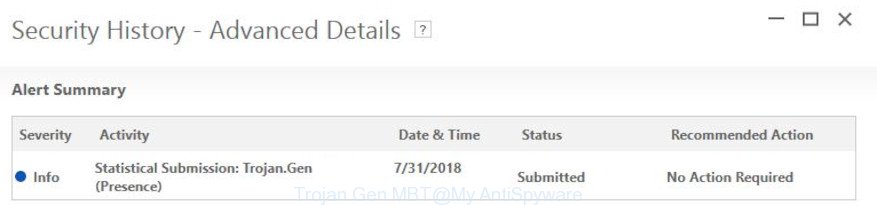
To remove RTA from your computer, perform the following steps:
- Remove RTA manually from your Windows installed programs
- Reset your browser infected with RTA
- Scan and remove infection remnants using an adware removal program
- Clean your Windows Registry
Full Answer
What is remote access trojan (RAT)?
A Remote Access Trojan (RAT) is a type of malware that lets a hacker take control of your computer. The spying activities that the hacker may carry out once that RAT is installed vary from exploring your files system, watching activities on the screen,...
How do I remove a Trojan virus from my computer?
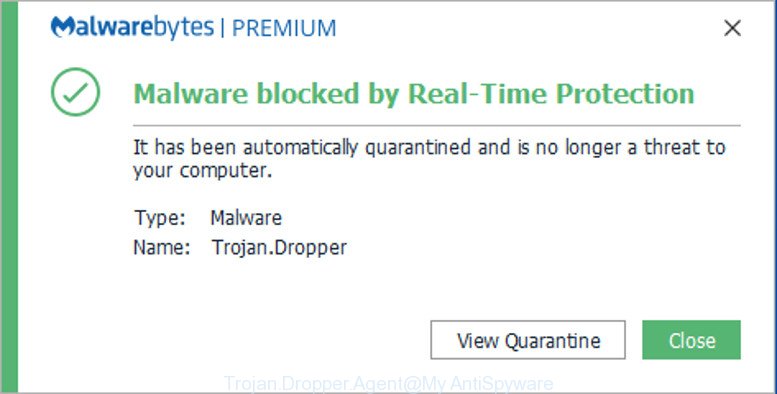
The best way to clean up a Trojan infection is to use Malwarebytes’ free trojan scanner, and then consider Malwarebytes Premium for proactive protection against future Trojan infections. Malwarebytes Premium will initiate a scan for Trojans and then remove Trojans so they can’t cause further damage.
Which is the Best Antivirus for remote access trojan detection?
Remote Access Trojan Detection 1 Avast 2 AVG 3 Avira 4 Bitdefender 5 Kaspersky 6 Malwarebytes 7 McAfee 8 Microsoft Windows Defender 9 Norton 10 PC Matic 11 Sophos 12 Trend Micro More ...
How do I check if a trojan is installed on my computer?
Click the “Scan” button and the Trojan scanner quickly checks your device. Download and install the Malwarebytes’ free Trojan scanner software. Click the “Scan” button and the Trojan scanner quickly checks your device.
Can remote access Trojans be detected?
AIDE—short for Advanced Intrusion Detection Environment—is a HIDS designed specifically to focus on rootkit detection and file signature comparisons, both of which are incredibly useful for detecting APTs like Remote Access Trojans.
What does a Remote Access Trojan do?
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
Can Trojan viruses be removed?
Trojan viruses can be removed in various ways. If you know which software contains the malware, you can simply uninstall it. However, the most effective way to remove all traces of a Trojan virus is to install antivirus software capable of detecting and removing Trojans.
How do I remove remote malware?
1:283:06How to remove a computer virus remotely - YouTubeYouTubeStart of suggested clipEnd of suggested clipYou can launch the anti-malware. Program first let's accept all the licensing terms and clickMoreYou can launch the anti-malware. Program first let's accept all the licensing terms and click continue. And then start scanning.
Is someone using my computer remotely?
Open your Task Manager or Activity Monitor. These utilities can help you determine what is currently running on your computer. Windows – Press Ctrl + Shift + Esc. Mac – Open the Applications folder in Finder, double-click the Utilities folder, and then double-click Activity Monitor.
How can I find a hidden virus on my computer?
You can also head to Settings > Update & Security > Windows Security > Open Windows Security on Windows 10, or Settings > Privacy and Security > Windows Security > Open Windows Security on Windows 11. To perform an anti-malware scan, click “Virus & threat protection.” Click “Quick Scan” to scan your system for malware.
Are Trojans easy to remove?
Trojan horses are some of the most frustrating viruses that you can get on your computer. Not only are they easy to pick up, they're not always easy to find. On top of that, Trojan horses are irritating to get off of the computer once they're there. However, they're not impossible to remove.
What is the best Trojan remover?
The best way to clean up a Trojan infection is to use Malwarebytes' free trojan scanner, and then consider Malwarebytes Premium for proactive protection against future Trojan infections. Malwarebytes Premium will initiate a scan for Trojans and then remove Trojans so they can't cause further damage.
Will resetting PC remove Trojan?
Running a factory reset, also referred to as a Windows Reset or reformat and reinstall, will destroy all data stored on the computer's hard drive and all but the most complex viruses with it. Viruses can't damage the computer itself and factory resets clear out where viruses hide.
Can you get a virus from remote access?
Many remote access software solutions don't scan the remote computer for viruses or malware. If your home or work PC has been infected, and you're using it to access your office network remotely, then a hacker could easily install malware onto your business's servers and spread to every machine in your office.
What are the 7 steps of malware removal?
Malware Removal (scenario)Identify and research malware symptoms. ... Quarantine the infected systems. ... Disable System Restore (in Windows). ... Remediate the infected systems. ... Schedule scans and run updates. ... Enable System Restore and create a restore point (in Windows). ... Educate the end user.
How do I remove a Trojan virus from Windows 10?
Remove malware from your Windows PCOpen your Windows Security settings.Select Virus & threat protection > Scan options.Select Windows Defender Offline scan, and then select Scan now.
Which of the following is a remote Trojan?
Troya is a remote Trojan that works remotely for its creator.
Are PUPs malware?
Type and source of infection. Detections categorized as PUPs are not considered as malicious as other forms of malware, and may even be regarded by some as useful. Malwarebytes detects potentially unwanted programs for several reasons, including: They may have been installed without the user's consent.
Can iphones get RAT virus?
So someone would need direct physical access to your iOS device and a computer to install a RAT exploit into it. Even if you accessed a web site or email with a RAT package hidden in it, it cannot execute or do anything on a normal iOS installation.
What was the first remote access Trojan?
The oldest RAT was first developed in 1996 [10], however legitimate remote access tools were first created in 1989 [11]. Since then, the number of RATs has grown rapidly. The first phase was marked by home-made RATs. In these years, everyone made their own RAT, however these did not prosper and were not heavily used.
What is RAT software?
RAT can also stand for remote administration tool, which is software giving a user full control of a tech device remotely. With it, the user can ac...
What’s the difference between the RAT computer virus and RAT software?
As for functions, there is no difference between the two. Yet, while remote administration tool is for legit usage, RAT connotes malicious and crim...
What are the popular remote access applications?
The common remote desktop tools include but are not limited to TeamViewer, AnyDesk, Chrome Remote Desktop, ConnectWise Control, Splashtop Business...
What are Remote Access Trojans?
Remote Access Trojans (RATs) are programs that allow hackers to control or monitor your computer remotely, usually through the internet. RATs can be either purchased or programmed by a hacker him-or-herself, but generally they fall under three categories:
How to prevent a RAT from taking over your computer again?
Plugging the Ethernet cable into your router and disabling WiFi should prevent a RAT from taking over your computer again. If you do not plug in an Ethernet cord, ensure that your wireless is turned off and that all security programs are up to date as this will stop any future attacks.
A Reader Writes
For the past month my computer has been acting strangely. From what I've read, I'm pretty sure it's been infected with a Remote Access Trojan. Obviously, I'm really concerned.Can you tell me how to remove them, and how I can avoid getting infected in the future?
Matthew's Reply
Ouch. Remote Access Trojans are nasty, simply because they allow an attacker to do just that – remotely access your machine from anywhere in the world.
Knowing When You're Infected
So, how do you know when you've been infected? Well, a good clue is when your computer is acting strangely.
Turn Off the Internet
The first step is, obviously, to disconnect your computer from the Internet.
Fire Up Your Anti-Malware Software
If you're sensible, you've likely already got some anti-malware already installed and updated. Now it's just a matter of running it, and hoping that it catches whatever's installed.
Wipe Your System
One of the biggest problems with RAT malware is that it gives the attacker complete control of your system. If they want, they can easily install additional malware. There's also the risk that your chosen anti-malware won't recognize the RAT on your system. With that in mind, you might be tempted to just wipe your machine and start afresh.
Prevention is Better Than the Cure
The most effective way to deal with RATs is to not get infected in the first place. I know, it's easier said than done, but by adopting a few strategies, you drastically improve your odds.
What happens when you give a Trojan remover an ok?
When you give the ok, the Trojan remover will clean up threats so your device, files, and privacy are secure. When you give the ok, the Trojan remover will clean up threats so your device, files, and privacy are secure.
How to clean up a Trojan infection?
The best way to clean up a Trojan infection is using a security protection solution like Malwarebytes’ free trojan scanner. Malwarebytes will initiate a scan for Trojans and then remove Trojans so they can’t cause further damage.
What is a Trojan 2021?
What is a Trojan? Even in 2021, Troj ans are still using deception and social engineering to trick unsuspecting users into running seemingly benign computer programs that hide malevolent ulterior motives.
Can a Trojan download malware?
Trojans can download code or software that looks legitimate but, in reality, it will take control of your device and install malicious threats including malware, ransomware, and spyware. Trojans aren’t limited to Windows laptops and desktop computers; they can also impact Macs and mobile devices.
Is a Trojan a virus?
You might assume a Trojan is a type of virus or a worm, but it’s really neither. It’s actually a delivery mechanism for infecting your device with cybersecurity threats, from ransomware that immediately demands money, to spyware that conceals itself while it steals personal and financial data.
Remote Access Trojan Definition
Malware developers code their software for a specific purpose, but to gain remote control of a user’s device is the ultimate benefit for an attacker who wants to steal data or take over a user’s computer.
How are Remote Access Trojans Useful to Hackers?
A 2015 incident in Ukraine illustrates the widespread and nefarious nature of RAT programs. Attackers using remote control malware cut power to 80,000 people by remotely accessing a computer authenticated into SCADA (supervisory control and data acquisition) machines that controlled the country’s utility infrastructure.
How Does a Remote Access Trojan Work?
To discover the way RATs work, users can remotely access a device in their home or on a work-related network. RATs work just like standard remote-control software, but a RAT is programmed to stay hidden to avoid detection either from anti-malware software or the device owner.
How to Detect a Remote Access Trojan
Because RATs are programmed to avoid detection, they can be difficult for the average user to identify. Depending on the RAT, users can take several steps to determine if they have a RAT installed on their system. These steps can be used to identify most malware on a system so that eradication steps can be taken to remove it.
What is intrusion detection?
Intrusion detection systems are important tools for blocking software intrusion that can evade detection by antivirus software and firewall utilities. The SolarWinds Security Event Manager is a Host-based Intrusion Detection System. However, there is a section of the tool that works as a Network-based Intrusion Detection System. This is the Snort Log Analyzer. You can read more about Snort below, however, you should know here that it is a widely used packet sniffer. By employing Snort as a data collector to feed into the Snort Log Analyzer, you get both real-time and historic data analysis out of the Security Event Manager.
How to get rid of a RAT?
Sometimes, the only solution to rid your computer of a RAT is to wipe out all of your software and reinstall the operating system. RAT prevention systems are rare because the RAT software can only be identified once it is operating on your system.
What is OSSEC in security?
OSSEC stands for Open Source HIDS Security . A HIDS is a Host Intrusion Detection System, which examines events on the computers in a network rather than trying to spot anomalies in the network traffic, which is what network intrusion detection systems do.
What can a hacker do with a RAT?
A hacker with a RAT can command power stations, telephone networks, nuclear facilities, or gas pipelines. RATs not only represent a corporate network security risk, but they can also enable belligerent nations to cripple an enemy country.
Is remote access a Trojan?
There are a number of remote access systems that could have legitimate applications, but are well-known as tools that are mainly used by hackers as part of a Trojan; these are categorized as Remote Access Trojans. The details of the best-known RATs are explained below.
Can antivirus be used to get rid of a RAT?
Antivirus systems don’t do very well against RATs. Often the infection of a computer or network goes undetected for years. The obfuscation methods used by parallel programs to cloak the RAT procedures make them very difficult to spot. Persistence modules that use rootkit techniques mean that RATs are very difficult to get rid of. Sometimes, the only solution to rid your computer of a RAT is to wipe out all of your software and reinstall the operating system.
Is Snort a free intrusion detection system?
Snort. Snort is free to use and it is the industry leader in NIDS, which is a Network Intrusion Detection System. This system was created by Cisco Systems and it can be installed on Windows, Linux, and Unix. Snort can implement defense strategies, which makes it an intrusion prevention system. It has three modes: