorized and potentially damaging attacks. Securing access to company resources from employees working remotely ensures IT assets and employees are shielded from potential disruptions.
How to create a remote access security policy
Remote access security policies should be developed by a cross-functional team to address operational, legal, competitive and other issues associated with remote access to information resources. The team should coordinate with internal departments for input on their remote access requirements and with HR to ensure uniform compliance by employees.
Remote access security policy sample
A remote access security policy can be simple. In fact, a few paragraphs added to an existing cybersecurity policy may be sufficient. The policy language should define remote access security activities and how they build on existing security policies and procedures, noting the metrics discussed previously.
1. Identifying the Objective of the Access Control Policy
It's important to know what you're trying to accomplish with your access control policy. It's not just about establishing policies and procedures for the IT department, but also about identifying and protecting sensitive information and defining your authentication mechanisms.
2. Determining What Type of Data Needs to Be Protected
Access control policies are designed to protect data that is sensitive to the organization.
4. Identifying What Kind of Tasks Will Be Performed by These Individuals or Groups
In addition to who will have access, it's important for you to know what kind of work will be performed by these individuals or groups and what the business requirements are.
5. Specifying the Level of Sensitivity of the Data Required for Each Task
It's important to decide how sensitive the data is and how much protection it needs to prevent unauthorized access.
6. Maintaining Regulatory and Government Access Compliance
As a business, it is imperative that you maintain Government and regulatory compliance.
What is the purpose of remote access policy?
Hence, the purpose of this policy is to define standards for connecting to the group’s network from any host. These standards are designed to minimize the potential exposure to the group from damages, which may result from unauthorized use of the group resources. Damages include the loss of sensitive or company confidential data, intellectual property, damage to public image, damage to critical group internal systems, etc.
What is the Organization Group policy?
This policy applies to all Organization Group employees, contractors and vendors with corporate owned computers or workstations used to connect to the Group’s network. This policy applies to remote access connections used to do work on behalf of the Group, including reading or sending email, viewing intranet web resources and network/system/application support.
What is the purpose of e-Citrix?
The main objective of this policy is to allow Organization IT Support staff, selected vendors and approved business users to access Organization resources through remote access. The current infrastructure through e-Citrix technology allows remote access to Organization’s enterprise application system.
Can IT support staff access applications?
a) IT Support staff are allowed remote access for applications for support purposes. IT Managers are advised to allow remote access only on a “need to have” basis based on Classification of Business Functions in Appendix A.
Can IT Security provide remote support?
c) IT Remote Support Services should not be provided for application with business function that has been classified as “Required” or “Non -Critical”. IT Security does not recommend remote support services for such applications to reduce the Groups’ exposure to unnecessary outside threats. However, such application may be allowed remote support services on an ad-hoc basis for a limited time period and approved by the Organization IT Management.
What is remote access?
Remote access refers to the process of connecting to internal resources from an external source (home, hotel, district, or other public area). The ability to securely and reliably connect to business resources from a remote location increases productivity.
Who bears full responsibility for any access misuse?
Users shall bear full responsibility for any access misuse
What is LEP password policy?
All user passwords shall be strong and follow guidelines and procedures in the [LEP] Access Control and Password Policy. Staff shall ensure that devices used for work purposes are not shared in a multi-user capacity, violate AUP conditions, or used in any inappropriate activity.
What is LEP policy?
This policy defines standards for staff to connect to the [LEP] network from a remote location. These standards are designed to minimize potential exposures including loss of sensitive information, and limit exposure to security concerns through a consistent and standardized access method.
What happens if a staff member is found in a policy violation?
Staff members found in policy violation may be subject to disciplinary action, up to and including termination.
Can you use personal equipment to connect to a LEP network?
Personal equipment shall not be used to connect to the [LEP] network using remote connection software and exceptions require [Insert Appropriate Role] written approval
PURPOSE
The purpose of this policy is to define standards for connecting to {company_name}'s network from any host. These standards are designed to minimize the potential exposure to {company_name} from damages which may result from unauthorized use of {company_name} resources.
SCOPE
This policy applies to all {company_name} employees, contractors, vendors and agents with a {company_name} owned or personally-owned computer or workstation used to connect to the {company_name} network.
POLICY
It is the responsibility of {company_name} employees, contractors, vendors and agents with remote access privileges to {company_name}'s corporate network to ensure that their remote access connection is given the same consideration as the user's on-site connection to {company_name}.
COMPLIANCE
The {company_name} Team will verify compliance to this policy through various methods, including but not limited to, business tool reports, internal and external audits, and feedback to the policy owner.
