What is remote access trojan and how it work?
- Checking client conduct through keyloggers or other spyware.
- Getting to private data, for example, Mastercard and government backed retirement numbers.
- Enacting a framework's webcam and recording video.
- Taking screen captures.
- Appropriating infections and other malware.
- Designing drives.
- Erasing, downloading or adjusting documents and record frameworks.
How to create remote access trojan?
Remote Access Trojan Examples
- Back Orifice. Back Orifice (BO) rootkit is one of the best-known examples of a RAT. ...
- Sakula. Sakula, also known as Sakurel and VIPER, is another remote access trojan that first surfaced in November 2012.
- Sub7. Sub7, also known as SubSeven or Sub7Server, is a RAT botnet. ...
- PoisonIvy. ...
- DarkComet. ...
How to create a trojan (RAT)?
how to create Remote Administration Tool (RAT)
- Remote Access Tool (RAT)
- Proxy
- File Sending Trojan
- Security Disable rs
- Denial Of Service (DOS)
- File Sending Trojans (FTP Trojan)
- Destructive Trojans
What is a remote access trojan?
- Functions of Remote Access Trojan : It can be used to monitor the user by using some spyware or other key-logger. It can be used to activate the webcam.
- Prevention of the Remote Access Trojan : The anti-virus should always be updated. ...
- Advantage of Remote Access Trojans : It can be used to capture screenshots. ...
Can remote access Trojans be detected?
AIDE—short for Advanced Intrusion Detection Environment—is a HIDS designed specifically to focus on rootkit detection and file signature comparisons, both of which are incredibly useful for detecting APTs like Remote Access Trojans.
What can remote access Trojans do?
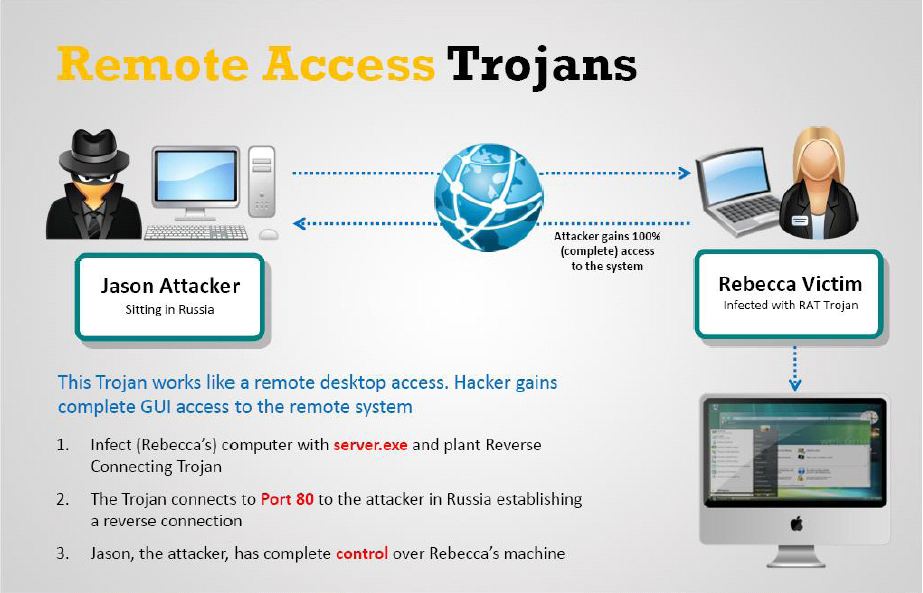
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
How are remote access Trojans delivered?
A remote access Trojan (RAT) is a malware program that includes a back door for administrative control over the target computer. RATs are usually downloaded invisibly with a user-requested program -- such as a game -- or sent as an email attachment.
What is the best remote access Trojan?
10 Best Remote Access Software (Remote Control Software) In 2022Comparison of Top Remote Access Tools.#1) NinjaOne (Formerly NinjaRMM)#2) SolarWinds Dameware Remote Support.#3) Atera.#4) Supremo.#5) ManageEngine Remote Access Plus.#6) RemotePC.#7) TeamViewer.More items...•
Is someone using my computer remotely?
Open your Task Manager or Activity Monitor. These utilities can help you determine what is currently running on your computer. Windows – Press Ctrl + Shift + Esc. Mac – Open the Applications folder in Finder, double-click the Utilities folder, and then double-click Activity Monitor.
How do I remove remote access?
How to Disable Remote Access in Windows 10Type “remote settings” into the Cortana search box. Select “Allow remote access to your computer”. ... Check “Don't Allow Remote Connections” to this Computer. You've now disabled remote access to your computer.
How is RAT malware installed?
An attacker must convince the user to install a RAT either by downloading malicious software from the web or running an executable from a malicious email attachment or message. RATs can also be installed using macros in Microsoft Word or Excel documents.
How can I find a hidden virus on my computer?
You can also head to Settings > Update & Security > Windows Security > Open Windows Security on Windows 10, or Settings > Privacy and Security > Windows Security > Open Windows Security on Windows 11. To perform an anti-malware scan, click “Virus & threat protection.” Click “Quick Scan” to scan your system for malware.
Which of the following is a remote Trojan?
Troya is a remote Trojan that works remotely for its creator.
Can Norton detect RATs?
Antivirus software like Bitdefender, Kaspersky, Webroot, or Norton, can detect RATs and other types of malware if they infect your devices.
Which connection is most commonly used in RATs?
RAT infections are typically carried out via spear phishing and social engineering attacks. Most are hidden inside heavily packed binaries that are dropped in the later stages of the malware's payload execution.
What is smart RAT switch app?
RAT infected Android devices can be remotely zombified by the perpetrator, allowing virtually unlimited access to photos, data and messages on the device. The Dendroid RAT provides full access to infected devices' camera and microphone, and can place calls or listen in on a user's phone conversations or text messages.
Which of the following is a remote Trojan?
Troya is a remote Trojan that works remotely for its creator.
Can Windows Defender detect Trojans?
Although, Windows Defender is not capable of handling all kinds of viruses, malware, trojan, and other security threats. You can trust it for basic Firewall protection, but not beyond based on the antimalware capabilities it offers.
What are the variants of remote access Trojan?
Common Remote Access TrojansSakula. Sakula is a seemingly benign software with a legitimate digital signature, yet it allows attackers complete remote administration capabilities over a machine. ... KjW0rm. ... Havex. ... Agent. ... Dark Comet. ... AlienSpy. ... Heseber BOT. ... Sub7.More items...
What is a backdoor Trojan?
Backdoor malware is generally classified as a Trojan. A Trojan is a malicious computer program pretending to be something it's not for the purposes of delivering malware, stealing data, or opening up a backdoor on your system.
Can a Remote Access Trojan be installed to BIOS?
Access to the BIOS has been known to the world’s hackers since 2015. Many believe that the NSA was planting RATs and trackers on BIOS even earlier.
How is a Remote Access Trojan RAT different from a regular Trojan horse?
A Trojan is a virus that gets onto a victim computer by passing itself off as a legitimate piece of software. A RAT is a Trojan that the hacker can...
What is the Sakula Remote Access Trojan RAT?
Sakula is a RAT that is used to intrude on IT systems serving government departments and agencies, healthcare facilities, and other large organizat...
What is RAT software?
RAT can also stand for remote administration tool, which is software giving a user full control of a tech device remotely. With it, the user can ac...
What’s the difference between the RAT computer virus and RAT software?
As for functions, there is no difference between the two. Yet, while remote administration tool is for legit usage, RAT connotes malicious and crim...
What are the popular remote access applications?
The common remote desktop tools include but are not limited to TeamViewer, AnyDesk, Chrome Remote Desktop, ConnectWise Control, Splashtop Business...
Remote Access Trojan Definition
Malware developers code their software for a specific purpose, but to gain remote control of a user’s device is the ultimate benefit for an attacker who wants to steal data or take over a user’s computer.
How are Remote Access Trojans Useful to Hackers?
A 2015 incident in Ukraine illustrates the widespread and nefarious nature of RAT programs. Attackers using remote control malware cut power to 80,000 people by remotely accessing a computer authenticated into SCADA (supervisory control and data acquisition) machines that controlled the country’s utility infrastructure.
How Does a Remote Access Trojan Work?
To discover the way RATs work, users can remotely access a device in their home or on a work-related network. RATs work just like standard remote-control software, but a RAT is programmed to stay hidden to avoid detection either from anti-malware software or the device owner.
How to Detect a Remote Access Trojan
Because RATs are programmed to avoid detection, they can be difficult for the average user to identify. Depending on the RAT, users can take several steps to determine if they have a RAT installed on their system. These steps can be used to identify most malware on a system so that eradication steps can be taken to remove it.
Short bio
Remote Access Trojans are programs that provide the capability to allow covert surveillance or the ability to gain unauthorized access to a victim PC.
History
While the full history of Remote Access Trojans is unknown, these applications have been in use for a number of years to help attackers establish a foothold onto a victim PC. Well-known and long established Remote Access Trojans include the SubSeven, Back Orifice, and Poison-Ivy applications.
Common infection method
Remote Access Trojans can be installed in a number of methods or techniques, and will be similar to other malware infection vectors. Specially crafted email attachments, web-links, download packages, or .torrent files could be used as a mechanism for installation of the software.
Associated families
There are a large number of Remote Access Trojans. Some are more well-known than others. SubSeven, Back Orifice, ProRat, Turkojan, and Poison-Ivy are established programs. Others, such as CyberGate, DarkComet, Optix, Shark, and VorteX Rat have a smaller distribution and utilization.
Remediation
Remote Access Trojans are covert by nature and may utilize a randomized filename/path structure to try to prevent identification of the software.
Aftermath
Remote Access Trojans have the potential to collect vast amounts of information against users of an infected machine. If Remote Access Trojan programs are found on a system, it should be assumed that any personal information (which has been accessed on the infected machine) has been compromised.
Avoidance
As in all cases, never click email or website links from unknown locations or install software at the urging of unknown parties. Using a reputable antivirus and anti-malware solution will help to ensure Remote Access Trojans are unable to properly function, and will assist in mitigating any collection of data.
What can a hacker do with a RAT?
A hacker with a RAT can command power stations, telephone networks, nuclear facilities, or gas pipelines. RATs not only represent a corporate network security risk, but they can also enable belligerent nations to cripple an enemy country.
How to get rid of a RAT?
Sometimes, the only solution to rid your computer of a RAT is to wipe out all of your software and reinstall the operating system. RAT prevention systems are rare because the RAT software can only be identified once it is operating on your system.
What is intrusion detection?
Intrusion detection systems are important tools for blocking software intrusion that can evade detection by antivirus software and firewall utilities. The SolarWinds Security Event Manager is a Host-based Intrusion Detection System. However, there is a section of the tool that works as a Network-based Intrusion Detection System. This is the Snort Log Analyzer. You can read more about Snort below, however, you should know here that it is a widely used packet sniffer. By employing Snort as a data collector to feed into the Snort Log Analyzer, you get both real-time and historic data analysis out of the Security Event Manager.
How does Beast RAT work?
The Beast RAT attacks Windows systems from Windows 95 up to Windows 10. This uses the same client-server architecture that Back Orifice pioneered with the server part of the system being the malware that gets installed surreptitiously on the target computer. Once the server element is operational, the hacker can access the victim computer at will through the client program. The client connects to the target computer at port number 6666. The server is also able to open connections back to the client and that uses port number 9999. Beast was written in 2002 and is still widely in use.
What is a RAT?
RATs are tools that are usually used in a stealth type of hacker attack, which is called an Advanced Persistent Threat, or APT. This type of intrusion is not focused on damaging information or raiding computers quickly for data.
Why do companies use RATs?
RATs can also be used to reroute traffic through your company network to mask illegal activities. Some hacker groups, predominantly in China, have even created a hacker network that runs through the corporate networks of the world and they rent out access to this cybercrime highway to other hackers.
Is remote access a Trojan?
There are a number of remote access systems that could have legitimate applications, but are well-known as tools that are mainly used by hackers as part of a Trojan; these are categorized as Remote Access Trojans. The details of the best-known RATs are explained below.
What is a RAT trojan?
RAT trojan is typically installed on a computer without its owner’s knowledge and often as a trojan horse or payload. For example, it is usually downloaded invisibly with an email attachment, torrent files, weblinks, or a user-desired program like a game. While targeted attacks by a motivated attacker may deceive desired targets into installing RAT ...
Why do RATs use a randomized filename?
It is kind of difficult. RATs are covert by nature and may make use of a randomized filename or file path structure to try to prevent identification of itself. Commonly, a RAT worm virus does not show up in the lists of running programs or tasks and its actions are similar to those of legal programs.
What is a RAT?
A remote access trojan (RAT), also called cree pware, is a kind of malware that controls a system via a remote network connection. It infects the target computer through specially configured communication protocols and enables the attacker to gain unauthorized remote access to the victim. RAT trojan is typically installed on a computer without its ...
What is poison ivy rat keylogger?
PoisonIvy RAT keylogger, also called “Backdoor.Darkmoon”, enables keylogging, screen/ video capturing, system administrating, file transferring, password stealing, and traffic relaying. It was designed by a Chinese hacker around 2005 and has been applied in several prominent attacks including the Nitro attacks on chemical companies and the breach of the RSA SecurID authentication tool, both in 2011.
What does RAT stand for?
RAT can also stand for remote administration tool, which is software giving a user full control of a tech device remotely. With it, the user can access your system just like he has physical access to your device. So, the user can access your files, use your camera, and even turn off or turn on your machine.
Can a RAT remote access trojan be used on a computer?
Since RAT remote access trojan will probably utilize the legitimate apps on your computer, you’d better upgrade those apps to their latest versions. Those programs include your browsers, chat apps, games, email servers, video/audio/photo/screenshot tools, work applications…
Is Sub 7 a trojan horse?
Typically, Sub 7 allows undetected and unauthorized access. So, it is usually regarded as a trojan horse by the security industry. Sub7 worked on the Windows 9x and Windows NT family of OSes, up to and including Windows 8.1. Sub7 has not been maintained since 2014. 4.
What is a RAT?
A Remote Access Trojan (RAT) is a type of malware that provides the attacker with full remote control over your system. When a RAT reaches your computer, it allows the hacker to easily access your local files, secure login authorization, and other sensitive information, or use that connection to download viruses you could unintentionally pass on to others.
What percentage of Georgia's internet was affected by the Russian invasion?
Thirty-five percent of Georgia’s Internet networks suffered decreased functionality during the attacks, with the highest levels of online activity coinciding with the Russian invasion of South Ossetia on August 8, 9, and 10. Even the National Bank of Georgia had to suspend all electronic services from August 8–19.
Is Heimdal RAT good?
RATs are never good news, therefore it is of utmost importance to protect your systems against them. What you should know is that our Heimdal™ Threat Prevention solution is compatible with any antivirus product available on the market that will block threats at their root.
Can remote access Trojans wipe hard drives?
But they don’t stop here. The administrative access Remote Access Trojans provide means cybercriminals can wipe hard drives, download illegal and classified information, or even passing themselves off as somebody else on the Internet. These actions can lead to geopolitical implications.
What is remote access trojan?
Like most other forms of malware, Remote Access Trojans are often attached to files appearing to be legitimate, like emails or software bundles. However, what makes Remote Access Trojans particularly insidious is they can often mimic above-board remote access programs.
Can a RAT program be used to download viruses?
Once a RAT program is connected to your computer , the hacker can examine the local files, acquire login credentials and other personal information, or use the connection to download viruses you could unwittingly spread along to others.