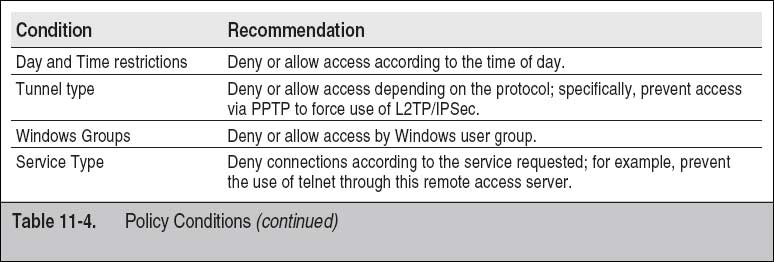
Remote policies have guidelines for access that can include the following:
- Hardware and software configuration standards for remote access, including anti-malware, firewalls, and antivirus
- Encryption policies
- Information security, confidentiality, and email policies
- Physical and virtual device security
- Access privileges, authentication, and access hierarchy
- Password protocols
How to properly secure remote access?
- Windows or Mac login when connecting remotely
- Request permission to connect to the user’s computer
- Automatically blank the remote screen when connected
- Automatically lock remote computer when disconnected
- Lock the remote computer’s keyboard and mouse while in session
- Lock the streamer settings using Splashtop admin credentials
How secure is enabling remote access?
- iOS/Android: Swap album and artist titles in CarPlay/Android Auto.
- iOS/Android: Rare crash if your library had ~200,000 items.
- Desktop: Reduce hover play background size to allow clicking on poster.
- iOS: Crash for high CPU in some cases if server disks were offline.
- CarPlay/Android Auto: Show all albums when album types are enabled.
What are remote access protocols?
WHAT ARE REMOTE ACCESS PROTOCOLS?
- Point-to-Point Protocol (PPP)
- Point-to-Point Tunneling (PPTP)
- IPsec (Internet Protocol Security)
- Layer Two Tunneling Protocol (L2TP)
- Remote Authentication Dial-In User Service (RADIUS)
- Terminal Access Controller Access Control System (TACACS)
What are remote access policies?
Types of Remote Access Security Risks
- Permissive Policies of Remote Access. Attackers can quickly acquire access to the rest of the network if they compromise a VPN (virtual private network).
- Remote Devices Control. ...
- Remote Activity with Limited Visibility. ...
- Reusing Passwords. ...
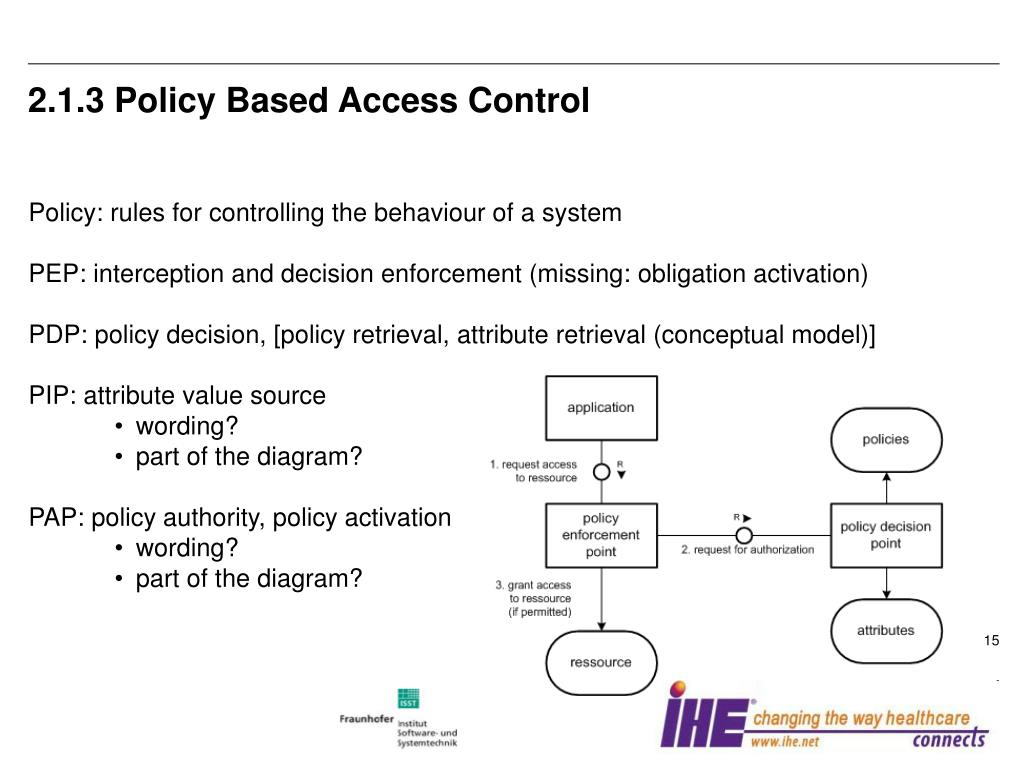
What is a remote access standard?
PURPOSE. Remote Access refers to the ability to access UMW network resources while off campus. Security measures for remote access should be implemented based on sensitivity and risk to University systems and data.
Which is the secure standard function for remote access?
MFA is imperative to authenticate users for secure remote access. Many regulations and compliance standards require MFA for privileged remote access.
What is the importance of remote access policy?
A remote access policy is vital to ensure that your organization can maintain its cybersecurity protocols even with all the uncertainty that remote access brings: unknown users (you can't see the person, after all), using potentially unknown devices on unknown networks, to access your corporate data center and all the ...
What are the examples of remote user security policy best practices?
Best Practices For Remote Access SecurityEnable encryption. ... Install antivirus and anti-malware. ... Ensure all operating systems and applications are up to date. ... Enforce a strong password policy. ... Use Mobile Device Management (MDM) ... Use Virtual Private Network (VPN) ... Use two-factor authentication.More items...•
What is a best practice for compliance in the remote access domain?
Instead, a best practice is to adopt the principle of least privilege, which means that access for all users should be blocked by default and enabled only for the specific accounts that require it. This will require more configuration, but it is well worth the added security benefits.
What are two types of remote access servers?
Remote Access Methods1- Remote Access Server: It's one server in organization network that it is the destination of all remote access connections.2- Remote Access Client: All computers that remote connect to network, called remote access client or remote computer.More items...•
What should be included in an access control policy?
Organizations planning to implement an access control system should consider three abstractions: access control policies, models, and mechanisms. Access control policies are high-level requirements that specify how access is managed and who may access information under what circumstances.
What is a VPN policy?
A VPN security policy is a policy that defines. just about everything that anyone would need to know about your VPN. It defines. things like who can use the VPN, what they can use it for, and what it is that. keeps them from using improperly or maliciously.
Which of the below are correct protocol for remote access?
REMOTE DESKTOP PROTOCOL (RDP)
How do I make remote access secure?
Basic Security Tips for Remote DesktopUse strong passwords.Use Two-factor authentication.Update your software.Restrict access using firewalls.Enable Network Level Authentication.Limit users who can log in using Remote Desktop.
How do you secure remote access to a network?
Use virtual private networks (VPN) - Many remote users will want to connect from insecure Wi-Fi or other untrusted network connections. VPNs can eliminate that risk, however VPN endpoint software must also be kept up-to-date to avoid vulnerabilities that can occur from older versions of the software client.
How do I protect my remote worker?
Here are the top remote working security tips to ensure you and your staff are working from home safely.Use antivirus and internet security software at home. ... Keep family members away from work devices. ... Invest in a sliding webcam cover. ... Use a VPN. ... Use a centralized storage solution. ... Secure your home Wi-Fi.More items...
How do I create a secure remote access?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
What is secure remote communications?
Secure Remote Working is a combination of multiple technologies and procedures comprising: Virtual Private Network (VPN) – Facilitates secure access to on-premises applications and services. VPNs also provide secure internet access for employees on public wireless or third-party corporate networks.
Which is a more secure form of remote access over a network?
Virtual private network (VPN)Virtual private network (VPN) – The most common and well-known form of secure remote access, VPNs typically use the public Internet to connect to a private network resource through an encrypted tunnel.
Why is SSH Secure?
Encryption and integrity The SSH protocol uses industry standard strong encryption algorithms, like AES, to secure the communication between the involved parties. In addition, the protocol uses hashing algorithms, such as SHA-2, to ensure the integrity of the data transmitted.
What is telecommuting?
“Telecommuting,” a term coined in the 1970s, has experienced explosive growth in today’s era of mobile connectivity. Now called distributed offices, remote work, telework, mobile work, smart work, and work shifting, many people are finding flexibility and increased productivity conducting business away from a centralized office environment. Researchers have long studied the benefits of remote work - from the successes that remote work had on traffic reduction during the 1984 Los Angeles Olympics to the 2016 findings by a Gallup survey on the increased hours for remote work.
What devices do remote workers use?
The numerous types of mobile devices and the different ways to connect pose challenges for the IT department. Devices can include cell phones, tablets, laptops, and any other device a remote worker relies on to conduct business.
What is remote access?
Remote access is any connection made to an organization's internal network and systems from an external source by a device or host. Remote locations can be almost anywhere in the world, from the employee’s home to an off-site office, hotels, transportation hubs, and cafes.
What are the risks of using proprietary information?
The hazards to sensitive or proprietary information through unauthorized or inappropriate use can lead to compliance problems, from statutes such as those found in the Health Insurance Portability and Accountability Act (HIPAA) or Payment Card Industry Data Security Standards (PCI DSS).
Is remote access feasible?
There are plenty of advantages to remote access, but there are also instances where remote access is simply not feasible. For example: Organizations with strict, government access restrictions due to sensitive information. Retail and food-service workers. Workers who lack discipline outside of the office.
Is remote work available?
While remote work is not available to or appropriate for everyone, non-self-employed work at home opportunities have grown by 115 percent since 2005 - especially for non-union, college educated, and high wage workers, according to Global Workplace Analytics .
Who is Trave Harmon?
Trave Harmon, CEO of Triton Technologies, implemented a remote access policy in order to effectively allow full-time employees to work remotely around the world. He explained the core tenants of his policy: “We provide managed IT services, 24-hour support, and cloud-based everything.
What is remote work?
Remote work has brought with it a few challenges, including potential computer and network security risks. There is a real need for guidelines surrounding remote access, along with other policies. A remote access policy serves as a guide for remote users connecting to the network. It extends the policies governing network and computer use in ...
What should a remote access policy cover?
To be effective, a remote access policy should cover everything related to network access for remote workers. Organizations must identify which users should be given access, since not everyone may benefit from having the privilege. For example, it might not be a good idea to give remote access to users with access to sensitive data ...
Why is password policy important?
It helps ensure that only those users who need it are given network access, as long as their devices are also compliant with the guidelines. When implemented properly, it helps safeguard the network from potential security threats.
What is RAS in IT?
Parallels® Remote Application Server (RAS) provides secure remote access for your networks out of the box. It features granular permission policies that enable administrators to enforce access restrictions and settings based on the end-users device or Active Directory group, helping ease the workloads of IT administrators by not requiring any further configuration.
What are the considerations when formulating a remote access policy?
Other considerations when formulating a remote access policy include but are not limited to the following: Standardized hardware and software, including firewalls and antivirus/antimalware programs. Data and network encryption standards. Information security and confidentiality. Email usage.
Can you customize remote access policy?
Always ensure that your remote access policy is not an exact copy of another organization’s template; rather, you should customize it depending on your requirements. Otherwise, it might not be that useful for your organization.
What is the responsibility of Connecticut College employees, students, and College Affiliates?
It is the responsibility of Connecticut College employees, students, and College Affiliates with remote access privileges to Connecticut College's campus network to ensure that their remote connection is given the same information security consideration as the user's onsite connection to Connecticut College.
What is the purpose of the Connecticut College network policy?
These standards are designed to minimize the potential security exposure to Connecticut College from damages which may result from unauthorized use of Connecticut College resources. Potential damages include the loss of sensitive or college confidential data, intellectual property, damage to public image, and damage to critical Connecticut College internal systems.
Can you use VPN on a computer in Connecticut?
VPN and general access to the Internet for recreational use by immediate household members through the Connecticut College network on collegeowned computers is prohibited. The Connecticut College employee bears responsibility for the consequences should the access be misused as outlined in section 5.3 Non Compliance.
Can a VPN account be revoked?
For all others, the Vice President of Information Services, may revoke accounts for those who are neither employed nor enrolled in the College.
Purpose
To establish usage and documentation requirements for remote access methods used at the University of Florida.
Standard
Firewalls and other technology will be used to restrict Remote Access to only approved Remote Access mechanisms.
What is the purpose of remote access policy?
Hence, the purpose of this policy is to define standards for connecting to the group’s network from any host. These standards are designed to minimize the potential exposure to the group from damages, which may result from unauthorized use of the group resources. Damages include the loss of sensitive or company confidential data, intellectual property, damage to public image, damage to critical group internal systems, etc.
What is the Organization Group policy?
This policy applies to all Organization Group employees, contractors and vendors with corporate owned computers or workstations used to connect to the Group’s network. This policy applies to remote access connections used to do work on behalf of the Group, including reading or sending email, viewing intranet web resources and network/system/application support.
Can two factor authentication be shared?
Two factor authentication devices (e.g. hardware tokens or smart cards) must not be shared under any circumstances. Users with remote access privileges must ensure that all authentication devices (e.g. hardware tokens or smart cards) must return to IT Security once task completed or the privileges has been revoked.
Does IT Security recommend remote support?
IT Security does not recommend remote support services for such applications to reduce the Groups’ exposure to unnecessary outside threats. However, such application may be allowed remote support services on an ad-hoc basis for a limited time period and approved by the Organization IT Management.