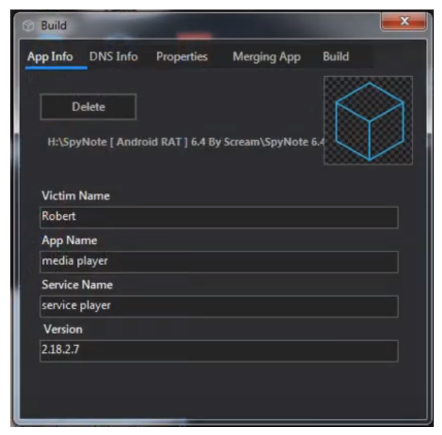
Remote Access Trojan Examples
- Back Orifice. Back Orifice (BO) rootkit is one of the best-known examples of a RAT. It was made by a hacker group...
- Sakula. Sakula, also known as Sakurel and VIPER, is another remote access trojan that first surfaced in November 2012.
- Sub7. Sub7, also known as SubSeven or Sub7Server, is a RAT botnet. Its name was derived by...
How to create remote access trojan?
What is a worm?
- Install backdoors on the victim’s computers. The created backdoor may be used to create zombie computers that are used to send spam emails, perform distributed denial of service attacks, etc. ...
- Worms may also slowdown the network by consuming the bandwidth as they replicate.
- Install harmful payload code carried within the worm.
What is remote access and how can I use it?
Windows 10 Fall Creator Update (1709) or later
- On the device you want to connect to, select Start and then click the Settings icon on the left.
- Select the System group followed by the Remote Desktop item.
- Use the slider to enable Remote Desktop.
- It is also recommended to keep the PC awake and discoverable to facilitate connections. ...
How to detect remote access?
What Does a RAT Virus Do?
- Get access to confidential info including usernames, passwords, social security numbers, and credit card accounts.
- Monitor web browsers and other computer apps to get search history, emails, chat logs, etc.
- Hijack the system webcam and record videos.
- Monitor user activity by keystroke loggers or spyware.
- Take screenshots on the target PC.
Can someone help me with remote access?
Windows Remote Assistance lets someone you trust take over your PC and fix a problem from wherever they are. Before you can use it, you'll need to enable access. In the search box on the taskbar, type remote assistance, and then select Allow Remote Assistance invitations to be sent from this computer from the list of results.
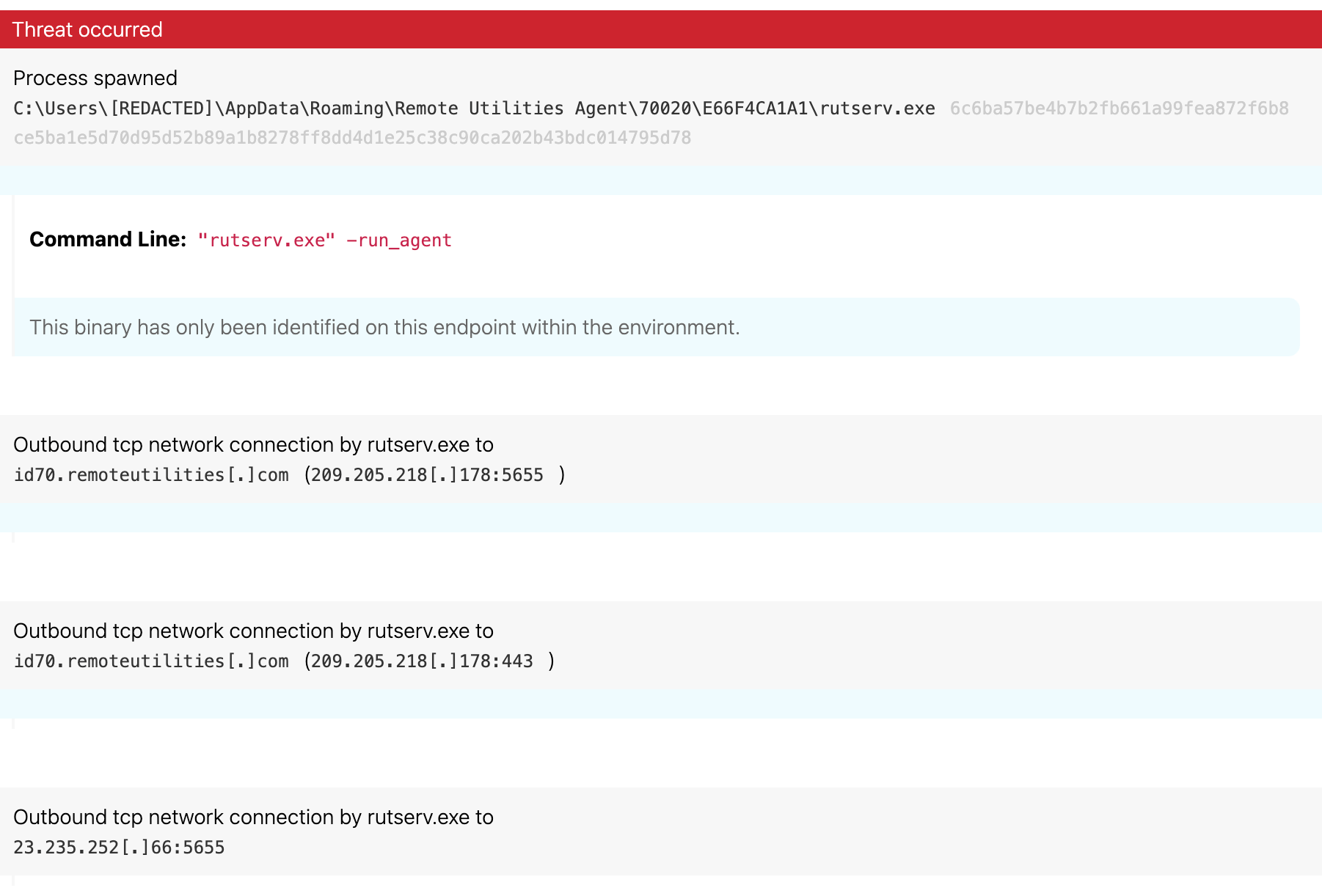
What is Trojan virus example?
Examples of govware trojans include the Swiss MiniPanzer and MegaPanzer and the German "state trojan" nicknamed R2D2. German govware works by exploiting security gaps unknown to the general public and accessing smartphone data before it becomes encrypted via other applications.
What are remote access Trojans used for?
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
How are remote access Trojans delivered?
A remote access Trojan (RAT) is a malware program that includes a back door for administrative control over the target computer. RATs are usually downloaded invisibly with a user-requested program -- such as a game -- or sent as an email attachment.
What is the best remote access Trojan?
10 Best Remote Access Software (Remote Control Software) In 2022Comparison of Top Remote Access Tools.#1) NinjaOne (Formerly NinjaRMM)#2) SolarWinds Dameware Remote Support.#3) Atera.#4) Supremo.#5) ManageEngine Remote Access Plus.#6) RemotePC.#7) TeamViewer.More items...•
Which of the following is a remote Trojan?
Troya is a remote Trojan that works remotely for its creator.
What was the first remote access Trojan?
The oldest RAT was first developed in 1996 [10], however legitimate remote access tools were first created in 1989 [11]. Since then, the number of RATs has grown rapidly. The first phase was marked by home-made RATs. In these years, everyone made their own RAT, however these did not prosper and were not heavily used.
Can an Iphone get a remote access Trojan?
The iOS Trojan is smart and spies discretely, i.e. does not drain a battery. The RCS mobile Trojans are capable of performing all kinds of spying you can expect from such a tool, including location reporting, taking photos, spying on SMS, WhatsApp and other messengers, stealing contacts and so on.
Is remote access Trojan illegal?
Law enforcement officials say that simply possessing a remote-access tool isn't illegal. In fact, remote-access tools are often used for IT support purposes in corporate environments.
Is TeamViewer a RAT?
The JS script then launches the malware, which installs a version of TeamViewer, a remote administration tool (RAT), modified by the attackers. As in earlier attacks, the attackers use a malicious DLL library to hide the graphical user interface in order to control the infected system without the user's knowledge.
What are remote applications?
A remote application is an application delivery solution wherein the actual application is installed on a central server and is used from a remote device. The end user receives screenshots of the application while being able to provide keyboard, thumb tap and mouse inputs.
What is a remote access tool?
Remote access programs and tools (sometimes referred to as RATs) allow access and manipulation of systems remotely from another location. Many remote access programs are legitimate tools used by all types of users to access files and data on remote computers.
What is the best RAT for Windows?
njRAT', also known as 'Bladabindi' or 'Njw0rm', is a well established and prevalent remote access trojan (RAT) threat that was initially created by a cyber criminal threat group. Now it is available for free that anyone can download and use it.
Are remote access Trojans illegal?
Law enforcement officials say that simply possessing a remote-access tool isn't illegal. In fact, remote-access tools are often used for IT support purposes in corporate environments.
What are rootkits used for?
The whole purpose of a rootkit is to protect malware. Think of it like an invisibility cloak for a malicious program. This malware is then used by cybercriminals to launch an attack. The malware protected by rootkit can even survive multiple reboots and just blends in with regular computer processes.
Are PUPs malware?
Type and source of infection. Detections categorized as PUPs are not considered as malicious as other forms of malware, and may even be regarded by some as useful. Malwarebytes detects potentially unwanted programs for several reasons, including: They may have been installed without the user's consent.
Can an Iphone get a remote access Trojan?
The iOS Trojan is smart and spies discretely, i.e. does not drain a battery. The RCS mobile Trojans are capable of performing all kinds of spying you can expect from such a tool, including location reporting, taking photos, spying on SMS, WhatsApp and other messengers, stealing contacts and so on.
What is RAT software?
RAT can also stand for remote administration tool, which is software giving a user full control of a tech device remotely. With it, the user can ac...
What’s the difference between the RAT computer virus and RAT software?
As for functions, there is no difference between the two. Yet, while remote administration tool is for legit usage, RAT connotes malicious and crim...
What are the popular remote access applications?
The common remote desktop tools include but are not limited to TeamViewer, AnyDesk, Chrome Remote Desktop, ConnectWise Control, Splashtop Business...
What is a RAT trojan?
RAT trojan is typically installed on a computer without its owner’s knowledge and often as a trojan horse or payload. For example, it is usually downloaded invisibly with an email attachment, torrent files, weblinks, or a user-desired program like a game. While targeted attacks by a motivated attacker may deceive desired targets into installing RAT ...
Why do RATs use a randomized filename?
It is kind of difficult. RATs are covert by nature and may make use of a randomized filename or file path structure to try to prevent identification of itself. Commonly, a RAT worm virus does not show up in the lists of running programs or tasks and its actions are similar to those of legal programs.
What is poison ivy rat keylogger?
PoisonIvy RAT keylogger, also called “Backdoor.Darkmoon”, enables keylogging, screen/ video capturing, system administrating, file transferring, password stealing, and traffic relaying. It was designed by a Chinese hacker around 2005 and has been applied in several prominent attacks including the Nitro attacks on chemical companies and the breach of the RSA SecurID authentication tool, both in 2011.
What is a back orifice rootkit?
Back Orifice (BO) rootkit is one of the best-known examples of a RAT. It was made by a hacker group named the Cult of the Dead Cow (cDc) to show the security deficiencies of Microsoft’s Windows 9X series of operating systems (OS).
Is Sub 7 a trojan horse?
Typically, Sub 7 allows undetected and unauthorized access. So, it is usually regarded as a trojan horse by the security industry. Sub7 worked on the Windows 9x and Windows NT family of OSes, up to and including Windows 8.1. Sub7 has not been maintained since 2014. 4.
Can a RAT remote access trojan be used on a computer?
Since RAT remote access trojan will probably utilize the legitimate apps on your computer, you’d better upgrade those apps to their latest versions. Those programs include your browsers, chat apps, games, email servers, video/audio/photo/screenshot tools, work applications…
What is remote access trojan?
Functions of Remote Access Trojan : It can be used to monitor the user by using some spyware or other key-logger. It can be used to activate the webcam. It can be used to record video. It can be used to delete files, alter files. This Remote Access Trojan can also be used to capture screenshots.
What is the most powerful Trojan?
One of the most powerful Trojans that are popularly used by the attacker or hacker is Remote Access Trojan. This is mostly used for malicious purposes. This Trojan ensures the stealthy way of accumulating data by making itself undetected. Now, these Trojans have the capacity to perform various functions that damages the victim.
What is the advantage of remote access?
Advantage of Remote Access Trojans : It can be used to capture screenshots. The attacker can activate the webcam, or they can record video. The RAT can be used to delete the files or alter files in the system. It can also be used to capture screenshots.
Remote Access Trojan Definition
Malware developers code their software for a specific purpose, but to gain remote control of a user’s device is the ultimate benefit for an attacker who wants to steal data or take over a user’s computer.
How are Remote Access Trojans Useful to Hackers?
A 2015 incident in Ukraine illustrates the widespread and nefarious nature of RAT programs. Attackers using remote control malware cut power to 80,000 people by remotely accessing a computer authenticated into SCADA (supervisory control and data acquisition) machines that controlled the country’s utility infrastructure.
How Does a Remote Access Trojan Work?
To discover the way RATs work, users can remotely access a device in their home or on a work-related network. RATs work just like standard remote-control software, but a RAT is programmed to stay hidden to avoid detection either from anti-malware software or the device owner.
How to Detect a Remote Access Trojan
Because RATs are programmed to avoid detection, they can be difficult for the average user to identify. Depending on the RAT, users can take several steps to determine if they have a RAT installed on their system. These steps can be used to identify most malware on a system so that eradication steps can be taken to remove it.
Why are remote access Trojans important?
Remote Access Trojans fulfill an important function for hackers. Most attack vectors, like phishing, are ideal for delivering a payload to a machine but don’t provide the hacker with the ability to explore and interact with the target environment. RATs are designed to create a foothold on the target machine that provides the hacker with the necessary level of control over their target machine.
What is the next step in a phishing attack?
Once a hacker has gained initial access to a target machine, expanding and solidifying that foothold is the next logical step. In the case of a phishing attack, this involves using malware to take advantage of the access provided by the email.
Do remote access Trojans exist?
Many different Remote Access Trojans exist, and some hackers will modify existing ones or develop their own to be better suited to their preferences. Different RATs are also designed for different purposes, especially with RATs geared specifically to each potential target (desktop versus mobile, Windows versus Apple and so on).
What is remote access trojan?
Like most other forms of malware, Remote Access Trojans are often attached to files appearing to be legitimate, like emails or software bundles. However, what makes Remote Access Trojans particularly insidious is they can often mimic above-board remote access programs.
Can a RAT program be used to download viruses?
Once a RAT program is connected to your computer , the hacker can examine the local files, acquire login credentials and other personal information, or use the connection to download viruses you could unwittingly spread along to others.
Short bio
Remote Access Trojans are programs that provide the capability to allow covert surveillance or the ability to gain unauthorized access to a victim PC.
History
While the full history of Remote Access Trojans is unknown, these applications have been in use for a number of years to help attackers establish a foothold onto a victim PC. Well-known and long established Remote Access Trojans include the SubSeven, Back Orifice, and Poison-Ivy applications.
Common infection method
Remote Access Trojans can be installed in a number of methods or techniques, and will be similar to other malware infection vectors. Specially crafted email attachments, web-links, download packages, or .torrent files could be used as a mechanism for installation of the software.
Associated families
There are a large number of Remote Access Trojans. Some are more well-known than others. SubSeven, Back Orifice, ProRat, Turkojan, and Poison-Ivy are established programs. Others, such as CyberGate, DarkComet, Optix, Shark, and VorteX Rat have a smaller distribution and utilization.
Remediation
Remote Access Trojans are covert by nature and may utilize a randomized filename/path structure to try to prevent identification of the software.
Aftermath
Remote Access Trojans have the potential to collect vast amounts of information against users of an infected machine. If Remote Access Trojan programs are found on a system, it should be assumed that any personal information (which has been accessed on the infected machine) has been compromised.
Avoidance
As in all cases, never click email or website links from unknown locations or install software at the urging of unknown parties. Using a reputable antivirus and anti-malware solution will help to ensure Remote Access Trojans are unable to properly function, and will assist in mitigating any collection of data.
How Does a Remote Access Trojan Work?
RATS can infect computers like any other type of malware. They might be attached to an email, be hosted on a malicious website, or exploit a vulnerability in an unpatched machine.
The Threat of the RAT
Different attacks require different levels of access to a target system, and the amount of access that an attacker gains determines what they can accomplish during a cyberattack.
How to Protect Against a Remote Access Trojan
RATs are designed to hide themselves on infected machines, providing secret access to an attacker. They often accomplish this by piggybacking malicious functionality on a seemingly legitimate application. For example, a pirated video game or business application may be available for free because it has been modified to include malware.
Prevent RAT Infections with Check Point
Protecting against RAT infections requires solutions that can identify and block malware before it gains access to an organization’s systems.