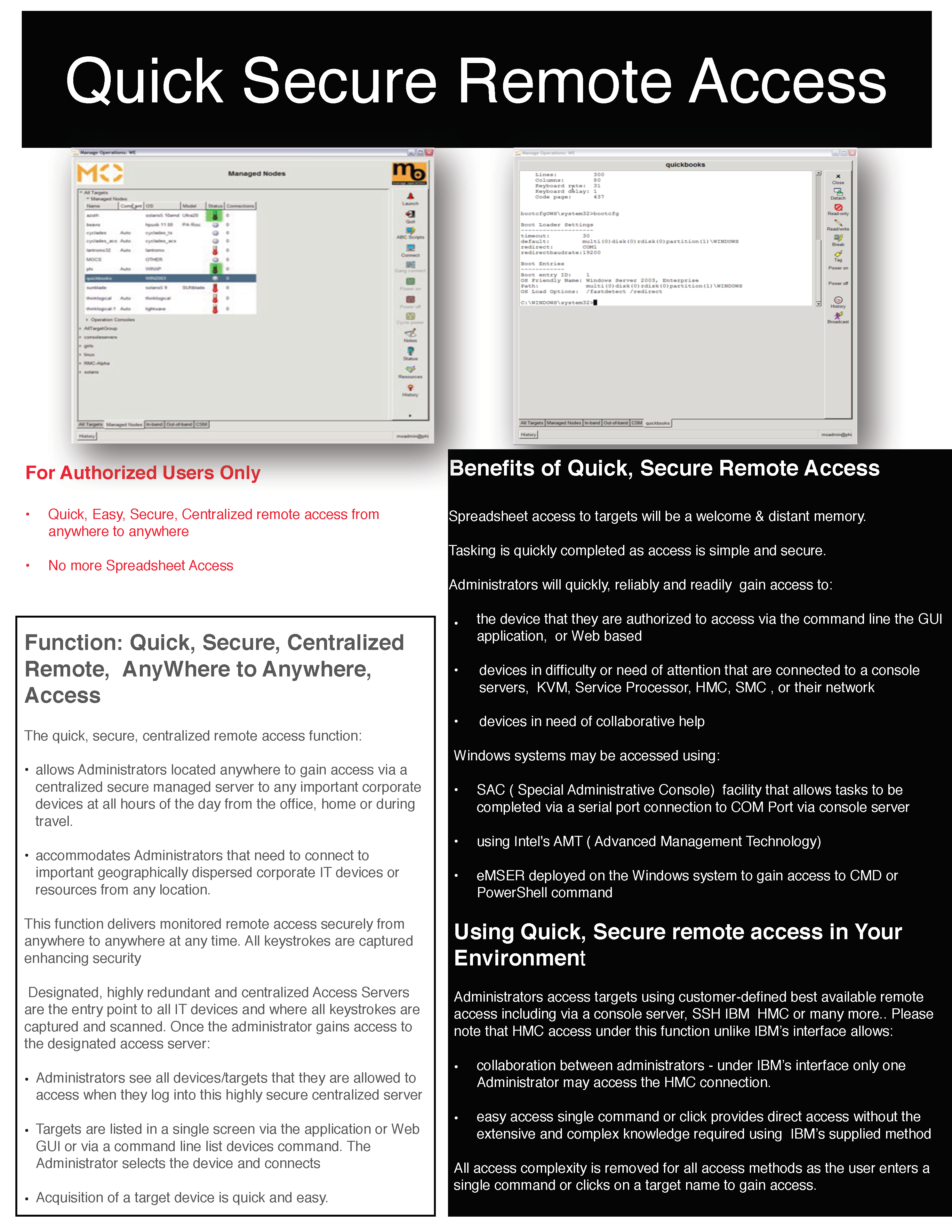
Remote Access Agreement . 1. Acceptable Use standard. Remote User agrees to read and adhere to Children’sAcceptable Use policy (AD-1001) while connected to and utilizing any information system remotely. 2. Protection of Confidential Information. Remote User agrees to protect the confidentiality,
Full Answer
How secure is enabling remote access?
- iOS/Android: Swap album and artist titles in CarPlay/Android Auto.
- iOS/Android: Rare crash if your library had ~200,000 items.
- Desktop: Reduce hover play background size to allow clicking on poster.
- iOS: Crash for high CPU in some cases if server disks were offline.
- CarPlay/Android Auto: Show all albums when album types are enabled.
How to set up secure remote access?
- Windows or Mac login when connecting remotely
- Request permission to connect to the user’s computer
- Automatically blank the remote screen when connected
- Automatically lock remote computer when disconnected
- Lock the remote computer’s keyboard and mouse while in session
- Lock the streamer settings using Splashtop admin credentials
What are remote access policies?
Types of Remote Access Security Risks
- Permissive Policies of Remote Access. Attackers can quickly acquire access to the rest of the network if they compromise a VPN (virtual private network).
- Remote Devices Control. ...
- Remote Activity with Limited Visibility. ...
- Reusing Passwords. ...
Can someone help me with remote access?
Windows Remote Assistance lets someone you trust take over your PC and fix a problem from wherever they are. Before you can use it, you'll need to enable access. In the search box on the taskbar, type remote assistance, and then select Allow Remote Assistance invitations to be sent from this computer from the list of results.
What should be included in a remote access policy?
What Should You Address in a Remote Access Policy?Standardized hardware and software, including firewalls and antivirus/antimalware programs.Data and network encryption standards.Information security and confidentiality.Email usage.Physical and virtual device security.Network connectivity, e.g., VPN access.More items...•
What is remote user access?
Remote access is the ability for an authorized person to access a computer or network from a geographical distance through a network connection. Remote access enables users to connect to the systems they need when they are physically far away.
What is a remote access plan?
A well-designed remote access plan provides access to the required corporate data and applications for users when they're off-premises.
What are some common remote access methods?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What are the benefits of remote access?
Here, we discuss the most common flexible working benefits that can be supported by your remote access strategy.A more productive workforce. ... Better talent acquisition. ... IT support from anywhere. ... Improved security for remote workers. ... Lower overhead cost. ... Business continuity planning.
Can someone remotely access my computer?
Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular. Remote desktop servers connect directly to the Internet when you forward ports on your router. Hackers and malware may be able to attack a weakness in those routers.
What is the main purpose of a RAS server?
A remote access server (RAS) is a type of server that provides a suite of services to remotely connected users over a network or the Internet. It operates as a remote gateway or central server that connects remote users with an organization's internal local area network (LAN).
What is a VPN policy?
A VPN security policy is a policy that defines. just about everything that anyone would need to know about your VPN. It defines. things like who can use the VPN, what they can use it for, and what it is that. keeps them from using improperly or maliciously.
How do I activate my remote access plan?
Activate your Remote Access licenseStep 1: Prepare your remote computer. ... Step 2: Create your TeamViewer account & activate the license. ... Step 3: Log into your TeamViewer account within the TeamViewer program on the local computer. ... Step 4: Add your remote computer(s) to your TeamViewer account.
What are the examples of remote user security policy best practices?
Best Practices For Remote Access SecurityEnable encryption. ... Install antivirus and anti-malware. ... Ensure all operating systems and applications are up to date. ... Enforce a strong password policy. ... Use Mobile Device Management (MDM) ... Use Virtual Private Network (VPN) ... Use two-factor authentication.More items...•
What are security considerations for remote users examples?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
What are the vulnerabilities of remote access?
Many remote access security risks abound, but below is a list of the ones that jump out.Lack of information. ... Password sharing. ... Software. ... Personal devices. ... Patching. ... Vulnerable backups. ... Device hygiene. ... Phishing attacks.
How do I stop remote access to my computer?
How to Disable Remote Access in Windows 10Type “remote settings” into the Cortana search box. Select “Allow remote access to your computer”. ... Check “Don't Allow Remote Connections” to this Computer. You've now disabled remote access to your computer.
How can I tell who is accessing my remote desktop?
The easiest way to determine who has access to a particular Windows machine is to go into computer management (compmgmt. msc) and look in Local Users and Groups. Check the Administrators group and the Remote Desktop Users group to see who belongs to these.
Can my company see my remote desktop?
Can my employer see me at home via Citrix, Terminal, and Remote Desktop sessions? A: NO, your employer cannot see you at home through the Citrix/Terminal Server or Remote Desktop sessions. The way this technology works, it is not possible in general.
How do I trace remote access?
1:132:22How to trace remote access logs VPN access - YouTubeYouTubeStart of suggested clipEnd of suggested clipAnd I'm just gonna type in C colon backslash Windows backslash tracing and that's gonna open up myMoreAnd I'm just gonna type in C colon backslash Windows backslash tracing and that's gonna open up my tracing directory.