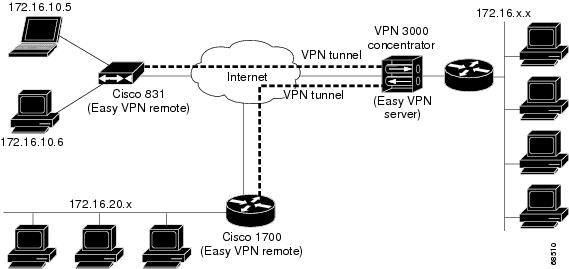
Configuring a VPN Using Easy VPN and an IPSec Tunnel
| 1 | Remote, networked users |
| 2 | VPN client—Cisco 870 series access route ... |
| 3 | Router—Providing the corporate office ne ... |
| 4 | VPN server—Easy VPN server; for example, ... |
| 5 | Corporate office with a network address ... |
Full Answer
How to enable Cisco AnyConnect VPN through remote desktop?
To enable Cisco Anyconnect VPN through a remote desktop you must first create an Anyconnect Client Profile. The client profile is basically a XML file that gets pushed out to the client upon VPN establishment. This XML file can be created using a text editor or ASDM. I wouldn’t recommend using anything but the ASDM to create this file as you will see.
How to connect to Cisco router using telnet?
- The “ line vty ” command enable the telnet and the “ 0″ is just let a single line or session to the router. ...
- The “ password ” command set the “ Pass123 ” as a password for telnet. ...
- The “ login ” command authenticate and ask you the password of telnet. ...
- The “ logging synchronous ” command stops any message output from splitting your typing.
What is Cisco Systems VPN client?
Cisco Systems VPN Client is a software application for connecting to virtual private networks based on Internet Key Exchange version 1.. On July 29, 2011, Cisco announced the end of life of the product. No further product updates were released after July 30, 2012, and support ceased on July 29, 2014. The Support page with documentation links was taken down on July 30, 2016, replaced with an ...
How to configure Cisco IP SLA?
These steps are:
- Creating IP SLA Operation
- Configure IP SLA Operation as ICMP Echo
- Set repeat frequency
- Configure Schedule
- Save The configuration

What is remote access VPN Cisco?
This allows remote users to connect to the ASA and access the remote network through an IPsec encrypted tunnel. The remote user requires the Cisco VPN client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network.
Can VPN be accessed remotely?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
How do I setup a VPN on my Cisco router?
Let us examine each of the above steps.Step 1: Creating Extended ACL. Next step is to create an access-list and define the traffic we would like the router to pass through the VPN tunnel. ... Step 2: Create IPSec Transform (ISAKMP Phase 2 policy) ... Step 3: Create Crypto Map. ... Step 4: Apply Crypto Map to the Public Interface.
Do Cisco routers have VPN?
Remote VPN access is an extremely popular service amongst Cisco routers and ASA Firewalls. The flexibility of having remote access to our corporate network and its resources literally from anywhere in the world, has proven extremely useful and in many cases irreplaceable.
How do I remotely log into a VPN?
Simply go to Start -> Accessories -> Remote Desktop Connection and enter the IP address of the other Windows computer. desktop software. From HOME Mac to OFFICE Windows: Connect with VPN, then use Remote Desktop Client. From HOME Windows to OFFICE Mac: Connect with VPN, then use VNC client.
Which VPN is best for remote access?
Perimeter 81 – Best all-round business VPN. Jul 2022. ... GoodAccess – Security Strategy Options. Apps Available: ... ExpressVPN – Lightning Fast VPN. ... Windscribe – VPN with Enterprise-Friendly Features. ... VyprVPN – Secure VPN with Business Packages. ... NordVPN – Security-first VPN. ... Surfshark – VPN with Unlimited User Connections.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What is Cisco Ezvpn?
Cisco Easy VPN is a convenient method to allow remote users to connect to your network using IPsec VPN tunnels. The advantage of Easy VPN is that you don't have to worry about all the IPSEC security details on the client side. Just configure the remote router, group name, username /password and you are ready to go.
What are the two types of VPN connections choose two?
Virtual Private Network (VPN) is basically of 2 types:Remote Access VPN: Remote Access VPN permits a user to connect to a private network and access all its services and resources remotely. ... Site to Site VPN: A Site-to-Site VPN is also called as Router-to-Router VPN and is commonly used in the large companies.
How do I setup a VPN tunnel?
Preshared key authenticationIn the administration interface, go to Interfaces.Click Add > VPN Tunnel.Type a name of the new tunnel.Set the tunnel as active and type the hostname of the remote endpoint. ... Select Type: IPsec.Select Preshared key and type the key.More items...
How do I see tunnels on my Cisco router?
From the Wired Client, browse to http://dcloud.cisco.com/ to access the Cisco dCloud UI and then log in with your Cisco.com credentials. Use the Bandwidth Test to verify that the port needed for VPN connectivity (TCP 443) is not blocked at your site. From the Wired Client, ping AD1 at 198.18. 133.1.
How do I enable IPsec on my router?
Choose the menu Status > System Status and Network > LAN. Check the VPN Router B. Choose the menu Status > System Status and Network > LAN. (1) Choose the menu VPN > IPSec > IPSec Policy and click Add to load the following page on the VPN router.
What does a VPN do when working remotely?
A VPN allows remote employees to become an extension of the network as if they're in the office with the same security and connectivity benefits. Think of it as a secure network line from a user to applications, whether those applications reside in a private data center or on a public network.
How can I access a private network remotely?
The best solution that will allow organizations to access files remotely is to set-up a virtual private network (VPN). A VPN provides a cable-like connection via the Internet between a remote PC and your office's server.
What are the disadvantages of using a VPN?
The 10 biggest VPN disadvantages are:A VPN won't give you complete anonymity: Read more.Your privacy isn't always guaranteed: Read more.Using a VPN is illegal in some countries: Read more.A safe, top-quality VPN will cost you money: Read more.VPNs almost always slow your connection speed: Read more.More items...•
What is the difference between a site-to-site VPN and a remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
What is VPN on Cisco router?
This chapter explains the basic tasks for configuring an IP-based, remote access Virtual Private Network (VPN) on a Cisco 7200 series router. In the remote access VPN business scenario, a remote user running VPN client software on a PC establishes a connection to the headquarters Cisco 7200 series router.
What is Cisco IOS firewall proxy?
Using the Cisco IOS firewall authentication proxy feature , network administrators can apply specific security policies on a per-user basis. Users can be identified and authorized on the basis of their per-user policy, and access privileges tailored on an individual basis are possible, in contrast with general policy applied across multiple users.
What are the two types of VPNs?
Two types of VPNs are supported—site-to-site and remote access. Site-to-site VPNs are used to connect branch offices to corporate offices, for example. Remote access VPNs are used by remote clients to log in to a corporate network. The example in this chapter illustrates the configuration of a remote access VPN that uses ...
What is a Cisco 870 router?
The Cisco 870 series routers support the creation of Virtual Private Networks (VPNs). Cisco routers and other broadband devices provide high-performance connections to the Internet, but many applications also require the security of VPN connections which perform a high level of authentication and which encrypt the data between two particular ...
Does Cisco ASA support PPTP?
Cisco supports PPTP on its IOS routers. Cisco ASA firewalls do not support termination of PPTP on the firewall itself.
Can a remote user use PPTP?
Like other types of remote access solutions, a remote user can use PPTP to connect to a corporate network and be treated as directly connected to that internal network even if he/she is physically outside the network. PPTP is always implemented between a server (e.g a Cisco router) and a client (e.g a windows workstation).
Does PPTP work with IPSEC?
However, you should note that PPTP does not offer the strong encryption and security offered by IPSEC or SSL VPN remote access solutions. Although the Microsoft Point-to-Point Encryption (MPPE) supported by Cisco routers offers a good degree of security, PPTP remote access should not be used in situations where you need to provide access ...
What is Cisco IOS firewall?
Cisco IOS software provides an extensive set of security features with which you can configure a simple or elaborate firewall, according to your particular requirements. When you configure Cisco IOS firewall features on your Cisco router, you turn your router into an effective, robust firewall.
How does IPSec work?
In IPSec tunnel mode, the entire original IP datagram is encrypted, and it becomes the payload in a new IP packet. This mode allows a network device, such as a router, to act as an IPSec proxy. That is, the router performs encryption on behalf of the hosts. The source router encrypts packets and forwards them along the IPSec tunnel. The destination router decrypts the original IP datagram and forwards it on to the destination system. Tunnel mode protects against traffic analysis; with tunnel mode, an attacker can only determine the tunnel endpoints and not the true source and destination of the packets passing through the tunnel, even if they are the same as the tunnel endpoints.
What is IPSEC used for?
IPSec can be used to protect one or more data flows between a pair of hosts, between a pair of security Cisco 7200 series routers, or between a security Cisco 7200 series router and a host.
How to configure a policy map?
To configure a policy map and create class policies (including a default class) comprising the service policy, use the first global configuration command to specify the policy-map name. Then use the following policy-map configuration commands to configure policy for a standard class and the default class. For each class that you define, you can use one or more of the following policy-map configuration commands to configure class policy. For example, you might specify bandwidth for one class and both bandwidth and queue limit for another class.
Where is NAT configured?
NAT is configured on the router at the border of a stub domain (referred to as the inside network) and a public network such as the Internet (referred to as the outside network ). NAT translates the internal local addresses to globally unique IP addresses before sending packets to the outside network.
How does extranet work?
In the extranet scenario, the headquarters and business partner are connected through a secure IPSec tunnel and the business partner is given access only to the headquarters public server to perform various IP-based network tasks, such as placing and managing product orders.
Introduction
This document provides a sample configuration of how to configure an IOS/IOS-XE headend for remote access using AnyConnect IKEv2 and AnyConnect-EAP authentication method with local user database.
Background Information
AnyConnect-EAP, also known as aggregate authentication, allows a Flex Server to authenticate the AnyConnect client using the Cisco proprietary AnyConnect-EAP method.
Configure
Note: In order to authenticate users against the local database on the router, EAP needs to be used. However, in order to use EAP, the local authentication method has to be rsa-sig, so the router needs a proper certificate installed on it, and it can't be a self-signed certificate.
Verify
Use this section in order to confirm that your configuration works properly.
Troubleshoot
This section provides information you can use in order to troubleshoot your configuration.