
Remote access VPNs are secure, encrypted connections, or tunnels, between remote users and your company’s private network. The connection consists of a VPN endpoint device, which is a workstation or mobile device with VPN client capabilities, and a VPN headend device, or secure gateway, at the edge of the corporate private network.
Full Answer
Who should use the VPN topology?
The VPN topology determines whether access controls are in use or not. When set to Custom, the configured services and Access Groups become active. Who should use this? The administrator should set the VPN topology based on the need for access controls for the VPN. When should I make use of this?
What topologies can be used with remote access?
Remote Access can be set up with any of the following topologies: With two network adapters: The Remote Access server is installed at the edge with one network adapter connected to the Internet and the other to the internal network.
What is an ravpn topology?
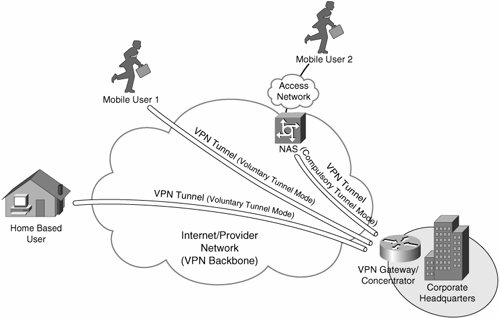
As we discussed in Chapter 1, "Introduction to VPN Technologies," the two core elements that comprise an RAVPN topology are VPN concentrators and VPN clients. These two elements communicate with one another over a predefined media at Layer 3 of the OSI Model.
What is remote access VPN?
Remote Access VPN deployments have become the central focus of secure connectivity in enterprise mobility, allowing secure Layer 3 communications to any VPN endpoint that has an internet connection to the appropriate VPN concentrator.
What topology is a VPN?
The VPN topologies discussed here can be split into three major categories: Topologies influenced by the overlay VPN model, which include hub-and-spoke topology, partial or full-mesh topology, and hybrid topology. Extranet topologies, which include any-to-any Extranet and Central Services Extranet.
How does remote access work with VPN?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What are the main topologies for implementing a VPN?
In general, we group VPN topology in three main categories, remote access VPN, intranet VPN, extranet VPN. A classic concept of a VPN is a remote access VPN, which allows users to have the ability to securely access internal resources.
Is VPN same as remote access?
Flexibility. While having some similarities, VPN and remote desktop are functionally different things. A VPN will give you access to a network while remote desktop (or RDP) will give you control of an entire computer.
What are the two types of VPN connections?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
How does VPN split tunneling work?
Split tunneling is a VPN feature that divides your internet traffic and sends some of it through an encrypted virtual private network (VPN) tunnel, but routes the rest through a separate tunnel on the open network. Typically, split tunneling will let you choose which apps to secure and which can connect normally.
Which topology shows the VPN connections between sites :?
VPN connections can be setup in a Hub and Spoke VPN topology, or also known as Site-to-Multi site VPN topology.
What is star topology?
Star topology is a network topology in which each network component is physically connected to a central node such as a router, hub or switch. In a star topology, the central hub acts like a server and the connecting nodes act like clients.
What difference does Dmvpn make to a hub and spoke VPN topology?
What difference does DMVPN make to a hub and spoke VPN topology? It allows the spokes to establish a direct connection, rather than relaying all communications via the hub, What step can you take to prevent unauthorized use of a remote access server?
Which VPN is best for remote access?
Perimeter 81 – Best all-round business VPN. Jul 2022. ... GoodAccess – Security Strategy Options. Apps Available: ... ExpressVPN – Lightning Fast VPN. ... Windscribe – VPN with Enterprise-Friendly Features. ... VyprVPN – Secure VPN with Business Packages. ... NordVPN – Security-first VPN. ... Surfshark – VPN with Unlimited User Connections.
How do I setup a VPN remote access?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
Which is better VPN or RDP?
Security. Although both VPN and RDP are encrypted through internet connection, a VPN connection is less accessible to threats than a remote desktop connection. For this reason, VPN is often considered more secure than RDP.
Does VPN allow you to access a computer remotely?
Overview VPN is a tool that enables you to access one computer from another. Typical uses for Pop Center members would be 1) access their pop center computer from a home computer or laptop 2) access HSPH Kresge computers from the pop center 3) access the HSPH network drives from a non-HSPH internet connection.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
Can you be tracked if you use VPN?
However, if you use a poor quality VPN, you could still be tracked. A premium quality VPN encrypts data and hides your IP address by routing your activity through a VPN server; even if someone tries to monitor your traffic, all they'll see is the VPN server's IP and complete gibberish.
What are the disadvantages of using a VPN?
The 10 biggest VPN disadvantages are:A VPN won't give you complete anonymity: Read more.Your privacy isn't always guaranteed: Read more.Using a VPN is illegal in some countries: Read more.A safe, top-quality VPN will cost you money: Read more.VPNs almost always slow your connection speed: Read more.More items...•
How does a NAS work?
Users connect to the NAS over the internet in order to use a remote access VPN. In order to sign in to the VPN, the NAS requires that users provide valid credentials. To authenticate these credentials, the NAS uses either its own authentication process or a separate authentication server running on the network .
What is remote access VPN?
What is a remote access VPN? Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What is site to site VPN?
A site-to-site VPN uses a secure gateway to connect a network at one location to one or more networks at another location. This type of VPN doesn’t require each device at the end location to have a VPN client installed because the gateway handles the traffic.
Is remote access VPN secure?
Since remote access VPNs are affordable and secure, organizations can feel more comfortable with letting their employees work from home or while traveling.
Is VPN a security initiative?
Top VPN brands join security initiative. Ethics and VPN: the industry needs to aim higher. While VPNs have grown increasingly popular among users looking to protect their data and privacy online, using the right type of VPN can make all the difference when working remotely.
Where does Anthony live?
After living and working in South Korea for seven years, Anthony now resides in Houston, Texas where he writes about a variety of technology topics for ITProPortal and TechRadar. He has been a tech enthusiast for as long as he can remember and has spent countless hours researching and tinkering with PCs, mobile phones and game consoles.
What is a VPN?
The Virtual Private Dial-up Network (VPDN) service (also described in the section, "Business Problem-based VPN Classification," earlier in this chapter) usually is implemented by tunneling PPP frames exchanged between the dial-up user and his home gateway in IP packets exchanged between the network access server, as shown in Figure 7-22.
How does VPDN work?
Every VPDN solution requires an underlying IP infrastructure to exchange tunneled PPP frames between the NAS and the home gateway. In the simplest possible scenario, the public Internet can be used as the necessary infrastructure. When the security requirements are stricter, a virtual private network could be built to exchange the encapsulated PPP frames. The resulting structure is thought to be complex by some network designers, because they try to understand the whole picture in all details at once. As always, the complexity can be reduced greatly through proper decoupling:
What is a full mesh topology?
Provisioning a full-mesh topology is pretty simple?you just need a traffic matrix indicating the bandwidth required between a pair of sites in the VPN and you can start ordering the VCs from the service provider. Provisioning a partial mesh, on the other hand, can be a real challenge, as you have to do the following:
What is the network model in Figure 7-21?
Logically, the network in Figure 7-21 uses a peer-to-peer VPN model, with distribution routers acting as PE routers of the peer-to-peer model. The actual physical topology differs from the logical view: The distribution routers are linked with the customer sites (CE routers) through the overlay VPN model (for example, Frame Relay network).
Who provides security in the central services extranet?
The security in the central services extranet typically is provided by the central organization sponsoring the extranet. Other participants with mission-critical internal networks (for example, stock brokers or commercial banks) also might want to implement their own security measures (for example, a firewall between their internal network and the extranet).
What is an extranet?
Extranets linking organizations that belong to the same community of interest are often pretty open, allowing any-to-any connectivity between the organizations. Dedicated-purpose extranets (for example, a supply chain management network linking a large organization with all its suppliers) tend to be more centralized and allow communication only between the organization sponsoring the extranet and all other participants, resembling the example shown in Figure 7-19.
What is a second peer VPN gateway?
For Classic VPN, if your on-premises side is hardware based, having a second peer VPN gateway provides redundancy and failover on that side of the connection. A second physical gateway allows you to take one of the gateways offline for software upgrades or other scheduled maintenance.
Can you create two VPN tunnels?
Redundancy and failover options. Note: With Classic VPN, it is not possible to create two VPN tunnels within the same Cloud VPN gateway to the same destination VPN gateway. You can provide redundancy and failover for Classic VPN gateways by either moving to HA VPN or by using a second Classic VPN gateway.
How to use ISATAP?
To use ISATAP do the following: 1. Register the ISATAP name on a DNS server for each domain on which you want to enable ISATAP-based connectivity, so that the ISATAP name is resolvable by the internal DNS server to the internal IPv4 address of the Remote Access server. 2.
What is DNS in DirectAccess?
DNS is used to resolve requests from DirectAccess client computers that are not located on the internal network. DirectAccess clients attempt to connect to the DirectAccess network location server to determine whether they are located on the Internet or on the corporate network.
Why is ISATAP required?
ISATAP is required for remote management of DirectAccessclients, so that DirectAccess management servers can connect to DirectAccess clients located on the Internet . ISATAP is not required to support connections that are initiated by DirectAccess client computers to IPv4 resources on the corporate network.
What should be included in a management server?
The management servers list should include domain controllers from all domains that contain security groups that include DirectAccess client computers. It should contain all domains that contain user accounts that might use computers configured as DirectAccess clients. This ensures that users who are not located in the same domain as the client computer they are using are authenticated with a domain controller in the user domain.
What is a network location server?
The network location server is a website that is used to detect whether DirectAccess clients are located in the corporate network. Clients in the corporate network do not use DirectAccess to reach internal resources; but instead, they connect directly.
What is remote access?
Remote Access creates a default web probe that is used by DirectAccess client computers to verify connectivity to the internal network. To ensure that the probe works as expected, the following names must be registered manually in DNS:
What is a single label name?
Single label names, such as https://paycheck, are sometimes used for intranet servers. If a single label name is requested and a DNS suffix search list is configured, the DNS suffixes in the list will be appended to the single label name. For example, when a user on a computer that is a member of the corp.contoso.com domain types https://paycheck in the web browser, the FQDN that is constructed as the name is paycheck.corp.contoso.com. By default, the appended suffix is based on the primary DNS suffix of the client computer.
What is it?
"Custom" is a configuration option for the VPN Topology configuration item. The VPN topology determines whether access controls are in use or not. When set to Custom, the configured services and Access Groups become active.
Who should use this?
The administrator should set the VPN topology based on the need for access controls for the VPN.
When should I make use of this?
VPN topology is set to ‘Custom,’ when access to configured Services, Networks and Hosts need to be controlled and only specific end-points need to be authorized access to specific Services. Access Groups need to be configured to implement the needed access controls.
