
Why secure remote access is important?
Your organization's policy should be sure to address several issues, including:
- How decisions are made as to which employees are eligible for telecommuting assignments and remote access privileges
- What behavior constitutes acceptable use of remote access connections
- Acknowledgement that any organization equipment provided to employees remains the organization's property
What is the most secure remote access protocol?
Extensible Authentication Protocol (EAP) EAP allows for authentication of a remote access connection through the use of authentication schemes, known as EAP types. EAP offers the strongest security by providing the most flexibility in authentication variations.
What creates a secure connection to a remote server?
- The remote computer must be turned on at all times and have a network connection.
- The client and server applications need to be installed and enabled.
- You need the IP address or the name of the remote machine you want to connect to.
- You need to have the necessary permissions to access the remote computer.
How to protect remote access?
UniFi Protect - Getting started
- UniFi Protect overview. UniFi Protect is Ubiquiti's surveillance camera and video management system for UniFi cameras and security products.
- Set up UniFi Protect. Launch the UniFi Portal mobile app and t urn on the console. ...
- Use Protect in a web browser. ...
- Adopt devices with UniFi Protect. ...
- Add other users. ...
- Frequently asked questions. ...
- Related articles. ...
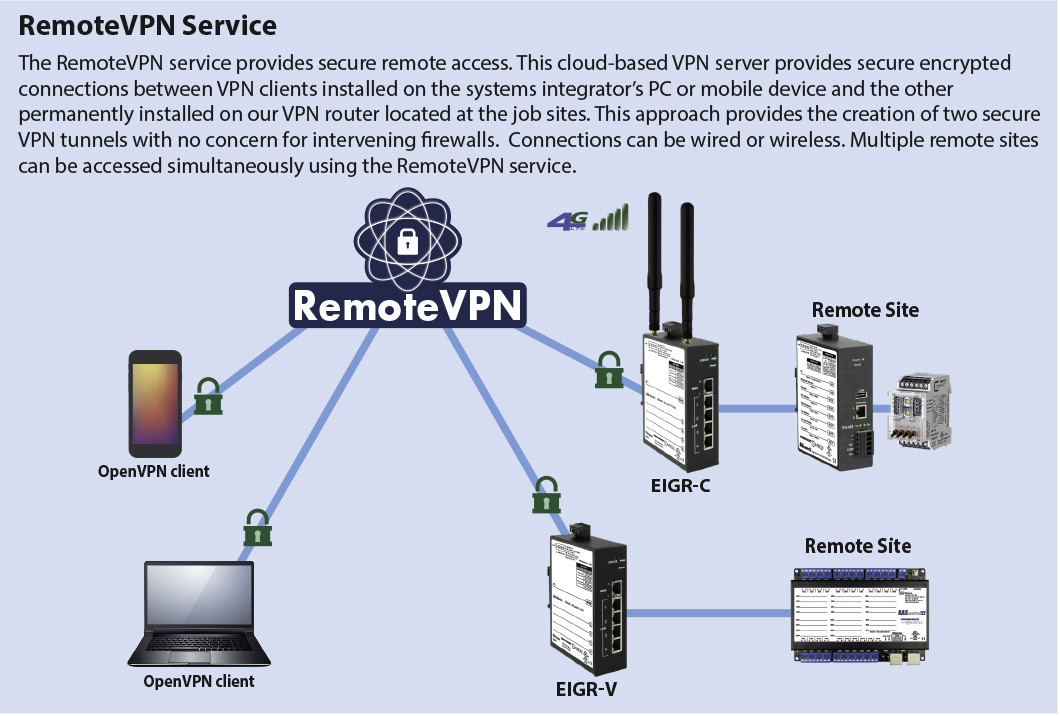
Which method of remote access is the most secure?
Implement a Secure Connection for Remote Network AccessWired Connection: A wired connection is the most secure method for remote network access.Home Wi-Fi: The second most secure network connection is using a secured home Wi-Fi connection.More items...•
Can remote access be more secure?
While Remote Desktop is more secure than remote administration tools such as VNC that do not encrypt the entire session, any time Administrator access to a system is granted remotely there are risks. The following tips will help to secure Remote Desktop access to both desktops and servers that you support.
How do I create a secure remote access?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
What allows for secure remote console access?
You can enable remote access (dial-up or VPN), Network Address Translation (NAT), both VPN and NAT, a secure connection between two private networks (site-to-site VPN), or you can do a custom configuration to select any combination of these, as shown in Figure 14.25.
Can someone remotely access my computer when it's off?
Without appropriate security software installed, such as anti-malware tools like Auslogics Anti-Malware, it is possible for hackers to access the computer remotely even if it is turned off.
Can someone remotely access my computer without my knowledge?
"Can someone access my computer remotely without me knowing?" The answer is "Yes!". This could happen when you are connected to the internet on your device.
What is secure remote access VPN?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
Why is RDP a security risk?
While this prevents access by a standard user, it represents an unacceptable risk, since only administrators can authenticate via RDP into the asset. This does not follow the security best practice of least privilege. Therefore, access for administrators should be eliminated.
What are potential risks associated with remote access?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
What is remote access examples?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
How does a remote access work?
Remote access simply works by linking the remote user to the host computer over the internet. It does not require any additional hardware to do so. Instead, it requires remote access software to be downloaded and installed on both the local and remote computers.
How do you remotely access another computer?
Use Remote Desktop to connect to the PC you set up: On your local Windows PC: In the search box on the taskbar, type Remote Desktop Connection, and then select Remote Desktop Connection. In Remote Desktop Connection, type the name of the PC you want to connect to (from Step 1), and then select Connect.
What are potential risks associated with remote access?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
Is RDP more secure than teamviewer?
Is Teamviewer safer than RDP? When it comes to safety, RDP is more secure against hackers' attacks. This is because of the powerful encryption method RDP is featured with.
What is ZTNA security?
ZTNA takes a user-to-application approach rather than a network-centric approach to security . The network becomes deemphasized, and the internet becomes the new corporate network, leveraging end-to-end encrypted TLS micro-tunnels instead of MPLS.
How does ZTNA improve security?
ZTNA improves your security posture by drastically reducing your attack surface. Application access is decoupled from network access. ZTNA moves away from network-centric security and instead focuses on securing the connection between user and application.
Why are IPs never exposed to the internet?
IPs are never exposed to the internet, creating a “darknet” and making the network impossible to find. Apps segmentation ensures that once users are authorized, application access is granted on a one-to-one basis so that authorized users have access only to specific applications rather than full access to the network.
Can IoT services be hosted on premises?
IoT services that are hosted on-premises can benefit from optimized speeds. Performance speeds can increase if local users do not have to connect out to the internet to access apps that are hosted on-premises. The other option is ZTNA as a service, such as Zscaler Private Access.
Can a VPN be found by adversaries?
Opening the network in this way enables it to be “found” by your remote users, but it also means it can be found by adversaries. They can (and do) exploit the VPN attack surface to infiltrate the network, deliver malware such as ransomware, launch denial-of-service attacks, and exfiltrate critical business data.
Secure Remote Access for Employees and Vendors
Traditional remote access methods, such as RDP, Virtual Private Networks, and legacy remote desktop tools lack granular access management controls. These processes enable easy exploits via stolen credentials and session hijacking. Extending remote access to your vendors makes matters even worse.
Privileged Remote Access: Use Cases
BeyondTrust Privileged Remote Access controls, manages, and audits remote privileged access to critical IT systems by authorized employees and third-party vendors. No VPN required.
Remote Support: Use Cases
BeyondTrust Remote Support allows help desk teams to securely access and fix any remote device on any platform, located anywhere in the world. All with the same solution.
Secure Remote Access and Remote Support Features
BeyondTrust Remote Support and Privileged Remote Access solutions work hand-in-hand to secure remote access points within the enterprise, including employees, vendors, third-parties, and more.
What is secure remote access?
Secure remote access refers to any security policy, solution, strategy or process that exists to prevent unauthorized access to your network, its resources, or any confidential or sensitive data. Essentially, secure remote access is a mix of security strategies and not necessarily one specific technology like a VPN.
What technologies are used for secure remote access?
Secure remote access is comprised of a multitude of security solutions and technologies. Some of the most prominent include the following:
Secure remote access solution
Enables employees with precise access to the applications and data required to do their job from anywhere.
Why is secure remote access important?
With the work from home shift in the workforce, endpoints are accessing corporate networks from multiple locations. Today, employees’ home networks are often the originating point for network connections, multiplying the risk on both home and corporate networks.
What are the benefits of secure remote access?
While the benefits of secure remote access are numerous, there are four key advantages in which to focus on:
Can secure remote access be achieved without VPN?
Yes. A robust cloud-based, highly secure remote access solution can provide unified protection for virtually all users against web-based threats — independent of a VPN connection.
How can AT&T help organizations with secure remote access?
AT&T Cybersecurity is uniquely positioned to help organizations address these immediate challenges with an eye toward the future by helping them balance connectivity, collaboration, and cybersecurity affordably.
How does secure remote access work?
Enabling remote access means walking a tightrope between usability and cybersecurity. Every remote worker needs a way to connect with remote desktop services and applications that won't slow down their workflows. At the same time, IT administrators must manage those connections to ensure they don't leave the network open to threats.
Why is secure remote access important to remote work security?
Secure remote access approaches are so vital because it’s now impossible to control security at the endpoint. Each user in a remote or hybrid workforce is connecting to the network from a different type of computer or smartphone, and they’re using a variety of internet connections to log in.
What are the options for secure remote access?
Multiple solutions go into a comprehensive secure remote access package—and each one delivers vital functionality that reflects the way companies use their networks today. These features work together to protect users, data, and network assets in a distinct way.
Next-gen remote access solutions for a secure digital workspace
Learn how remote access solutions can secure digital workspaces and enhance the user experience.
Citrix solutions for secure remote access
Citrix secure access solutions take several forms to give companies a balanced selection of options based on their specific requirements. Whatever level of engagement with remote work these businesses have, there is a secure remote access solution for the situation.
Why is remote access important?
Remotely accessing a desktop from a different location allows an authorized organizational user to take control of a computer to view or change files, fix technical issues, or configure settings. However, the method of access must be completely secure to protect your business data.
What are the advantages of remote access?
Secure remote access systems have four important advantages for users and their networks. 1. Secure access from any device. When you have a secure remote access solution in place, it grants authorized users access to your company network on any compatible device. Employees have seamless access to all of their data and files, ...
What is endpoint security?
Endpoint security: An endpoint security system secures a company's various devices on a network. These devices can include mobile devices, laptops, desktops and servers.
What is ZTNA VPN?
A ZTNA system often defaults to access denial, unlike a VPN, which generally grants users open access with the right credentials. The type of data, systems and amount of access a user has is determined by the system their company has set up.
Is Connectwise a good app?
If your business is looking for a little more customization, ConnectWise is a good choice. It allows you to create your security settings and personalize the software with your company's brand. These features are available across multiple operating systems and devices.
Is RemotePC safe for small businesses?
Perfect for small businesses, RemotePC is easy to implement and offers several plans to fit the size of your company and number of devices. One of its biggest advantages is that you don't need to configure firewalls or proxy servers; once you're connected, you are already secure and can get to work.
Do you need to install software before you can remotely log on to a device?
Before you can remotely log on to a device or program, you'll need to install software on both the device you're using and the device you want to access. Once the application is installed, both devices need to be turned on.
What are the benefits of secure remote access?
Secure remote access benefits are numerous, but the following four are particularly valuable:
Pros and Cons of Secure Remote Access Technologies
VPNs enable secure remote access between distant network nodes. A process known as "tunneling" is used to provide secure data transmission between the endpoints of a VPN connection. VPN connections can be classified as Site-to-Site or Client-to-Site connections. Site-to-Site VPNs connect numerous Wide Area Network (WAN) sites.
Best Practices for Secure Remote Access
Passwordless authentication refers to an authentication method that does not require a password at all. Passwords aren't used as a backup or as an alternative authentication method. In addition, passwords are never stored in a password vault or manager.
Ensure remote access to your data is secure
It is essential to ensure your security systems keep pace with the ever-changing threat landscape and your internal processes adapt as organizations continue to work remotely or in hybrid environments.
What is remote access app?
Remote access apps let you either access your home or office computer from another location, or allow others to have access to some or all of your files, as if they were actually sitting in front of your PC instead of somewhere else entirely.
What is GoToMyPC?
GoToMyPC is a mature, easy-to-use remote access software with the best available balance between features and ease of use. Unless you need support for Linux or enterprise-level operating systems, this is the app you want.
Is VNC Connect secure?
VNC Connect is solid, secure, and simple to use, once you get the hang of it. It has fewer features than other corporate-level remote access software, but it's also a lot less expensive.
A single, easy-to-use platform that provides secure remote access to vendors
Current methods fail to properly secure third party remote access by identifying each individual, controlling their access, and auditing their activity.
What Is Secure Remote Access?
In today’s business environment, remote access to systems, data, and servers is a common and necessary occurrence. This remote access can be for employees, who are working from home or distributed remotely, and it can also be for third parties, such as contractors, technology vendors, business partners, and consultants.
Is Your Remote Access Secure?
Evaluate your current vendor security practices and learn the industry standards for data protection.
Why Does Secure Remote Access Matter?
If you’re realizing you don’t have all of those 4 key elements in place, but are wondering if it’s worth the effort and investment to make those changes, consider the potential costs of failing to do so.
What To Look For In A Secure Remote Access Method
Often individual identification is a key element to meet regulatory requirements and general security best practices. You need to know who is in your network, and ensure that the person with access is who they say they are, and that they should even have access (unlike, a bad actor or external hacker). At minimum, this should include:
Empower your team to work from anywhere
From connecting your colleagues and customers with GoToMeeting to securing your business with LastPass, we have the solutions to make anywhere work for you.
Cyber Week Savings!
Work wherever the season takes you with discounts on GoToConnect and GoToMeeting.
