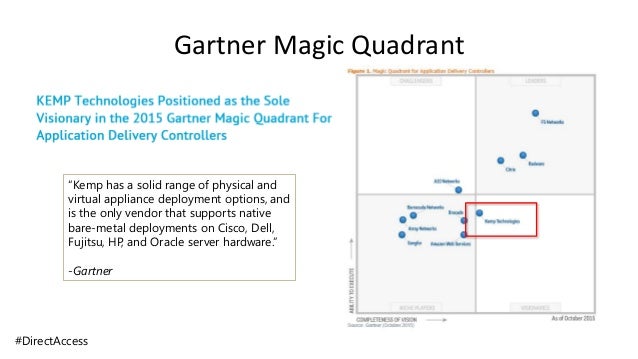
According to Gartner by 2022, 80% of new digital business applications opened up to ecosystem partners will be accessed through zero trust network access (ZTNA), and by 2023 60% of enterprises will phase out their remote access virtual private networks (VPN
Virtual private network
A virtual private network extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running on a computing device, e.g. …
Full Answer
What is a virtual private network (VPN)?
Virtual private networks (VPNs) are products and services used to achieve security and confidentiality for data in motion by means of encryption and access controls. Solutions may be implemented in software on end-user devices, servers and appliances.
Where do VPN communications occur in a virtual environment?
In the case of virtual environments and multitenant architectures, VPN communications may occur within a server hosting the equivalent of several sites and tenants. AnyConnect from Cisco is a industry-wide used software to connect to internet and VPN services.
What are Gartner Peer Insights reviews?
Gartner Peer Insights reviews constitute the subjective opinions of individual end users based on their own experiences, and do not represent the views of Gartner or its affiliates.
What is your primary use case for a mobile VPN?
Mobile VPN with SSL allows your travelling employees to connect to your corporate network with a high security. very cost effective. Very good experience with using sentry. The logs from all microservices are sent to sentry even those of the UI and it is a one shop stop to monitor the status of applications as a whose i production.

4 questions to ask before you deploy
As companies support more work-from-home employees, they must have the right technology in place to ensure avoid poor performance and ensure secure access. Ask these four questions before deploying modern high-volume remote access products.
Build a remote access end-user policy
After determining use cases and technology, build an end-user remote access policy with buy-in from all business units. If this is an urgent issue, like COVID-19, the policy must be escalated to legal counsel.
Experience Information Technology conferences
Join your peers for the unveiling of the latest insights at Gartner conferences.
Subscribe to the Latest Insight
By clicking the "Continue" button, you are agreeing to the Gartner Terms of Use and Privacy Policy.
What VPN gateways are needed for IaaS?
On-premises and IaaS-hosted applications might require a combination of on-premises VPN and ZTNA or cloud-hosted VPN gateway.
Is Gartner a registered trademark?
Disclaimer: GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Is Netmotion a single platform?
Our view is that NetMotion stands alone in meeting Gartner’s optimum criteria for most organizations in a single platform, offering the best of both remote access technologies as businesses and public sector bodies slowly migrate to the cloud.
Is remote access VPN a dying technology?
Remote access VPN was thought of as a dying technology until COVID-19 changed the way people work.
Is Netmotion a VPN?
NetMotion is the only major vendor on the market to provide the 98% of organizations that have a blend of on-premise and cloud application with a ZTNA and a VPN solution as part of the same platform.
What is VPN vulnerability?
The solution to the gaping problems exposed by VPN weaknesses is a system that does not create any trust between the remote worker devices and company network; and which authenticates remote workers in the cloud or away from company network before granting access to only authorized systems. Systems that fit this category are often referred to as Zero-Trust Network Access.
What is the flaw of VPN?
The original flaw of the VPN is that it establishes too much trust between the remote device and the corporate network. While the VPN tunnel between a remote worker and corporate network is cryptographically secure, the trust between the two is easily exploited. As a result, threats (including ransomware) affecting the remote worker device or network can travel to, and infect, the corporate network. Segmenting a company network to limit access over VPN is an arduous task and does not guarantee security from lateral threat movements.
Why do VPN gateways need to be patched?
Like all technologies, VPN gateways need to be constantly patched to improve security. However, because they are exposed to the entire world, they are far more targeted than most systems. As a result, VPN needs to be updated more frequently. The challenge is that many companies rely on their VPN to be up at all hours of ...