
How does Secure Remote Access work?
- Protect endpoints for all remote users and their devices - Securing endpoints in a datacenter is fairly simple compared...
- Prevent remote access from increasing attack surface - Setting up remote access can present risks to the organization.
- Adopt multifactor authentication - Two factor authentication (2FA) requires users to provide...
How to setup RDP for remote access?
- Get the IP address for that PC using the procedure we outlined previously.
- Use Registry Editor to change the Remote Desktop listening port number on that PC.
- Make notes on which port number goes with which IP address.
How to properly secure remote access?
- Windows or Mac login when connecting remotely
- Request permission to connect to the user’s computer
- Automatically blank the remote screen when connected
- Automatically lock remote computer when disconnected
- Lock the remote computer’s keyboard and mouse while in session
- Lock the streamer settings using Splashtop admin credentials
What is the best remote access for PC?
What is the Best Remote Desktop Software?
- GoToMyPC. GoToMyPC is the best remote desktop software on this list. ...
- AnyDesk. AnyDesk is one of the most popular remote desktop software platforms, used by over 100 million users globally.
- LogMeIn. ...
- Parallels. ...
- Splashtop Business Access. ...
- Zoho Assist. ...
- ConnectWise Control. ...
- RemotePC. ...
- TeamViewer. ...
- Remote Utilities for Windows. ...
How secure is enabling remote access?
- iOS/Android: Swap album and artist titles in CarPlay/Android Auto.
- iOS/Android: Rare crash if your library had ~200,000 items.
- Desktop: Reduce hover play background size to allow clicking on poster.
- iOS: Crash for high CPU in some cases if server disks were offline.
- CarPlay/Android Auto: Show all albums when album types are enabled.
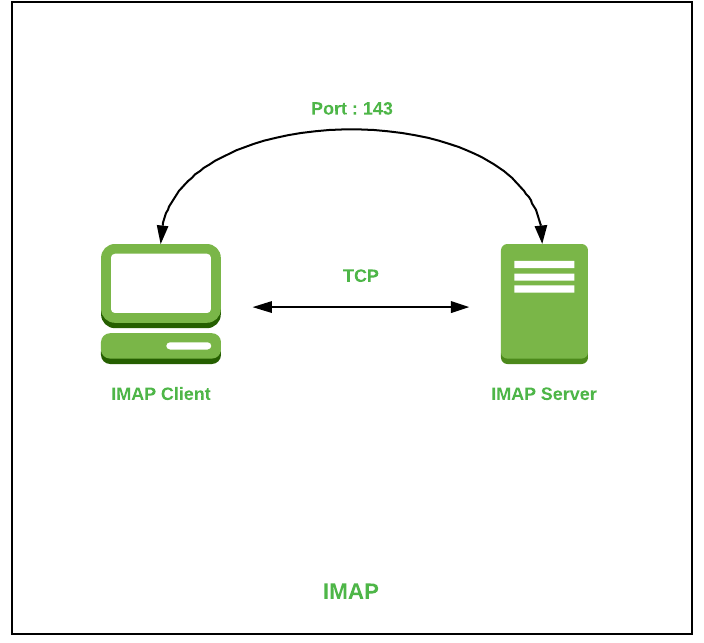
Who is more secure protocol for remote login?
While Remote Desktop is more secure than remote administration tools such as VNC that do not encrypt the entire session, any time Administrator access to a system is granted remotely there are risks. The following tips will help to secure Remote Desktop access to both desktops and servers that you support.
Which method of remote access is the most secure?
Implement a Secure Connection for Remote Network AccessWired Connection: A wired connection is the most secure method for remote network access.Home Wi-Fi: The second most secure network connection is using a secured home Wi-Fi connection.More items...•
What is secure remote access?
Secure Remote Access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization's digital assets and prevent the loss of sensitive data.
Which protocol for remote access is more secure and why?
POINT-TO-POINT TUNNELING PROTOCOL (PPTP) It's used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network. PPTP is a great option because it's simple and secure.
How do you secure remote access to employees?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
What are three examples of remote access locations?
What Is Remote Access?Queens College.Harvard University Extension School.
Which protocol is used for encrypted remote access to a server?
IPsec. Internet Protocol security (IPsec) can be used as a remote access tunneling protocol to encrypt traffic going over the Internet.
What is the technology used in remote access?
virtual private network (VPN) technologyRemote access software is usually accomplished using a virtual private network (VPN) technology. This type of method is more available compared to others since it is a more secure remote access software that connects the user and the enterprise's networks through an internet connection.
What is remote access protocol?
A remote access protocol is responsible for managing the connection between a remote access server and a remote computer. It’s necessary for desktop sharing and remote access for help desk activities. The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), ...
What is PPP protocol?
PPP is a remote access protocol that allows you to implement TCP/IP. It establishes a connection via point-to-point links (i.e., dedicated leased lines and dial-up). PPP is used most often for remote connections to LANs and ISPs. PPP utilizes the Link Control Protocol (LCP), which tests the link between client and PPP host ...
How to use PPTP?
To use PPTP, you’ll have to set up a PPP session between the server and the client, usually over the internet. Once the session is established, you’ll create a second dial-up session. This dial-up session will use PPTP to dial through the existing PPP session.
What is PPTP in a network?
PPTP is a remote access protocol, based on PPP, created by Microsoft. It’s used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network.
What is RDP in Citrix?
Finally, there is the RDP, which is very similar to the Independent Computing Architecture (ICA) protocol used by Citrix products. RDP is utilized to access Windows Terminal Services, which is a close relative of the product line provided by Citrix WinFrame.
What are the disadvantages of PPP?
Unfortunately, one of PPP’s disadvantages is it attracts a high overhead and isn’t compatible with certain older configurations. For technicians, PPP is generally considered easily configurable. Once you connect the router via PPP, it assigns all other TCP/IP parameters for you.
What is managed services provider?
As a managed services provider (MSP), you likely already work with remote access protocols on a daily basis. But learning how to best explain the various types of remote access protocols and their advantages and disadvantages to customers is critical in helping them understand your decisions—and why they should trust you and your services.
What is secure remote access?
Secure remote access refers to any security policy, solution, strategy or process that exists to prevent unauthorized access to your network, its resources, or any confidential or sensitive data. Essentially, secure remote access is a mix of security strategies and not necessarily one specific technology like a VPN.
What technologies are used for secure remote access?
Secure remote access is comprised of a multitude of security solutions and technologies. Some of the most prominent include the following:
Secure remote access solution
Enables employees with precise access to the applications and data required to do their job from anywhere.
Why is secure remote access important?
With the work from home shift in the workforce, endpoints are accessing corporate networks from multiple locations. Today, employees’ home networks are often the originating point for network connections, multiplying the risk on both home and corporate networks.
What are the benefits of secure remote access?
While the benefits of secure remote access are numerous, there are four key advantages in which to focus on:
Can secure remote access be achieved without VPN?
Yes. A robust cloud-based, highly secure remote access solution can provide unified protection for virtually all users against web-based threats — independent of a VPN connection.
How can AT&T help organizations with secure remote access?
AT&T Cybersecurity is uniquely positioned to help organizations address these immediate challenges with an eye toward the future by helping them balance connectivity, collaboration, and cybersecurity affordably.
What is SASE security?
SASE is a new security model, leveraging software-defined networking (SDN), that helps users connect securely to remote data centers. It includes technologies like cloud access security broker (CASB), secure web gateway (SWG), firewall as a service (FWaaS), and ZTNA (ZTNA, described above, can be a component within a SASE solution).
What is RDP server?
RDP is a protocol originally developed by Microsoft, which enables remote connection to a compute system. RDP is also available for MacOs, Linux and other operating systems. The RDP server listens on TCP port 3389 and UDP port 3389, and accepts connections from RDP clients.
What is multifactor authentication?
Multi-factor authentication (MFA) is a secure access control process that combines multiple credentials to verify the identity of a user. It is especially important, and is commonly used, for secure remote access.
What is zero trust security?
In the zero trust security model, users only have the rights they need to perform the role they have. All user accounts and devices on the network are not trusted by default. This is very different from traditional security solutions that allow users full access to the target network.
Can an attacker compromise a VPN?
When an attacker compromises a VPN (virtual private network), they can easily gain access to the rest of the network. Historically, many companies deployed VPNs primarily for technical roles, enabling them to access key IT systems. Today, all users, including non-technical roles, might access systems remotely using VPN. The problem is that many old firewall rules allow access for VPN clients to almost anything on the network.
Who needs privileged accounts?
Many organizations need to provide privileged accounts for two types of users: employees and external users, such as technicians and contractors. However, organizations using external vendors or contractors must protect themselves from potential threats from these sources.
Is remote access technology progressing?
Remote access technology made great progress. There are many new ways for users to access computing resources remotely, from a variety of endpoint devices. Here are some of the technologies enabling secure remote access at organizations today.
What is the line of defense for remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly.
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
Why is IPSec VPN important?
IPSec VPN connections are also important for an employee who needs widespread access to the company’s network. A word of warning: If you are using IPSec VPN for remote access, but you are not deploying Internet Key Exchange (IKE, certificates) as an authentication method, the connection will be vulnerable.
Why is IPSEC used?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
What is client side VPN?
The client-side software is responsible for establishing a tunneling connection to the RAS and for the encryption of data. RAS VPNs are appropriate for small companies, requiring a remote access for a few employees. However, most serious businesses have moved on from this basic form of VPN connection.
What is IPSEC protocol?
IPSec: IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect data flows between hosts and security gateways. The unique feature of IPSec is that it operates at the Network Layer of the Open Systems Interconnection (OSI) protocol model.
Should a company use IPSEC VPN?
A company should go for IPSec VPN remote access if it has a strong networking department with the ability to configure each employee’s hardware device individually (installing client software, enforcing security policies etc.).
How to secure RDP?
Ananth: There are some built-in, no-cost defenses that can secure RDP. These include: 1 Patching: Keep servers especially up to date. 2 Complex passwords: Also use two-factor authentication, and implement lockout policies. 3 Default port: Change the default port used by RDP from 3389 to something else via the Registry. 4 Windows firewall: Use the built-in Windows firewall to restrict RDP sessions by IP address. 5 Network Level Authentication (NLA): Enable NLA, which is non-default on older versions. 6 Limit RDP access: Limit RDP access to a specific user group. Don't allow any domain admin to access RDP. 7 Tunnel RDP access: Tunnel access via IPSec or Secure Shell (SSH).
What are some built-in, no-cost defenses that can secure RDP?
Ananth: There are some built-in, no-cost defenses that can secure RDP. These include: Patching: Keep servers especially up to date. Complex passwords: Also use two-factor authentication, and implement lockout policies. Default port: Change the default port used by RDP from 3389 to something else via the Registry.
What is the RDP vulnerability?
Most notably, 2019 gave rise to a vulnerability known as BlueKeep that could allow cybercriminals to remotely take over a connected PC that's not properly patched.
How many systems are exposed to the internet via RDP?
Web crawlers like shodan.io make it easy for attackers to quickly identify vulnerable public-facing machines. Worldwide, more than two million systems are exposed to the internet via RDP, of which more than 500,000 are in the US.
Do all RDP instances need a VPN?
Gamblin: Without many exceptions, all RDP instances should require multiple levels of access and authentication controls. This would include the use of a VPN to access an RDP instance and requiring a second factor (like Duo) for authentication.
Can RDP be placed on the internet?
Some major organizations place RDP directly on the internet, but most (hopefully) are doing this unknowingly. Checking on this is pretty simple; just fire up your favorite internet-wide scanner and look at all the RDP instances directly exposed. Ananth: There are some built-in, no-cost defenses that can secure RDP.
A single, easy-to-use platform that provides secure remote access to vendors
Current methods fail to properly secure third party remote access by identifying each individual, controlling their access, and auditing their activity.
What Is Secure Remote Access?
In today’s business environment, remote access to systems, data, and servers is a common and necessary occurrence. This remote access can be for employees, who are working from home or distributed remotely, and it can also be for third parties, such as contractors, technology vendors, business partners, and consultants.
Is Your Remote Access Secure?
Evaluate your current vendor security practices and learn the industry standards for data protection.
Why Does Secure Remote Access Matter?
If you’re realizing you don’t have all of those 4 key elements in place, but are wondering if it’s worth the effort and investment to make those changes, consider the potential costs of failing to do so.
What To Look For In A Secure Remote Access Method
Often individual identification is a key element to meet regulatory requirements and general security best practices. You need to know who is in your network, and ensure that the person with access is who they say they are, and that they should even have access (unlike, a bad actor or external hacker). At minimum, this should include:
What is SRP protocol?
The SRP protocol has a number of desirable properties: it allows a user to authenticate themselves to a server, it is resistant to dictionary attacks mounted by an eavesdropper, and it does not require a trusted third party. It effectively conveys a zero-knowledge password proof from the user to the server.
What is SRP authentication?
In layman's terms, during SRP (or any other PAKE protocol) authentication, one party (the "client" or "user") demonstrates to another party (the "server") that they know the password, without sending the password itself nor any other information from which the password can be derived. The password never leaves the client and is unknown to ...
How many passwords can be guessed per connection attempt?
In revision 6 of the protocol only one password can be guessed per connection attempt. One of the interesting properties of the protocol is that even if one or two of the cryptographic primitives it uses are attacked, it is still secure. The SRP protocol has been revised several times, and is currently at revision 6a.
Is SRP more secure than SSH?
In cases where encrypted communications as well as authentication are required, the SRP protocol is more secure than the alternative SSH protocol and faster than using Diffie–Hellman key exchange with signed messages. It is also independent of third parties, unlike Kerberos.
Does a password leave the client?
The password never leaves the client and is unknown to the server. Furthermore, the server also needs to know about the password (but not the password itself) in order to instigate the secure connection.
Can a man in the middle guess a password?
Like all PAKE protocols, an eavesdropper or man in the middle cannot obtain enough information to be able to brute-force guess a password or apply a dictionary attack without further interactions with the parties for each guess. Furthermore, being an augmented PAKE protocol, the server does not store password-equivalent data.
Does augmented poke store passwords?
Furthermore, being an augmented PAKE protocol, the server does not store password-equivalent data. This means that an attacker who steals the server data cannot masquerade as the client unless they first perform a brute force search for the password. In layman's terms, during SRP (or any other PAKE protocol) authentication, ...
What is SRP protocol?
SRP protocol consists of many calculations, back-and-forth communication between client & server, and complex terms to understand. Luckily since its an open protocol several implementations available to make life easier,
What is zero knowledge protocol?
It is a zero-knowledge proof protocol, where the server doesn’t have to store password equivalently information (hashed version), and clients can securely authenticate to the server. And an eavesdropper or man-in-the-middle cannot obtain any meaningful information to perform an attack.
What is SRP in a network?
SRP — registration network request. As you can see in the Request payload, the password was never sent, instead, the client sends ( username, salt, and verifier) to the server. This will be stored on the server-side and the verifier is never transmitted back again.
Can an attacker eavesdrop on a server?
An attacker can eavesdrop ( MITM attack) communication between client and server and can acquire the password. What we needed, in this case, is a strong Zero-knowledge proof (without transferring password) system that does mutual authentication on the client & server. Let's look at a shy and less popular implementation called Secure Remote Password ...
Is hashed passwords secure?
Hashed passwords offer a good trade-off between simplicity and security but for a piece of highly sensitive information or system it has its own drawbacks, It needed a trusted server to securely process & store the hashed passwords (which promises not to log passwords 😀)
Is SRP a strong password?
SRP protocol offers the right amount of flexibility, strong security, and user convenience. So we don't have to reinvent the wheel and use SRP as the Strong password system, even a low entropy password that can be used securely.

Serial Line Internet Protocol (Slip)`
Point-To-Point Protocol
- PPP is a remote access protocol that allows you to implement TCP/IP. It establishes a connection via point-to-point links (i.e., dedicated leased lines and dial-up). PPP is used most often for remote connections to LANs and ISPs. PPP utilizes the Link Control Protocol (LCP), which tests the link between client and PPP host and specifies PPP client configuration, to communicate between h…
Point-To-Point Tunneling Protocol
- PPTP is a remote access protocol, based on PPP, created by Microsoft. It’s used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network. PPTP is a great option because it’s simple and secure. To use PPTP, you’ll ha...
Windows Remote Access Services
- Windows 2000 and Windows NT let users dial up a server and connect to both the server and the server’s host network. This is referred to as RAS, which is used in smaller networks where a dedicated dial-up router would not be possible or practical. With a RAS setup, you can connect a modem to a Windows 2000 or Windows NT server and configure the modem as dial-out only, di…
Remote Desktop Protocol
- Finally, there is the RDP, which is very similar to the Independent Computing Architecture (ICA) protocol used by Citrix products. RDP is utilized to access Windows Terminal Services, which is a close relative of the product line provided by Citrix WinFrame. RDP offers the same core functions as ICA, although there are some limitations. RDP provides remote access for Windows clients o…