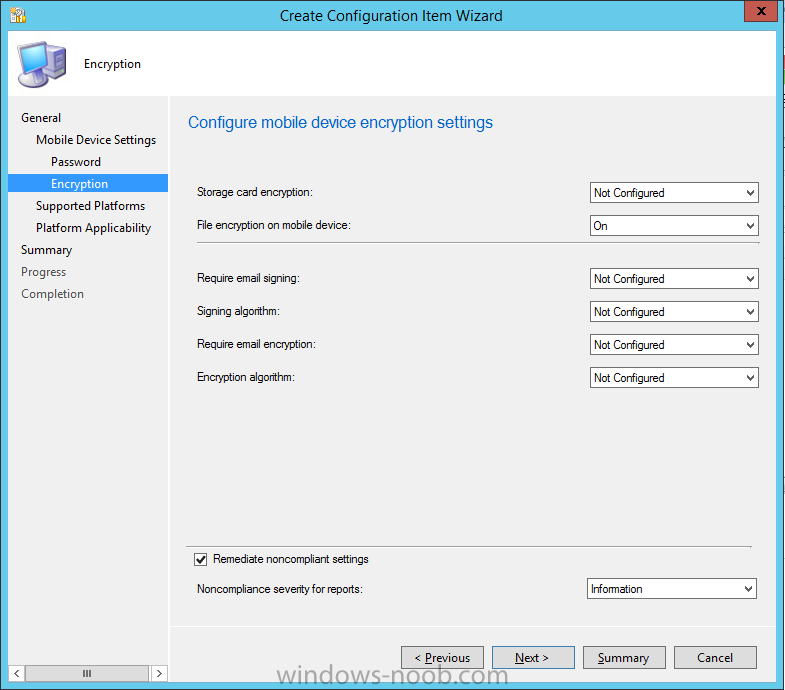
To configure encryption policies for specific users:
- Open Global Properties > Remote Access > Authentication and Encryption.
- From the Encryption algorithms section, click Edit.
- In the Encryption Properties window, click the IPSEC Security Association (Phase 2) tab.
- Clear Enforce Encryption Algorithm and Data Integrity on all users.
- Click OK and close the Global Properties window.
What is encryption and how does encryption work?
Encryption is a mathematical algorithm that is used to lock the data stream being passed between two devices (end-to-end) during a remote access session. The key to this lock is a secret number known only to the sender and receiver, and that changes with each session. The level of encryption reflects the number of possible key combinations.
What are the best practices for securing remote access?
Best Practices for Securing Remote Access. RAS: The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network ... IPSec: IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect ...
How can I Secure my remote desktop (RDP) session?
The ones we recommend changing are: Set client connection encryption level – Set this to High Level so your Remote Desktop sessions are secured with 128-bit encryption. Require secure RPC communication – Set this to Enabled. Require use of specific security layer for remote (RDP) connections – Set this to SSL (TLS 1.0).
How to enable and secure remote desktop on Windows 10?
How to Enable and Secure Remote Desktop on Windows 1 Enabling Remote Desktop. First, we need to enable Remote Desktop and select which users have remote access to the computer. ... 2 Securing Remote Desktop. ... 3 Security through Obscurity: Changing the Default RDP Port. ... 4 Last Steps. ...
What is a remote access method that uses encryption?
A VPN provides a mechanism to access corporate networks safely using Internet. VPN uses encryption to ensure only authorized user can access the corporate resources. A secure tunnel is created through the public network through which the packets are transported between the remote computer and the corporate network.
Does remote desktop use encryption?
Remote Desktop sessions operate over an encrypted channel, preventing anyone from viewing your session by listening on the network. However, there is a vulnerability in the method used to encrypt sessions in earlier versions of RDP.
How do you secure remote access?
Use virtual private networks (VPN) - Many remote users will want to connect from insecure Wi-Fi or other untrusted network connections. VPNs can eliminate that risk, however VPN endpoint software must also be kept up-to-date to avoid vulnerabilities that can occur from older versions of the software client.
Which method of remote access is the most secure?
Implement a Secure Connection for Remote Network AccessWired Connection: A wired connection is the most secure method for remote network access.Home Wi-Fi: The second most secure network connection is using a secured home Wi-Fi connection.More items...•
How do I know if my RDP is encrypted?
You can check the encryption level on target server where you got connected, open TS Manager and check the status of RDP connection, there you see encryption level.
Is remote access secure?
Remote access solutions could leave you vulnerable. If you don't have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data. Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular.
Why is RDP a security risk?
These are the most important vulnerabilities in RDP: Weak user sign-in credentials. Most desktop computers are protected by a password, and users can typically make this password whatever they want. The problem is that the same password is often used for RDP remote logins as well.
What are potential risks associated with remote access?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
Which protocol for remote access is more secure and why?
POINT-TO-POINT TUNNELING PROTOCOL (PPTP) It's used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network. PPTP is a great option because it's simple and secure.
What are two types of remote access servers?
Remote Access Methods1- Remote Access Server: It's one server in organization network that it is the destination of all remote access connections.2- Remote Access Client: All computers that remote connect to network, called remote access client or remote computer.More items...•
Who is more secure protocol for remote login?
Virtual private networks (VPNs) are a commonly used remote-access solution. They are designed to provide an encrypted tunnel for network traffic between a remote user and the enterprise network. VPNs also support security solutions like MFA that help to mitigate the threat of compromised accounts.
Is RDP traffic encrypted by default?
RDP has always supported strong encryption and is by default encrypted!
What level of encryption does RDP use?
RDP uses RSA's RD4 encryption to cipher all data transmitted to and from the local and remote desktop. The system administrators can choose whether to encrypt data using a 56-bit key or a 128-bit key, the 128-bit being the more secure route.
Does RDP use TLS?
Native RDP encryption (as opposed to SSL encryption) is not recommended. SSL (TLS 1.0): The SSL method requires the use of TLS 1.0 to authenticate the RD Session Host server. If TLS is not supported, the connection fails. This is the recommended setting for this policy.
Why is RDP a security risk?
These are the most important vulnerabilities in RDP: Weak user sign-in credentials. Most desktop computers are protected by a password, and users can typically make this password whatever they want. The problem is that the same password is often used for RDP remote logins as well.
How does secure remote access work?
Enabling remote access means walking a tightrope between usability and cybersecurity. Every remote worker needs a way to connect with remote desktop services and applications that won't slow down their workflows. At the same time, IT administrators must manage those connections to ensure they don't leave the network open to threats.
Why is secure remote access important to remote work security?
Secure remote access approaches are so vital because it’s now impossible to control security at the endpoint. Each user in a remote or hybrid workforce is connecting to the network from a different type of computer or smartphone, and they’re using a variety of internet connections to log in.
What are the options for secure remote access?
Multiple solutions go into a comprehensive secure remote access package—and each one delivers vital functionality that reflects the way companies use their networks today. These features work together to protect users, data, and network assets in a distinct way.
Next-gen remote access solutions for a secure digital workspace
Learn how remote access solutions can secure digital workspaces and enhance the user experience.
Citrix solutions for secure remote access
Citrix secure access solutions take several forms to give companies a balanced selection of options based on their specific requirements. Whatever level of engagement with remote work these businesses have, there is a secure remote access solution for the situation.
Why is IPSec VPN important?
IPSec VPN connections are also important for an employee who needs widespread access to the company’s network. A word of warning: If you are using IPSec VPN for remote access, but you are not deploying Internet Key Exchange (IKE, certificates) as an authentication method, the connection will be vulnerable.
Why is IPSEC used?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
What is client side VPN?
The client-side software is responsible for establishing a tunneling connection to the RAS and for the encryption of data. RAS VPNs are appropriate for small companies, requiring a remote access for a few employees. However, most serious businesses have moved on from this basic form of VPN connection.
What is IPSEC protocol?
IPSec: IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect data flows between hosts and security gateways. The unique feature of IPSec is that it operates at the Network Layer of the Open Systems Interconnection (OSI) protocol model.
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
What is the line of defense for remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly.
Should a company use IPSEC VPN?
A company should go for IPSec VPN remote access if it has a strong networking department with the ability to configure each employee’s hardware device individually (installing client software, enforcing security policies etc.).
What port is Remote Desktop listening to?
By default, Remote Desktop listens on port 3389. Pick a five digit number less than 65535 that you’d like to use for your custom Remote Desktop port number. With that number in mind, open up the Registry Editor by typing “regedit” into a Run prompt or the Start menu.
How to change the port on a firewall?
Go to the Start screen, search for “Windows Firewall” and click on it. When Windows Firewall opens, click “Advanced Settings” on the left side of the window . Then right-click on “Inbound Rules” and choose “New Rule.”. The “New Inbound Rule W izard” will pop up, select Port and click next.
Do remote desktop users need passwords?
All of the users that you gave Remote Desktop access need to have strong passwords. There are a lot of bots constantly scanning the internet for vulnerable PCs running Remote Desktop, so don’t underestimate the importance of a strong password.
Is remote desktop secure?
How to Enable and Secure Remote Desktop on Windows. While there are many alternatives, Microsoft’s Remote Desktop is a perfectly viable option for accessing other computers, but it has to be properly secured. After recommended security measures are in place, Remote Desktop is a powerful tool for geeks to use and lets you avoid installing third ...
Is network level authentication necessary?
It’s not a necessity to require Network Level Authentication, but doing so makes your computer more secure by protecting you from Man in the Middle attacks . Systems even as old as Windows XP can connect to hosts with Network Level Authentication, so there’s no reason not to use it.
What Is VPN Encryption?
VPN Encryption is a process by which a VPN hides your data in a coded format unreadable by anyone trying to snoop on your data.
Different Types Of VPN
A VPN uses different combinations and techniques for encryption which can be easily understood when you know the types of VPN and the protocols they use for encryption and security.
Types Of VPN Protocols
The level of privacy and security that you get from a VPN is dependent on what type of protocol it uses to secure your data and maintain privacy. The VPN providers use different types of VPN protocols; each type of VPN protocol mentioned below provides an extra level of security, so let’s take a look at them.
VPN Without Encryption
Not all VPNs need to offer encryption. It is a sporadic case that a VPN tunnel is unencrypted, but it happens; some VPNs might not use encryption to protect data traveling via a tunnel.
VPN Encryption Algorithms
VPN uses protocols and some encryption algorithms for the ultimate privacy protection. There are mainly three VPN encryption algorithms used by the commercial or standard VPN companies AES, RSA, and SHA., briefly described below.
Conclusion
After all the discussion we have done to let you know entirely about what a VPN does for your privacy and security and how it does so, we helped a little more towards protecting your internet privacy and encryption.
What authentication protocol does PowerShell use?
By default, PowerShell Remoting uses Kerberos (if available) or NTLM for authentication. Both of these protocols authenticate to the remote machine without sending credentials to it. This is the most secure way to authenticate, but because the remote machine does not have the user's credentials, it cannot access other computers and services on the user's behalf. This is known as the "second hop problem".
Why use SSL certificate for NTLM?
Using SSL certificates to validate server identity during NTLM-based connections. Since the NTLM authentication protocol cannot ensure the identity of the target server (only that it already knows your password), you can configure target servers to use SSL for PowerShell Remoting. Assigning a SSL certificate to the target server (if issued by ...
What is WinRM service?
WinRM runs as a service under the Network Service account, and spawns isolated processes running as user accounts to host PowerShell instances. An instance of PowerShell running as one user has no access to a process running an instance of PowerShell as another user.
What is TLS protocol?
When connecting over HTTPS, the TLS protocol is used to negotiate the encryption used to transport data. When connecting over HTTP, message-level encryption is determined by initial authentication protocol used. Basic authentication provide no encryption. NTLM authentication uses an RC4 cipher with a 128-bit key.
Does NTLM know the password?
The server typically does not know the user's password, so it communicates with the domain controller, which does know the user's password and calculates the session key for the server. The NTLM protocol does not, however, guarantee server identity.
