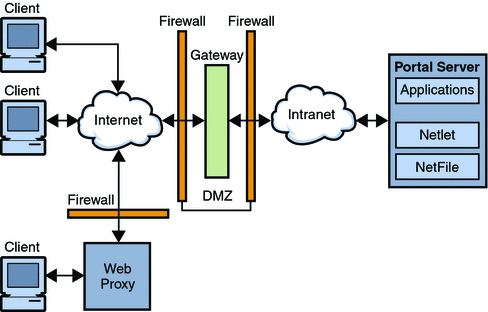
Secure Server Connectivity
- Establish and Use a Secure Connection. When connecting to a remote server, it is essential to establish a secure channel for communication.
- Use SSH Keys Authentication. Instead of a password, you can authenticate an SSH server using a pair of SSH keys, a better alternative to traditional logins.
- Secure File Transfer Protocol. ...
How to secure your remote access?
- In-session file transfer
- Out-of-session file transfer
- Remote print
- Text copy/paste
- Remote wake
- Remote Reboot
- Out-of-session chat
- Session recording
- Concurrent remote sessions
- Remote command
How to protect remote access?
To enable Remote Access in your UniFi Protect application:
- Access the UniFi OS Console hosting Protect via its IP address. ...
- Log in to your Ubiquiti SSO account.
- Go to the System Settings > Advanced menu, and enable the Remote Access toggle.
How secure is enabling remote access?
- iOS/Android: Swap album and artist titles in CarPlay/Android Auto.
- iOS/Android: Rare crash if your library had ~200,000 items.
- Desktop: Reduce hover play background size to allow clicking on poster.
- iOS: Crash for high CPU in some cases if server disks were offline.
- CarPlay/Android Auto: Show all albums when album types are enabled.
What are the risks of remote access?
The Risks and Rewards of Remote Access in your Business
- Benefits of remote access. For your employees, accessing information has never been easier. ...
- The security risks of remote access software. The greatest rewards often come with some risks. ...
- Reduce the risks, enhance the reward. ...
Why is IPSec VPN important?
Why is IPSEC used?
What is client side VPN?
What is IPSEC protocol?
What is remote access VPN?
What is the line of defense for remote access?
Should a company use IPSEC VPN?
See more
About this website

What is remote access security?
Secure remote access refers to any security policy, solution, strategy or process that exists to prevent unauthorized access to your network, its resources, or any confidential or sensitive data. Essentially, secure remote access is a mix of security strategies and not necessarily one specific technology like a VPN.
How do I secure a remote access server?
Basic Security Tips for Remote DesktopUse strong passwords. ... Use Two-factor authentication. ... Update your software. ... Restrict access using firewalls. ... Enable Network Level Authentication. ... Limit users who can log in using Remote Desktop. ... Set an account lockout policy.
Is remote access a security risk?
Despite its many benefits, remote access can expose your business to risks. You will have to manage these risks to keep your remote access secure at all times. Otherwise, your network may become vulnerable and your business data exposed.
Which method of remote access is the most secure?
Implement a Secure Connection for Remote Network AccessWired Connection: A wired connection is the most secure method for remote network access.Home Wi-Fi: The second most secure network connection is using a secured home Wi-Fi connection.More items...•
What are potential risks associated with remote access?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
How secure is RDP over internet?
However, the highest risk is the exposure of RDP on the Internet, port 3389, and allowing it to traverse directly through the firewalls to a target on the internal network. This practice is common and should absolutely be avoided.
Why is RDP so insecure?
RDP itself is not a secure setup and therefore requires additional security measures to keep workstations and servers protected. Without proper security protocols in place, organizations face several potential risks, including the increased risk of cyberattacks.
How do you secure remote access to employees?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
What happens if you give someone remote access to your computer?
This can be even worse than just conning you out of money, as undetected malware can allow hackers to steal your identity, including your passwords and financial information, over and over again, even if you get new passwords and account numbers.
What are two types of remote access servers?
Remote Access Methods1- Remote Access Server: It's one server in organization network that it is the destination of all remote access connections.2- Remote Access Client: All computers that remote connect to network, called remote access client or remote computer.More items...•
Which protocol for remote access is more secure and why?
POINT-TO-POINT TUNNELING PROTOCOL (PPTP) It's used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network. PPTP is a great option because it's simple and secure.
Which protocol is used for encrypted remote access to a server?
IPsec. Internet Protocol security (IPsec) can be used as a remote access tunneling protocol to encrypt traffic going over the Internet.
What are the secure methods the remote users can use to connect to the internal network to perform file operations?
A remote-access VPN allows individual users to establish secure connections with a remote computer network. Those users can access the secure resources on that network as if they were directly plugged in to the network's servers.
Which protocol is used for encrypted remote access to a server?
IPsec. Internet Protocol security (IPsec) can be used as a remote access tunneling protocol to encrypt traffic going over the Internet.
Which option creates a secure connection for remote workers?
The only way to secure your remote workforce is a secure VPN. Employees must connect from their laptops, desktops and mobile devices over a VPN connection. It's the secure, private method for virtually entering the corporate office, so to speak.
Which of the following describes the best way to make sure you are securely accessing the company network remotely?
You should use WPA2 or WPA3 encryption when remotely connecting to a network. WPA2 or WPA3 encryption are the encryption standards that will protect information sent over a wireless network.
How to Secure Remote Access for Employees {Checklist}
How do you maintain security when employees work remotely, and your team is transitioning to a remote workforce? As remote work is becoming a more prevalent trend in business and considering the recent COVID-19 outbreak, there’s no better time for employees and companies alike to make strides in securing remote work.
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
What is the line of defense for remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly.
Why is IPSec VPN important?
IPSec VPN connections are also important for an employee who needs widespread access to the company’s network. A word of warning: If you are using IPSec VPN for remote access, but you are not deploying Internet Key Exchange (IKE, certificates) as an authentication method, the connection will be vulnerable.
Why is IPSEC used?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
What is client side VPN?
The client-side software is responsible for establishing a tunneling connection to the RAS and for the encryption of data. RAS VPNs are appropriate for small companies, requiring a remote access for a few employees. However, most serious businesses have moved on from this basic form of VPN connection.
What is IPSEC protocol?
IPSec: IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect data flows between hosts and security gateways. The unique feature of IPSec is that it operates at the Network Layer of the Open Systems Interconnection (OSI) protocol model.
Should a company use IPSEC VPN?
A company should go for IPSec VPN remote access if it has a strong networking department with the ability to configure each employee’s hardware device individually (installing client software, enforcing security policies etc.).
How to install Remote Access on DirectAccess?
On the DirectAccess server, in the Server Manager console, in the Dashboard, click Add roles and features. Click Next three times to get to the server role selection screen. On the Select Server Roles dialog, select Remote Access, and then click Next.
What group does DirectAccess belong to?
For a client computer to be provisioned to use DirectAccess, it must belong to the selected security group . After DirectAccess is configured, client computers in the security group are provisioned to receive the DirectAccess Group Policy Objects (GPOs) for remote management.
Author: Haris Khan
Remote work is the new normal for IT teams around the globe, and there is no surprise as to why remote work is becoming so increasingly popular for organizations. The modern employee workforce is no longer restricted to one physical location.
What is secure remote access?
Secure remote access refers to the technology used for securely accessing a system or application remotely. Cybercriminals and malicious actors are consistently looking out for vulnerabilities and loopholes in remote work infrastructures to exploit and plan cyber attacks.
Which technologies are used for remote work access?
Secure remote access can be effectively implemented by utilizing a collection of highly innovative, secure, and flexible technologies while accessing a system or application from a remote location A few prominent examples of such technologies are listed below:
10 Best Practices for Secure Remote Work Access
Some of the best practices that you can adopt to improvise remote access security in your organization are described below:
Why cloud desktops are an optimal choice for secure remote access?
Cloud desktop solutions offer greater flexibility and ease of access as all of your files, applications and desktop reside on the cloud. Cloud desktops are one of the most resilient and secure forms of remote access.
All-In-One Secure Remote Access with V2 Cloud
As the organizational trend keeps transitioning to remote work, it’s crucial to comprehend the numerous cybersecurity risks and threats that are associated with remote access security. Remote work has become an increasingly viable option with tons of advantages.
Reimagine Security in the Remote Workplace
Learn how to provide a secure online work environment for your remote employees.
Strengthen your security with an integrated solution
Join us to learn how Microsoft’s end-to-end security solutions can help you provide greater visibility and control over your digital environment.
How to select a server from the server pool?
On the Select destination server page, select the Select a server from the server pool option. Under Server Pool, select the local computer and select Next. On the Select server roles page, in Roles, select Remote Access, then Next. On the Select features page, select Next. On the Remote Access page, select Next.
How to start remote access?
Select Start service to start Remote Access. In the Remote Access MMC, right-click the VPN server, then select Properties. In Properties, select the Security tab and do: a. Select Authentication provider and select RADIUS Authentication.
How to install Remote Access Role in VPN?
On the VPN server, in Server Manager, select Manage and select Add Roles and Features. The Add Roles and Features Wizard opens. On the Before you begin page, select Next.
How many switches do you need to install VPN?
If you are installing the VPN server on a VM, you must create two External virtual switches, one for each physical network adapter; and then create two virtual network adapters for the VM, with each network adapter connected to one virtual switch.
What is NAS in a network?
A NAS is a device that provides some level of access to a larger network. A NAS using a RADIUS infrastructure is also a RADIUS client, sending connection requests and accounting messages to a RADIUS server for authentication, authorization, and accounting. Review the setting for Accounting provider: Table 1.
Can you use a VPN as a RADIUS client?
When you configure the NPS Server on your Organization/Corporate network, you will add this VPN Server as a RADIUS Client. During that configuration, you will use this same shared secret so that the NPS and VPN Servers can communicate. In Add RADIUS Server, review the default settings for: Time-out.
Can you assign a VPN to a pool?
Additionally, configure the server to assign addresses to VPN clients from a static address pool. You can feasibly assign addresses from either a pool or a DHCP server; however, using a DHCP server adds complexity to the design and delivers minimal benefits.
Why use a VPN for remote servers?
When you want to connect to a remote server as if doing it locally through a private network, use a VPN. It enables an entirely secure and private connection and can encompass multiple remote servers.
What is the best way to establish a secure connection?
When connecting to a remote server, it is essential to establish a secure channel for communication. Using the SSH (Secure Shell) Protocol is the best way to establish a protected connection. Unlike the previously used Telnet, SSH access encrypts all data transmitted in the exchange.
What port does SSH use?
By default, SSH uses port 22. Everyone, including hackers, knows this. Most people do not configure this seemingly insignificant detail. However, changing the port number is an easy way to reduce the chances of hackers attacking your server.
Why use intrusion prevention software?
Using intrusion prevention software to monitor login attempts is a way to protect your server against brute force attacks. These automated attacks use a trial-and-error method, attempting every possible combination of letters and numbers to gain access to the system.
How to detect unauthorized activity?
To detect any unauthorized activities, use an intrusion detection system (IDS), such as Sophos , which monitors processes running on your server. You may set it to check day-to-day operations, run periodical automated scans, or decide to run the IDS manually.
Can you authenticate an SSH server with a password?
Instead of a password, you can authenticate an SSH server using a pair of SSH key s, a better alternative to traditional logins. The keys carry many more bits than a password and are not easily cracked by most modern computers. The popular RSA 2048-bit encryption is equivalent to a 617-digit password.
Can you disable root login in SSH?
Every server has a root user who can execute any command. Because of the power it has, the root can be very hazardous to your server if it falls into the wrong hands. It is widespread practice to disable the root login in SSH altogether.
What is unauthorized software?
Unauthorized software is a common entrypoint for ransomware attacks. Monitoring software and integrations is very important, especially when workers are at home with others who may be installing software on their devices.
What is cybersecurity readiness?
Cybersecurity readiness is the ability to identify, prevent, and respond to cyber threats. Yet despite the daily headlines and warnings, organizations struggle to achieve cybersecurity readiness. Just look at the statistics: 78% of... READ MORE ».
What is the first step in mitigating risk throughout your attack surface?
Documenting policies, protocols, and authorized software is the first step in mitigating risk throughout your attack surface. From there, you can start to enforce changes that will improve security performance across your expanding digital ecosystem. 2. Unsecured networks.
Is social engineering easier than phishing?
Social engineering has a new dimension now that employees aren’t in the same physical space. It’s much easier to impersonate a colleague when they’re not sitting next to you, and in the current stressful environment some emotionally driven phishing emails are working better now than ever before.
Why is IPSec VPN important?
IPSec VPN connections are also important for an employee who needs widespread access to the company’s network. A word of warning: If you are using IPSec VPN for remote access, but you are not deploying Internet Key Exchange (IKE, certificates) as an authentication method, the connection will be vulnerable.
Why is IPSEC used?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
What is client side VPN?
The client-side software is responsible for establishing a tunneling connection to the RAS and for the encryption of data. RAS VPNs are appropriate for small companies, requiring a remote access for a few employees. However, most serious businesses have moved on from this basic form of VPN connection.
What is IPSEC protocol?
IPSec: IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect data flows between hosts and security gateways. The unique feature of IPSec is that it operates at the Network Layer of the Open Systems Interconnection (OSI) protocol model.
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
What is the line of defense for remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly.
Should a company use IPSEC VPN?
A company should go for IPSec VPN remote access if it has a strong networking department with the ability to configure each employee’s hardware device individually (installing client software, enforcing security policies etc.).
