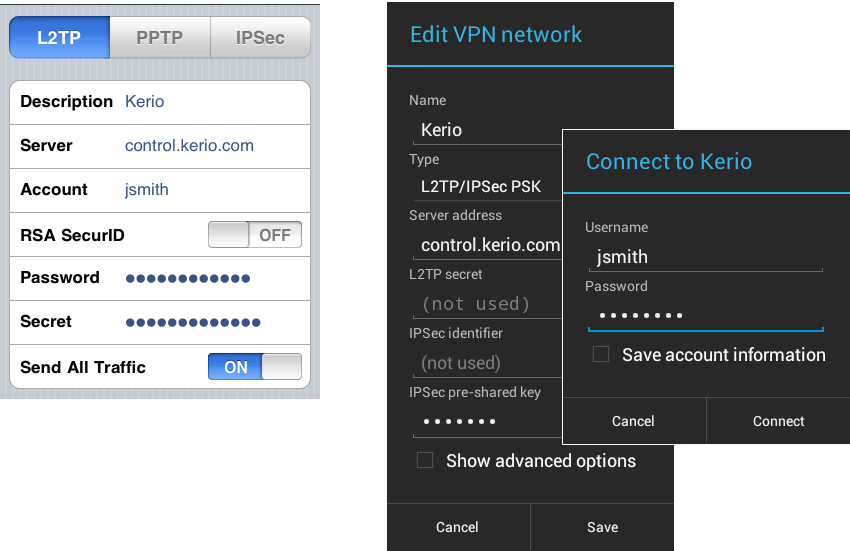
Go to VPN > IPsec (remote access) and click Enable. Specify the general settings: Select a WAN port. Specify a preshared key or the local and remote certificates. Specify the IDs if required. Select the users and groups you want to allow. Specify the client information.
Full Answer
What is IPSec VPN client?
The IPSec VPN Client supports your remote workforce, gives you peace of mind from access anywhere outside the office. Whether you’re in office or home office, it is a security-conscious VPN service, providing one of the best way to protect your privacy as you communicate over the Internet!
What VPN license do I need to use IPSEC remote access VPN?
IPsec remote access VPN using IKEv2 requires an AnyConnect Plus or Apex license, available separately. IPsec remote access VPN using IKEv1 and IPsec site-to-site VPN using IKEv1 or IKEv2 uses the Other VPN license that comes with the base license.
What are remote access VPNs?
Remote access VPNs allow users to connect to a central site through a secure connection over a TCP/IP network. The Internet Security Association and Key Management Protocol, also called IKE, is the negotiation protocol that lets the IPsec client on the remote PC and the ASA agree on how to build an IPsec Security Association.
How many concurrent connections does the IPsec VPN profile support?
Enter the number of concurrent connections that the VPN profile supports. Range is 1 through 4294967295. When the maximum number of connections is reached, no more remote access user (VPN) endpoints attempting to access an IPsec VPN can begin Internet Key Exchange (IKE) negotiations.
Does remote access VPN use IPsec?
While Remote access VPN supports SSL and IPsec technology.
What is IPsec remote access VPN?
The IPsec Remote Access feature introduces server support for the Cisco VPN Client (Release 4. x and 5. x) software clients and the Cisco VPN hardware clients. This feature allows remote users to establish the VPN tunnels to securely access the corporate network resources.
How can I configure IPsec client based VPN for remote users?
Navigate to IPSec VPN | DHCP over VPN and select Central Gateway from the menu.Click Configure. The DHCP over VPN Configuration window is displayed.Select the appropriate options for your configuration. Refer to the information below for more details. Use Internal DHCP Server- ... Click OK.
Can VPN be accessed remotely?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
Can IPsec be hacked?
Hackers Could Decrypt IPsec Information However, a team of researchers discovered numerous security vulnerabilities related to an internet key exchange protocol called “IKEv1.” IPsec maintains encrypted connections between two parties when both of them define and exchange shared keys during communications.
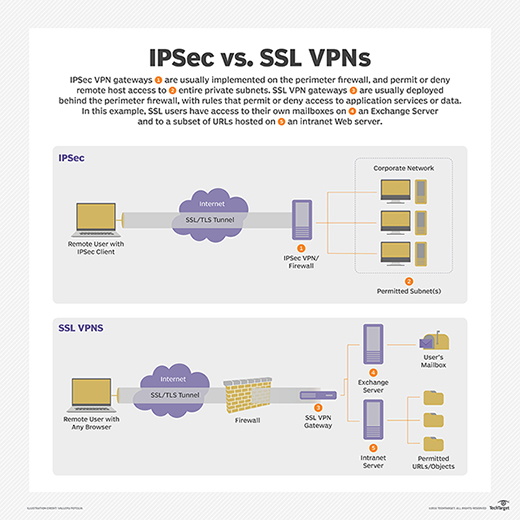
What is the difference between VPN and IPsec?
The major difference between an IPsec VPN and an SSL VPN comes down to the network layers at which encryption and authentication are performed. IPsec operates at the network layer and can be used to encrypt data being sent between any systems that can be identified by IP addresses.
What is the difference between global VPN and SSL VPN?
2) The main differences to consider are the end clients that they support and the data transfer rates. --GVC can only be used for Windows clients whereas SSLVPN can be used for MAC, Windows, and Mobile devices.
How do I setup a global VPN client?
Navigate to MANAGE| VPN |DHCP over VPN, select Central Gateway from the drop down.Click Configure. The DHCP over VPN Configuration window is displayed.Select Use Internal DHCP Server if SonicWall is the DHCP server. Check the For Global VPN Client checkbox to use the DHCP Server for Global VPN clients.
What is required when creating an IPsec VPN policy?
Creating an IPsec VPN connection Go to VPN > IPsec Connections > Select Wizard > Enter a name > Click Start. Select Site To Site as the connection type, select Head office, and the policy created earlier. Set the Authentication type to Preshared key. In Local subnet field, select the local LAN created earlier.
Which VPN is best for remote access?
Perimeter 81 – Best all-round business VPN. Jul 2022. ... GoodAccess – Security Strategy Options. Apps Available: ... ExpressVPN – Lightning Fast VPN. ... Windscribe – VPN with Enterprise-Friendly Features. ... VyprVPN – Secure VPN with Business Packages. ... NordVPN – Security-first VPN. ... Surfshark – VPN with Unlimited User Connections.
What is the difference between remote access VPN and site to site VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
How does a remote access VPN differ from a host to host VPN?
**With a remote access VPN, a server on the edge of a network (called a VPN concentrator) is configured to accept VPN connections from individual hosts in a client to site configuration. Hosts that are allowed to connect using the VPN connection are granted access to resources on the VPN server or the private network.
Which is better IPSec or OpenVPN?
IPSec is generally regarded as faster than OpenVPN. The main reason for this is actually a pro for OpenVPN in another area, and that is how it is implemented. IPSec is implemented in the IP stack of the kernel, whereas OpenVPN is implemented in the userspace.
What are the benefits of IPSec?
IPsec provides the following security services for traffic at the IP layer: Data origin authentication—identifying who sent the data. Confidentiality (encryption)—ensuring that the data has not been read en route. Connectionless integrity—ensuring the data has not been changed en route.
When should I use IPSec tunnel mode?
When to Use IPsec Tunnel ModeTunnel mode protects internal routing information by encrypting the original packet's IP header by creating a new IP header on top of it. ... Tunnel mode is mandatory when one of the peers is a security gateway applying IPsec on behalf of another host.More items...•
How do I activate IPSec?
How do I enable IPSec on a machine?Right click on 'My Network Places' and select Properties.Right click on 'Local Area Connection' and select Properties.Select 'Internet Protocol (TCP/IP)' and click Properties.Click the Advanced button.Select the Options tab.Select 'IP security' and click Properties.More items...
Description
This article will walk you through configuring, installing, and using the Global VPN Client (GVC) Software for Remote IPSec VPN connections.
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Can SRX be used as an EAP server?
SRX Series device cannot act as an EAP server. An external RADIUS server must be used for IKEv2 EAP to do the EAP authentication. SRX will act as a pass-through authenticator relaying EAP messages between the Juniper Secure Connect client and the RADIUS server. This option is enabled by default.
Can a firewall be created between internal zones?
Auto-create Firewall Policy. If you select Yes, a firewall policy is automatically created between internal zone and tunnel interface zone with local protected networks as source address and remote protected networks as destination address. Another firewall policy will be created visa-versa.
Remote Access VPN Products
Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser.
What is Remote Access VPN?
Remote Access VPN ensures that the connections between corporate networks and remote and mobile devices are secure and can be accessed virtually anywhere users are located. A secure remote access solution promotes collaboration by connecting global virtual teams at headquarters, branch offices, remote locations, or mobile users on the go.
Technical Resources
The place to discuss all of Check Point’s Remote Access VPN solutions, including Mobile Access Software Blade, Endpoint Remote Access VPN, SNX, Capsule Connect, and more!
Our Customers Love Us
Versatile Security Protection –Like A Swiss Army Knife For Security Checkpoint Next Generation Firewall proves to be a great solution for our small business infrastructure. R80 Security Management has allowed our company to easily (and significantly) improve our protections over time. read more >
Quantum is powered by ThreatCloud
ThreatCloud, the brain behind all of Check Point’s products, combines the latest AI technologies with big data threat intelligence to prevent the most advanced attacks, while reducing false positives.
Extend the Working Experience with Zero-Trust Network Security
Businesses from small to large all need to get ready for the growing demands of an increasingly mobile workforce and distributed work site expansions. As to protect your businesses from inside out, you need the right VPN service to apply proper access control.
IPSec VPN Client
The new time-based subscription* and perpetual licenses are available for IPSec VPN Client, enabling you to customize for your business needs. The IPSec VPN Client supports your remote workforce, gives you peace of mind from access anywhere outside the office.
SSL VPN Client
Remote work is becoming the new normal, secured verification of devices and data is imperative. The SSL VPN Client is a lite VPN software which is provided to set up secured connection without the common difficulties. The SSL VPN allows not only you but also your employees to expand network access wherever you are travelling, mobile, or in homes.
Remote Access Security Solutions
Operating with Zero Trust best practices across wired or wireless network infrastructures – wherever your employees: HQ, branch offices, on-the-go, or even working from home. Together we can help your business maintain continuity and safety.
Description
- This article will walk you through configuring, installing, and using the Global VPN Client (GVC) Software for Remote IPSec VPN connections. CAUTION:Please make sure to read this article to completion and follow the included steps closely. Even one missed step will result in a failed configuration.
Resolution For SonicOS 7.x
- This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware. Configure WAN Group VPN on the SonicWall 1. Login to the SonicWall management GUI. 2. ClickNetworkin the top navigation menu. 3. Navigate toIPSec VPN | Rules and Settings. 4…
Olution For SonicOS 6.5
- This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware. Configure WAN Group VPN on the SonicWall 1. Login to the SonicWall management GUI. 2. Click Managein the top navigation menu. 3. Navigate toVPN | Base Settings. 4. Ensure th…
Related Articles
Categories
- Firewalls> TZ Series> GVC/L2TP
- Firewalls> NSa Series> GVC/L2TP
- Firewalls> NSv Series> GVC/L2TP