
Trojan:Android/AndroRat
- Summary. Trojan:Android/AndroRat is a remote access tool (RAT) embedded into a 'carrier' app (essentially trojanizing).
- Removal. Once the scan is complete, the F-Secure security product will ask if you want to uninstall the file, move it to...
- Technical Details. In July [2013], there were reports of a new toolkit (aka "binders") that simplify the...
Full Answer
What is a remote access trojan (RAT)?
A common way of expanding this beachhead on the target machine is through Remote Access Trojans (RATs). This type of malware is designed to allow a hacker to remotely control a target machine, providing a level of access similar to that a remote system administrator.
What is remote access toolkit malware?
This type of malware is designed to allow a hacker to remotely control a target machine, providing a level of access similar to that a remote system administrator. In fact, some RATs are derived from or based upon legitimate remote administration toolkits.
Is there a remote administration tool for Windows?
Windows Remote Administration Tool via Telegram. Written in Python A repository full of malware samples. TechNowHorse is a RAT (Remote Administrator Trojan) Generator for Windows/Linux systems written in Python 3. RAT-el is an open source penetration test tool that allows you to take control of a windows machine.
See more
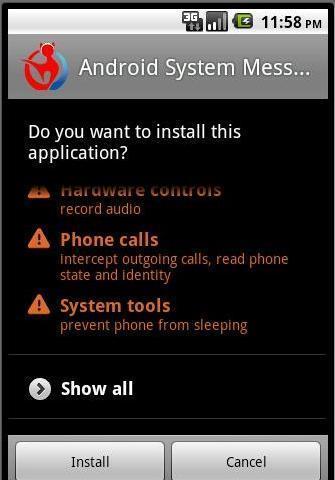
Can Trojan work on Android?
Trojans that run on the Android operating system are usually either specially-crafted programs that are designed to look like desirable software (e.g., games, system updates or utilities), or copies of legitimate programs that have been repackaged or trojanized to include harmful components.
What is a Mobile Remote Access Trojan?
This mobile remote access Trojan is known for targeting financial apps with malicious code in order to steal credentials and two-factor authentication codes. At that point, the malware-as-a-service can then empty the victim's banking account, install malicious apps and/or control the infected device with TeamViewer.
Can remote access Trojans be detected?
AIDE—short for Advanced Intrusion Detection Environment—is a HIDS designed specifically to focus on rootkit detection and file signature comparisons, both of which are incredibly useful for detecting APTs like Remote Access Trojans.
What is the best remote access Trojan?
10 Best Remote Access Software (Remote Control Software) In 2022Comparison of Top Remote Access Tools.#1) NinjaOne (Formerly NinjaRMM)#2) SolarWinds Dameware Remote Support.#3) Atera.#4) Supremo.#5) ManageEngine Remote Access Plus.#6) RemotePC.#7) TeamViewer.More items...•
What can remote access Trojans do?
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
What is AndroRat used for?
Summary. Trojan:Android/AndroRat is a remote access tool (RAT) embedded into a 'carrier' app (essentially trojanizing). Once the app is installed onto a device, the embedded RAT allows a remote attacker to control the affected device.
How are remote access Trojans delivered?
A remote access Trojan (RAT) is a malware program that includes a back door for administrative control over the target computer. RATs are usually downloaded invisibly with a user-requested program -- such as a game -- or sent as an email attachment.
What is smart RAT switch app?
RAT infected Android devices can be remotely zombified by the perpetrator, allowing virtually unlimited access to photos, data and messages on the device. The Dendroid RAT provides full access to infected devices' camera and microphone, and can place calls or listen in on a user's phone conversations or text messages.
What is a logic bomb and how does it work?
A Logic Bomb is a piece of often-malicious code that is intentionally inserted into software. It is activated upon the host network only when certain conditions are met. Logic bombs execute their functions, or launch their payload, once a certain condition is met such as upon the termination of an employee.
What can NanoCore do?
NanoCore can provide the threat actor with information such as computer name and OS of the affected system. It also opens a backdoor that allows the threat actors to access the webcam and microphone, view the desktop, create internet message windows and offers other options.
Can Remotepc be hacked?
Remote Desktop Protocol (RDP) has been known since 2016 as a way to attack some computers and networks. Malicious cyber actors, hackers, have developed methods of identifying and exploiting vulnerable RDP sessions via the Internet to steal identities, login credentials and install and launch ransomeware attacks.
What is AlienSpy?
Also known as AlienSpy, Frutas, Unrecom, Sockrat, JSocket and jRat, Adwind is a Remote Access Tool (RAT) based on Java which is distributed as a single malware-as-a-service platform.
Can an Iphone get a remote access Trojan?
The iOS Trojan is smart and spies discretely, i.e. does not drain a battery. The RCS mobile Trojans are capable of performing all kinds of spying you can expect from such a tool, including location reporting, taking photos, spying on SMS, WhatsApp and other messengers, stealing contacts and so on.
Which of the following is a remote Trojan?
Troya is a remote Trojan that works remotely for its creator.
What is a backdoor Trojan?
Backdoor malware is generally classified as a Trojan. A Trojan is a malicious computer program pretending to be something it's not for the purposes of delivering malware, stealing data, or opening up a backdoor on your system.
What is data sending Trojan?
A data-sending Trojan is a kind of Trojan virus that relays sensitive information back to its owner. This type of Trojan can be used to retrieve sensitive data, including credit card information, email addresses, passwords, instant messaging contact lists, log files and so on.
How many infections does Bitdefender have?
Since July, Bitdefender says they've seen 200 infections on devices running Bitdefender's mobile security software. That's only a fraction of the Android using populace, concedes Botezatu. However, he told me that he's seen individuals bragging on forums about AndroRAT botnets with 500 infected phones.
Is Androrat free?
AndroRAT has always been free and open-source, but the APK binder originally cost $35. Two months ago, Symantec reported only 23 installations of AndroRAT. That is until someone else cracked the binder and posted it for free online. "Look at the irony," said Botezatu.
Is Androrat a bad Trojan?
Originally, AndroRAT was an open-source proof-of-concept that became an actual remote access Trojan. That's bad, but it could be worse. At least it was hard to deliver to victim's phones and notoriously unstable.
Is Androrat monetized?
Most malware has a money-making angle behind it, but right now AndroRAT hasn't been monetized on a huge scale. That's usually the end-goal for Android malware; to exploit the victims in a way that earns the bad guys some cash.
What does RAT stand for?
Open-Source Origins. RAT can also stand for the safer-sounding phrase "Remote Administration Tool.". That's the phrase used to describe the open-source tool Androrat, which provides the actual remote control and monitoring.
What is a RAT?
A Remote-Access Trojan, or RAT, is a targeted tool, and that makes it quite a different story. When a PC has a RAT running, the RAT's owner can download files, run programs, spy using your webcam... the RAT gives total control.
Does Androrat offer refunds?
He points out that he is not the creator of Androrat and does not offer Androrat support. And he doesn't offer refunds.
Can a RAT herder run without the owner's knowledge?
That means it can run without the phone owner's knowledge. Of course the RAT-herder won't be managing it all the time, but a simple text can engage the phone's connection to the server. Send in the Trojans. Androrat is a free, open-source project that anybody can download and use.
Is Androrat free?
Androrat is a free, open-source project that anybody can download and use. With full access to someone's phone, you could just install it manually. What you get for your $37 is the Androrat APK Binder. Using this simple tool, you can take the APK file for any Android app and inject Androrat's code into it.
What is the Triangulum product?
The exact product that is being sold by Triangulum is a mobile remote access Trojan. A dangerous RAT that is capable of exfiltration of sensitive data from a C&C server.
What is remote access trojan?
The mobile remote access Trojan reached the gates of the Android world. Researchers have warned Android users of the risk of exfiltration of their information, such as photos, locations, contacts, and messages from popular apps such as Facebook, Instagram, WhatsApp, Skype, Telegram, Kik, Line, and Google Messages. This danger is derived from a second threat actor who uses an Android malware vendor, let the attackers take over the android device. As attackers can sell remote access Trojan devices through the dark market, it seems that earning money is their motivation for taking part in these attacks.
When did Triangulum go off?
It seems that investors have ignored Triangulum, just like how researchers did. Being ignored made Triangulum go off in the middle of 2018. One and half years later on April 6, 2019, a new user named “HeXaGoN Dev” who seems to specialize in the development of Android-based RATs, began selling a mobile remote access Trojan called “rouge”.
Did Triangulum develop this creation from scratch?
Therefore, the fact that Triangulum didn’t develop this creation from scratch does not put his creativity under question. This software is designed in such a way that mobile users will not be able to see its icon. Therefore, the victims will not realize that they have been attacked.
Is Triangulum a threat?
Although the Triangulum initiative has been ignored by many people in various dark markets, including those active in the Russian Dark Market, today it has become a serious threat to Android users. Hacking each Android user costs only $ 30, which is a security disaster.
Why are remote access Trojans important?
Remote Access Trojans fulfill an important function for hackers. Most attack vectors, like phishing, are ideal for delivering a payload to a machine but don’t provide the hacker with the ability to explore and interact with the target environment. RATs are designed to create a foothold on the target machine that provides the hacker with the necessary level of control over their target machine.
What is the next step in a phishing attack?
Once a hacker has gained initial access to a target machine, expanding and solidifying that foothold is the next logical step. In the case of a phishing attack, this involves using malware to take advantage of the access provided by the email.
What is the primary evaluation criteria for a given RAT?
The primary evaluation criteria for a given RAT is how well they allow a hacker to accomplish their goals on the target computer. Different RATs are specialized for certain purposes, but many of the top RATs are designed to provide a great deal of functionality on a variety of different systems.
What is RAT in mobile?
In the mobile market, RATs are advertised as solutions to help parents monitor their child’s cellular use or for employers to monitor how their employees are using company-owned devices. There are iOS monitoring applications available that do not require jailbreaking of the target device.
What is the most popular Android RAT?
The same is true for Android RATs. However, one of the most famous Android RATs in existence is AndroRAT.
What is PhoneSpector?
PhoneSpector offers the hacker the ability to monitor a wide variety of activities on the device. This includes monitoring phone calls and SMS messages (even those that were deleted) as well as app activity. PhoneSpector even provides a customer service helpline in case a hacker gets in a bind. 4.
What is a quasar?
Quasar is billed as a lightweight remote administration tool that runs on Windows. However, it also has a variety of functionalities designed for “employee monitoring” (i.e., useful for hackers as well). This includes keylogging, ability to open remote shells and downloading executing files.
What is the advantage of remote access?
Advantage of Remote Access Trojans : It can be used to capture screenshots. The attacker can activate the webcam, or they can record video. The RAT can be used to delete the files or alter files in the system. It can also be used to capture screenshots.
What is remote access trojan?
Functions of Remote Access Trojan : It can be used to monitor the user by using some spyware or other key-logger. It can be used to activate the webcam. It can be used to record video. It can be used to delete files, alter files. This Remote Access Trojan can also be used to capture screenshots.
What is the most powerful Trojan?
One of the most powerful Trojans that are popularly used by the attacker or hacker is Remote Access Trojan. This is mostly used for malicious purposes. This Trojan ensures the stealthy way of accumulating data by making itself undetected. Now, these Trojans have the capacity to perform various functions that damages the victim.
