
Traditional VPN-based remote access architecture The traditional remote access architecture separates a remote access architecture into a strong outer perimeter and multiple internal layers that are separated using firewalls. At a high level, these layers of this walled garden are: The access layer, authenticating remote devices.
How do I deploy a remote access VPN architecture on Oracle?
To deploy a Remote Access VPN architecture on Oracle Cloud Infrastructure by using the Cisco ASA Virtual Firewall, perform the following steps: Oracle recommends deploying the architecture from Oracle Cloud Marketplace.
What is the best VPN for Oracle Cloud Infrastructure?
Cisco ASAv provides Oracle Cloud Infrastructure (OCI) a scalable VPN solution with multiple feature options, such as remote-access, site-to-site, client less, and more. Deploy a scalable remote access VPN architecture by using Cisco ASAv on Oracle Cloud Infrastructure
What is a client based VPN?
In the last design scenario we looked at DMZs, in this post we will talk about client based Virtual Private Networks (VPN) usually referred to by their original name of Secure Sockets layer (SSL) VPN. I say old name because SSL is now a deprecated protocol and has been replaced with Transport layer security (TLS).
What is the remote access server role in Windows Server 2016?
In Windows Server 2016, the Remote Access server role is designed to perform well as both a router and a remote access server; therefore, it supports a wide array of features. For this deployment guidance, you require only a small subset of these features: support for IKEv2 VPN connections and LAN routing.
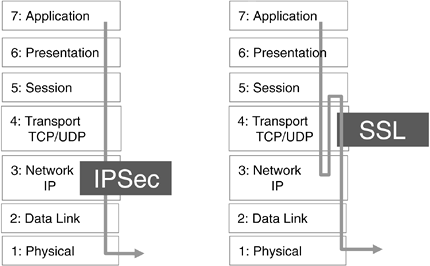
What is the architecture of VPN?
VPN uses authentication methods, encryption algorithms, and other precautions to ensure that data sent between the two endpoints of its connection remains secure. VPN runs on the network layer of the TCP/IP layered communications stack model. Specifically, VPN uses the IP Security Architecture (IPSec) open framework.
How does remote access work with VPN?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
Is VPN same as remote access?
Flexibility. While having some similarities, VPN and remote desktop are functionally different things. A VPN will give you access to a network while remote desktop (or RDP) will give you control of an entire computer.
How do I set up VPN server for remote access?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
What are the two types of VPN connections?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
Which VPN is best for remote access?
Perimeter 81 – Best all-round business VPN. Jul 2022. ... GoodAccess – Security Strategy Options. Apps Available: ... ExpressVPN – Lightning Fast VPN. ... Windscribe – VPN with Enterprise-Friendly Features. ... VyprVPN – Secure VPN with Business Packages. ... NordVPN – Security-first VPN. ... Surfshark – VPN with Unlimited User Connections.
What is the difference between RDS RDP and VPN?
Unlike VPN, RDP typically enables users to access applications and files on any device, at any time, over any type of connection. The biggest advantage of RDP is that you have access to network resources, databases, and line-of-business software applications without the limitations and high bandwidth demands of VPN.
What are important characteristics of remote access VPNs?
What is an important characteristic of remote-access VPNs?The VPN configuration is identical between the remote devices.Internal hosts have no knowledge of the VPN.Information required to establish the VPN must remain static.The VPN connection is initiated by the remote user.
Why would you use RDS instead of VPN?
VPN – Virtual Private Network encrypts your data and masks the IP address so that no malicious hacker can access the data and detect your location. The data is decrypted only at the intended destination. RDS – In RDS, the data is stored on the remote server and not on the end-point device.
What is the difference between RAS and RRAS?
Microsoft Remote Access Server (RAS) is the predecessor to Microsoft Routing and Remote Access Server (RRAS). RRAS is a Microsoft Windows Server feature that allows Microsoft Windows clients to remotely access a Microsoft Windows network.
Can I use RDP and VPN at the same time?
There's nothing wrong with VPN connection to the network then RDP to LAN while on the VPN. That's very common as it adds security. This person is a verified professional. Verify your account to enable IT peers to see that you are a professional.
How does VPN split tunneling work?
Split tunneling is a VPN feature that divides your internet traffic and sends some of it through an encrypted virtual private network (VPN) tunnel, but routes the rest through a separate tunnel on the open network. Typically, split tunneling will let you choose which apps to secure and which can connect normally.
Does VPN allow you to access a computer remotely?
In order to fully secure a remote desktop, a VPN is the best option. With a VPN like Access Server, you have secure access to the network, and then the VPN server has least a privilege access policy setup that would limit an employee to using a remote desktop to connect only to his or her computer's IP address.
Can you be tracked if you use VPN?
However, if you use a poor quality VPN, you could still be tracked. A premium quality VPN encrypts data and hides your IP address by routing your activity through a VPN server; even if someone tries to monitor your traffic, all they'll see is the VPN server's IP and complete gibberish.
What are the disadvantages of using a VPN?
The 10 biggest VPN disadvantages are:A VPN won't give you complete anonymity: Read more.Your privacy isn't always guaranteed: Read more.Using a VPN is illegal in some countries: Read more.A safe, top-quality VPN will cost you money: Read more.VPNs almost always slow your connection speed: Read more.More items...•
What is remote access VPN?
A remote access Virtual Private Network (VPN) allows users working remotely to access and use applications and data residing in the corporate data center,headquarter offices, and cloud locations, often encrypting all user traffic.
How do remote access VPNs work?
Remote access VPNs create virtually 'private' tunnels between an organization's network and a remote user, regardless of the user's location.
Why are remote access VPNs becoming obsolete?
The days of network-centric security are over. For almost three decades, enterprises have relied on castle-and-moat methods to connect users to the network, and by extension, the applications running on it.
Why is a SASE approach better than remote access VPN?
SASE is a framework identified by Gartner as the way to securely connect entities such as users and devices to applications and services when their locations may be anywhere.
Why is zero trust network access (ZTNA) preferred over remote access VPN?
Zero trust network access (ZTNA) takes a user- and application-centric approach to private application access, ensuring that only authorized users have access to specific private applications by creating secure segments of one between individual devices and apps. That means no more network access, no more lateral movement.
What is Zscaler Private Access (ZPA)?
Zscaler Private Access (ZPA) is a cloud service from Zscaler that provides seamless, zero trust access to private applications running on the public cloud or within the data center. With ZPA, applications are never exposed to the internet, making them completely invisible to unauthorized users.
Why is ZPA superior to remote access VPN?
In contrast to VPN, ZPA is a more modern, robust security solution offering the following benefits:
Why are VPNs so secure?
While VPNs provide traffic encryption and user authentication, they still present a security risk because they grant access to the entire network without the option of controlling granular user access to specific resources. There is no scrutiny of the security posture of the connecting device, which could allow malware to enter the network. To maintain proper security, traffic must be routed through a security stack at the VPN’s terminus on the network. In addition to inefficient routing and increased network latency, this can result in having to purchase, deploy, monitor, and maintain security stacks at multiple sites to decentralize the security load. Simply put, VPNs are a challenge – an expensive one at that – when it comes to remote access security.
What is a SASE network?
SASE converges Zero Trust Network Access, NextGen firewall (NGFW), and other security services along with network services such as SD-WAN, WAN optimization, and bandwidth aggregation into a cloud-native platform. Enterprises that leverage a SASE networking architecture receive the benefits of ZTNA, plus a full suite of converged network and security solutions that is both simple to manage and highly-scalable. The Cato SASE solution provides all this in a cloud-native platform.
What is remote access VPN?
What Is a Remote Access VPN? A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive. The remote access VPN does this by creating a tunnel between an ...
Why is VPN remote access?
The remote access VPN does this by creating a tunnel between an organization’s network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
Does SASE require a VPN?
Using SASE, an organization does not have to maintain a separate stand-alone proxy or VPN. Rather, users connect to a SASE solution (which provides access to the cloud and data center) with consistent security. Some advantages of using a SASE are that it allows companies to:
Why are VPNs so secure?
While VPNs provide traffic encryption and user authentication, they still present a security risk because they grant access to the entire network without the option of controlling granular user access to specific resources. There is no scrutiny of the security posture of the connecting device, which could allow malware to enter the network. To maintain proper security, traffic must be routed through a security stack at the VPN’s terminus on the network. In addition to inefficient routing and increased network latency, this can result in having to purchase, deploy, monitor, and maintain security stacks at multiple sites to decentralize the security load. Simply put, VPNs are a challenge – an expensive one at that – when it comes to remote access security.
What does SASE mean for remote access?
What does this mean for the remote access worker? SASE makes it very quick and easy to give optimized and highly secure access to any and all workers. For users in the office, access can be limited only to designated resources, complying with zero-trust principles.
What is a SASE network?
SASE converges Zero Trust Network Access, NextGen firewall (NGFW), and other security services along with network services such as SD-WAN, WAN optimization, and bandwidth aggregation into a cloud-native platform. Enterprises that leverage a SASE networking architecture receive the benefits of ZTNA, plus a full suite of converged network and security solutions that is both simple to manage and highly-scalable. SASE provides all this in a cloud-native platform.
What is Cisco VPN deployment guide?
This deployment guide is a reference design for Cisco customers and partners. It covers the Internet edge remote access VPN component of Borderless Networks and is meant to be used in conjunction with the Cisco SBA—Borderless Networks Firewall and IPS Deployment Guide in addition to the MPLS WAN Deployment Guide, which can be found here:
What is Cisco AnyConnect client profile?
Cisco AnyConnect Client Profile is the location where the newer configura-tion of the Cisco AnyConnect client is defined . Cisco AnyConnect 2.5 and later use the configuration in this section, including many of the newest features added to the Cisco AnyConnect client.
What is Cisco ASA?
Cisco ASA advertises each connected user to the rest of the network as individual host routes. Summarizing the address pool reduces the IP route table size for easier troubleshooting and faster recovery from failures.
What is step 16 in VPN?
Step16: Repeat the export in PEM format. This format is used for distribu-tion to VPN client devices when using self-signed certificates. A secure passphrase is not used with the PEM format.
How does Cisco AnyConnect work?
The Cisco AnyConnect client’s initial connection is typically launched with a web browser. After the client is installed on a user’s computer, subsequent connections can be established through the web browser again or directly through the Cisco AnyConnect client, which is now installed on the user’s computer. The user needs the IP address or DNS name of the appliance, a username and password, and the name of the VPN group to which they are assigned. Alternatively, the user can directly access the VPN group with the group-url, after which they need to provide their username and password.
What is Cisco Borderless Networks?
Cisco SBA Borderless Networks is a solid network foundation designed to provide networks with up to 10,000 connected users the flexibility to sup-port new users and network services without re-engineering the network. We created a prescriptive, out-of-the-box deployment guide that is based on best-practice design principles and that delivers flexibility and scalability.
Does Cisco ASDM require HTTPS?
Cisco ASDM requires that the appliance’s HTTPS server be available. Be sure that the configuration includes networks where administrative staff has access to the device through Cisco ASDM; the appliance can offer controlled Cisco ASDM access for a single address or management subnet (in this case, 10.4.48.0/24).
What is VPN configuration?
The VPN configuration requires an Active Directory-based public key infrastructure (PKI). Organizations can use AD CS to enhance security by binding the identity of a person, device, or service to a corresponding public key.
What is VPNv2 CSP?
Also contained in the VPNv2 CSP is a node called ProfileXML, which allows you to configure all the settings in one node rather than individually. For more information about ProfileXML, see the section "ProfileXML overview" later in this deployment. For details about each VPNv2 CSP node, see the VPNv2 CSP.
What version of Windows 10 is the VPN?
In addition to the server components, ensure that the client computers you configure to use VPN are running Windows 10 Anniversary Update (version 1607). The Windows 10 VPN clients must be domain-joined to your Active Directory domain.
What is NPS in VPN?
When you use NPS as a Remote Authentication Dial-In User Service (RADIUS) server, you configure network access servers, such as VPN servers, as RADIUS clients in NPS.
What is an Active Directory user?
Active Directory Users and Computers is a component of AD DS that contains accounts that represent physical entities, such as a computer, a person, or a security group. A security group is a collection of user or computer accounts that administrators can manage as a single unit.
Can you use RAS gateway to access external resources?
With RAS Gateway, you can also create a site-to-site VPN connection between two servers at different locations, such as between your primary office and a branch office, and use Network Address Translation (NAT) so that users inside the network can access external resources, such as the Internet.
What are the advantages of a stand alone VPN?
How healthy the budget is might determine that. One of the advantages of purchasing a stand alone specialty VPN appliances is that ' typically ' they might have more flexibility when it comes to user policy and security settings. Some appliances also might have more robust client applications.
Why is SSL VPN called SSL VPN?
I believe the name SSL VPN came back from the inception of the concept because users would connect via a web browser using SSL to a web page to login. Although the web page based VPN method is still used, most vendors have released client applications that install on a computer which facilitates the secure connection.
Is remote access part of a business continuity plan?
In general remote access should be a part of a business continuity plan. That alone could be the reason you justify deployment, which would mean you'd need to ensure there is some language about remote access and how the design works to meet the BC plan needs.
