
Remote access fraud
- You receive an unexpected phone call claiming to be from a well-known company, such as your internet service provider or...
- They tell you your computer is experiencing technical problems, your broadband is unusually slow, or that there’s a...
- To fix it, they insist on you giving them remote access to your computer – they’ll explain how to do this –...
Full Answer
What is an remote access scam?
Remote access scams try to convince you that you have a computer or internet problem and that you need to buy new software to fix the problem.
What are the signs of unwanted remote access to computer?
They ask you to buy software or sign up to a service to fix the computer. They ask for your personal details and your bank or credit card details. The caller is very persistent and may become abusive. Never give an unsolicited caller remote access to your computer.
What are the signs of a broadband scam?
They may claim that your broadband connection has been hacked. The caller will request remote access to your computer to ‘find out what the problem is’. The scammer may try to talk you into buying unnecessary software or a service to ‘fix’ the computer, or they may ask you for your personal details and your bank or credit card details.
How can scammers obtain my number fraudulently?
Scammers can obtain your number fraudulently. Make sure your computer is protected with regularly updated anti-virus and anti-spyware software, and a good firewall. Research first and only purchase software from a source that you know and trust.

What is remote fraud?
Remote authentication fraud occurs when a person who is not the legitimate owner of an identity or financial account either fraudulently creates a new account or takes over an existing digital account for the sole purpose of committing an illegal activity using stolen payment credentials or unauthorized payment ...
What types of internet frauds are most common?
Email-based phishing scams are among the most prevalent types of internet fraud, which continues to pose a serious threat to internet users and businesses.
What happens when a hacker gets remote access to my computer?
Hackers use RDP to gain access to the host computer or network and then install ransomware on the system. Once installed, regular users lose access to their devices, data, and the larger network until payment is made.
Can a scammer access my phone?
Scammers use auto-dialers and spoofed area codes to trick people into picking up the phone. From there, it's a numbers game. The scammers want to get as much personal information from the call recipient as possible. That can include anything from names and birth dates to credit card numbers.
What are the signs of being scammed?
Some 7 signs that you are being scammed:A company is contacting you out of the blue. ... You've been rejected for credit, but you've got a good credit history. ... You're being rushed. ... Your bank is asking you for your PIN number personal information. ... The letter or email you have received is full of dodgy spelling and bad grammar.More items...•
Do online fraudsters get caught?
Except in rare cases, you won't strike it rich as a criminal, and you have a strong chance of getting caught and sentenced to jail. Let's compare that to Internet crime statistics. Per an FBI 2011 report, 300,000 people were victimized over the Internet to the tune of $1.1 billion.
What can a scammer do with remote access to your computer?
In a remote access scam, a scammer attempts to persuade you into giving them remote control over your personal computer, which allows the scammer to con money out of you and steal your private information.
Can someone remotely access my computer without me knowing?
"Can someone access my computer remotely without me knowing?" The answer is "Yes!". This could happen when you are connected to the internet on your device.
How can I tell if someone is remotely accessing my computer?
To see all the login activities on your PC, use Windows Event Viewer. This tool will show you all Windows services that have been accessed and logins, errors and warnings. To access the Windows Event Viewer, click the search icon and type in Event Viewer. Click Windows Logs, then choose Security.
What are 2 things you should do if your identity is stolen?
Scan credit card and bank statements for unauthorized charges.File a Claim with Your Identity Theft Insurance. ... Notify Companies of Your Stolen Identity. ... File a Report with the Federal Trade Commission. ... Contact Your Local Police Department. ... Place a Fraud Alert on Your Credit Reports. ... Freeze Your Credit.More items...
Can someone hack my bank account with my phone number?
With your phone number, a hacker can start hijacking your accounts one by one by having a password reset sent to your phone. They can trick automated systems — like your bank — into thinking they're you when you call customer service.
What do I dial to see if my phone has been hacked?
After you discover your phone was hacked, you can take this number and file a police report. Just enter *#06# code utilizing the dialer pad on your device. Your IMEI number will appear, and there is a necessity to save this number in a secret place so nobody can know it.
Can a hacker remotely turn on my computer?
Generally speaking, hacking a turned-off computer is not possible in a home environment. However, it may happen in shared networks such as an office environment. There are features that allow you to remotely turn on and boot a computer.
Can a hacker take control of my computer?
Your computer can be used to attack other computers. Sometimes hackers will take over a computer, sometimes thousands of them, to launch an attack on a website they've targeted.
Can a hacker access my PC?
These online villains typically use phishing scams, spam email or instant messages and bogus websites to deliver dangerous malware to your computer and compromise your computer security. Computer hackers can also try to access your computer and private information directly if you are not protected by a firewall.
What can hackers do remotely?
Remote Desktop Protocol (RDP) Hacks Remote hackers use online scanning tools to find unsecured RDP endpoints. They then use stolen credentials to exploit such ports, access the network, and lock systems or data that they then use as leverage for ransom payments.
Identity fraud
Fraudsters steal personal information about you to impersonate you. They then take out loans and credit cards in your name, or withdraw cash from your bank account.
Cash machine fraud
Fraudsters continue to find new ways to pull off this con, but the outcome is still the same – distracted at an ATM, you lose sight of your card and your bank account is emptied before you realise.
Emails, text messages and calls
You receive an email, text message or call claiming to be from a well-known company or organisation, such as a bank or the police.
Card fraud
A fraudster gets access to your personal information or steals your credit or debit card details. This lets them spend with your card.
Return to fraud and scams homepage
Have you educated yourself enough on the different types of scams? Head back to the homepage.
What is malware scam?
Malware tricks you into installing software that allows scammers to access your files and track what you are doing, while ransomware demands payment to ‘unlock’ your computer or files.
What does it mean when you receive a phone call out of the blue?
You receive a phone call out of the blue and the caller claims to be from a large telecommunications or computer company, or a technical support service provider.
What is remote access scam?
Remote access scams try to convince you that you have a computer or internet problem and that you need to buy new software to fix the problem.
What is identity theft?
Identity theft is a type of fraud that involves using someone else's identity to steal money or gain other benefits.
What to do if you think you have provided your account details to a scammer?
If you think you have provided your account details to a scammer, contact your bank or financial institution immediately.
How to protect your computer from spyware?
Make sure your computer is protected with regularly updated anti-virus and anti-spyware software, and a good firewall. Research first and only purchase software from a source that you know and trust.
Is the caller persistent?
The caller is very persistent and may become abusive.
What does a caller ask about internet speed?
The caller might ask if you have experienced slow internet connection speed or interruptions to your service. They might claim you are due for a router, modem or infrastructure (copper to fiber) upgrade. They might even ask you to visit a speed test website. Maybe they wanted to provide you with a refund for this slow service?
What remote access programs are available?
Anydesk, TeamViewer and GoToAssist are among the most popular remote access programs. In any case, you would have been requested to provide an access code or PIN so the so called ‘technician’ could access your device and fix the problems.
What do you need to provide to a caller to verify your identity?
These callers may often request that you provide a photo of yourself holding your driver licence or passport to verify your identity. You may also be asked to disclose email addresses, phone numbers, residential address or tax details.
What is the liability of IDCARE?
IDCARE’S liability for any loss or damage suffered by any person or organisation (including, without limitation, any direct, indirect or consequential loss or damage) arising out of or in connection with the Services (including without limitation liability for any negligent act or omission, or statement, representation or misrepresentation of any officers, employees, agents, contractors or consultants of IDCARE) shall be limited to the fees paid by you to IDCARE in respect of the Services. For the avoidance of doubt, this limitation of liability extends to any liability arising from any actions performed or not performed as a result of any recommendations made in course of providing the Services.
Is the NBN rollout searchable?
The caller may initiate contact with you. Remember – rollout of the NBN is easily searchable via the internet. Scam callers may use this information to target suburbs where the NBN is due for an upgrade or has reported a recent outage.
Can anyone remotely access my phone?
Never allow anyone to remotely access your device. Be wary of anyone requesting a PIN number or code that appears on your device. Many callers will try to deceive you and others who are not ‘in the know’ surrounding technology.
Is IDCARE liable to other people?
The Services provided by IDCARE are intended to be provided solely to the initial recipient of this document or service and IDCARE will not be liable to any other person who may receive this document.
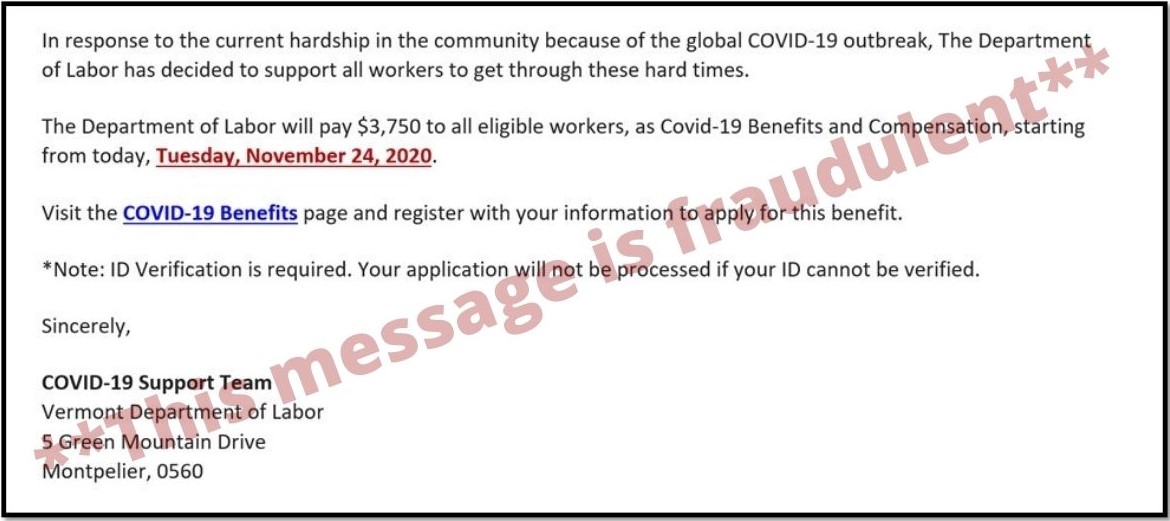
What Is A Remote Access Scam?
How Big Is The Problem?
- In Australia, remote access scams are now the sixth largest scam type. As of September, the total reported losses via the ACCC are $4.7 million, yet this only represents reported losses. We can safely assume that total losses run well into the tens of millions per annum. The losses are on the rise as well, with September 2020 representing a new record, with over $1.1 million lost and in e…
What Is The Impact on Victims?
- From a trust and emotional perspective, all victims are materially impacted by scams. From a loss perspective, the amounts can vary from a few thousand dollars to someone's entire life savings. Different banks have different approaches in terms of reimbursing customers — that is, at what stage is the bank liable for protecting the customer vs. the victim being responsible. However, th…
How Can We Protect Victims?
- Dubbed the “call that could wipe out your life savings,” four in ten consumers have not heard of remote access scams. Protection begins on the front lines, and raising awareness about these scams with consumers and businesses is a starting point. There is a lot of great work being done in this space by entities such as Scamwatch and UK Financeas well as by the banking industry it…
What Can Banks Do to Detect Remote Access Scams?
- Most authentication and fraud prevention solutions rely on known device and IP location parameters to measure fraud risk. While these controls can be effective, RATs, by design, circumvent traditional fraud detection tools that look for the presence of malware, bots, and blacklisted devices, or IP addresses. Instead of relying on static controls, BioCatchuses machin…