Type of VPN and its protocols
- Remote Access VPN. A Remote Access VPN allows people to connect to a private network and remotely access all of its resources and services.
- Site-to-Site VPN. ...
- Protocols of Virtual Private Network (VPN) IPsec, or Internet Protocol Security, is a protocol used to secure Online communication over an IP network.
- PPTP. Point-to-Point Tunneling Protocol is one of the oldest VPN protocols in existence. ...
- L2TP/IPSec. Layer 2 Tunnel Protocol is a replacement of the PPTP VPN protocol. ...
- OpenVPN. ...
- SSTP. ...
- IKEv2.
What are the different types of remote access protocols?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
How do I grant remote access to a VPN Server?
Select the Grant access. Grant access if the connection request matches this policy option. c. Under Type of network access server, select Remote Access Server (VPN-Dial up) from the drop-down. In the Routing and Remote Access MMC, right-click Ports, and then select Properties.
What is PPTP VPN protocol?
PPTP is one of the most widely used VPN protocol and has been in use since the early release of Windows. PPTP is also used on Mac and Linux apart from Windows.
What is remote access VPN and how it works?
The connection between the user and the private network occurs through the Internet and the connection is secure and private. Remote Access VPN is useful for home users and business users both.
What protocol does VPN use?
6 common VPN protocolsOpenVPN. OpenVPN is a very popular and highly secure protocol used by many VPN providers. ... IPSec/IKEv2. IKEv2 sets the foundation for a secure VPN connection by establishing an authenticated and encrypted connection. ... WireGuard. ... SSTP. ... L2TP/IPSec. ... PPTP.
What are the 3 types of VPN?
VPNs can be divided into three main categories – remote access, intranet-based site-to-site, and extranet-based site-to-site. Individual users are most likely to encounter remote access VPNs, whereas big businesses often implement site-to-site VPNs for corporate purposes.
Does VPN allow remote access?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
How does remote access work with VPN?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What are the 5 types of VPN?
Here are five common VPN protocols and their primary benefits. PPTP. Point-to-Point Tunneling Protocol is one of the oldest VPN protocols in existence. ... L2TP/IPSec. Layer 2 Tunnel Protocol is a replacement of the PPTP VPN protocol. ... OpenVPN. ... SSTP. ... IKEv2.
What are four types of VPN?
Virtual Private Network (VPN) services fall into four main types: personal VPNs, remote access VPNs, mobile VPNs, and site-to-site VPNs....How Personal VPNs WorkInstall software from your VPN service provider onto your device. ... Connect to a server in your VPN provider's network.More items...•
Which VPN is best for remote access?
Perimeter 81 – Best all-round business VPN. Jul 2022. ... GoodAccess – Security Strategy Options. Apps Available: ... ExpressVPN – Lightning Fast VPN. ... Windscribe – VPN with Enterprise-Friendly Features. ... VyprVPN – Secure VPN with Business Packages. ... NordVPN – Security-first VPN. ... Surfshark – VPN with Unlimited User Connections.
What is the difference between VPN and remote access?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
What are the two types of VPN connections?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
How do I setup a VPN remote access?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What do you need for remote access?
Remote computer access requires a reliable internet connection. You'll need to activate or install software on the device you want to access, as well as on the device — or devices — you want to use to get that access.
How many types of VPNs are there?
Virtual Private Network (VPN) is basically of 2 types: Remote Access VPN: Remote Access VPN permits a user to connect to a private network and access all its services and resources remotely. The connection between the user and the private network occurs through the Internet and the connection is secure and private.
Which VPN is the best?
The Best VPN Service for 2022NordVPN - Best VPN for Privacy.Surfshark - Best VPN for Security.Private Internet Access VPN - Best VPN for Windows.IPVanish - Best VPN for Android.Ivacy - Most Affordable.Atlas VPN - Best Data Breach Monitoring.ExpressVPN - Best Encryption.PureVPN - Best Server Base.More items...
What is an example of a VPN?
Virtual Private Network Basics For example, employees at a branch office could use a VPN to connect to the main office's internal network. Alternatively, a remote worker, who may be working from home, could need to connect to their company's internet or restricted applications.
Which of the following is a type of VPN?
Explanation: There are six types of protocols used in VPN. These are Internet Protocol Security or IPSec, Layer 2 Tunnelling Protocol (L2TP), Point – to – Point Tunnelling Protocol (PPTP), Secure Sockets Layer (SSL), OpenVPN and Secure Shell (SSH).
What is the newest VPN protocol?
WireGuard. WireGuard is the newest VPN protocol on the block. Meant to be a replacement of IPSec, it is allegedly lighter and faster. Furthermore, it is open source, which means a reduced likelihood of security vulnerabilities.
What is site to site VPN?
Site-to-Site VPN. A site-to-site VPN, also referred to as router-to-router VPN, enables offices in multiple locations to safely connect with each other. Remote Access VPN. A remote access VPN allows a user to securely connect to a business or home network and access its resources from a remote location.
What port is OpenVPN on TCP?
SSTP VPN: Open port 1701 for both UDP/TCP. OpenVPN: Open port 53 for UDP and port 80 for TCP. L2TP VPN: Open port 1701 for both UDP/TCP.
What is L2TP protocol?
L2TP – Layer 2 Tunneling Protocol. Since it does not provide strong authentication, L2TP is used with IPSec for security. Though it may conflict with some firewalls, it is a great alternative to the OpenVPN protocol because it supports all modern platforms, and can get around ISP/network limitations.
Why is VPN important?
VPN protocols are important. They provide safety and speed to your online communications. Whether your VPN is optimized for speed or security depends on the VPN protocol that you are currently using. These operate as tunnels through which your online traffic can pass through. Some tunnels are secure.
Which is the most secure VPN?
OpenVPN is the most secure VPN protocol. It offers the highest level of encryption and uses digital certificates for authentication. SSTP also comes with strong security, but it can only be used on Windows operating systems. Winner: OpenVPN.
Which is more secure, PPTP or OpenVPN?
If we talk about security, PPTP is far from secure. It is also the last VPN protocol you would want to use to stay safe online. IKEv2 and L2TP are more secure because they encapsulate your data twice. OpenVPN is the most secure VPN protocol.
What is remote access protocol?
A remote access protocol is responsible for managing the connection between a remote access server and a remote computer. It’s necessary for desktop sharing and remote access for help desk activities. The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), ...
What is PPP protocol?
PPP is a remote access protocol that allows you to implement TCP/IP. It establishes a connection via point-to-point links (i.e., dedicated leased lines and dial-up). PPP is used most often for remote connections to LANs and ISPs. PPP utilizes the Link Control Protocol (LCP), which tests the link between client and PPP host ...
How to use PPTP?
To use PPTP, you’ll have to set up a PPP session between the server and the client, usually over the internet. Once the session is established, you’ll create a second dial-up session. This dial-up session will use PPTP to dial through the existing PPP session.
What is PPTP in a network?
PPTP is a remote access protocol, based on PPP, created by Microsoft. It’s used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network.
What is RDP in Citrix?
Finally, there is the RDP, which is very similar to the Independent Computing Architecture (ICA) protocol used by Citrix products. RDP is utilized to access Windows Terminal Services, which is a close relative of the product line provided by Citrix WinFrame.
What are the disadvantages of PPP?
Unfortunately, one of PPP’s disadvantages is it attracts a high overhead and isn’t compatible with certain older configurations. For technicians, PPP is generally considered easily configurable. Once you connect the router via PPP, it assigns all other TCP/IP parameters for you.
What is managed services provider?
As a managed services provider (MSP), you likely already work with remote access protocols on a daily basis. But learning how to best explain the various types of remote access protocols and their advantages and disadvantages to customers is critical in helping them understand your decisions—and why they should trust you and your services.
What is VPN protocol?
VPN protocols determine exactly how data is routed through a connection. These protocols have different specifications based on the benefits and desired circumstances; for example, some VPN protocols prioritize data throughput speed while others focus on masking or encrypting data packets for privacy and security. 5 Common VPN Protocols.
What are the different protocols used in VPN?
5 Common VPN Protocols. There are two main approaches to VPN functionality: 1) two protocols are used (one protocol to move the data through the tunnel and one protocol to secure that traffic); or 2) one protocol is used for both data transfer and data security. Here are five common VPN protocols and their primary benefits.
What is SSTP encryption?
SSTP utilizes 2048-bit SSL/TLS certificates for authentication and 256-bit SSL keys for encryption. The biggest drawback to SSTP is that is basically a Microsoft-developed proprietary protocol and developers do not have access to the underlying code.
What is VPN in web?
By remaining on this website you indicate your consent. Privacy Notice. Virtual private networks (VPNs) create a tunnel between a private network and a public network, allowing users on the public network to send and receive data as if they were directly connected to the private network. VPNs have long been a popular choice for consumers seeking ...
What is enterprise VPN?
Enterprise VPNs. Virtual private networks (VPNs) create a tunnel between a private network and a public network, allowing users on the public network to send and receive data as if they were directly connected to the private network. VPNs have long been a popular choice for consumers seeking more privacy in their everyday Internet browsing, ...
Is VPN good for business?
VPNs have long been a popular choice for consumers seeking more privacy in their everyday Internet browsing, but the use of VPNs in the business sector has exploded in recent years. This is especially true since March 2020, when VPN usage skyrocketed by 41% in a single month, according to industry research.
Is PPTP still used?
But while PPTP is still used in certain applications, most providers have since upgraded to faster more reliable protocols. Layer 2 Tunnel Protocol is a replacement of the PPTP VPN protocol. This protocol does not provide any encryption or privacy out-of-the-box and is frequently paired with security protocol IPsec.
What is a VPN Protocol?
A VPN protocol is the set of instructions/rules that outline how a connection should be made between your device and the VPN server. The protocol in some way determines the speed and may use encryption algorithms to help keep your data secure.
Commonly Used VPN Protocols
These are protocols most reputable VPN providers & best VPNs prefer to offer. They are very secure with fast speeds, stability, and they are not easily compromised.
Outdated VPN Protocols
These are protocols that most reputable VPN providers stopped offering due to their vulnerabilities. However, you can still get them on a majority of VPN providers.
Proprietary VPN Protocols
These are protocols that are owned and controlled by a given VPN provider. They are solely created and customized to be used within their VPN services.
Wrap Up
VPN protocols provide guidelines and specifications on how a VPN connection should be made. Depending on the protocol in use, a VPN connection can be faster, secure, or stable.
How to install Remote Access Role in VPN?
On the VPN server, in Server Manager, select Manage and select Add Roles and Features. The Add Roles and Features Wizard opens. On the Before you begin page, select Next.
How to start remote access?
Select Start service to start Remote Access. In the Remote Access MMC, right-click the VPN server, then select Properties. In Properties, select the Security tab and do: a. Select Authentication provider and select RADIUS Authentication.
How to select a server from the server pool?
On the Select destination server page, select the Select a server from the server pool option. Under Server Pool, select the local computer and select Next. On the Select server roles page, in Roles, select Remote Access, then Next. On the Select features page, select Next. On the Remote Access page, select Next.
How many switches do you need to install VPN?
If you are installing the VPN server on a VM, you must create two External virtual switches, one for each physical network adapter; and then create two virtual network adapters for the VM, with each network adapter connected to one virtual switch.
What is NAS in a network?
A NAS is a device that provides some level of access to a larger network. A NAS using a RADIUS infrastructure is also a RADIUS client, sending connection requests and accounting messages to a RADIUS server for authentication, authorization, and accounting. Review the setting for Accounting provider: Table 1.
Can you assign a VPN to a pool?
Additionally, configure the server to assign addresses to VPN clients from a static address pool. You can feasibly assign addresses from either a pool or a DHCP server; however, using a DHCP server adds complexity to the design and delivers minimal benefits.
Is RRAS a router or a server?
RRAS is designed to perform well as both a router and a remote access server because it supports a wide array of features. For the purposes of this deployment, you require only a small subset of these features: support for IKEv2 VPN connections and LAN routing.
1. OpenVPN
While scouring the selection of different types of VPN protocols, you’ll stumble upon OpenVPN right away. Touted as the most popular protocol among VPN providers and users, this option is highly secure and works on multiple platforms, including Windows, macOS, Linux, Android, and iOS.
3. SSTP
Owned and controlled by Microsoft, The Secure Socket Tunneling Protocol is fully integrated with all Microsoft operating systems, going back to Windows Vista SP1. On the flip side, that means there is no access to the underlying code, as it’s not an open-source protocol.
4. IKEv2 VPN Protocol
Internet key exchange version 2 or IKEv2 is a tunneling protocol developed by Microsoft and Cisco that uses a secure key exchange. Similar to L2TP, it needs to be paired with IPSec for authentication and encryption.
5. PPTP
Although somewhat obsolete and typically not ranked among the three main VPN tunneling protocols, Point-to-Point Tunneling Protocol is still being used. Developed in 1985 by Microsoft for dial-up connections and integrated into Windows 95, it’s one of the oldest protocols, lacking some of the newer security features.
6. WireGuard
WireGuard is a state-of-the-art VPN protocol that uses a much simpler and smaller codebase and is easier to set up than most of its counterparts. In addition, WireGuard uses one of the newest encryption algorithms, ChaCha20, that offers faster speeds with fewer resources, allowing your battery to last longer.
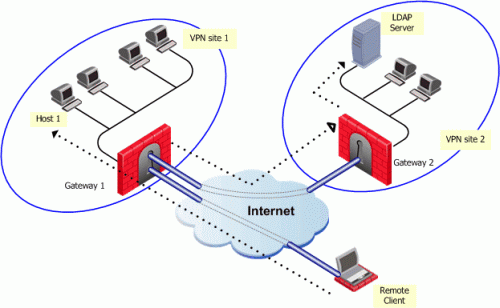
Remote Access VPN
A Remote Access VPN allows people to connect to a private network and remotely access all of its resources and services. The person's connection to the private network is made over the Internet, and the connectivity is safe and confidential. Remote Access VPN is beneficial to both residential and business users.
Site-to-Site VPN
A Site-to-Site VPN, also known as a Router-to-Router VPN, is widely employed in big corporations. Site-to-site VPN is used by businesses and organizations with branches offices in different places to link the network of one office location to the network of another office location.
Protocols of Virtual Private Network (VPN)
IPsec, or Internet Protocol Security, is a protocol used to secure Online communication over an IP network. IPsec protects Internet Protocol communication by validating the session and encrypting each datagram transmitted throughout the connection.

Serial Line Internet Protocol (Slip)`
Point-To-Point Protocol
- PPP is a remote access protocol that allows you to implement TCP/IP. It establishes a connection via point-to-point links (i.e., dedicated leased lines and dial-up). PPP is used most often for remote connections to LANs and ISPs. PPP utilizes the Link Control Protocol (LCP), which tests the link between client and PPP host and specifies PPP client configuration, to communicate between h…
Point-To-Point Tunneling Protocol
- PPTP is a remote access protocol, based on PPP, created by Microsoft. It’s used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network. PPTP is a great option because it’s simple and secure. To use PPTP, you’ll ha...
Windows Remote Access Services
- Windows 2000 and Windows NT let users dial up a server and connect to both the server and the server’s host network. This is referred to as RAS, which is used in smaller networks where a dedicated dial-up router would not be possible or practical. With a RAS setup, you can connect a modem to a Windows 2000 or Windows NT server and configure the modem as dial-out only, di…
Remote Desktop Protocol
- Finally, there is the RDP, which is very similar to the Independent Computing Architecture (ICA) protocol used by Citrix products. RDP is utilized to access Windows Terminal Services, which is a close relative of the product line provided by Citrix WinFrame. RDP offers the same core functions as ICA, although there are some limitations. RDP provides remote access for Windows clients o…