Is remote access WFHC safe to use?
Remoteaccess.wfhc.org most likely does not offer any malicious content. Remoteaccess.wfhc.org provides SSL-encrypted connection. Availability or unavailability of the flaggable/dangerous content on this website has not been fully explored by us, so you should rely on the following indicators with caution.
What is the page load time for remote access WFH?
We analyzed Remoteaccess.wfhc.org page load time and found that the first response time was 115 ms and then it took 1.3 sec to load all DOM resources and completely render a web page. This is quite a good result, as only 20% of websites can load faster. In fact, the total size of Remoteaccess.wfhc.org main page is 131.8 kB.
How do I contact CCF support for remote access?
If you have a general question, you may find your answer under the Help tab on this site, or you may send an email to remoteaccess@ccf.org to receive a response within one business day. Non-CCF managed devices will use Outlook Web Access (OWA) to process email. CCF-managed devices will continue to use Enterprise Outlook.
How do I access mypractice when using remote access?
To access MyPractice from one of the remote access portals, you will need to use the Enterprise Published Application. Going to the Intranet to connect to Epic does not work when using remote access.
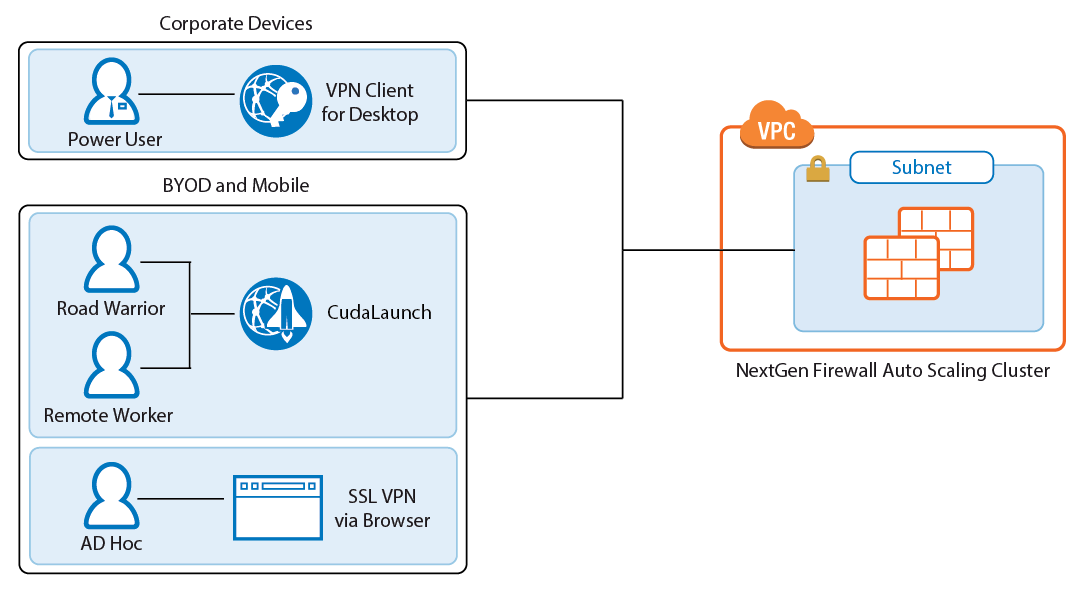
1. Reinforce network security standards
First and foremost, enterprises need to start adding the rigor back into their systems and processes.
2. Bolster home network security
Home network systems use personal equipment or devices provided by a broadband provider. Network security teams must work with remote users to bolster security for home networks by using the following steps:
3. Establish endpoint protection
To manage the network security environments, teams must reestablish endpoint protection, which requires the following steps:
4. Consider new and innovative alternatives
Once upon a time, it was common for employers to provide work-from-home systems with traditional security, but this disappeared with the emergence of BYOD and widespread broadband.