What is a VPN?
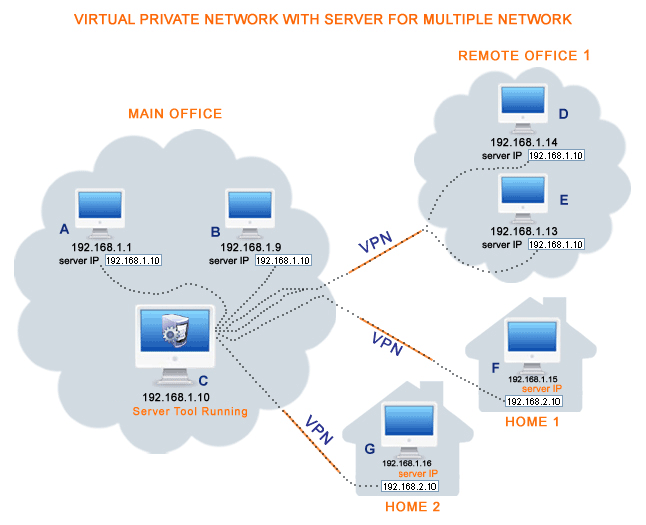
Computer and Network Examples A Virtual Private Network (VPN) is a network that allows the private networks at a remote location securely connect to the public Internet and provide access only to the intended recipients for transmitting data.
What is a remote access VPN?
What is a remote access VPN? Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
How secure is a VPN on a campus network?
The VPN server carries the transmissions securely into the wired part of the campus network. From that point on, however, the users' communications are subject to the same protections and vulnerabilities as any wired computer on the campus network. For more information, see Security and VPN.
How do I use a VPN on a NAS?
Users connect to the NAS over the internet in order to use a remote access VPN. In order to sign in to the VPN, the NAS requires that users provide valid credentials. To authenticate these credentials, the NAS uses either its own authentication process or a separate authentication server running on the network.

How does remote access work with VPN?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
Does VPN allow remote access?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
How do I setup a VPN remote access?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
What is VPN with diagram?
A VPN is a point-to-point connection between a VPN client and server, or a site-to-site connection between two VPN servers. In the diagram below the connection between the branch office and headquarters could be a permanent site to site VPN connection.
What is difference between VPN and RDP?
While RDP and VPN serve similar functions for remote access, VPNs allow users to access secure networks whereas RDP grants remote access to a specific computer. While useful to provide access to employees and third parties, this access is open-ended and unsecure.
What are the two types of VPN connections?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
What are the steps to setup a VPN?
Click on the Windows button, then head into “Settings” > “Network & Internet” > “VPN.” Click on “Add a VPN connection.” In the fields on the menu, select “Windows (built-in)” for your VPN provider.
Can I create my own VPN at home?
To create your own VPN for personal use, you have a few specific hosting options: Run the software on a cloud virtual private server. All cloud providers, from titans like Amazon Web Services to smaller operations like Vultr, offer cloud-hosted servers called VPSs.
What is VPN example?
VPNs are primarily used for remote access to a private network. For example, employees at a branch office could use a VPN to connect to the main office's internal network. Alternatively, a remote worker, who may be working from home, could need to connect to their company's internet or restricted applications.
What are VPN protocols?
A VPN protocol is a set of rules or instructions that will determine how your data routes between your computer (or other device) and the VPN server. VPN providers rely on protocols to ensure a stable and secure connection.
What type of protocols are used in VPNs?
6 common VPN protocolsOpenVPN. OpenVPN is a very popular and highly secure protocol used by many VPN providers. ... IPSec/IKEv2. IKEv2 sets the foundation for a secure VPN connection by establishing an authenticated and encrypted connection. ... WireGuard. ... SSTP. ... L2TP/IPSec. ... PPTP.
What are the disadvantages of using a VPN?
The 10 biggest VPN disadvantages are:A VPN won't give you complete anonymity: Read more.Your privacy isn't always guaranteed: Read more.Using a VPN is illegal in some countries: Read more.A safe, top-quality VPN will cost you money: Read more.VPNs almost always slow your connection speed: Read more.More items...•
Is VPN more secure than remote desktop?
Virtual Private Network (VPN) Business networks can connect with each other, and remote workers can access sensitive data from a business network without exposure to unauthorized users. This is obviously more secure than an open, public Wi-Fi network, which offers no such protection.
Which VPN is best for Remote Desktop?
Best Remote Access VPNs for business.Perimeter 81 – Best all-round business VPN.GoodAccess – Security Strategy Options.ExpressVPN – Lightning Fast VPN.Windscribe – VPN with Enterprise-Friendly Features.VyprVPN – Secure VPN with Business Packages.NordVPN – Security-first VPN.More items...•
What is VPN in the internet?
A Virtual Private Network (VPN) is a network that allows the private networks at a remote location securely connect to the public Internet and provide access only to the intended recipients for transmitting data. VPN is built by creating the virtual point-to-point connection using the dedicated connections, traffic encryption or virtual tunneling protocols.
What is network virtualization?
Well known forms of network virtualization are virtual networks based on the virtual devices (for example the network based on the virtual devices inside a hypervisor), protocol-based virtual networks (VLAN, VPN, VPLS, Virtual Wireless network, etc.) and their combinations. This example was created in ConceptDraw DIAGRAM using ...
What is a vDS switch?
The VMware vNetwork Distributed Switch (vDS) is the new virtual switch (vSwitch) with vSphere 4 that extends the set of features of the VMware vNetwork Standard Switch (vSS). The VMware vSS is the base-level virtual networking alternative that extends the capabilities, configuration and appearance of the standard vSwitch in VMware ESX 3.5 to ESX 4.0 and vSphere 4.
What does VPN do?
Once the user authenticates and makes the encrypted connection to the VPN server, the VPN server handles unencrypted communication with the rest of the network and represents the original computer's identity as a part of the VPN-assigned network address range.
What is VPN server?
The VPN server carries the transmissions securely into the wired part of the campus network. From that point on, however, the users' communications are subject to the same protections and vulnerabilities as any wired computer on the campus network. For more information, see Security and VPN. Keywords:
What is the goal of VPN?
The goal of the VPN server is not to make transmissions end-to-end secure; the goal is to provide a secure connection from the computer off-campus back to campus, so that traffic traversing the Internet on it's way to campus is secure.
Can VPN users be placed in a firewall?
Systems can be placed in any campus firewall group, including Fully Closed, and VPN users will be provided access through the campus firewalls. The VPN IP space is defined as on-campus IP space, and the campus perimeter blocks won't apply to VPN users. Departmental firewalls: IP ranges.
A Picture-Perfect Deck
A uniquely designed pattern with an eye-catching vector presents the advantages of remote access VPN.
Feature-Rich Template
Easily and quickly scale and recolor the icons, illustrations, diagrams, and flowcharts to suit your requirements without extensive editing skills and support.
What are the advantages of a stand alone VPN?
How healthy the budget is might determine that. One of the advantages of purchasing a stand alone specialty VPN appliances is that ' typically ' they might have more flexibility when it comes to user policy and security settings. Some appliances also might have more robust client applications.
Why is SSL VPN called SSL VPN?
I believe the name SSL VPN came back from the inception of the concept because users would connect via a web browser using SSL to a web page to login. Although the web page based VPN method is still used, most vendors have released client applications that install on a computer which facilitates the secure connection.
Is remote access part of a business continuity plan?
In general remote access should be a part of a business continuity plan. That alone could be the reason you justify deployment, which would mean you'd need to ensure there is some language about remote access and how the design works to meet the BC plan needs.
What is a header in a VPN?
headers including fields that allow the VPN devices to make the traffic secure. The VPN devices also encrypt the original IP packet, meaning that the original packet’s contents are indecipherable to anyone who happens to see a copy of the packet as it traverses the Internet.
Can each branch have an internet connection?
However, each branch could instead have an Internet connection and use VPN technology, usually saving money over the other WAN options.
Is VPN as secure as WAN?
Security: Internet VPN solutions can be as secure as private WAN connections.
Does a VPN gateway encrypt data?
Whenever the host tries to send any information, the VPN client software encapsulates and encrypts the information before sending it over the Internet to the VPN gateway at the edge of the target network. On receipt, the VPN gateway handles the data in the same way as it would handle data from a site-to-site VPN.
What is remote access VPN?
What is a remote access VPN? Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What are the advantages of remote access VPN?
Another advantage of remote access VPNs is that they provide companies with an affordable way to secure data sent by offsite employees. The initial investment needed to set up a remote access VPN is minimal and they can easily be scaled as a company grows and this is especially true if a VPN service provider is used.
Why is VPN important for business?
The most important benefit though is data security. When an offsite employee sends data through a VPN, it is encrypted, so even if a hacker is able to intercept that data, they won’t be able to use it. This is particularly important if an employee accesses their companies’ network using public Wi-Fi while traveling because traffic sent over these networks is usually not encrypted.
How does a NAS work?
Users connect to the NAS over the internet in order to use a remote access VPN. In order to sign in to the VPN, the NAS requires that users provide valid credentials. To authenticate these credentials, the NAS uses either its own authentication process or a separate authentication server running on the network .
What is a network access server?
A network access server could be a dedicated server or it might be a software application running on a shared server. Users connect to the NAS over the internet in order to use a remote access VPN. In order to sign in to the VPN, the NAS requires that users provide valid credentials. To authenticate these credentials, the NAS uses either its own authentication process or a separate authentication server running on the network.
Why do businesses use VPNs?
Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What is site to site VPN?
A site-to-site VPN uses a secure gateway to connect a network at one location to one or more networks at another location. This type of VPN doesn’t require each device at the end location to have a VPN client installed because the gateway handles the traffic.