Configure Remote Access as a VPN Server
- On the VPN server, in Server Manager, select the Notifications flag.
- In the Tasks menu, select Open the Getting Started Wizard The Configure Remote Access wizard opens. ...
- Select Deploy VPN only. ...
- Right-click the VPN server, then select Configure and Enable Routing and Remote Access. ...
When to use remote desktop over VPN?
- Get the IP address for that PC using the procedure we outlined previously.
- Use Registry Editor to change the Remote Desktop listening port number on that PC.
- Make notes on which port number goes with which IP address.
How to set up routing and remote access?
- In Routing and Remote Access, expand the server → IPV4 → NAT.
- Right click on External Network, go to properties → Services and ports.
- Click on Add, enter the description for this service, enter the RDP port and IP address of the VPS and click on Ok.
How to set up your own home VPN Server?
How to Set Up Your Own VPN Server
- Method 2: Flash Your Current router (DD-WRT, OpenWRT, or Tomato Firmware)
- Method 3: Use Other Devices as VPN Servers. Firmware such as DD-WRT replaces the operating system on your router’s flash memory – a process called ‘flashing’.
- Method 4: Use a Cloud Computing Provider to Set up a VPN Server. ...
How to use your smart card to access CDC VPN?
Watch Event
- Needs the Smart Card Reader, please read How to Purchase Your Smart Card Reader
- Needs the Smart Card Software skip to How to Download and Install Smart Card software
- Already has the Smart Card software and a Smart Card Reader you can skip to the section How to Login to Remote IPTV .
How to install Remote Access Role in VPN?
On the VPN server, in Server Manager, select Manage and select Add Roles and Features. The Add Roles and Features Wizard opens. On the Before you begin page, select Next.
How to start remote access?
Select Start service to start Remote Access. In the Remote Access MMC, right-click the VPN server, then select Properties. In Properties, select the Security tab and do: a. Select Authentication provider and select RADIUS Authentication.
How to select a server from the server pool?
On the Select destination server page, select the Select a server from the server pool option. Under Server Pool, select the local computer and select Next. On the Select server roles page, in Roles, select Remote Access, then Next. On the Select features page, select Next. On the Remote Access page, select Next.
How many Ethernet adapters are needed for VPN?
Install two Ethernet network adapters in the physical server. If you are installing the VPN server on a VM, you must create two External virtual switches, one for each physical network adapter; and then create two virtual network adapters for the VM, with each network adapter connected to one virtual switch.
What is NAS in a network?
A NAS is a device that provides some level of access to a larger network. A NAS using a RADIUS infrastructure is also a RADIUS client, sending connection requests and accounting messages to a RADIUS server for authentication, authorization, and accounting. Review the setting for Accounting provider: Table 1.
Can you assign a VPN to a pool?
Additionally, configure the server to assign addresses to VPN clients from a static address pool. You can feasibly assign addresses from either a pool or a DHCP server; however, using a DHCP server adds complexity to the design and delivers minimal benefits.
Is RRAS a router or a server?
RRAS is designed to perform well as both a router and a remote access server because it supports a wide array of features. For the purposes of this deployment, you require only a small subset of these features: support for IKEv2 VPN connections and LAN routing.
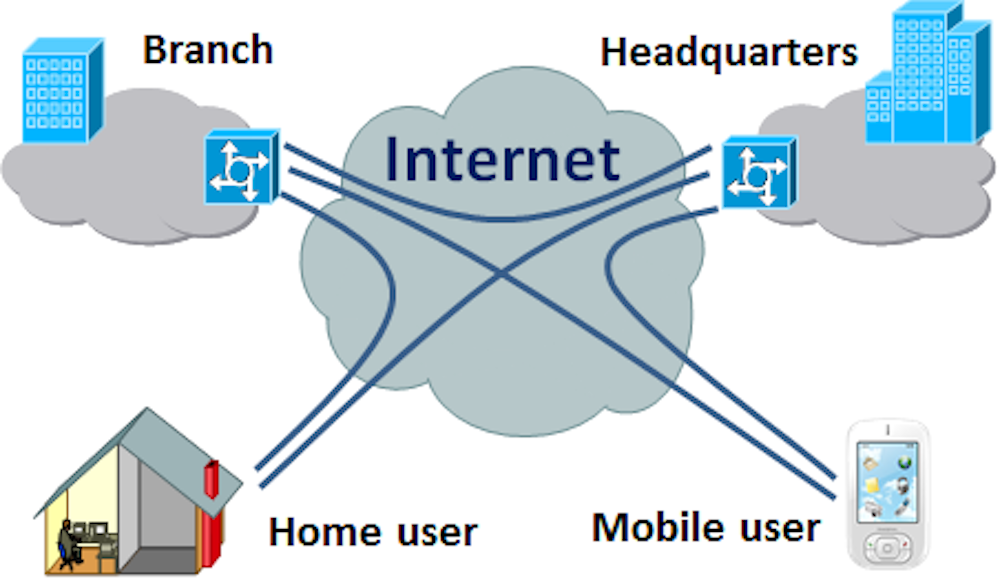
What is remote access VPN?
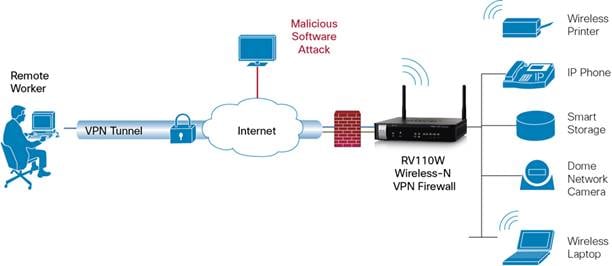
What Is a Remote Access VPN? A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive. The remote access VPN does this by creating a tunnel between an ...
Why is VPN remote access?
The remote access VPN does this by creating a tunnel between an organization’s network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
Does SASE require a VPN?
Using SASE, an organization does not have to maintain a separate stand-alone proxy or VPN. Rather, users connect to a SASE solution (which provides access to the cloud and data center) with consistent security. Some advantages of using a SASE are that it allows companies to:
What is SSTP in VPN?
SSTP is a Microsoft proprietary SSL-based solution that can penetrate firewalls since most firewalls open the outbound TCP port that 443 SSL uses. OpenVPN. OpenVPN is a SSL-based solution that can penetrate firewalls since most firewalls open the outbound TCP port that 443 SSL uses. IKEv2 VPN.
Can a syslog be routed over a site to site connection?
No. It can only be routed over a Site-to-Site connection.
Does Radius support OpenVPN?
RADIUS authentication is supported for the OpenVPN protocol only through PowerShell.
Does Azure support P2S VPN?
Azure supports Windows, Mac, and Linux for P2S VPN.
Does VPN reestablish automatically?
By default, the client computer will not reestablish the VPN connection automatically.
Do you need a VPN for a resource manager?
Yes. For the Resource Manager deployment model , you must have a RouteBased VPN type for your gateway. For the classic deployment model, you need a dynamic gateway. We do not support Point-to-Site for static routing VPN gateways or PolicyBased VPN gateways.
Can a point to site client connect to a VNet?
Yes, Point-to-Site client connections to a virtual network gateway that is deployed in a VNet which is peered with other VNets may have access to other peered VNets. Point-to-Site clients will be able to connect to peered VNets as long as the peered VNets are using the UseRemoteGateway / AllowGatewayTransit features.
Why connect to a VPN on your home computer before anything else?
Why connect to a VPN on your home computer before anything else? This ensures that all TeamViewer traffic is routed through the VPN’s encrypted tunnel, keeping your data safe and sound. You don’t want to run into a situation such as this one where the person accessed TeamViewer before connecting to their VPN, thus dropping the remote desktop connection.
How secure is VPN?
How can VPNs provide secure access? Well, once you connect to a VPN client, all the data passing through your network is encrypted. Any hacker or other malicious third parties trying to snoop in will only see an encrypted data stream, which basically looks like gibberish.
What websites were hit by ransomware in 2016?
In 2016, a number of major websites including the New York Times and the BBC were hit by ransomware attacks. How does this relate to ad-blockers? Well, the malicious code was actually injected into ads running on those websites, which attempted to exploit any vulnerabilities found on the victims’ devices.
How to find remote PC on TeamViewer?
If you use a TeamViewer account, then log in on your home computer and find your remote PC in the “ Computers & Contacts ” section. Double click on it.
Can you unattended access TeamViewer?
Once TeamViewer is done installing on your work computer, you’ll be prompted to set up unattended access. Refer to the image below for details.
Can a hacker see encrypted data?
Any hacker or other malicious third parties trying to snoop in will only see an encrypted data stream, which basically looks like gibberish. Learn more: Deconstructing VPN: What Is VPN Encryption. You can safely transfer files from your office network, as well as access your work computer from home for various tasks.
Can phishing attack open a PDF?
Other phishing attacks trick you into opening malware-infected files. For example, they could masquerade malicious .exe files as .pdf or other document formats. Always verify the file extension and the validity of any email before opening any attachments. Just to be safe, you should also install some decent anti-malware software on your device (s).
How to log into remote desktop?
Once you’re done setting things up, you should be able to log into Remote Desktop over the internet by connecting to the public IP address your router exposes for your local network followed by a colon and then the port number for the PC to which you want to connect.
What port is used for remote desktop?
You’ll need to log into your router and have it forward all traffic using TCP port 3389 to the IP address of the PC running Remote Desktop.
Can you save a connection in Remote Desktop?
Of course, you can always save that connection in Remote Desktop by name, so that you don’t have to type in the IP address and port number every time.
Is VPN safe for remote desktop?
It is not your only option, though.
How to connect to VPN?
Connect to VPN. First, you must connect to Virtual Private Network. Type of sign-in info → your type (in this case, it is login and password). Click on “Save” button. Also, you can get the Touch VPN in Windows Store (it’s free) and use it for a VPN connection.
How to lock your computer?
Now lock your computer. You can do this by pressing CTRL+ALT+DEL and then selecting “Lock the Computer.” Or you can press the Windows + L key.
Is Touch VPN free?
Also, you can get the Touch VPN in Windows Store (it’s free) and use it for a VPN connection.

About Point-To-Site Vpn
Scenario 1 - Users Need Access to Resources in Azure only
- In this scenario, the remote users only need to access to resources that are in Azure. At a high level, the following steps are needed to enable users to connect to Azure resources securely: 1. Create a virtual network gateway (if one does not exist). 2. Configure point-to-site VPN on the gateway. 2.1. For certificate authentication, follow this li...
Scenario 2 - Users Need Access to Resources in Azure and/or On-Prem Resources
- In this scenario, the remote users need to access to resources that are in Azure and in the on premises data center(s). At a high level, the following steps are needed to enable users to connect to Azure resources securely: 1. Create a virtual network gateway (if one does not exist). 2. Configure point-to-site VPN on the gateway (see Scenario 1). 3. Configure a site-to-site tunnel o…
FAQ For Native Azure Certificate Authentication
- How many VPN client endpoints can I have in my point-to-site configuration?
It depends on the gateway SKU. For more information on the number of connections supported, see Gateway SKUs. - What client operating systems can I use with point-to-site?
The following client operating systems are supported: 1. Windows Server 2008 R2 (64-bit only) 2. Windows 8.1 (32-bit and 64-bit) 3. Windows Server 2012 (64-bit only) 4. Windows Server 2012 R2 (64-bit only) 5. Windows Server 2016 (64-bit only) 6. Windows Server 2019 (64-bit only) 7. Windo…
Next Steps