
How to implement an effective remote access policy?
How to Implement an Effective Remote Access Policy | Smartsheet Now called distributed offices, remote work, telework, mobile work, smart work, and. A remote access policy statement, sometimes called a remote access control. have a standard policy in place - as work-life balance, productive and happy.
What are remote access policies?
Types of Remote Access Security Risks
- Permissive Policies of Remote Access. Attackers can quickly acquire access to the rest of the network if they compromise a VPN (virtual private network).
- Remote Devices Control. ...
- Remote Activity with Limited Visibility. ...
- Reusing Passwords. ...
How to create a remote work policy?
What to include in your remote work policy
- Purpose and scope. Start by explaining why you created the policy and who it applies to. ...
- Eligible positions and employees. Even if your business is entirely remote, there may be some eligibility criteria you’ll want to include in your policy.
- Remote work expectations. ...
- Legal considerations for hourly remote employees. ...
- Remote tools, equipment and supplies. ...
How to properly secure remote access?
- Windows or Mac login when connecting remotely
- Request permission to connect to the user’s computer
- Automatically blank the remote screen when connected
- Automatically lock remote computer when disconnected
- Lock the remote computer’s keyboard and mouse while in session
- Lock the streamer settings using Splashtop admin credentials
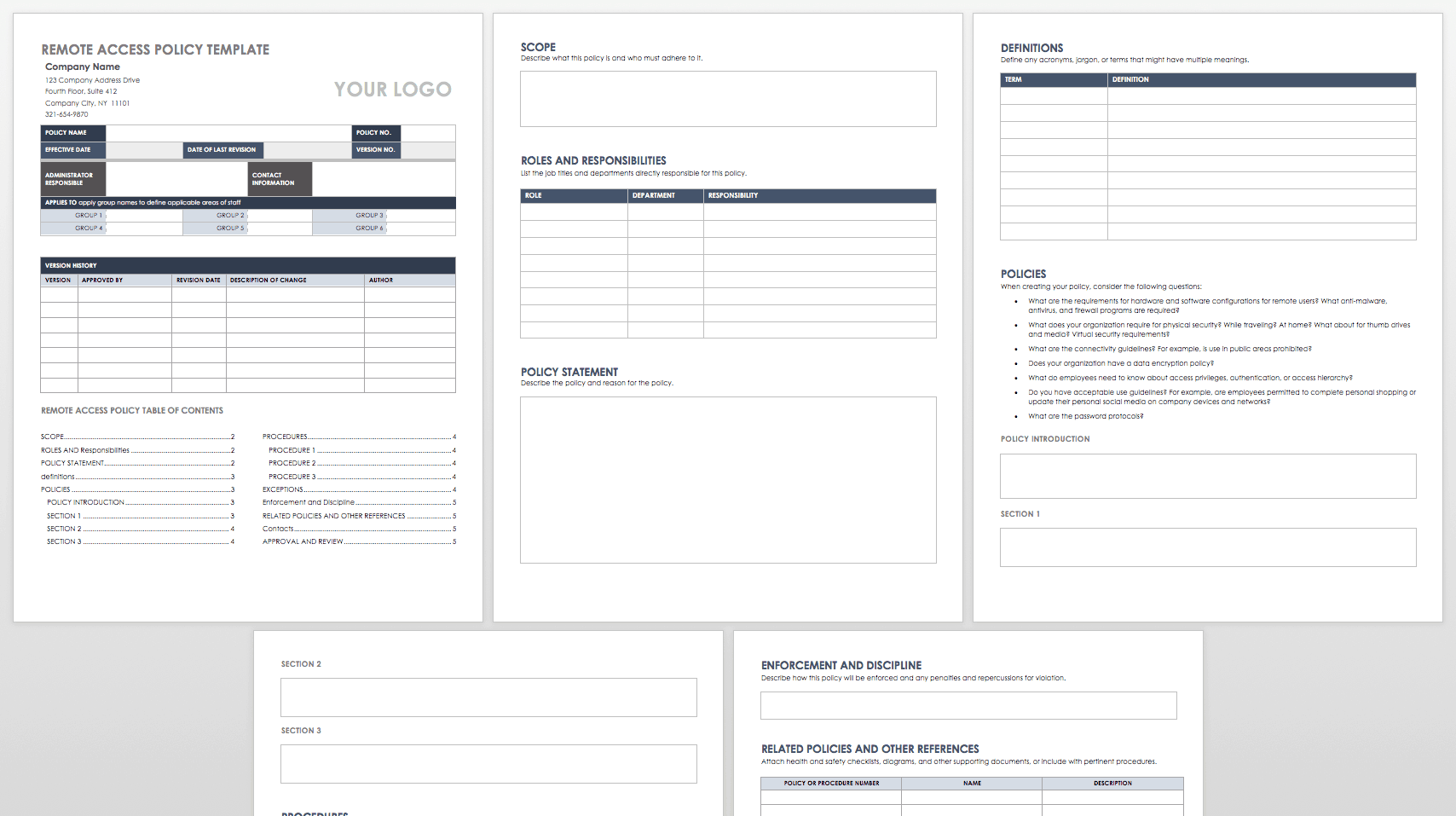
What should be in a remote access policy?
A remote access policy should cover everything—from the types of users who can be given network access from outside the office to device types that can be used when connecting to the network. Once written, employees must sign a remote access policy acceptance form.
What are the examples of remote user security policy best practices?
Best Practices For Remote Access SecurityEnable encryption. ... Install antivirus and anti-malware. ... Ensure all operating systems and applications are up to date. ... Enforce a strong password policy. ... Use Mobile Device Management (MDM) ... Use Virtual Private Network (VPN) ... Use two-factor authentication.More items...•
How a remote access policy may be used and its purpose?
The purpose of a remote access policy is to outline the expectations of those users' behaviors while connecting to your network in an attempt to safeguard that network from viruses, threats or other security incidents.
How do I give permission for remote access?
Right-click on "Computer" and select "Properties". Select "Remote Settings". Select the radio button for "Allow remote connections to this computer". The default for which users can connect to this computer (in addition to the Remote Access Server) is the computer owner or administrator.
How do you keep security when employees work remotely?
Remote Work Security Best PracticesEstablish and enforce a data security policy. ... Equip your employees with the right tools and technology. ... Frequently update your network security systems. ... Regulate the use of personal devices. ... Institute a “Zero Trust” approach. ... Make sure all internet connections are secure.More items...
What is a best practice for compliance in the remote access domain?
Setting up a VPN and requiring all remote connections to pass through it is a basic best practice for keeping resources secure when employees work remotely.
What is a VPN policy?
A VPN security policy is a policy that defines. just about everything that anyone would need to know about your VPN. It defines. things like who can use the VPN, what they can use it for, and what it is that. keeps them from using improperly or maliciously.
Why should an organization have a remote access policy even if IT already has an acceptable use policy AUP for employees?
A remote access policy is vital to ensure that your organization can maintain its cybersecurity protocols even with all the uncertainty that remote access brings: unknown users (you can't see the person, after all), using potentially unknown devices on unknown networks, to access your corporate data center and all the ...
What is an access policy?
n. Principles or procedures that control the conditions under which individuals have permission and ability to consult a repository's holdings.
Do you need admin rights to remote desktop?
To sign in remotely, you need the right to sign in through Remote Desktop Services. By default members of the Administrators group have this right. If the group you're in does not have the right, or if the right has been removed from the Administrators group, you need to be granted the right manually.
What is remote admin access?
Alternatively referred to as remote administration, remote admin is way to control another computer without physically being in front of it. Below are examples of how remote administration could be used. Remotely run a program or copy a file. Remotely connect to another machine to troubleshoot issues.
How do I manage remote desktop users?
Open the system settings by right-clicking the start menu and selecting “System”, choose “Advanced system settings”, select the “Remote” tab, click the “Select Users…” button then click the “Add” button. Now enter the user's name in the text box and click OK.
What security considerations do you think are important for users accessing their company desktops remotely?
These are the top remote work security issues businesses should be wary of.Managing All Devices and Employees.Insecure Passwords.Phishing Emails.Using Unsecured Personal Devices & Networks.Video Attacks.Weak Backup and Recovery Systems.Require employees to connect over VPNs.Install multi-factor authentication.More items...
What can we do in order to limit or prevent remote access?
Firewalls can be your first line of defense in network security by limiting those who have remote access. You should set up firewalls to restrict access using software or hardware or both. Update your software regularly. Make sure your software updates automatically so you're working with the latest security fixes.
What is the responsibility of Connecticut College employees, students, and College Affiliates?
It is the responsibility of Connecticut College employees, students, and College Affiliates with remote access privileges to Connecticut College's campus network to ensure that their remote connection is given the same information security consideration as the user's onsite connection to Connecticut College.
What is the purpose of the Connecticut College network policy?
These standards are designed to minimize the potential security exposure to Connecticut College from damages which may result from unauthorized use of Connecticut College resources. Potential damages include the loss of sensitive or college confidential data, intellectual property, damage to public image, and damage to critical Connecticut College internal systems.
Can you use VPN on a computer in Connecticut?
VPN and general access to the Internet for recreational use by immediate household members through the Connecticut College network on collegeowned computers is prohibited. The Connecticut College employee bears responsibility for the consequences should the access be misused as outlined in section 5.3 Non Compliance.
Can a VPN account be revoked?
For all others, the Vice President of Information Services, may revoke accounts for those who are neither employed nor enrolled in the College.
How long do remote users have to log in?
Remote access must be logged in a central database and kept for a period of at least 30 days. Access logs must be reviewed regularly.
What is remote access in a company name?
Remote access is defined as any connection to [COMPANY NAME]’s internal network from a location outside of any affiliated company offices.
What is the purpose of the Company Name policy?
The intent of this policy is to establish guidelines specifically pertaining to remote access to [COMPANY NAME]’s internal network. Preventing unauthorized access to company data from insecure networks is of utmost importance to [COMPANY NAME]. This policy is designed to ensure remote and/or traveling employees have the ability to securely connect to the corporate network without fear of threat and to provide the Company with an additional means of monitoring and controlling access to the internal network.
Is VPN good for remote employees?
The home networks of most remote employees lack the security provided by a large corporate network, making them sitting ducks for hackers. A VPN puts a strong hedge of protection around their connection, keeping the interactions they have with your internal network – from emails to confidential data access – secure.
Is multifactor authentication required for VPN?
And to make it even stronger, we recommend multi-factor authentication as a requirement for VPN access. Restricted use. Remote access privileges shouldn’t be given out in the office like candy, but rather on an as-needed basis.
Can I use a VPN with another VPN?
Users shall not connect to the [COMPANY NAME] VPN while also using another VPN.
Do authorized users share login credentials?
Authorized users must protect their login credentials and must not share them with anyone for any reason. All inbound connections to [COMPANY NAME] internal networks must pass through an access control point before the user can reach a login banner.
