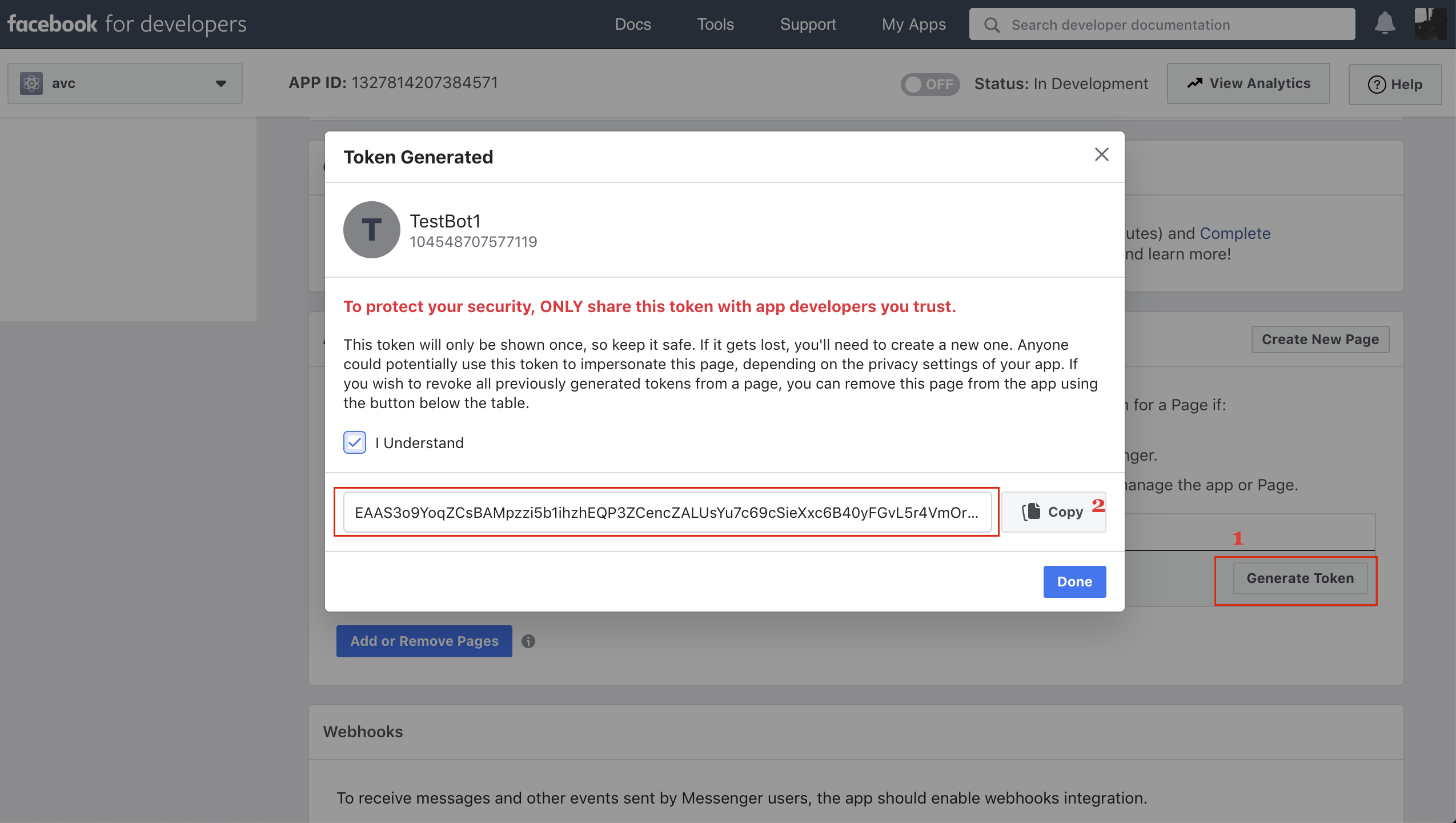
How to create an access token?
Quickstart: Create and manage access tokens
- Prerequisites. An Azure account with an active subscription. ...
- Final code. Find the finalized code for this quickstart on GitHub.
- Set up your environment. ...
- Authenticate the client. ...
- Create an identity. ...
- Issue access tokens. ...
- Create an identity and issue a token in the same request. ...
- Refresh access tokens. ...
- Revoke access tokens. ...
- Delete an identity. ...
How to retrieve the access token?
To request the token, you will need the following values from your app's registration:
- The name of your Azure AD domain. Retrieve this value from the Overview page of your Azure Active Directory.
- The tenant (or directory) ID. Retrieve this value from the Overview page of your app registration.
- The client (or application) ID. ...
- The client redirection URI. ...
- The value of the client secret. ...
How to create remote access trojan?
Remote Access Trojan Examples
- Back Orifice. Back Orifice (BO) rootkit is one of the best-known examples of a RAT. ...
- Sakula. Sakula, also known as Sakurel and VIPER, is another remote access trojan that first surfaced in November 2012.
- Sub7. Sub7, also known as SubSeven or Sub7Server, is a RAT botnet. ...
- PoisonIvy. ...
- DarkComet. ...
How to get access token through authorization token?
Required parameters
- response_type - Must be set to the value token.
- client_id - The client ID of a registered developer app.
- redirect_uri - This parameter is mandatory if a Callback URI was not provided when the client developer app was registered. ...

What is a remote access token?
In computer systems, an access token contains the security credentials for a login session and identifies the user, the user's groups, the user's privileges, and, in some cases, a particular application.
How do I get access token?
Basic stepsObtain OAuth 2.0 credentials from the Google API Console. ... Obtain an access token from the Google Authorization Server. ... Examine scopes of access granted by the user. ... Send the access token to an API. ... Refresh the access token, if necessary.
What is access token example?
Access tokens are used in token-based authentication to allow an application to access an API. For example, a Calendar application needs access to a Calendar API in the cloud so that it can read the user's scheduled events and create new events.
How do remote tokens work?
How do tokens work? In many cases, tokens are created via dongles or key fobs that generate a new authentication token every 60 seconds in accordance with a known algorithm. Due to the power these hardware devices hold, users are required to keep them safe at all times to ensure they don't fall into the wrong hands.
How do I find my token username and password?
You can obtain an access token by providing the resource owner's username and password as an authorization grant. It requires the base64 encoded string of the consumer-key:consumer-secret combination. You need to meet the following prerequisites before using the Token API to generate a token.
How do I generate tokens?
Creating a tokenVerify your email address, if it hasn't been verified yet.In the upper-right corner of any page, click your profile photo, then click Settings.In the left sidebar, click Developer settings.In the left sidebar, click Personal access tokens.Click Generate new token.Give your token a descriptive name.More items...
What is the use of tokens?
Tokens can be used for investment purposes, to store value, or to make purchases. Cryptocurrencies are digital currencies used to facilitate transactions (making and receiving payments) along the blockchain. Altcoins and crypto tokens are types of cryptocurrencies with different functions.
What is a token in API?
An API token is similar to a password and allows you to authenticate to Dataverse Software APIs to perform actions as you. Many Dataverse Software APIs require the use of an API token.
Which is better JWT or OAuth?
OAuth2 is very flexible. JWT implementation is very easy and does not take long to implement. If your application needs this sort of flexibility, you should go with OAuth2. But if you don't need this use-case scenario, implementing OAuth2 is a waste of time.
What is an RSA device?
An RSA SecurID device is a small, portable, electronic device that can be attached easily to a keychain. Every 60 seconds the device generates and displays a unique, random numeric passcode. If you have an RSA SecurID device from Wells Fargo, you can use codes from your device when Advanced Access is required.
Why do we need token based authentication?
Token-based authentication is a protocol that generates encrypted security tokens. It enables users to verify their identity to websites, which then generates a unique encrypted authentication token.
What should access token contain?
Access tokens contain the following information:The security identifier (SID) for the user's account.SIDs for the groups of which the user is a member.A logon SID that identifies the current logon session.A list of the privileges held by either the user or the user's groups.An owner SID.The SID for the primary group.More items...•
What is access token and ID token?
Access tokens are what the OAuth client uses to make requests to an API. The access token is meant to be read and validated by the API. An ID token contains information about what happened when a user authenticated, and is intended to be read by the OAuth client.
What is Access Bank token?
The Access Bank token is a security device that allows generating encrypted codes needed to perform online and internet banking transactions. The Access Bank token number gives you access to initiate various transactions on the Access online banking platform.
What is a security token?
The security token is a small electronic device designed for secure two-factor authentication of users, generation and storage of encryption keys,...
What are security tokens used for?
Security tokens are used as intellectual key carriers and means of electronic signature in PKI systems, in systems of legally significant electroni...
How does a USB security token work?
USB security tokens protect computing resources via two-factor authentication. This type of security requires that two conditions are met when enac...
Token service REST API
To create access tokens, the Secure Token Service provides a single REST API. The URL for the STS service depends on the account domain of the remote rendering account. It is in the form https://sts. [account domain], e.g. https://sts.southcentralus.mixedreality.azure.com
Getting a token using PowerShell
The PowerShell code below demonstrates how to send the necessary REST request to the STS. It then prints the token to the PowerShell prompt.
What is an access token?
An access token is an object encapsulating the security identity of a process or thread. A token is used to make security decisions and to store tamper-proof information about some system entity. While a token is generally used to represent only security information, it is capable of holding additional free-form data that can be attached while the token is being created. Tokens can be duplicated without special privilege, for example to create a new token with lower levels of access rights to restrict the access of a launched application. An access token is used by Windows when a process or thread tries to interact with objects that have security descriptors ( securable objects ). In Windows, an access token is represented by the system object of type Token .
What is primary token?
Primary tokens can only be associated to processes, and they represent a process's security subject. The creation of primary tokens and their association to processes are both privileged operations, requiring two different privileges in the name of privilege separation - the typical scenario sees the authentication service creating the token, and a logon service associating it to the user's operating system shell. Processes initially inherit a copy of the parent process's primary token.
Can you duplicate a token?
Tokens can be duplicated without special privilege, for example to create a new token with lower levels of access rights to restrict the access of a launched application. An access token is used by Windows when a process or thread tries to interact with objects that have security descriptors ( securable objects ).
Can you use a token in more than one organization?
If you have more than one organization, you can also select the organization where you want to use the token. Select the scopes for this token to authorize for your specific tasks. For example, to create a token to enable a build and release agent to authenticate, limit your token's scope to Agent Pools (read, manage).
Can you use Pats with Azure AD?
But, if you're working with third-party tools that don't support Microsoft or Azure AD accounts – or you don 't want to provide your primary credentials to the tool – you can make use of PATs to limit your risk. PATs are easy to create when you need them and easy to revoke when you don’t.
What is Excellian EHR?
Excellian ® is one of the most comprehensive electronic health record (EHR) systems in the nation. For technical assistance, call 612-262-1900 or 1-800-315-4085.
Can I use Excellian from a remote location?
When accessing Excellian from a remote location, providers will be able to do everything in Excellian that they would do if they were using Excellian at an Allina Health facility (i.e., chart, orders, etc). Remote access does not replace a clinic's current practice management (e.g. billing) or clinical system.
How to use RSA token?
1. Go to https://login.microsoftonline.com/ . Enter your work email address to be directed to the Single Sign-On page. 2. Enter your work email address and password. Click Sign In. 3. Enter your RSA SecurID passcode followed by the token code. Do not put any spaces or dashes between your PIN number and the Token code.
How many digits are in a hard token?
Your Hard Token generates a random, six-digit passcode every sixty seconds, also known as a Token code. Your Token Passcode is your PIN followed the Token code (the six random digits) from the hard Token, with no spaces between them.
How to add a PIN to Outlook?
Note: Android device users may be prompted to create an 8-digit PIN when installing the App.#N#2. Enter your work email address and click Add Account .#N#3. Enter your work email address and password . (This is the same email you use to log onto your work computer.) Then click Sign In.#N#4. Enter your RSA SecurID Passcode. This number is your Personal Identification Number (PIN) followed by the dynamic Token code found on your hardware Token. Do not put any spaces or dashes between your PIN number and the Token code.
To avoid handing over "the keys to the castle"..
Note that sigmavirus24's response requires you to give Travis a token with fairly wide permissions -- since GitHub only offers tokens with wide scopes like "write all my public repos" or "write all my private repos".
Step 1: Get the access token
Go to this link: https://github.com/settings/tokens. And generate the token there. Or from you Github account, Go to: Settings -> Developer Settings -> Personal Access Tokens
Step 1
git remote add origin https://<access-token-name>:<access-token>@gitlab.com/path/to/project.git