
Sophos Firewall: How to Configure remote access SSL VPN with Sophos Connect client.
- Create a user group and add a user. Go to Authentication > Groups and click Add. ...
- Create IP hosts for local subnet and remote SSL VPN clients. Create Local Subnet: Go to Hosts and Services > IP Host > Add. ...
- Add an SSL VPN remote access policy. ...
- Check authentication services. ...
- Add a firewall rule. ...
Full Answer
What is remote access VPN and how does it work?
Remote Access VPN ensures that the connections between corporate networks and remote and mobile devices are secure and can be accessed virtually anywhere users are located. A secure remote access solution promotes collaboration by connecting global virtual teams at headquarters, branch offices, remote locations, or mobile users on the go.
How do I grant remote access to a VPN Server?
Select the Grant access. Grant access if the connection request matches this policy option. c. Under Type of network access server, select Remote Access Server (VPN-Dial up) from the drop-down. In the Routing and Remote Access MMC, right-click Ports, and then select Properties.
How do I deploy a VPN on a Windows Server?
Select Deploy VPN only. The Routing and Remote Access Microsoft Management Console (MMC) opens. Right-click the VPN server, then select Configure and Enable Routing and Remote Access. The Routing and Remote Access Server Setup Wizard opens. In the Welcome to the Routing and Remote Access Server Setup Wizard, select Next.
What is a remote access virtual private network?
A remote access virtual private network enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
Does VPN allow remote access?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
Is VPN same as remote access?
Flexibility. While having some similarities, VPN and remote desktop are functionally different things. A VPN will give you access to a network while remote desktop (or RDP) will give you control of an entire computer.
How does remote access work with VPN?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
Do you need VPN for remote access?
No, but they serve a similar function. A VPN lets you access a secure network. RDP lets you remotely access a specific computer. Both will (usually) encrypt your traffic in one way or another, and both will grant you private access to a server or device that might be thousands of miles away.
Why would you use RDS instead of VPN?
VPN – Virtual Private Network encrypts your data and masks the IP address so that no malicious hacker can access the data and detect your location. The data is decrypted only at the intended destination. RDS – In RDS, the data is stored on the remote server and not on the end-point device.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
Which VPN is best for remote access?
Perimeter 81 – Best all-round business VPN. Jul 2022. ... GoodAccess – Security Strategy Options. Apps Available: ... ExpressVPN – Lightning Fast VPN. ... Windscribe – VPN with Enterprise-Friendly Features. ... VyprVPN – Secure VPN with Business Packages. ... NordVPN – Security-first VPN. ... Surfshark – VPN with Unlimited User Connections.
What are the disadvantages of VPN?
VPN disadvantages#1: Not designed for continuous use. The use case for remote access VPN was never to connect an entire enterprise to the WAN. ... #2: Complexity impedes scalability. ... #3: Lack of granular security. ... #4: Unpredictable performance. ... #5: Unreliable availability.
Which is better VPN or remote desktop?
Security. Although both VPN and RDP are encrypted through internet connection, a VPN connection is less accessible to threats than a remote desktop connection. For this reason, VPN is often considered more secure than RDP.
Which is better VPN or remote desktop?
Security. Although both VPN and RDP are encrypted through internet connection, a VPN connection is less accessible to threats than a remote desktop connection. For this reason, VPN is often considered more secure than RDP.
Which VPN is best for remote access?
Perimeter 81 – Best all-round business VPN. Jul 2022. ... GoodAccess – Security Strategy Options. Apps Available: ... ExpressVPN – Lightning Fast VPN. ... Windscribe – VPN with Enterprise-Friendly Features. ... VyprVPN – Secure VPN with Business Packages. ... NordVPN – Security-first VPN. ... Surfshark – VPN with Unlimited User Connections.
What are the two types of VPN connections?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
Is Chrome remote desktop a VPN?
Chrome Remote Desktop - A Better VPN and RDP Solution.
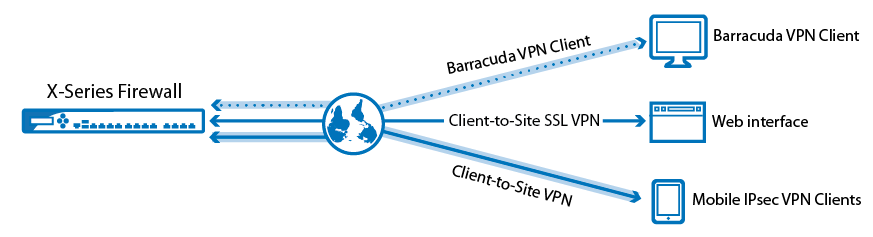
Remote Access VPN Products
Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser.
What is Remote Access VPN?
Remote Access VPN ensures that the connections between corporate networks and remote and mobile devices are secure and can be accessed virtually anywhere users are located. A secure remote access solution promotes collaboration by connecting global virtual teams at headquarters, branch offices, remote locations, or mobile users on the go.
Technical Resources
The place to discuss all of Check Point’s Remote Access VPN solutions, including Mobile Access Software Blade, Endpoint Remote Access VPN, SNX, Capsule Connect, and more!
Our Customers Love Us
Versatile Security Protection –Like A Swiss Army Knife For Security Checkpoint Next Generation Firewall proves to be a great solution for our small business infrastructure. R80 Security Management has allowed our company to easily (and significantly) improve our protections over time. read more >
Quantum is powered by ThreatCloud
ThreatCloud, the brain behind all of Check Point’s products, combines the latest AI technologies with big data threat intelligence to prevent the most advanced attacks, while reducing false positives.
How to install Remote Access Role in VPN?
On the VPN server, in Server Manager, select Manage and select Add Roles and Features. The Add Roles and Features Wizard opens. On the Before you begin page, select Next.
How to start remote access?
Select Start service to start Remote Access. In the Remote Access MMC, right-click the VPN server, then select Properties. In Properties, select the Security tab and do: a. Select Authentication provider and select RADIUS Authentication.
How to select a server from the server pool?
On the Select destination server page, select the Select a server from the server pool option. Under Server Pool, select the local computer and select Next. On the Select server roles page, in Roles, select Remote Access, then Next. On the Select features page, select Next. On the Remote Access page, select Next.
How many Ethernet adapters are needed for VPN?
Install two Ethernet network adapters in the physical server. If you are installing the VPN server on a VM, you must create two External virtual switches, one for each physical network adapter; and then create two virtual network adapters for the VM, with each network adapter connected to one virtual switch.
What is NAS in a network?
A NAS is a device that provides some level of access to a larger network. A NAS using a RADIUS infrastructure is also a RADIUS client, sending connection requests and accounting messages to a RADIUS server for authentication, authorization, and accounting. Review the setting for Accounting provider: Table 1.
Can you assign a VPN to a pool?
Additionally, configure the server to assign addresses to VPN clients from a static address pool. You can feasibly assign addresses from either a pool or a DHCP server; however, using a DHCP server adds complexity to the design and delivers minimal benefits.
Is RRAS a router or a server?
RRAS is designed to perform well as both a router and a remote access server because it supports a wide array of features. For the purposes of this deployment, you require only a small subset of these features: support for IKEv2 VPN connections and LAN routing.
What is Cisco Secure Endpoint?
Cisco Secure Endpoint New packages fit for every organization Every Cisco Secure Endpoint (formerly AMP for Endpoints) package comes with Cisco SecureX built-in. It’s our cloud-native platform that integrates all your security solutions into one view wit... view more
What is TCP port?
It tcp is used is it is a configureable port on the gateway, so whatever port is opened needs to be allowed thru. 2. If the vpn gateway is behind a nat/pat device, or if it expects clients to be behind a nat/pat device, then configure the gateway to allow nat-t, which means nat transversal. This will allow the gateway to strip off ...
What is a personal firewall?
Some equate "personal" with host-based firewalls, while others extend the definition to include off-box firewalls or hardware appliances if they're designed to protect only a single home computer or small network. In the context of this article, we'll use the broader definition and include the low-cost so-called "telecommuter" and "SOHO" appliances offered by many major firewall vendors.
How much does Norton Personal Firewall cost?
It allows configuration of different firewall settings for different network, something that can be handy for laptops that connect to more than one network. It includes intrusion detection and privacy control, and uses LiveUpdate to automatically check for updates online. List price is $49.95.
How much does Netscreen 5XP cost?
Cost starts at just under $500.
Does Windows XP have a firewall?
The Windows firewall (formerly known as Internet Connection Firewall or ICF) built into Windows XP. This choice has a couple of important advantages: it comes with Windows so there's nothing to install, and it doesn't cost extra. It's a pretty rudimentary firewall but sufficient for most home users, and XP Service Pack 2 (SP2) makes some improvements to the firewall (we'll discuss these in detail in a future article).
What is site to site VPN?
A site-to-site VPN is a connection between two or more networks, such as a corporate network and a branch office network. Site-to-site VPNs are frequently used by companies with multiple offices in different geographic locations that need to access and use the corporate network on an ongoing basis.
What is remote access?
Remote access provides end users with the ability to access resources on the corporate network from a distant location. The most common function of remote access is to enable employees who are traveling or telecommuting to connect to the company network and access resources such as internal applications, intranet, mail services and file sharing.
How does VPN work?
The VPN will forward device traffic to and from the intended website or network through its secure connection. This allows your remote users and offices to connect securely to a corporate network or website. It also hides your IP addresses from hackers and prying eyes.
Why is VPN important?
A VPN establishes the secure connection necessary for enabling the mobile workforce.
What is VPN tunnel?
As mentioned above, a VPN creates a private connection known as a tunnel. All information traveling from a device connected to a VPN will get encrypted and go through this tunnel. When connected to a VPN, a device behaves as if it’s on the same local network as the VPN.
How to secure remote workforce?
The only way to secure your remote workforce is a secure VPN. Employees must connect from their laptops, desktops and mobile devices over a VPN connection. It’s the secure, private method for virtually entering the corporate office, so to speak. In many cases, remote workforce technology requires hardware.
Why do people use VPNs?
A VPN makes your internet connection more secure and offers privacy online. Organizations, governments and businesses of all sizes use VPNs to secure remote connections to the internet for protection against malicious actors, malware and other cyberthreats. Personal VPNs have also become widely popular as they keep users’ locations private, safely encrypt data and allow users to browse the internet anonymously.
What’s A Personal Firewall and Who Needs One?
Enforcing Personal Firewall Policy
- All that is well and good, but how do you enforce the policy over computers that aren’t under your physical control? The best way is via your own corporate firewall or VPN/remote access server. The latest products of most major vendors include a feature that allows you to block connections if the remote client doesn’t meet your specified criteria. ...
Picking A Personal Firewall
- Of course, you could just allow your remote users to pick whatever personal firewall they like (after all, any firewall is better than no firewall), but the best practice is to have them all use the same one. After all, you’ll probably be called on to support it when they have problems. That’s easier to do when their computer hardware is issued by the company. If it belongs to them, you …
Summary
- There are a plethora of software- and hardware-based firewall products available that are designed with the telecommuter in mind, and can provide vital protection to the computers that connect to your network via remote access. Your organization should develop a written policy requiring personal firewall protection (and other protections such as anti-virus and up-to-date se…