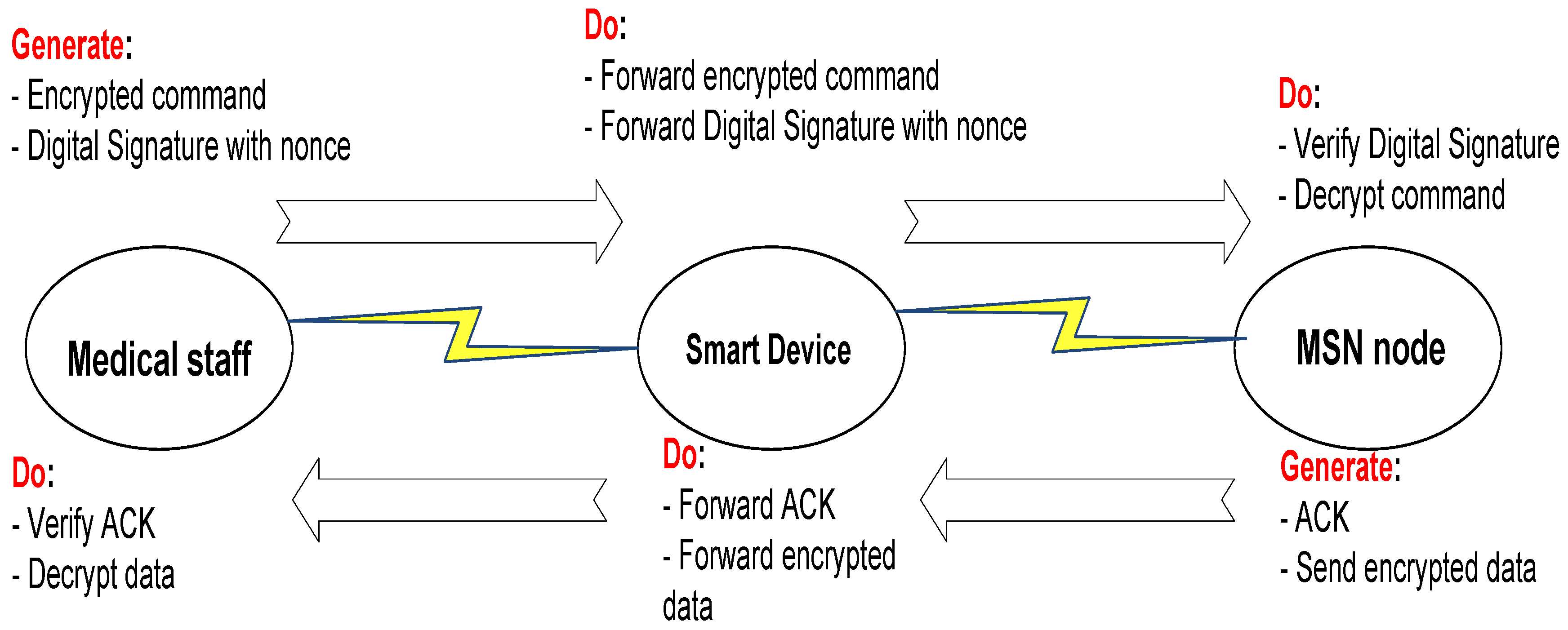
How to use SSH to connect to a remote system?
SSH, or Secure Shell, is a protocol used to securely log onto remote systems. It is the most common way to access remote Linux servers. In this guide, we will discuss how to use SSH to connect to a remote system. Basic Syntax. To connect to a remote system using SSH, we’ll use the ssh command. The most basic form of the command is: ssh remote_host
What is the SSH protocol?
SSH protocol is the standard for strong authentication, secure connection, and encrypted file transfers. We developed it. This page is about the SSH protocol. For the company behind it, see SSH Communications Security. For using the Linux ssh command, see ssh command usage.
How do I connect to device portal using SSH?
Once connected to Device Portal, navigate to the SSH tab in the left-hand pane. The SSH tab is at the bottom of the list. Select Enable SSH. To be able to connect using a username and password, you have to first configure a username and password.
Where can I find the SSH key for my Device?
Where C:\Users\User/.ssh/id_rsa id your private key, user is the username you chose when setting up SSH, and 192.168.1.2 is your Factory OS device's IP address. Enter the password for your user if you're connecting with a username and password, or if you configured your key to require a password.
Is SSH used for remote access?
RDP and SSH are both used to remotely access machines and other servers. They're both essential for securely accessing cloud-based servers, and aid remote employees in leveraging infrastructure on-prem as well.
What is SSH remote protocol?
SSH or Secure Shell is a network communication protocol that enables two computers to communicate (c.f http or hypertext transfer protocol, which is the protocol used to transfer hypertext such as web pages) and share data.
What is SSH protocol and how it works?
SSH refers to the protocol by which network communications can take place safely and remotely via an unsecured network. SSH enables a variety of crucial functions: protected file transfers, automated processes, command execution, and remote access to private network systems, devices, and applications.
Does SSH use TCP or UDP?
The SSH protocol uses or has used 22/UDP for tunneling control through TCP. If decoded properly via Wireshark and you are tunneling a connection through via either ssh-agent or tunneling remotely or locally you would notice that UDP is encapsulated within the TCP segments.
Why do we need SSH?
SSH encrypts and authenticates all connections. SSH provides IT and information security (infosec) professionals with a secure mechanism to manage SSH clients remotely. Rather than requiring password authentication to initialize a connection between an SSH client and server, SSH authenticates the devices themselves.
How does SSH authenticate a user?
The SSH key pair is used to authenticate the identity of a user or process that wants to access a remote system using the SSH protocol. The public key is used by both the user and the remote server to encrypt messages. On the remote server side, it is saved in a file that contains a list of all authorized public keys.
What happens when you SSH in a remote host?
An SSH client is an application you install on the computer which you will use to connect to another computer or a server. The client uses the provided remote host information to initiate the connection and if the credentials are verified, establishes the encrypted connection.
What is difference between SSL and SSH?
The key difference between SSH vs SSL is that SSH is used for creating a secure tunnel to another computer from which you can issue commands, transfer data, etc. On the other end, SSL is used for securely transferring data between two parties – it does not let you issue commands as you can with SSH.
How do I access SSH?
Type the host name or IP address of the SSH server into the “Host name (or IP address)” box. Ensure the port number in the “Port” box matches the port number the SSH server requires. SSH servers use port 22 by default, but servers are often configured to use other port numbers instead. Click “Open” to connect.
What security does SSH use?
The SSH protocol uses industry standard strong encryption algorithms, like AES, to secure the communication between the involved parties. In addition, the protocol uses hashing algorithms, such as SHA-2, to ensure the integrity of the data transmitted.
What TCP port does SSH always listen on?
TCP port 22SSH uses TCP/IP as its transport mechanism, usually TCP port 22 on the server machine, as it encrypts and decrypts the traffic passing over the connection.
What encryption does SSH use?
SSH uses asymmetric encryption in a few different places. During the initial key exchange process used to set up the symmetrical encryption (used to encrypt the session), asymmetrical encryption is used.
What is the difference between SSL and SSH?
The key difference between SSH vs SSL is that SSH is used for creating a secure tunnel to another computer from which you can issue commands, transfer data, etc. On the other end, SSL is used for securely transferring data between two parties – it does not let you issue commands as you can with SSH.
What is SSH and TCP?
SSH. Telnet is the standard TCP/IP protocol for virtual terminal service. It enables you to establish a connection to a remote system in such a manner that it appears as a local system. SSH or Secure Shell is a program to log into another computer over a network to execute commands in a remote machine.
What is the difference between https and SSH?
Any time someone uses a website with a URL that starts with HTTPS, he is on a site with SSL/TLS. SSH is for securely executing commands on a server. SSL is used for securely communicating personal information. SSH uses a username/password authentication system to establish a secure connection.
What is the difference between SSH and sshd?
SSHD is a server ( Analogous to a web server serving https) SSH is a client (Analogous to a browser). In order to work, a compatible set of protocols and authentication mechanisms need to be negotiated. Generally the server defines what it will accept, and the client negotiates the best common protocol.
What is SSH protocol?
When it was first developed, SSH sought to address the security lapses of Telnet, a protocol that allows one computer to log into another on the same open network. In its original form, distinguished as SSH-1, secure shell protocol made great leaps in networking operation security but had a few notable design vulnerabilities.
What is SSH in a network?
SSH refers to the protocol by which network communications can take place safely and remotely via an unsecured network. SSH enables a variety of crucial functions: protected file transfers, automated processes, command execution, and remote access to private network systems, devices, and applications.
What port does SSH use?
SSH protocol’s default settings are to listen on TCP port 22 for connections.
How does SSH work?
SSH works within a network through a client/server architecture. An SSH client is the program that runs SSH protocol from a specific device in order to access remote machines, automate data transfers, issue commands, and even manage network infrastructure. The client/server model means that the network system components being used ...
What is asymmetrical key authentication?
An asymmetrical key authentication method relies on SSH key pairs, which do not require a password and thus avoid the possibility of exploitation. In a host-based system, the host has authenticated its clients and essentially vouches for them.
What is user authorization?
User authorization can take several forms. The client sends a user authentication service request that specifies the method of authentication—asymmetrical key authentication, passwords, or host-based verification. Many SSH users depend on the password method, which is completely acceptable in some environments.
What is a shared master key?
The end result is a shared master key that can be used by both client and host to encrypt and decrypt data.
Getting Started With SSH
By default, most Linux systems include the ssh client and server applications. The packages that include ssh tools in RHEL and Fedora distributions are openssh, openssh-server, and openssh-client. Use the grep command to fetch ssh tools from the installed list:
How to Use SSH Client Tools
Among many other tools to utilize SSH protocol for Linux system remote access, the most frequently used are the ssh command for remote code execution and log in, where scp and rsync are useful in copying one or more files between the client and server.
Getting to Know SSH
The article is a guide for the most widely used protocol for remote management of Linux servers. We display how to use the most important SSH commands with some tips and tricks to ease the task of file copy and management.
What is remote access protocol?
A remote access protocol is responsible for managing the connection between a remote access server and a remote computer. It’s necessary for desktop sharing and remote access for help desk activities. The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), ...
What is PPP protocol?
PPP is a remote access protocol that allows you to implement TCP/IP. It establishes a connection via point-to-point links (i.e., dedicated leased lines and dial-up). PPP is used most often for remote connections to LANs and ISPs. PPP utilizes the Link Control Protocol (LCP), which tests the link between client and PPP host ...
How to use PPTP?
To use PPTP, you’ll have to set up a PPP session between the server and the client, usually over the internet. Once the session is established, you’ll create a second dial-up session. This dial-up session will use PPTP to dial through the existing PPP session.
What is PPTP in a network?
PPTP is a remote access protocol, based on PPP, created by Microsoft. It’s used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network.
What is RDP in Citrix?
Finally, there is the RDP, which is very similar to the Independent Computing Architecture (ICA) protocol used by Citrix products. RDP is utilized to access Windows Terminal Services, which is a close relative of the product line provided by Citrix WinFrame.
What is managed services provider?
As a managed services provider (MSP), you likely already work with remote access protocols on a daily basis. But learning how to best explain the various types of remote access protocols and their advantages and disadvantages to customers is critical in helping them understand your decisions—and why they should trust you and your services.
Is RDP the same as ICA?
RDP offers the same core functions as ICA, although there are some limitations. RDP provides remote access for Windows clients only, while ICA can provide access for numerous platforms. ICA also offers support for automatic client updates, publishing an app to a web browser, and more.
How to enable SSH on a PC?
Open a browser on your technician PC and navigate to the URL of your Factory OS device. Once connected to Device Portal, navigate to the SSH tab in the left-hand pane. The SSH tab is at the bottom of the list. Select Enable SSH.
What is OpenSSH in FTP?
OpenSSH (Secure Shell) is a standard protocol for secure terminal connections. You can use SSH to connect to all Factory OS images.
Can I use SSH to transfer files?
You can use SSH for file transfer, over the sftp protocol. If you've enabled SSH on your Factory OS device, you'll also be able to connect with sftp. WinSCP is the most popular GUI Client for file transfer over sftp in Windows. Follow the documentation to learn how to use it.
What is SSH protocol?
SSH (Secure Shell) is a protocol which define how to connect securely over a network. The catch us Securely. Unlike telnet which is not secure, SSH protocol provides the three main concepts of security; authentication- Authentication to reliably determine the identity of the connecting computer. confidentiality (via encryption) ...
What is SSH encryption?
confidentiality (via encryption) – , encryption to scramble data so that only the intended recipient can read it. integrity of data transfer over a network – to guarantees the data sent over the network is not changed along the way by a third party. SSH has two main versions, SSH1 and SSH2.
Does SSH2 use TCP?
SSH uses TCP as its transport layer protocol and uses well-known port number 22. Now, to allow Telnet or SSH access to any device like a router or a switch, the device needs an IP address.
What is remote access software?
A remote access software is a tool that allows you to access another computer from a remote location. From there, you can now access files, use apps, and even perform administrative tasks on the remote computer as if you’re in front of it.
Is VPN a security risk?
While a Virtual Private Network or VPN is one of the most sought-after remote access solutions at the moment, it can still pose a few security risks for your organization. A VPN can still be exposed to a bunch of security threats outside of a company’s network.
Can remote desktop access restrict access to sensitive data?
Remote Desktop Access software also can restrict users to access sensitive and confidential data. You can also disable file transfer features on remote access software when there’s no reason for your employees to do so.
Can a VPN be exposed to a security threat?
A VPN can still be exposed to a bunch of security threats outside of a company’s network. A report from Trustwave found that the majority of the data breaches it investigated in 2011 were associated with a VPN connection. One alternative option for a VPN is remote access software. A remote access software is a tool that allows you ...

CORE Syntax
- To connect to a remote system using SSH, we’ll use the sshcommand. If you are using Windows, you’ll need to install a version of OpenSSH in order to be able to ssh from a terminal. If you prefer to work in PowerShell, you can follow Microsoft’s documentation to add OpenSSH to PowerShell. If you would rather have a full Linux environment available, ...
How Does Ssh Work?
- SSH works by connecting a client program to an ssh server, called sshd. In the previous section, ssh was the client program. The ssh server was already running on the remote_hostthat we specified. On nearly all Linux environments, the sshdserver should start automatically. If it is not running for any reason, you may need to temporarily access your server through a web-based co…
How to Configure Ssh
- When you change the configuration of SSH, you are changing the settings of the sshd server. In Ubuntu, the main sshd configuration file is located at /etc/ssh/sshd_config. Back up the current version of this file before editing: Open it using nanoor your favourite text editor: You will want to leave most of the options in this file alone. However, there are a few you may want to take a loo…
How to Log Into Ssh with Keys
- While it is helpful to be able to log in to a remote system using passwords, it is faster and more secure to set up key-based authentication.
Client-Side Options
- There are a number of optional flags that you can provide when connecting through SSH. Some of these may be necessary to match the settings in the remote host’s sshdconfiguration. For instance, if you changed the port number in your sshdconfiguration, you will need to match that port on the client-side by typing: If you only want to execute a single command on a remote syst…
Disabling Password Authentication
- If you have created SSH keys, you can enhance your server’s security by disabling password-only authentication. Apart from the console, the only way to log into your server will be through the private key that pairs with the public key you have installed on the server. As root or user with sudo privileges, open the sshdconfiguration file: Locate the line that reads Password Authentica…
Conclusion
- Learning your way around SSH will greatly benefit any of your future cloud computing endeavours. As you use the various options, you will discover more advanced functionality that can make your life easier. SSH has remained popular because it is secure, light-weight, and useful in diverse situations. Next, you may want to learn about working with SFTPto perform command line file tr…