How to create an access token?
Quickstart: Create and manage access tokens
- Prerequisites. An Azure account with an active subscription. ...
- Final code. Find the finalized code for this quickstart on GitHub.
- Set up your environment. ...
- Authenticate the client. ...
- Create an identity. ...
- Issue access tokens. ...
- Create an identity and issue a token in the same request. ...
- Refresh access tokens. ...
- Revoke access tokens. ...
- Delete an identity. ...
How to retrieve the access token?
To request the token, you will need the following values from your app's registration:
- The name of your Azure AD domain. Retrieve this value from the Overview page of your Azure Active Directory.
- The tenant (or directory) ID. Retrieve this value from the Overview page of your app registration.
- The client (or application) ID. ...
- The client redirection URI. ...
- The value of the client secret. ...
How to create remote access trojan?
Remote Access Trojan Examples
- Back Orifice. Back Orifice (BO) rootkit is one of the best-known examples of a RAT. ...
- Sakula. Sakula, also known as Sakurel and VIPER, is another remote access trojan that first surfaced in November 2012.
- Sub7. Sub7, also known as SubSeven or Sub7Server, is a RAT botnet. ...
- PoisonIvy. ...
- DarkComet. ...
How to get access token through authorization token?
Required parameters
- response_type - Must be set to the value token.
- client_id - The client ID of a registered developer app.
- redirect_uri - This parameter is mandatory if a Callback URI was not provided when the client developer app was registered. ...

What is a remote access token?
In computer systems, an access token contains the security credentials for a login session and identifies the user, the user's groups, the user's privileges, and, in some cases, a particular application.
What are access tokens used for?
Access tokens are used in token-based authentication to allow an application to access an API. The application receives an access token after a user successfully authenticates and authorizes access, then passes the access token as a credential when it calls the target API.
How do remote tokens work?
How do tokens work? In many cases, tokens are created via dongles or key fobs that generate a new authentication token every 60 seconds in accordance with a known algorithm. Due to the power these hardware devices hold, users are required to keep them safe at all times to ensure they don't fall into the wrong hands.
What makes up an access token?
An access token is a tiny piece of code that contains a large amount of data. Information about the user, permissions, groups, and timeframes is embedded within one token that passes from a server to a user's device. Plenty of websites use access tokens.
Where are access tokens stored?
After your frontend received the token, it will be attached to every single HTTP request you make in the future. So you need to store it somewhere. The easiest is to put it into the application state.
How do I get access token?
Obtain User Access TokenGo to Graph API Explorer.In Facebook App, select an app used to obtain the access token.In User or Page, select User Token.Under Permissions, check ads_read .Click Generate Access Token. The box on top of the button is populated with the access token.Store that token for later use.
What are VPN tokens?
A VPN token is a type of security mechanism that is used to authenticate a user or device on a VPN infrastructure. A VPN token works similarly to a standard security token. It primarily provides an additional layer of authentication and security within a VPN.
What are tokens in API?
API tokens allow a user to authenticate with cloud apps and bypass two-step verification and SSO, and retrieve data from the instance through REST APIs. Token controls allow admins to view and revoke the use of API tokens by their managed accounts.
What are the best security tokens?
Best 5 Security Token Issuance BlockchainsPolymath. Polymath is branding itself as the Ethereum for security tokens. ... Securitize. Securitize is another blockchain platform that provides an end-to-end platform for issuers that are seeking to tokenize assets. ... Harbor. ... Swarm. ... Securrency.
How do I generate tokens?
Creating a tokenVerify your email address, if it hasn't been verified yet.In the upper-right corner of any page, click your profile photo, then click Settings.In the left sidebar, click Developer settings.In the left sidebar, click Personal access tokens.Click Generate new token.Give your token a descriptive name.More items...
Which is better JWT or OAuth?
OAuth2 is very flexible. JWT implementation is very easy and does not take long to implement. If your application needs this sort of flexibility, you should go with OAuth2. But if you don't need this use-case scenario, implementing OAuth2 is a waste of time.
Does Facebook use JWT?
It provides an entry point: “/auth/facebook” that redirects to FBs and proceeds to the authentication. After that it acquires the AccessToken for the logged user and creates a JWT Token that returns to the client.
What is the difference between ID token and access token?
Access tokens are what the OAuth client uses to make requests to an API. The access token is meant to be read and validated by the API. An ID token contains information about what happened when a user authenticated, and is intended to be read by the OAuth client.
How use OAuth access token?
Using OAuth 2. 0 to Access Google APIsObtain OAuth 2. 0 credentials from the Google API Console.Obtain an access token from the Google Authorization Server.Examine scopes of access granted by the user.Send the access token to an API.Refresh the access token, if necessary.
What is a security token?
The security token is a small electronic device designed for secure two-factor authentication of users, generation and storage of encryption keys,...
What are security tokens used for?
Security tokens are used as intellectual key carriers and means of electronic signature in PKI systems, in systems of legally significant electroni...
How does a USB security token work?
USB security tokens protect computing resources via two-factor authentication. This type of security requires that two conditions are met when enac...
How long does a token last in REST?
These tokens are issued by the Secure Token Service (STS) in exchange for an account key. Tokens have a lifetime of 24 hours and thus can be issued to users without giving them full access to the service.
Can you copy and paste tokens in a script?
The script just prints the token to the output, from where you can copy & paste it. For a real project, you should automate this process.
What platforms can Redcentric software tokens be installed on?
Our token software can be installed on a wide range of operating systems, such as Mac OSX, Apple IOS, Android, Windows or Blackberry.
How many digits are in a hard token?
Hard tokens are the old key fobs with ten digits on, you punch in a 4-6-digit pin and it then produces a code which you enter into your client.
What is Redcentric shared platform?
The Redcentric shared platform is built on Cisco and Gemalto technology who are both market leaders in the security sector. In short, we use best of breed technology to deliver our remote access solutions.
How many users are needed for Redcentric?
For the Redcentric shared platform and dedicated platform, minimum order is 10 users.
What can Redcentric offer?
A customer shared platform which is highly scalable and can support thousands of users and is resilient by design. This is very similar to the BT remote access token platform and is suited for remote users who need access to HSCN.
How to edit a token in Access?
Under Security, select Personal access tokens. Select the token for which you want to modify, and then select Edit.
How to keep tokens secure?
To keep your token more secure, use credential managers so you don't have to enter your credentials every time. We recommend the following credential manager:
How to revoke a token in Windows 10?
Under Security, select Personal access tokens. Select the token for which you want to revoke access, and then select Rev oke.
What is a token in a PAT?
Your token is your identity and represents you when it's used. Treat and use a PAT like your password.
When is it a good time to switch from basic auth to OAuth?
When your code is working, it's a good time to switch from basic auth to OAuth.
Can you use a token in more than one organization?
If you have more than one organization, you can also select the organization where you want to use the token. Select the scopes for this token to authorize for your specific tasks. For example, to create a token to enable a build and release agent to authenticate, limit your token's scope to Agent Pools (read, manage).
Can you use Pats with Azure AD?
But, if you're working with third-party tools that don't support Microsoft or Azure AD accounts – or you don 't want to provide your primary credentials to the tool – you can make use of PATs to limit your risk. PATs are easy to create when you need them and easy to revoke when you don’t.
What is RSA token?
An activated RSA SecurID authentication token will enable you to access programs such as the Outlook Web Application (OWA), Office 365 (O365) products including SharePoint, and Virtual Desktop Infrastructure (VDI).
How to change my NY token?
Log in to https://mytoken.ny.gov/ and request a new Token. You must mention that you are replacing your existing Token. You are only allowed one Token at any given time.
What is RSA SecurID?
RSA SecurID is a multi-factor authentication technology that is used to protect network services. The RSA SecurID authentication mechanism consists of an assigned hardware or software "token" that generates a dynamic authentication number code at fixed intervals. Users provide the unique number code when logging into a protected service from any network outside the State network.
How many digits are in a soft token?
For a Software Token, your Token Passcode is the eight-digit number generated after entering your PIN on the RSA App. On your Soft token, the passcode refreshes every sixty seconds. If you have difficulty logging in after providing the passcode, ensure the correct PIN was entered.
What to do if you enter too many passcodes?
After entering too many incorrect passcodes, you may be required to enter a next Token code. If using a Soft Token, wait and then enter the next available passcode shown. If using a Hard Token, wait and then enter the next available Token code shown (random 6 digits). Do NOT enter PIN + Token code.
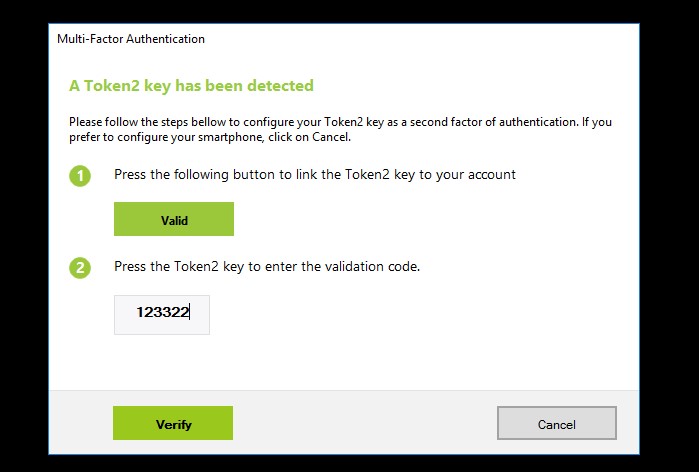
What is multi factor authentication?
Multi-Factor authentication (MFA) is a security system that requires more than one method of authentication from independent categories of credentials to verify the user's identity for a login.
What is ITS working remotely?
To work remotely is to access your agency's network while you are away from your primary workstation. This site contains resources and common troubleshooting tips to support individuals who may be working remotely.
Do you have to rm the remote?
You don't have to rm the remote, you can use set-url instead, as in git remote set-url origin https://scuzzlebuzzle:<MYTOKEN>@github.com/scuzzlebuzzle/ol3-1.git
Is a token a password?
Warning: Tokens have read/write access and should be treated like passwords. If you enter your token into the clone URL when cloning or adding a remote, Git writes it to your .git/config file in plain text, which is a security risk.
Can you authenticate with github?
As of 2021-Aug-28, github CLI can be used to authenticate (no need to generating PAT, can directly login with password if browser can be opened). Checkout: github.com/cli/cli#installation, cli.github.com/manual/gh_auth_login