
5 Key Considerations When Setting Up Secure Remote Access for Employees
- Off-site data security. Decide which employees are eligible to work from home, and what software and systems you’ll...
- Devices used for remote work. Decide who will provide the computers and laptops employees use for remote work. If...
- Enabling secure off-site file access. What about file...
- Develop a Cybersecurity Policy For Remote Workers. ...
- Choose a Remote Access Software. ...
- Use Encryption. ...
- Implement a Password Management Software. ...
- Apply Two-factor Authentication. ...
- Employ the Principle of Least Privilege. ...
- Create Employee Cybersecurity Training.
How to successfully onboard a remote employee?
- Cover the right information. ...
- Tailor digital onboarding material for the most impact. ...
- Be as flexible as possible. ...
- Train new hires at a slower-than-usual pace. ...
What programs allow remote access?
The best remote desktop software right now
- RemotePC. RemotePC is a hugely-popular remote computer access application that’s suitable for both home and—in particular—for business users.
- Zoho Assist. Cloud-based Zoho Assist is one of our favorite remote access tools because it enables you to access almost any device.
- Splashtop. ...
- Parallels Access. ...
- LogMeIn Pro. ...
- Connectwise Control. ...
- TeamViewer. ...
How to setup employee access?
- Enter employee Email in contact information
- Check Give Access Checkbox
- Enter password and Confirm Password
- Define Roles under roles tab for which you want to give access.
How to successfully manage remote employees?
Managing teams working remotely is not new ... Build Trust There is general consensus that a successful remote work environment requires high levels of trust i.e. managers have to trust workers to handle their responsibilities on their own, without ...
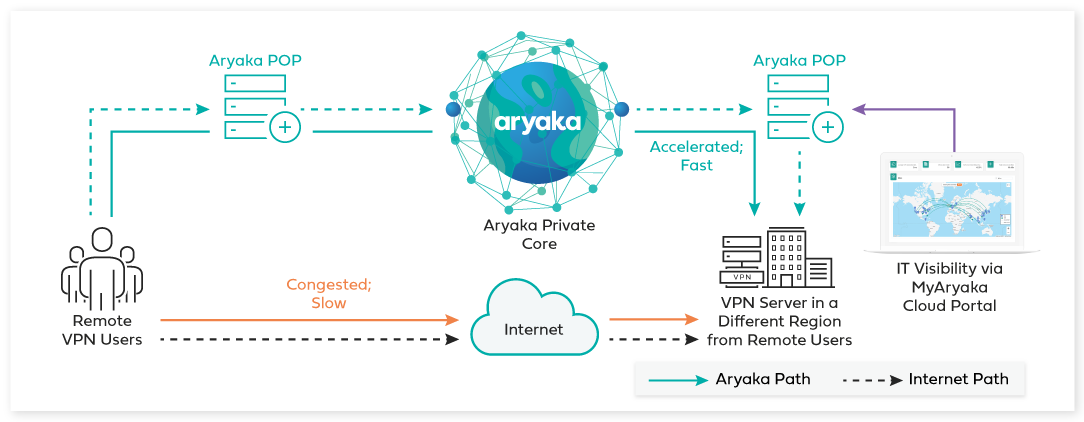
How do you secure remote access to employees?
Require employees and vendors to use secure connections when connecting remotely to your network. They should: Use a router with WPA2 or WPA3 encryption when connecting from their homes. Encryption protects information sent over a network so that outsiders can't read it.
Which method of remote access is the most secure?
Remote Access Solutions: Which is the Most Secure?VPNs. ... Desktop Sharing. ... The Verdict: VPNs and Desktop Sharing Are Not Secure Enough for Remote Vendor Access. ... The Best Alternative: Vendor Privileged Access Management. ... The Bottom Line.
Who is more secure protocol for remote login?
Virtual private networks (VPNs) are a commonly used remote-access solution. They are designed to provide an encrypted tunnel for network traffic between a remote user and the enterprise network. VPNs also support security solutions like MFA that help to mitigate the threat of compromised accounts.
Which is a more secure form of remote access over a network?
Virtual private network (VPN) – The most common and well-known form of secure remote access, VPNs typically use the public Internet to connect to a private network resource through an encrypted tunnel.
What is secure remote access?
Secure Remote Access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization's digital assets and prevent the loss of sensitive data.
What are the three types of remote connections?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
What is secure remote communications?
Secure Remote Working is a combination of multiple technologies and procedures comprising: Virtual Private Network (VPN) – Facilitates secure access to on-premises applications and services. VPNs also provide secure internet access for employees on public wireless or third-party corporate networks.
What is the remote access method that uses encryption?
A VPN provides a mechanism to access corporate networks safely using Internet. VPN uses encryption to ensure only authorized user can access the corporate resources. A secure tunnel is created through the public network through which the packets are transported between the remote computer and the corporate network.
What is VPN in remote office?
VPN – Virtual Private Network – You can restrict access so that employees must exclusively connect through a VPN, providing a direct, encrypted connection between their remote device and the main office server. This is a way to offer full, but secure access to remote employees. Be prescriptive about which VPN tools employees use.
Why don't companies allow remote work?
For various reasons, some employers discourage or don’t allow remote work. Manufacturers may feel it’s unfair to let operational staff work remotely when plant and warehouse workers have to come in. The office environment is naturally conducive to building friendships, fostering teamwork and encouraging collaboration.
Can employees work from home?
Keep in mind that some employees will have difficulty working from home. They may have children or other family members clamoring for their attention. They may not be comfortable with video chat and need extra time to learn technology and change their processes to find new ways to collaborate.
Can you work remotely and in office?
One of the easiest ways is to allow employees to work from home. Obviously, working remotely and in-office are not the same. You don’t have the same fluid interactions between employees as when they’re within walking distance from each other. Paperwork and contracts can’t be passed around.
Is it good to migrate to the cloud?
If you already have a cloud software set up, you’re good to go! If not, migrating to the cloud is a great way to keep files secure while giving employees access to their work anywhere. Both G-Suite and Microsoft Office 365 can be set up relatively quickly.
Do employees cause data breaches?
Most employees are loyal to your business, strive to act in a professional manner, and would never intentionally cause a data breach. Despite good intentions, studies show that employees are consistently the top source of data security breaches.
1. Multi-Factor Authentication (MFA) for employee access
Option 1) Leverage your existing LDAP user directory, for example an on-premise Active Directory together with a Time-based One-time Password (TOTP) to enforce Multi-Factor Authentication (MFA) for your employees.
2. Temporary access to authorized targets - without passwords
PrivX provides role-based access controls (RBAC) to authorized targets that consist of both the target host and target account.
3. Restricted Windows RDP access to targets or applications
You can also grant limited RDP access to specific targets, for example RDP without file transfer or clipboard could be allowed for some PrivX users to login as self to access their Windows workstations. You can restrict access even further.
4. Restricted SSH access
Any target host running a secure shell server can be configured with PrivX Roles to allow restricted access. Secure Shell access via the PrivX GUI is restricted by design to Shell (terminal) and File Transfers only.
Remote access management made easy
Our solution, PrivX, is a quick-to-implement and scalable privileged access management (PAM) solution that extends to all employees working from home for establishing secure remote access to web applications. It’s a viable alternative for VPNs and other traditional remote secure access tools.
Suvi Lampila
Suvi Lampila is a Senior Technical Services Engineer at SSH.COM. Suvi has been with SSH since 2001 and she has held various positions in technical support, quality assurance and professional services both in Finland and Hong Kong.
What percentage of Verizon network intrusions exploited weak or stolen credentials?
According to Verizon’s Data Breach Investigation Report, “76 percent of network intrusions exploited weak or stolen credentials.” Since vendors don’t need constant access to your network, they often use one remote access tool license and share generic logins and passwords across technicians. This makes the credentials easy for hackers to guess. What’s more, the vendor’s ex-employees often retain remote access to your systems.
What is the Telework Enhancement Act?
The Telework Enhancement Act requires federal agencies to have policies to govern and promote teleworking. Between teleworkers and vendors, we are challenged to enable secure access for increasingly large and diverse workforces, while simultaneously dealing with smaller budgets and tightening compliance mandates.
Why is remote access important?
It is essential for these individuals to have safe, anytime, anywhere access to corporate networks and services.
What is PAM in security?
To ensure continued security and compliance, you should use a modern privileged access management (PAM) solution with strong privileged access management capabilities to track, audit, record, and centrally monitor all access requests, approvals, revocations, and certifications—for both internal and external privileged users.
What is the first step in security journey?
The first step in any security journey is discovering your weaknesses and vulnerabilities, in other words, your cyber threat exposure. You should have the mindset that your organization is a target that malicious actors are already attempting to attack through your third-party vendors. So, assume hostile threats will occur!
What happens if you give access to an outsider?
Recognize that granting system access to an outsider lowers your security level to that of the external provider. If they lack strong security controls, they become your weakest link. If a hacker compromises their system, that partner can become a backdoor into your environment .
Why is reducing network entry points important?
By reducing network entry points to the least amount that are necessary, you increase your ability to monitor and block unwanted activity on your network.
Issue Secure Equipment to Remote Employees
Small businesses and managers need to remember that their employees are not IT professionals. The prospect of trusting employees to ensure security protocols on personal devices is like climbing Mount Everest without crampons; the intentions are sound but you will inevitably fail due to lack of foresight and proper equipment.
Implement a Secure Connection for Remote Network Access
When gauging the efficacy of a secure access strategy for remote employees, an organization needs to consider the path in which remote employees access and connect to the internet. Organizations can ensure a secure remote work environment by requiring employees to only access the corporate network through a secure connection.
Supply a VPN for Secure Remote Access
Organizations that utilize a Virtual Private Network (VPN) provide their remote employees a very similar experience to working in brick and mortar locations. A VPN allows an end-user to establish a direct connection between their PC and the corporate network through a firewall.
Empower Remote Employees through Education and Technology
Businesses need to recognize that their employees are usually the last line of defense when security breaches arise. While underprepared and uneducated employees can be a great security detriment, knowledgeable employees can be one of their greatest tools for combating remote security vulnerabilities.
Secure Remote Access for Employees and Vendors
Traditional remote access methods, such as RDP, Virtual Private Networks, and legacy remote desktop tools lack granular access management controls. These processes enable easy exploits via stolen credentials and session hijacking. Extending remote access to your vendors makes matters even worse.
Privileged Remote Access: Use Cases
BeyondTrust Privileged Remote Access controls, manages, and audits remote privileged access to critical IT systems by authorized employees and third-party vendors. No VPN required.
Remote Support: Use Cases
BeyondTrust Remote Support allows help desk teams to securely access and fix any remote device on any platform, located anywhere in the world. All with the same solution.
Secure Remote Access and Remote Support Features
BeyondTrust Remote Support and Privileged Remote Access solutions work hand-in-hand to secure remote access points within the enterprise, including employees, vendors, third-parties, and more.
How does ZTNA work?
If a user is looking to access another private application simultaneously or even from another device, ZTNA spins up different microtunnels. VPNs use a single tunnel per user through which all apps run. ZTNA improves your security posture by drastically reducing your attack surface.
Why are IPs never exposed to the internet?
IPs are never exposed to the internet, creating a “darknet” and making the network impossible to find. Apps segmentation ensures that once users are authorized, application access is granted on a one-to-one basis so that authorized users have access only to specific applications rather than full access to the network.
Why is VPN so bad?
Trust is inherent and often excessive for those inside the network. 2. There is a increased risk of external access to the network.
How does ZTNA improve security?
ZTNA improves your security posture by drastically reducing your attack surface. Application access is decoupled from network access. ZTNA moves away from network-centric security and instead focuses on securing the connection between user and application.
What is ZTNA security?
ZTNA takes a user-to-application approach rather than a network-centric approach to security . The network becomes deemphasized, and the internet becomes the new corporate network, leveraging end-to-end encrypted TLS micro-tunnels instead of MPLS.
What is ZTNA in IT?
In response to today’s needs, IT teams leverage zero trust network access (ZTNA) as a new framework for enabling secure remote access to off-network users. ZTNA is a term defined by Gartner, and the technology is also known as a software-defined perimeter (SDP). ZTNA provides secure access to your private enterprise applications, whether they’re hosted in public clouds, private clouds, or the data center, without the need for a VPN. ZTNA is based on an adaptive trust model, where trust is never implicit, and access is granted on a “need-to-know,” least-privileged basis defined by granular policies. Because it’s 100 percent software-defined, ZTNA solutions require no physical appliances but can be deployed in any environment to support all REST-API applications.
Can a VPN be found by adversaries?
Opening the network in this way enables it to be “found” by your remote users, but it also means it can be found by adversaries. They can (and do) exploit the VPN attack surface to infiltrate the network, deliver malware such as ransomware, launch denial-of-service attacks, and exfiltrate critical business data.
What is secure remote access?
What it means to provide secure remote access has changed considerably in the past few years as a result of new technologies and the pandemic. At its most basic, secure remote access is having location-agnostic connectivity among enterprise users and centralized applications, resources and systems, whether cloud-based or on premises.
Who is responsible for secure remote access?
Although remote access tools, such as VPNs and firewalls, are typically under the purview of network teams, in this new era, cybersecurity teams tend to lead and manage the policies, processes and technologies associated with ensuring secure remote access.
The diminishing power of VPNs
One tactic organizations use to combat the vulnerabilities associated with working remotely -- especially if employees are using consumer-grade systems -- is to reestablish VPN standards. This entails enforcing basic protections, such as strong passwords, multifactor authentication, role-based access and encryption.
Setting secure remote access policies
A hallmark of secure remote access is the underlying policy that safeguards access to and the use of enterprise resources, such as data, databases, systems and networks.
Components of the secure remote access ecosystem
Secure remote access touches just about every aspect of enterprise security. TechTarget has curated a series of guides to help IT and security professionals get up to speed on important technologies and concepts.
Zero trust and secure remote access
Cybersecurity and IT teams realize words like perimeter and trust are quickly becoming outdated as borders dissolve and the base of users that need access to resources expands. No longer are organizations protected by four castle walls, with a firewall moat keeping miscreants out.
SASE and secure remote access
Secure Access Service Edge is an emerging concept that combines network and security functions into a single cloud service, not only to alleviate traffic from being routed through the data center, but also to embrace a remote workforce, IoT adoption and cloud-based application use.
