A remote access policy is commonly found as a subsection of a more broad network security policy (NSP). The network security policy provides the rules and policies for access to a business’s network.
What is a remote access policy?
A remote access policy defines the conditions, remote access permissions, and creates a profile for every remote connection made to the corporate network. Through remote access policies you can define the following: Grant or deny dial-in based on connection parameters such as type and time of the day
What is a remote access policy (rap)?
What Is a Network Security Policy? A remote access policy is commonly found as a subsection of a more broad network security policy (NSP). The network security policy provides the rules and policies for access to a business’s network.
What are the security guidelines for remote access?
Remote policies have guidelines for access that can include the following: Hardware and software configuration standards for remote access, including anti-malware, firewalls, and antivirus. Encryption policies. Information security, confidentiality, and email policies. Physical and virtual device security.
How to increase security of remote remote access?
Security is further boosted by the enforcement of antivirus and firewall policies. A company should go for IPSec VPN remote access if it has a strong networking department with the ability to configure each employee’s hardware device individually (installing client software, enforcing security policies etc.).

What is remote access security policy?
A remote access policy serves as a guide for remote users connecting to the network. It extends the policies governing network and computer use in the office, e.g., password policy.
What are the examples of remote user security policy best practices?
Best Practices For Remote Access SecurityEnable encryption. ... Install antivirus and anti-malware. ... Ensure all operating systems and applications are up to date. ... Enforce a strong password policy. ... Use Mobile Device Management (MDM) ... Use Virtual Private Network (VPN) ... Use two-factor authentication.More items...•
What is the importance of remote access policy?
A remote access policy is vital to ensure that your organization can maintain its cybersecurity protocols even with all the uncertainty that remote access brings: unknown users (you can't see the person, after all), using potentially unknown devices on unknown networks, to access your corporate data center and all the ...
What constraints are available for use in a remote access policy?
Once a remote access policy has authorized a connection, it can also set connection restrictions (called constraints) based on the following: Encryption strength. Idle timeout. IP packet filters.
How do you protect remote access?
Basic Security Tips for Remote DesktopUse strong passwords. ... Use Two-factor authentication. ... Update your software. ... Restrict access using firewalls. ... Enable Network Level Authentication. ... Limit users who can log in using Remote Desktop. ... Set an account lockout policy.
What is a best practice for compliance in the remote access domain?
Instead, a best practice is to adopt the principle of least privilege, which means that access for all users should be blocked by default and enabled only for the specific accounts that require it. This will require more configuration, but it is well worth the added security benefits.
What are the key elements of remote access policy?
Remote access policies consist of the following elements: conditions, permissions, and profiles. We'll discuss each of these elements in turn, and list how each can be used to control remote access attempts by your network clients.
What is the remote access domain?
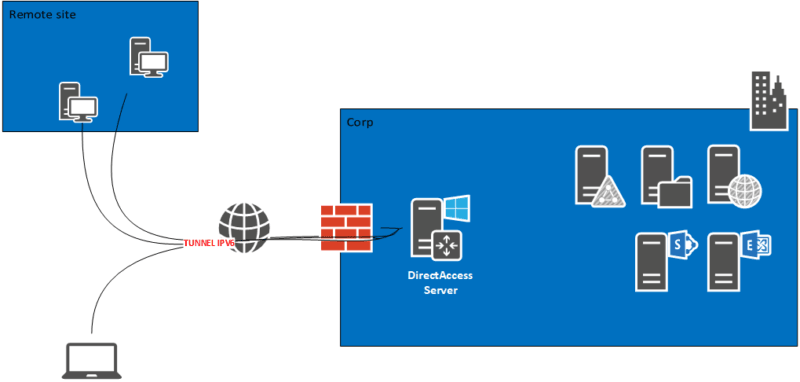
... is the domain in which a mobile user can access the local network remotely, usually through a VPN (Figure 7). ...
What should be included in an access control policy?
Organizations planning to implement an access control system should consider three abstractions: access control policies, models, and mechanisms. Access control policies are high-level requirements that specify how access is managed and who may access information under what circumstances.
How do I create a network security policy?
How To Develop & Implement A Network Security PlanArticle Navigation.Step 1: Understand Your Business Model.Step 2: Perform A Threat Assessment.Step 3: Develop IT Security Policies & Procedures.Step 4: Create A “Security-First” Company Culture.Step 5: Define Incident Response.Step 6: Implement Security Controls.More items...•
What is an access policy?
n. Principles or procedures that control the conditions under which individuals have permission and ability to consult a repository's holdings.
What is a network access policy?
Network policies are sets of conditions, constraints, and settings that allow you to designate who is authorized to connect to the network and the circumstances under which they can or cannot connect.
What practices allow you to be at your best when working remotely?
7 Best Practices for Working Remotely to Follow in 2022Make communication your top priority.Push yourself to experiment and find ways to be more productive.Be ready to work at different times of the day.Schedule in-person meetings every once in a while.Socialize and put efforts to strengthen your bond with the team.More items...
What is an example of remote control operations for providing security to an organization?
Popular examples include Remote Desktop Protocol (RDP) and Virtual Network Computing (VNC). While remote desktop access can have convenience advantages, this method is not typically recommended as it introduces significant security risks to the corporate network.
Which policy defines the security controls while working remotely?
ISO 27001 controls for remote working: A 6.2. 1 – Mobile device policy.
Why you need a remote access policy
Access to IT and business resources -- data, databases, systems and networks -- must be protected from unauthorized and potentially damaging attacks. Securing access to company resources from employees working remotely ensures IT assets and employees are shielded from potential disruptions.
How to create a remote access security policy
Remote access security policies should be developed by a cross-functional team to address operational, legal, competitive and other issues associated with remote access to information resources. The team should coordinate with internal departments for input on their remote access requirements and with HR to ensure uniform compliance by employees.
Remote access security policy sample
A remote access security policy can be simple. In fact, a few paragraphs added to an existing cybersecurity policy may be sufficient. The policy language should define remote access security activities and how they build on existing security policies and procedures, noting the metrics discussed previously.
Why Is a Remote Access Policy Necessary?
The numerous types of mobile devices and the different ways to connect pose challenges for the IT department. Devices can include cell phones, tablets, laptops, and any other device a remote worker relies on to conduct business. They can be company owned and secured, personally owned and authorized by a Bring Your Own Device (BYOD) policy, or a combination. Each class of device has its own set of security challenges. According to the National Institute for Standards and Technology’s Guidelines for Managing the Security of Mobile Devices in the Enterprise, “…Security controls available for laptops today are quite different than those available for smartphones, tablets, and other mobile device types.” Since different devices demand different controls, the policy has to detail what is allowed, compliant, and secure. The policy should answer the following questions:
What Problems Arise Without a Remote Access Policy?
Therefore, consequences for misuse can also be clearly outlined to compel compliance and appropriate precautions for data use and access. Elements such as firewalls, connectivity guidelines, personal use restrictions, and antivirus updates can help IT prevent both malicious and accidental loss and disruption of corporate information assets. The remote access control policies also provide protections for confidentiality, intellectual property, and information compliance.
What Is Remote Access?
Remote access is any connection made to an organization's internal network and systems from an external source by a device or host. Remote locations can be almost anywhere in the world, from the employee’s home to an off-site office, hotels, transportation hubs, and cafes.
What is VPN policy?
Policies for VPN remote access can be standardized. These policies “shore up” and prevent the use of rogue devices and access by non-authorized users , including the worker's family members or housemates. The policy also enforces proper email protocols to protect information from being sent through unsecured or untrusted sources, and also provides rules that limit or prohibit split tunnel configurations that allow mobile users to access both secure and unsecure networks simultaneously.
What percentage of people work remotely?
According to research conducted by Gallup, 43 percent of workers in the U.S. worked remotely at least some of the time in 2016. Remote workers report higher job satisfaction and flexibility, experience fewer distractions and interruptions, and are more productive. Companies experience less absenteeism, less stress on office accommodations, and realize greater employee retention. A recent New York Times article found that finance, insurance, real estate, and transportation were most likely to have and support remote work (retail and education were least likely candidates). The trend is only increasing: the 2016 Gallup poll also found that those who work remotely log more hours away from the office than was reported in their 2012 findings. Not only are people logging more hours, but remote workers are saving money when it comes to commuting costs and businesses are saving on office space expenses.
Why is remote access important?
Software organizations where development engineers need to connect across multiple locations, small organizations lacking office-space, and large, enterprise organizations all want to offer the most flexible work options in order to attract high-ranking candidates and reap the rewards of having such a policy.
What is unauthorized access policy?
Even if the employee provides their own equipment, laptop, or mobile device, the policy dictates and enforces the minimum-security requirements necessary. The policy can also provide determinations on who is allowed remote access, the level of access, and penalties for misuse.
What Is a Remote Access Policy?
For example, sales personnel can now use tablets and other mobile devices to connect remotely to their office networks while on client calls and bring up data that may be important for closing deals . Recent events have further boosted the number of remote workers to an estimated 42% of the US workforce.
Why Is a Remote Access Policy Important?
If a remote access policy is not in place, such risky behavior could go on unmitigated, without the organization finding out about it until after the occurrence of a breach.
What is remote work?
Remote work has brought with it a few challenges, including potential computer and network security risks. There is a real need for guidelines surrounding remote access, along with other policies. A remote access policy serves as a guide for remote users connecting to the network. It extends the policies governing network and computer use in ...
Why is password policy important?
It helps ensure that only those users who need it are given network access, as long as their devices are also compliant with the guidelines. When implemented properly, it helps safeguard the network from potential security threats.
What are the considerations when formulating a remote access policy?
Other considerations when formulating a remote access policy include but are not limited to the following: Standardized hardware and software, including firewalls and antivirus/antimalware programs. Data and network encryption standards. Information security and confidentiality. Email usage.
How to ensure that you do not miss anything when updating your remote access policy?
To ensure that you do not miss anything when updating your remote access policy, consider your organizational, legal, contractual and regulatory obligations when you compile the list of policy requirements. After that, identify the procedural and technical controls required to fulfill the policy, making sure to reinforce or replace existing controls that have not been effective.
Can you customize remote access policy?
Always ensure that your remote access policy is not an exact copy of another organization’s template; rather, you should customize it depending on your requirements. Otherwise, it might not be that useful for your organization.
What is the line of defense for remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly.
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
Why is IPSEC used?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
What are the implications of IPSec connections for corporations?
What are the implications of IPSec connections for corporations, considering the very nature of this connection? Well, your employee will only be able to access the network from a single, authorized device. Security is further boosted by the enforcement of antivirus and firewall policies.
What is IPSEC encryption?
IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect data flows between hosts and security gateways.
Why use two factor authentication for VPN?
Adopting two-factor authentication for remote access through VPN further boosts your network security. Now let’s take a look at why you should choose a particular VPN type as a secure connection methodology instead of the alternatives.
What is the first thing that’s required to ensure smooth remote access via a VPN?
The first thing that’s required to ensure smooth remote access via a VPN is to plan out a comprehensive network security policy.
What is a company security policy?
The company security policy provides a concrete standard of do’s and don’ts, and assures stakeholders that the organization takes IT security seriously, safeguards information, and has procedures in place in the event of an intrusion or security breach. What a Security Policy Should Contain.
What should a security policy contain?
The standard security policy typically consists of the following sections: Purpose of the policy. Outline the importance of information security. Stress the company’s reputation, legal, and ethical obligations to data privacy and proprietary information.
What is remote desktop policy?
This policy setting determines which users or groups can access the logon screen of a remote device through a Remote Desktop Services connection. It is possible for a user to establish a Remote Desktop Services connection to a particular server but not be able to log on to the console of that same server.
How to exclude users from remote desktop?
To exclude users or groups, you can assign the Deny log on through Remote Desktop Servicesuser right to those users or groups. However, be careful when you use this method because you could create conflicts for legitimate users or groups that have been allowed access through the Allow log on through Remote Desktop Servicesuser right.
Can you remove allow log on through Remote Desktop Services?
You should confirm that delegated activities are not adversely affected.
Can you log on to a domain controller?
For domain controllers, assign the Allow log on through Remote Desktop Servicesuser right only to the Administrators group. For other server roles and devices, add the Remote Desktop Users group. For servers that have the Remote Desktop (RD) Session Host role service enabled and do not run in Application Server mode, ensure that only authorized IT personnel who must manage the computers remotely belong to these groups.
Can you log on to Remote Desktop Services?
To use Remote Desktop Services to successfully log on to a remote device, the user or group must be a member of the Remote Desktop Users or Administrators group and be granted the Allow log on through Remote Desktop Servicesright. It is possible for a user to establish an Remote Desktop Services session to a particular server, but not be able to log on to the console of that same server.
When does a user rights assignment become effective?
Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on.
Can you deny log on to a group?
Alternatively, you can assign the Deny log on through Remote Desktop Servicesuser right to groups such as Account Operators, Server Operators, and Guests. However, be careful when you use this method because you could block access to legitimate administrators who also belong to a group that has the Deny log on through Remote Desktop Servicesuser right.
How to open domain controller security policy?
To open the domain controller security policy, in the console tree, locate GroupPolicyObject [ComputerName] Policy, click Computer Configuration, click Windows Settings, and then click Security Settings. Do one of the following:
How to configure local security policy?
To configure a setting using the Local Security Policy console. To open Local Security Policy, on the Start screen, type secpol.msc, and then press ENTER. Under Security Settings of the console tree, do one of the following: Click Account Policies to edit the Password Policy or Account Lockout Policy. Click Local Policies to edit an Audit Policy, ...
How to edit password policy?
Click Account Policies to edit the Password Policy or Account Lockout Policy. Click Local Policies to edit an Audit Policy, a User Rights Assignment, or Security Options. When you find the policy setting in the details pane, double-click the security policy that you want to modify. Modify the security policy setting, and then click OK. ...
How to change password policy in Windows 10?
In the console tree, click Computer Configuration, click Windows Settings, and then click Security Settings. Do one of the following: Click Account Policies to edit the Password Policy or Account Lockout Policy. Click Local Policies to edit an Audit Policy, a User Rights Assignment, or Security Options. In the details pane, double-click the ...
What does it mean when a local setting is inaccessible?
When a local setting is inaccessible, it indicates that a GPO currently controls that setting.
What console to use to configure security settings?
If you want to configure security settings for many devices on your network, you can use the Group Policy Management Console.
When does a user rights assignment become effective?
Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on.