IPsec VPN vs. SSL VPN: Is Your Remote Access VPN a Liability?
- IPsec VPN. IPsec has been around for decades and is the tried-and-true solution. As time goes on, IPsec adapts by adding...
- SSL VPN. The new hotness in terms of VPN is secure socket layer (SSL). You can use an SSL VPN to securely connect via a...
- Additional Security Considerations. For both SSL and IPsec VPNs,...
What is the difference between IPsec and SSL VPN?
The new hotness in terms of VPN is secure socket layer (SSL). You can use an SSL VPN to securely connect via a remote access tunnel, a layer 7 connection to a specific application. SSL is typically much more versatile than IPsec, but with that versatility comes additional risk.
What is IPsec and why is it used?
IPsec is often used to set up virtual private networks (VPNs). A VPN is an Internet security service that allows users to access the Internet as though they were connected to a private network. VPNs encrypt Internet communications as well as providing a strong degree of anonymity.
Which VPN protocol is the most secure?
Many VPN protocols and encryption algorithms have come and gone, like PPTP, modem banks, DES and so on. In today’s world there are two heavyweights in the realm of maximum security, support and functionality: IPsec and SSL. IPsec has been around for decades and is the tried-and-true solution.
How many IPsec VPNs can be set up from one source IP?
-From user's aspect, only one IPsec vpn can be established from one source IP. You can't set two IPsecs up behind the same NAT, like two employees at the same hotel trying to setup a VPN from their laptops. Only one comes through. With SSL VPN, it doesn't matter.

Which is better SSL VPN or IPsec VPN?
When it comes to corporate VPNs that provide access to a company network rather than the internet, the general consensus is that IPSec is preferable for site-to-site VPNs, and SSL is better for remote access.
What is difference between SSL VPN and remote access VPN?
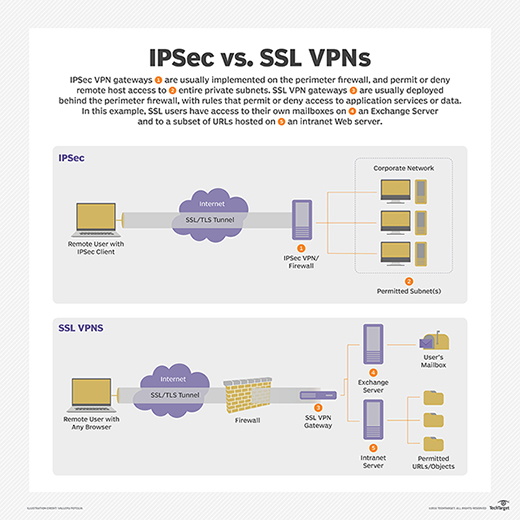
Whereas an IPsec VPN enables connections between an authorized remote host and any system inside the enterprise perimeter, an SSL VPN can be configured to enable connections only between authorized remote hosts and specific services offered inside the enterprise perimeter.
Is SSL VPN more secure than IPsec?
Once a user is logged into the network, SSL takes the upper hand in security. SSL VPNs work by accessing specific applications whereas IPsec users are treated as full members of the network. It's therefore easier to restrict user access with SSL.
Does remote access VPN use IPsec?
While Remote access VPN supports SSL and IPsec technology.
Why would you use IPsec Instead of SSL?
The main difference between IPsec and SSL VPNs is the endpoints for each protocol. While an IPsec VPN allows users to connect remotely to an entire network and all its applications, SSL VPNs give users remote tunneling access to a specific system or application on the network.
Is Cisco Anyconnect IPsec or SSL?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN.
Can IPsec be hacked?
Hackers Could Decrypt IPsec Information However, a team of researchers discovered numerous security vulnerabilities related to an internet key exchange protocol called “IKEv1.” IPsec maintains encrypted connections between two parties when both of them define and exchange shared keys during communications.
Which type of VPN is more secure?
OpenVPNMany VPN experts recommend OpenVPN as the most secure protocol. It uses 256-bit encryption as a default but also offers other ciphers such as 3DES (triple data encryption standard), Blowfish, CAST-128, and AES (Advanced Encryption Standard).
What is IPsec remote access?
The IPsec Remote Access feature introduces server support for the Cisco VPN Client (Release 4. x and 5. x) software clients and the Cisco VPN hardware clients. This feature allows remote users to establish the VPN tunnels to securely access the corporate network resources.
Why is SSL VPN slower than IPsec?
GlobalProtect is slower on SSL VPN because SSL requires more overhead than IPSec. Also, Transmission Control Protocol (TCP) is more prone to latency than User Datagram Protocol (UDP), which is used in IPsec GlobalProtect.
When should I use IPsec tunnel mode?
When to Use IPsec Tunnel ModeTunnel mode protects internal routing information by encrypting the original packet's IP header by creating a new IP header on top of it. ... Tunnel mode is mandatory when one of the peers is a security gateway applying IPsec on behalf of another host.More items...•
What is the difference between IPsec and TLS?
In other words, IPsec VPNs connect hosts or networks to a protected private network, while SSL/TLS VPNs securely connect a user's application session to services inside a protected network. IPsec VPNs can support all IP-based applications.
What is an SSL VPN?
A secure sockets layer VPN (SSL VPN) enables individual users to access an organization's network, client-server applications, and internal network utilities and directories without the need for specialized software.
How does SSL VPN Work?
SSL VPNs rely on the TLS protocol, which has replaced the older SSL protocol, to secure remote access. SSL VPNs enable authenticated users to establish secure connections to internal HTTP and HTTPS services via standard web browsers or client applications that enable direct access to networks.
What are the types of VPN connections?
The four main types of VPN are:Remote access VPNs.Personal VPN services.Mobile VPNs.Site-to-site VPNs.
Is TLS and SSL the same?
Transport Layer Security (TLS) is the successor protocol to SSL. TLS is an improved version of SSL. It works in much the same way as the SSL, using encryption to protect the transfer of data and information. The two terms are often used interchangeably in the industry although SSL is still widely used.
What is IPsec used for?
More specifically, IPsec is a group of protocols that are used together to set up secure connections between devices at layer 3 of the OSI model (the network layer ). IPsec accomplishes this by scrambling all messages so that only authorized parties can understand them — a process known as encryption. IPsec is often used to set up virtual private ...
Where does IPsec work?
The IPsec protocol suite operates at the network layer of the OSI model. It runs directly on top of IP (the Internet Protocol), which is responsible for routing data packets.
What is Cloudflare's alternative to VPNs for access control?
Cloudflare Access enables organizations to control and secure access to internal applications without a VPN. Cloudflare Access puts applications behind Cloudflare's global network, helping both on-premise and cloud applications remain secure.
What is SSL/TLS?
Secure Sockets Layer (SSL) is a protocol for encrypting HTTP traffic, such as connections between user devices and web servers. Websites that use SSL encryption have https:// in their URLs instead of http://. SSL was replaced several years ago by Transport Layer Security (TLS), but the term "SSL" is still in common use for referring to the protocol.
Why do organizations use VPNs?
VPNs are commonly used for access control, because no one outside the VPN can see data within the VPN. Many large organizations need to set up different levels of access control — for instance, so that individual contributors do not have the same levels of access as executives.
What is access control?
Access control is a security term for policies that restrict user access to information, tools, and software. Properly implemented access control ensures that only the right people can access sensitive internal data and the software applications for viewing and editing that data. VPNs are commonly used for access control, because no one outside the VPN can see data within the VPN.
Why do people use VPN?
VPNs are often used to allow remote employees to securely access corporate data. Meanwhile, individual users may choose to use VPNs in order to protect their privacy.
Why is SSL better than IPsec?
SSL gives users more specific access than IPsec. Rather than becoming a full member of the network, remote team members are granted access to particular applications. This makes it simple to provide different levels of access to different users. Security is maintained by restricting access to only what’s needed.
How secure is VPN?
VPN access is protected by a password. It’s essential for users to select strong passwords with combinations of letters and numbers, upper- and lowercase, special characters, and no dictionary words. The most locked-down systems won’t let users choose a weak password. Two-factor authentication (2FA) makes VPNs even more secure. This method requires a one-time code—sent via text message or generated by a mobile app—in addition to the password to log in. Even if a hacker discovers the password, he or she won’t be able to access the VPN without the second code.
Why do VPNs use encryption?
Security is a key factor to consider when implementing remote access. The more outside connections there are to a network, the more opportunities arise for nefarious parties to intercept data being transmitted. That’s why IPsec protocols use encryption. IPsec encryption works by scrambling data in transit so it cannot be deciphered if intercepted. Data can only be read if the user has the correct key to mathematically unscramble it. VPNs also mask a user’s Internet Protocol (IP) address for further security. The VPN assigns a new IP address, hiding the user’s original address and making it harder for an internet service provider to track them.
What is SSL tunnel mode?
This mode can only be used for web-based programs. It’s ideal for email, chat, file sharing, and other browser-based applications. In tunnel mode, by contrast, users can access any applications on the network , ...
How does IPsec work?
IPsec encryption works by scrambling data in transit so it cannot be deciphered if intercepted. Data can only be read if the user has the correct key to mathematically unscramble it. VPNs also mask a user’s Internet Protocol (IP) address for further security.
What is IPsec in a network?
The purpose of IPsec is to give the remote computer direct access to the central network, making it a full member. Remote users have access to any file storage locations, programs, printers, and backups, exactly as if they were in the office. IPsec is therefore a robust system that gives users whatever resources they need, wherever they are located.
When did SSL replace TLS?
The SSL protocol was replaced by a successor technology, Transport Layer Security (TLS), in 2015, but the terms are interchangeable in common parlance and “SSL” is still widely used. SSL VPNs are implemented through the remote user’s web browser and do not require the installation of special software.
What is the difference between SSL and IPsec?
Basically, IPsec doesn’t use TLS for encryption. Another difference between SSL vs IPsec is that the latter does not specify encryption of connections by default, while the former defaults to traffic encryption.
Why use SSL VPN?
One of the benefits of using a VPN with SSL is data privacy and security. Since an SSL VPN uses standard technologies and web browsers, it offers users more secure access to enterprise applications remotely. VPN Unlimited uses SSL/TLS in the KeepSolid Wise that allows users to establish VPN connections even in networks that band VPNs.
What is IPsec used for?
It is a standard suite of protocols used by IETF (Internet Engineering Task Force). It is used to create a tunnel between two communication points. IPsec takes part in web packet encryption, decryption, and authentication, protecting communications by applying cryptographic security services.
What is SSL tunneling?
Tunneling via SSL uses a client to connect to a backend server.
Is SSL better than IPSEC?
Some experts consider SSL to be better for remote access and IPSec to be preferable for site-to-site VPNs. However, corporate VPNs, such as VPN Unlimited for Teams, have to provide access to a company network as well as secure the connection to the internet. To this end, VPN Unlimited uses both SSL/TSL (in KeepSolid Wise to bypass VPN blocking) and IPsec (as part of the IKEv2 protocol). So just use the one that suits your needs at any given moment.
Can you use VPN for remote work?
Still, remote work has certain requirements to be effective. For one, it implies employees accessing their company’s network wherever they work from. To this end, many organizations and individuals use VPNs (Virtual Private Networks) like VPN Unlimited. How do VPNs do it? Using technologies, such as SSL and IPsec. Wait, what was that we just said? Yeah, these can be somewhat puzzling. Take a look at our SSL vs IPsec comparison and figure it out!
Is VPN Unlimited part of MonoDefense?
Note: VPN Unlimited is also available as a part of the MonoDefense® security bundle.
How many phases does IPsec VPN go through?
Every IPsec VPN connection goes through two phases. During phase one of the connection, the VPN peer devices negotiate how the are going to encrypt and pass traffic. If you must use the Internet Key Exchange (IKEv1) protocol here, there are a couple of important things to remember.
How has VPN revolutionized the world?
The VPN has revolutionized the way we work. For over 20 years it’s allowed everyone from executives on down a company’s organizational chart to work anywhere, from home to the airport to the resort. (The debate of work/life balance versus always available connectivity will not be solved by me and not here.) This ability to connect almost anywhere in the world has not only revolutionized how we work, but it has saved many on-call engineers late-night trips to the datacenter.
What are the two major protocols that are used in VPN?
In today’s world there are two heavyweights in the realm of maximum security, support and functionality: IPsec and SSL.
What is PFS in IPsec?
Once you are in phase two of the IPsec process enable perfect forward secrecy (PFS) and Replay Detection to protect the tunnel once it is established.
Can you use Active Directory for VPN?
Most environments will leverage Active Directory as the authentication source for the VPN using either RADIUS or LDAP. Both protocol options are relatively easy to set up and it’s easy to forget to use the secure options for both. Once connected, a VPN client has access to the business network.
What is the difference between SSL and IPsec VPN?
The main difference between IPsec and SSL VPNs is the endpoints for each protocol. While an IPsec VPN allows users to connect remotely to an entire network and all its applications, SSL VPNs give users remote tunneling access to a specific system ...
What is SSL VPN?
SSL VPN. An SSL VPN (secure sockets layer) runs over the Internet like an IPsec VPN. However, it is usually running through the web browser (among other application layer protocols) instead of having to install an actual application on the client computer. This makes it much easier to manage.
Why is SSL VPN so popular?
SSL VPNs are becoming more and more popular because entire networks are moving to the cloud where the servers are virtually simulated in software instead of being a dedicated piece of hardware that sits in a specific location. In cloud networks, all the software is web-enabled, so the SSL VPN works just as the IPsec VPN does for physical networks.
What is VPN for?
VPNs (Virtual Private Networks) have been used for years for remote access to a network for users to their corporate or education networks. The end goal of a VPN is to provide remote users access to network resources. There are two main types of VPN software in existence today, IPsec and SSL. IPsec has been around for a long time, but SSL VPNs are gaining popularity thanks to software platforms shifting to the cloud as well as the popularity of web-based applications. Let’s take a more in-depth look at both types.
Why is VPN software so hard to manage?
VPN client software can be hard to manage because they need to be kept up to date and running on the appropriate version that the VPN appliance requires. IT staff is usually tasked with installing and maintaining the software, so some measure of control must be exerted over the software installed on the users’ machines.
Why is IPsec used?
it uses encryption algorithms and in some cases two-factor authentication (2FA) to provide maximum security.
What is the benefit of VPN?
The main benefit of an IPsec VPN is that you can access almost anything on the network that you could if you were locally connected such as servers, printers, and attached storage. IPSec operates at the Network Layer of the OSI model, meaning users have full access to their corporate network regardless of application. A good VPN setup should provide remote users with the opportunity to achieve the same level of productivity as if they are sitting at their desks connected to the LAN.
Authentication and access control
Accepted security best practice is to only allow access that is expressly permitted, denying everything else. This encompasses both authentication, making sure the entity communicating -- be it person, application or device -- is what it claims to be, and access control, mapping an identity to allowable actions and enforcing those limitations.
Defense against attacks
Both SSL/TLS and IPsec support block encryption algorithms, such as Triple DES, which are commonly used in VPNs. SSL/TLS VPNs also support stream encryption algorithms that are often used for web browsing. Given comparable key lengths, block encryption is less vulnerable to traffic analysis than stream encryption.
Client security
Your VPN -- IPsec or SSL/TLS -- is only as secure as the laptops, PCs or mobile devices connected to it. Without precautions, any client device can be used to attack your network.
Client vs. clientless
The primary allure of SSL/TLS VPNs is their use of standard browsers as clients for access to secure systems rather than having to install client software, but there are a number of factors to consider.
Integrating VPN gateways
Server-side issues tend to get lost amid the buzz about clientless savings, but understanding what's involved is essential in VPN product selection, secure system design and cost-effective deployment.
The test of time
Will it always be SSL/TLS VPN vs. IPsec VPN? It's quite likely that IPsec will remain attractive for groups needing the highest degree of security, requiring broader access to IT systems or to rich sets of legacy applications, and, of course, for site-to-site connectivity -- now often under the control of an software-defined WAN rather than a VPN.

Osi Model Layer
Implementation
- IPsec VPNs typically require installing VPN software on the computers of all users who will use the VPN. Users must log into and run this software in order to connect to the network and access their applications and data. In contrast, all web browsers already support SSL (whereas most devices are not automatically configured to support IPsec VPNs)....
Access Control
- Access controlis a security term for policies that restrict user access to information, tools, and software. Properly implemented access control ensures that only the right people can access sensitive internal data and the software applications for viewing and editing that data. VPNs are commonly used for access control, because no one outside the VPN can see data within the VP…
On-Premise vs. Cloud Applications
- Traditional on-premise applications run in an organization's internal infrastructure, such as an on-site data center. IPsec VPNs typically work best with these applications, as users access them via internal networks instead of over the public Internet, and IPsec functions at the network layer. Cloud-based applications, also called SaaS (Software-as-a-Service) applications, are accessed o…