
What is industrial remote access?
What is industrial remote access? With remote access to connected industrial machines you can remotely troubleshoot and program programmable logic controllers (PLCs), view and control Human Machine Interfaces (HMIs), connect to an IP camera for assistance or support field technicians with specific problems.
Why secomea for industrial remote access?
With Secomea’s Industrial Remote Access to connected machines, you can provide fast and effective support and maintenance on equipment without compromising the high security demands that are expected from your customers.
What is an industrial remote access router (ixrouter)?
Different models of the industrial remote access router (IXrouter) allow you to choose the most appropriate connection type, ethernet, wifi and/or cellular. This way customers have great flexibility to pick the most appropriate technology to allow secure remote connection within their operation.
How does a remote access structure work?
The structure works online and can provide remote supervision of the machine to the operator through a secure VPN connection. CHAPTER 5Exploring Remote Access Success Stories 41 These materials are © 2017 John Wiley & Sons, Ltd.
Which method of remote access is the most secure?
Implement a Secure Connection for Remote Network AccessWired Connection: A wired connection is the most secure method for remote network access.Home Wi-Fi: The second most secure network connection is using a secured home Wi-Fi connection.More items...•
How can you secure the remote access?
Basic Security Tips for Remote DesktopUse strong passwords. ... Use Two-factor authentication. ... Update your software. ... Restrict access using firewalls. ... Enable Network Level Authentication. ... Limit users who can log in using Remote Desktop. ... Set an account lockout policy.
What remote access protocols are secure?
POINT-TO-POINT TUNNELING PROTOCOL (PPTP) It's used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network. PPTP is a great option because it's simple and secure.
What is the most sophisticated form of remote access?
Remote Desktop SoftwareRemote Desktop Software The most sophisticated form of remote access enables users on one computer to see and interact with the desktop user interface of another computer.
What is secure remote access VPN?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
What allows for secure remote console access?
You can enable remote access (dial-up or VPN), Network Address Translation (NAT), both VPN and NAT, a secure connection between two private networks (site-to-site VPN), or you can do a custom configuration to select any combination of these, as shown in Figure 14.25.
What are the three types of remote connections?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
Why RDP is not secure?
The risks of such exposure are far too high. RDP is meant to be used only across a local area network (LAN). Since RDP hosts support a listening port awaiting inbound connections, even the most secure installations can be profiled as a Windows Operating System and its version.
Is RDP secure without VPN?
Remote Desktop Protocol (RDP) Integrated in BeyondTrust Establishing remote desktop connections to computers on remote networks usually requires VPN tunneling, port-forwarding, and firewall configurations that compromise security - such as opening the default listening port, TCP 3389.
How do engineers secure remote access to employees?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
What tools do businesses use to protect their networks from external threats?
Network Security Tools and TechniquesAccess control. If threat actors can't access your network, the amount of damage they'll be able to do will be extremely limited. ... Anti-malware software. ... Anomaly detection. ... Application security. ... Data loss prevention (DLP) ... Email security. ... Endpoint security. ... Firewalls.More items...•
What are the two methods that the user can use to access the device remotely?
Today, remote access is more commonly accomplished using:Software: Using a secure software solution like a VPN.Hardware: By connecting hosts through a hard-wired network interface or Wi-Fi network interface.Network: By connecting via the internet.
What are the secure methods the remote users can use to connect to the internal network to perform file operations?
A VPN is a private network that uses a public network (usually the internet) to connect remote sites or users together. The VPN uses "virtual" connections routed through the internet from the business's private network or a third-party VPN service to the remote site or person.
What are security considerations for remote users examples?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
What are the benefits of industrial remote access?
Industrial remote access provides instant connectivity to machines anywhere, anytime. You can respond quickly to operational issues, minimize facil...
How to check if remote access is enabled?
The SiteManager Industrial IoT Gateway features a digital input that you can link to your operator panel or a physical switch, so that only when t...
Is it IPSec or SSL VPN?
Neither; the Secomea Solution is based on “Relay VPN,” which uses proxy technology instead of routing. This overcomes the network challenges of tra...
Does Secomea remote access allow full VPN access to equipment?
Yes. Although Secomea uses Relay VPN, the result is the same. Secomea’s remote access solution gives you transparent UDP/TCP access via Layer3 and...
How do I connect remotely to a machine from a PC?
The Secomea LinkManager Client software creates a transparent VPN connection directly to industrial devices such as PLC’s and HMI’s through an Io...
Does Secomea Remote Access use a Cloud service?
Secomea Remote access relies on an Internet based server called GateManager. You can have a free account on one of Secomea’s global GateManager s...
What are the benefits of industrial remote access?
What are the benefits of industrial remote access?#N#Industrial remote access provides instant connectivity to machines anywhere, anytime. You can respond quickly to operational issues, minimize facility downtime, and reduce time and travel costs. Remote access is key to productivity and increased uptime.
What is Secomea Remote Access?
With Secomea’s Industrial Remote Access to connected machines, you can provide fast and effective support and maintenance on equipment without compromising the high security demands that are expected from your customers. The Secomea SiteManager industrial IoT gateway is installed on the machine as software or hardware with multiple connection options, and access can be controlled to comply with the strictest IT policies. With integrated fleet management and alarm features, you can also support your customers in surveillance operations remotely.
What is IoT infrastructure?
IoT infrastructures interconnect building equipment with centrally monitored and controlled systems. Buildings are often maintained by many different service providers and using varying types of equipment for HVAC, lighting, elevators, etc. This presents a high–risk vulnerability to cybersecurity attacks. The Secomea Industrial Remote Access Solution provides an industrial IoT platform that secures on-demand remote access to selected equipment, and also secure tunneling to static surveillance using control protocols such as BACnet. You can easily manage who has remote access to which equipment in the building via drag-and-drop user access management.
What is a secomea solution?
The Secomea Solution is designed to address secure remote access needs at all scales; from small, medium, and enterprise-scale machine vendors servicing thousands of remote machines, to large-scale factories with complex global infrastructures.
Does Secomea use VPN?
Yes. Although Secomea uses Relay VPN, the result is the same. Secomea’s remote access solution gives you transparent UDP/TCP access via Layer3 and even Layer2, to specific devices, or entire networks, all depending on the type of “agent” configured on the IoT gateway that you have been granted access to.
See How the Remote Access for Industrial Automation Solution Works
Dive into the functionality that makes up this complete remote access solution.
A Complete Industrial Remote Access Solution
FactoryTalk Remote Access software is part of Remote Access for Industrial Equipment, a complete solution, which also includes the Stratix® 4300 Remote Access Router hardware. Together, these products enable secure access to industrial machines, skids, and assets wherever you are.
FactoryTalk Remote Access Software: Making More Possible
Being able to access customer equipment from anywhere and at any time can open a world of possibilities. This level of support goes the distance so your customers can, too.
Industrial Remote Access Software At a Glance
With FactoryTalk Remote Access software, you can provide installation support, programming upgrades, break-fix applications, remote services, and diagnostics – right where you are.
Protect the Work You Do
We know that security is a critical issue. With FactoryTalk Remote Access software, you can initiate and maintain secure connections, from anywhere.
What is a second OEM?
The second OEM sells a machine that does not require video monitoring. Local operator interface is provided by an embedded HMI with limited data logging and storage functionality. The OEM machine builder needs two kinds of remote access. The first is VPN access to remotely troubleshoot, debug, and program the machine’s PLC and HMI. Second, the OEM and its customers want to monitor the machine’s most important operating parameters on dashboard screens from remote devices, such as smartphones and tablets.
Does an OEM have an IT department?
The OEM machine builder does not have an IT department, just one part-time person who set up the internal network.
Can remote users access automation components connected to the local router through the VPN tunnel?
Once connected, remote users can access automation components connected to the local router through the VPN tunnel. Unlike option 1, there is no cloud server between the two devices with either method of connection: VPN router to VPN router, or VPN router to VPN software client.
A cyber attack on your industrial environment is likely to originate via your third parties
With the advancement of digitization and the industrial internet of things (IIoT), industrial environments are increasingly interconnected and remotely accessible. Historically, this hasn’t been the case, and manufacturers haven’t had to focus on cybersecurity.
Request a Demo
Request a demo to see how SecureLink’s Vendor Privileged Access solution helps identify, audit, and control third parties.
What is the port 443?
Cloud-based remote access solutions build outbound connections using the outbound service port 443 (normally reserved for secure website access using SSL) to access remote equipment, which does not present any issues for IT departments managing plant networks. Cloud-based remote access solutions can work in harmony with the IT security policies of machine operators.
What are security parameters in remote access?
In a cloud-based remote access solution, security parameters—such as hash functions, encryption/decryption algorithms, etc.—are configured automatically. Machine builders do not need to configure these parameters; they just need to click on a button to establish a remote connection.
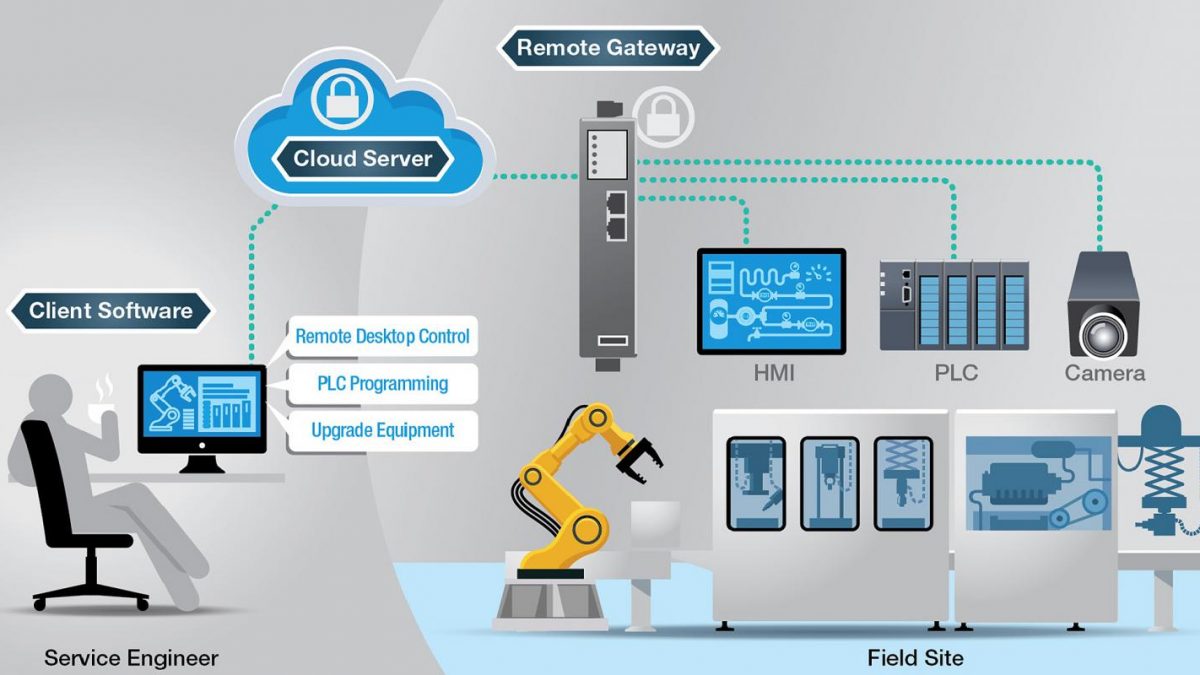
What is cloud based remote access?
Cloud-based remote access is a new type of remote access solution that enables flexible remote access to field machines. The network topology of a cloud-based remote access solution is composed of three components: a remote gateway, a cloud server, and client software. Remote gateways are connected to field equipment in order to remotely access and control them. Client software is installed on the engineer’s PC or desktop. The cloud server can be installed on a cloud-based platform such as Amazon Web Services or Microsoft Azure. The remote gateway and client software will both initiate outbound secure connection requests to the cloud server.
What is VPN connection?
VPN connections between machine builders and machine operators are usually site-to-site connections, which typically provide machine builders with remote access to all local devices in a plant’s network. Plant operators want to restrict the network access of machine builders so that only a selected set of machines are accessible. For example, plant operators need ways to restrict access by plant equipment and specify the applications that can be accessed remotely to prevent unauthorized access to production information and unauthorized or accidental operation of plant equipment. The only way to mitigate this risk is for IT departments to create separate end-to-end connections using VPN technology, which as previously noted, is complex and expensive, thereby drastically increasing setup and maintenance costs.
What are the parameters of an authentication?
Multiple parameters, including IP address, domain name, key ID, authentication mode, a suitable encryption algorithm, and an efficient hash function, all need to be configured to properly establish connectivity with remote machines and to be able to exchange the necessary authentication keys and data. This process is complex, time consuming, and requires extensive IT knowledge, which a majority of automation engineers may not be familiar with.
How to achieve higher level of security?
One way to achieve a higher-level of security is to have different pre-shared keys or X.509 certificates for each VPN tunnel. When the number of VPN tunnels/connections required are few, it is easy to manage the keys or certificates for these connections. However, as the number of VPN tunnels grows, it becomes very hard to manage these keys and certificates. When VPN servers or client systems are changed, certificates have to be regenerated. When a certificate expires, a new certificate has to be assigned and reloaded to the system, which further complicates maintenance.
What is a VNC?
Virtual Private Networking (VPN) and Remote Desktop Connection (RDC), the latter of which Virtual Network Computing (VNC), are two common methods used to remotely access machines and equipment at field sites.
