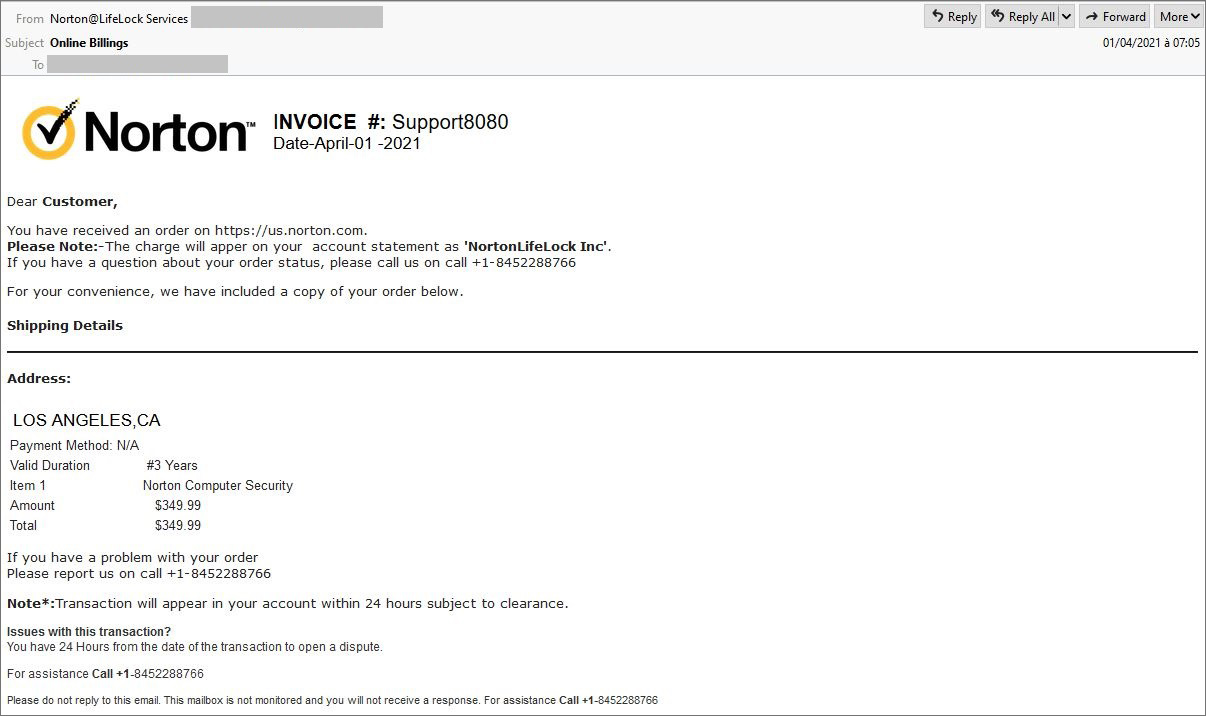
In a remote access scam, a scammer attempts to persuade you into giving them remote control over your personal computer, which allows the scammer to con money out of you and steal your private information. Remote access scams are often related to tech support scams, (example: Dell Computer tech support) and typically starts on the phone with either a cold call from a fake tech support specialist telling you your computer is infected with malware, or a scary-looking pop-up ad that says there’s a problem with your computer and gives you a phone number to call for help. Scammers may also try to convince you to give them remote access by telling you they have money to give you that they can only deliver by connecting to your computer, as seen in the recent FTC refund scam that’s been making the rounds. Another very recent refund scam includes asking you to display your online bank account, and putting a fake deposit on your account statement. The scammers then lead you to believe that they made a typo on the fake refund issued and ask for a gift card as a refund to them.
How do remote access scams work?
Remote access scams. Remote access scams try to convince you that you have a computer or internet problem and that you need to buy new software to fix the problem. The scammer will phone you and pretend to be a staff member from a large telecommunications or computer company, such as Telstra, the NBN or Microsoft.
What happens when you get a call from a computer scammer?
The caller will request remote access to your computer to ‘find out what the problem is’. The scammer may try to talk you into buying unnecessary software or a service to ‘fix’ the computer, or they may ask you for your personal details and your bank or credit card details.
How do computer scams affect the elderly?
Once given permission to take over the computer, the scammer is able to steal personal and financial information which can later be used to defraud the victim. Over 70% of these computer scams originate via a phone call, and 82% of losses are against victims aged 65 and over.
How big is the problem with computer scams?
Over 70% of these computer scams originate via a phone call, and 82% of losses are against victims aged 65 and over. How big is the problem? In Australia, remote access scams are now the sixth largest scam type.
What happens when a hacker gets remote access to my computer?
Hackers use RDP to gain access to the host computer or network and then install ransomware on the system. Once installed, regular users lose access to their devices, data, and the larger network until payment is made.
How do scammers control your computer?
The caller will request remote access to your computer to 'find out what the problem is'. The scammer may try to talk you into buying unnecessary software or a service to 'fix' the computer, or they may ask you for your personal details and your bank or credit card details.
How do I stop someone from accessing my computer remotely?
Windows 10 InstructionsClick the Windows Start button and type "Allow Remote Access to your computer". ... Make sure "Allow Remote Assistance connections to this computer" is unchecked.Select "Don't allow remove connections to this computer" under the Remote Desktop section and then click OK.
Can scammers access my phone remotely?
Yes. Unfortunately, they can even hack a phone's camera. But you can also learn how to block hackers from your Android or iOS phone. The first step is understanding how cybercriminals think and work.
Can someone remotely access my computer without my knowledge?
"Can someone access my computer remotely without me knowing?" The answer is "Yes!". This could happen when you are connected to the internet on your device.
What remote access software do scammers use?
Remote access scams are a unique scenario where victims are socially engineered to provide remote access to their computer via a legitimate remote access tool such as TeamViewer, LogMeIn, Go-To-Meeting, or a similar remote desktop software.
How do I see who is connected to my computer?
right click on my computer -> manage ->shared folders -> sessions/open files. that will tell you what windows shares they are looking at.
What would best prevent an unauthorized person from remotely accessing your computer?
It is essential to use a personal password for all your accounts to prevent unauthorized access. A user has to be more careful about this if they use a shared system. Apart from this, make sure to change passwords often. Use antivirus software.
How can I tell if remote access is enabled?
Allow Access to Use Remote Desktop ConnectionClick the Start menu from your desktop, and then click Control Panel.Click System and Security once the Control Panel opens.Click Allow remote access, located under the System tab.Click Select Users, located in the Remote Desktop section of the Remote tab.More items...•
Can hackers see you through your phone camera?
Are hackers really spying on people through their phone cameras and webcams? The short answer: Yes. Webcams and phone cameras can be hacked, giving bad actors complete control over how they function. As a result, hackers can use a device's camera to both spy on individuals and search for personal information.
What are the signs your phone has been hacked?
One or more of these could be a red flag that some has breached your phone:Your phone loses charge quickly. ... Your phone runs abnormally slowly. ... You notice strange activity on your other online accounts. ... You notice unfamiliar calls or texts in your logs. Hackers may be tapping your phone with an SMS trojan.
Can a scammer get your info if you call back?
“It's the concept that people think may have missed an important call.” At the very least, answering the phone or calling back makes you vulnerable to future scams, says Eva Velasquez, CEO and president of Identity Theft Resource Center.
How does a remote access work?
Remote access simply works by linking the remote user to the host computer over the internet. It does not require any additional hardware to do so. Instead, it requires remote access software to be downloaded and installed on both the local and remote computers.
Can a scammer access my bank account?
Yes, this is possible. Identity theft was the number one reported type of fraud in 2020 [*], according to the FTC. When scammers gain access to your personal information by phishing, for example, they can do one or more of the following: Gain access to your bank account and spend or transfer all your money.
What is remote access scam?
Remote access scams try to convince you that you have a computer or internet problem and that you need to buy new software to fix the problem.
What to do if you think you have provided your account details to a scammer?
If you think you have provided your account details to a scammer, contact your bank or financial institution immediately.
What is malware scam?
Malware tricks you into installing software that allows scammers to access your files and track what you are doing, while ransomware demands payment to ‘unlock’ your computer or files.
How to protect your computer from spyware?
Make sure your computer is protected with regularly updated anti-virus and anti-spyware software, and a good firewall. Research first and only purchase software from a source that you know and trust.
Can a scammer be abusive?
The scammer may initially sound professional and knowledgeable—however they will be very persistent and may become abusive if you don't do what they ask.
What is a remote access scam?
Remote access scams are a unique scenario where victims are socially engineered to provide remote access to their computer via a legitimate remote access tool such as TeamViewer , LogMeIn, Go-To-Meeting, or a similar remote desktop software . Once given permission to take over the computer, the scammer is able to steal personal and financial information which can later be used to defraud the victim.
What can banks do to detect remote access scams?
Most authentication and fraud prevention solutions rely on known device and IP location parameters to measure fraud risk. While these controls can be effective, RATs, by design, circumvent traditional fraud detection tools that look for the presence of malware, bots, and blacklisted devices, or IP addresses.
How does biocatch work?
Instead of relying on static controls, BioCatch uses machine learning to model behaviors and can differentiate a genuine user from a cybercriminal in real-time. Using behavioral biometrics, banks are able to protect customers after login and by detecting unusual behaviors that are indicative of RAT activity or social engineering. When a user accesses their online banking site, BioCatch monitors a user’s actual behavior and compares it to their historical profile. This detects anomalies and characteristics that are indicative of fraud as they occur. For example, hesitation on the part of the user may be observed through intuitive actions such as clicking on the Submit button. In a remote access scam and other social engineering attacks, it has been shown that there is a statistically significant increase on average in the time it takes users to perform simple actions.
Is cybercrime opportunistic?
Cybercrime is opportunistic, and there is no time like the present for criminals to adapt their tactics, old and new, to defraud online customers. Remote access scams are one of those tactics, and the number of attacks has grown during the COVID-19 pandemic. Cybercriminals are using the unstable environment to their advantage to take ...

What Is A Remote Access Scam?
How Big Is The Problem?
- In Australia, remote access scams are now the sixth largest scam type. As of September, the total reported losses via the ACCC are $4.7 million, yet this only represents reported losses. We can safely assume that total losses run well into the tens of millions per annum. The losses are on the rise as well, with September 2020 representing a new record, with over $1.1 million lost and in e…
What Is The Impact on Victims?
- From a trust and emotional perspective, all victims are materially impacted by scams. From a loss perspective, the amounts can vary from a few thousand dollars to someone's entire life savings. Different banks have different approaches in terms of reimbursing customers — that is, at what stage is the bank liable for protecting the customer vs. the victim being responsible. However, th…
How Can We Protect Victims?
- Dubbed the “call that could wipe out your life savings,” four in ten consumers have not heard of remote access scams. Protection begins on the front lines, and raising awareness about these scams with consumers and businesses is a starting point. There is a lot of great work being done in this space by entities such as Scamwatch and UK Financeas well as by the banking industry it…
What Can Banks Do to Detect Remote Access Scams?
- Most authentication and fraud prevention solutions rely on known device and IP location parameters to measure fraud risk. While these controls can be effective, RATs, by design, circumvent traditional fraud detection tools that look for the presence of malware, bots, and blacklisted devices, or IP addresses. Instead of relying on static controls, BioCatchuses machin…