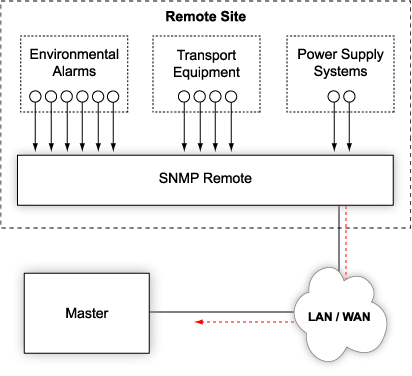
SNMP Remote Operations Overview
- SNMP Remote Operation Requirements. To use SNMP remote operations, you should be experienced with SNMP conventions. ...
- Setting SNMP Views. All remote operation MIBs supported by Junos OS require that the SNMP clients have read-write privileges.
- Setting Trap Notification for Remote Operations. ...
- Using Variable-Length String Indexes. ...
- Enabling Logging. ...
Full Answer
How do I configure a remote user to use SNMP?
To configure a remote user, specify the IP address or port number for the remote SNMP agent of the device where the user resides. Also, before you configure remote users for a particular agent, configure the SNMP engine ID, using the snmp-server engineID command with the remote option.
How do I accept SNMP requests on my Network?
To accept SNMP requests from any host on the network, regardless of identity, click Accept SNMP packets from any host. To limit the acceptance of SNMP packets, click Accept SNMP packets from these hosts, click Add, and then type the appropriate host name, IP, or IPX address in the Host name, IP or IPX address box. Click Add.
What is simple network management protocol (SNMP)?
The Microsoft Windows implementation of the Simple Network Management Protocol (SNMP) is used to configure remote devices, monitor network performance, audit network usage, and detect network faults or inappropriate access.
What is Microsoft Windows SNMP used for?
The Microsoft Windows implementation of the Simple Network Management Protocol (SNMP) is used to configure remote devices, monitor network performance, audit network usage, and detect network faults or inappropriate access.Important The Microsoft Windows SNMP API only supports protocol versions up to SNMPv2C.

Is SNMP remote?
About Service Controller SNMP You can monitor Service Controller remotely using the Simple Network Management Protocol (SNMP).
What is SNMP is used for?
Simple Network Management Protocol (SNMP) is an Internet Standard protocol used to monitor and manage the network devices connected over an IP. Different devices like routers, switches, firewalls, load balancers, servers, CCTV cameras, and wireless devices communicate using SNMP.
Is enabling SNMP a security risk?
SNMP is often used without any encryption, which makes it a security risk. This means that it is very important to protect your network from intrusion.
What can be monitored with SNMP?
SNMP can comprehensively monitor not only the network elements like routers and switches, but can also be used to monitor network servers. Details like server hardware description, physical location, IP address, available disk space and server uptime can be monitored through SNMP.
Is SNMP still used today?
SNMP may still be in use over the next decade, but it will be replaced as legacy networks become modernized. SNMP is dead; LONG LIVE NETWORK PROGAMMABILITY.
Is SNMP a TCP or UDP?
Typically, the SNMP protocol is implemented using the User Datagram Protocol (UDP). UDP is a connectionless protocol that works like the Transmission Control Protocol (TCP) but assumes that error-checking and recovery services are not required.
Should I turn off SNMP?
If you are worried about the risk with SNMP on your network, you can eliminate the risk by simply turning off SNMP on your network devices - but you will lose out on toner level monitoring and printer error statuses.
What happens if I disable SNMP?
By disabling SNMP, you significantly hamper your organizations ability to monitor infrastructure. Yes, other protocols like WMI, SOAP and the RESTful API are available, but they often incur much higher CPU utilization on the monitoring server and monitored devices.
Is it OK to disable SNMP?
The best way to avoid the SNMP risk is to disable the service. If you aren't actively using SNMP for network management, you have no reason to run it. If you aren't sure whether you need to run it, you probably don't need to run it.
What data can you get from SNMP?
Thanks to SNMP the monitoring software is able to retrieve the data from almost all devices – such as the CPU load of the firewall, the toner level of the network printer, the temperature in the server room, or all information on the interfaces of a switch.
How does SNMP monitoring work?
SNMP monitoring can be used to collect information from your entire fleet of network devices. SNMP relies on a client-server application model, where a software server component (the SNMP Manager) collects information by querying a software client component (the SNMP Agent), which runs on a network device.
Is SNMP push or pull?
SNMP operates in both push and pull mode. In the push mode, a managed device sends traps to an NMS upon a certain event, for instance when values exceed the defined limits (alarms).
What are the 3 components of SNMP?
SNMP consists of three key components: managed devices, agents, and the network management station (NMS). A managed device is a node that has an SNMP agent and resides on a managed network. These devices can be routers and access servers, switches, hubs, computer hosts, IP telephones, printers etc.
How does SNMP work in networking?
SNMP works by sending messages, called protocol data units (PDUs), to devices within your network that “speak” SNMP. These messages are called SNMP Get-Requests. Using these requests, network administrators can track virtually any data values they specify.
Do I need SNMP?
SNMP is without a doubt a very useful protocol for the management and monitoring of network devices, servers and applications. Whether it is secure or not really comes down to the level of risk which is acceptable to the organisation. SNMPv1 and v2c do have flaws in that authentication is almost non-existent.
Is SNMP a Layer 2 protocol?
Protocol details. SNMP operates in the application layer of the Internet protocol suite. All SNMP messages are transported via User Datagram Protocol (UDP).
Overview
This post explains the details of configuring the SNMP Credentials and Trap destination IP Address for monitoring the iDRAC7 in third party systems management consoles. The iDRAC7 enables the agent-free monitoring and capable of Out-of-Band management solution for the Dell 12G Servers.
Configuring the SNMP Credentials
Launch the iDRAC7 console and navigate to the Alerts section in the console.
Configuring multiple iDRAC7 devices using RACADM
A powerful feature of the Racadm utility is the capability to increase efficiency by automating the configuration of RACs. The administrators can use the racadm config command to deploy the settings specified in the configuration file to replicate the settings in multiple RACs in the environment.
Configuring SNMP Traps
Administrators can specify the SNMP trap settings by adding lines of code similar to the following in the RAC configuration file under the cfgTraps group:
What is SNMP remote operation?
A SNMP remote operation is any process on the router that can be controlled remotely using SNMP. Junos OS currently provides support for two SNMP remote operations: the Ping MIB and Traceroute MIB, defined in RFC 2925. Using these MIBs, an SNMP client in the network management system (NMS) can:
What is SNMP error code?
The SNMP error code returned in response to SNMP requests can only provide a generic description of the problem. The error descriptions logged by the remote operations process can often provide more detailed information about the problem and help you to solve the problem faster. This logging is not enabled by default. To enable logging, include the flag general statement at the [edit snmp traceoptions] hierarchy level:
Does Junos OS support SNMP?
All remote operation MIBs supported by Junos OS require that the SNMP clients have read-write privileges. The default SNMP configuration of Junos OS does not provide clients with a community string with such privileges.
Does Junos support snmpAdminString?
Junos OS does not handle SnmpAdminString any differently from the octet string variable type. However, the indexes are defined as variable length. When a variable length string is used as an index, the length of the string must be included as part of the object identifier (OID).
Can you associate an ACL to SNMP?
You can, as an option, associate an ACL to that command to filter the SNMP access to your device: snmp-server community <community> RO 10. access-list 10 permit X.X.X.X. Then, optionally, you can enable the device to send traps to your SNMP host (PRTG server):
Can PRTG monitor SNMP?
-Change back to 64bit counters in the compatibility options. Anyway, PRTG is probably not the best tool to SNMP monitor your devices, and also it uses one sensor per monitored interface.
What is SNMP application?
SNMP uses a distributed architecture consisting of management applications and agent applications. The SNMP service implements an SNMP agent. To use the information the SNMP service provides, you must have at least one host that is running an SNMP management application.
Is SNMP available for Windows?
[SNMP is available for use in the operating systems specified in the Requirements section. It may be altered or unavailable in subsequent versions. Instead, use Windows Remote Management, which is the Microsoft implementation of WS-Man.]
Can I use SNMP management software?
You can use third-party SNMP management software, or you can develop your own SNMP management software application. The following APIs are available for this purpose: SNMP Management API, a set of functions that can be used to quickly develop basic SNMP management systems.
What is SNMP in network management?
The network management system includes a schedule for querying agents. Each device on the network has a software agent installed on it, and the communication of SNMP takes place between the manager and the system management agents, making it unnecessary for the network manager to communicate directly with each device.
What is SNMP implemented on?
SNMP is implemented on a wide range of hardware including network devices such as switches, bridges, routers, and gateways, and also on endpoint equipment such as printers.
What is Solarwinds network performance monitor?
SolarWinds Network Performance Monitor EDITOR’S CHOICE This is the industry leader for network device monitoring and it uses SNMP to communicate with equipment and uses SNMP Trap receiver monitoring; The software installs on Windows Server 2016 or later and it is free to use on a 30-day free trial.
How many sensors does PRTG have?
So, there is a CPU Load Sensor, a Disk Free Sensor, and so on. In all, PRTG incorporates more than 200 sensors, giving you the ability to keep track of network performance over a wide range of factors. The manager software of PRTG can discover all available SNMP devices connected to the network.
What is the MIB in SNMP?
A central element of SNMP is the Management Information Base ( MIB). The MIB is a communications framework and dictates the format of data communicated between the network manager and each device agent. The SNMP standard allows for more than one manager. The responsibilities of each manager may overlap.
What is SNMP monitoring?
Simple Network Management Protocol or SNMP is a protocol for exchanging information between network devices. There are a lot of SNMP monitoring systems available on the market today that can detect SNMP traps in real-time and let you set alerts based on automatic or user-set trigger conditions. Trap details can be logged with the time ...
Why is Solarwinds used in multivendor networks?
SolarWinds is ideal for a multi-vendor network environment because it relies on the universal Simple Network Management Protocol to ensure interoperability.
What is SNMP in network?
The Simple Network Management Protocol (SNMP) is an application-layer protocol that provides a message format for communication between SNMP managers and agents. SNMP provides a standardized framework and a common language used for monitoring and managing devices in a network.
What is SNMP manager?
The Simple Network Management Protocol (SNMP) manager is a system that controls and monitors the activities of network hosts using SNMP. The most common managing system is a network management system (NMS).
What is SNMP MIB?
SNMP MIB. An SNMP agent contains MIB variables, whose values the SNMP manager can request or change through Get or Set operations. A manager can get a value from an agent or store a value in that agent. The agent gathers data from the SNMP MIB, the repository for information about device parameters and network data.
Can you enable multiple traps in Snmp?
If you enter the command without keywords, all trap types are enabled for the host. To enable multiple hosts, you must issue a separate snmp-server host command for each host. You can specify multiple notification types in the command for each host.
What is SNMP service?
The SNMP Service, when configured for an agent , generates trap messages that are sent to a trap destination, if any specific events occur. For example, you can configure the SNMP service to send a trap when it receives a request for information that does not contain the correct community name and does not match an accepted host name for the service.
How to configure SNMP agent?
Configure SNMP agent information 1 Click Start, point to Control Panel, point to Administrative Tools, and then click Computer Management. 2 In the console tree, expand Services and Applications, and then click Services. 3 In the right pane, double-click SNMP Service. 4 Click the Agent tab. 5 Type the name of the user or administrator of the computer in the Contact box, and then type the physical location of the computer or contact in the Location box.#N#These comments are treated as text and are optional. 6 Under Service, click to select the check boxes next to the services that are provided by your computer. Service options are:#N#Physical: Specifies whether the computer manages physical devices, such as a hard disk partition.#N#Applications: Specifies whether the computer uses any programs that send data by using TCP/IP.#N#Datalink and subnetwork: Specifies whether this computer manages a TCP/IP subnetwork or datalink, such as a bridge.#N#Internet: Specifies whether this computer acts as an IP gateway (router).#N#End-to-end: Specifies whether this computer acts as an IP host. 7 Click OK.
How to accept SNMP packets?
To limit the acceptance of SNMP packets, click Accept SNMP packets from these hosts, click Add, and then type the appropriate host name, IP, or IPX address in the Host name, IP or IPX address box.
How to get SNMP on Windows 10?
Click Start, point to Control Panel, point to Administrative Tools, and then click Computer Management. In the console tree, expand Services and Applications, and then click Services. In the right pane, double-click SNMP Service. Click the Agent tab.
How to send authentication trap?
Click Start, point to Control Panel, point to Administrative Tools, and then click Computer Management . In the console tree, expand Services and Applications, and then click Services. In the right pane, double-click SNMP Service. Click the Security tab . Click to select the Send authentication trap check box (if it is not already selected) ...
What is SNMP security?
Most SNMP security consists of two subsystems: The Security Module addresses the question of whether a message is authentic and timely (Internet delays can lead to the arrival of old messages) and identifies the originator. The Access Control Module identifies which objects are being managed and indicates whether the originator ...
What is SNMP public?
SNMP requests are accepted using one of two standard community names. Most SNMP agents use the terms “public” and “private” as the default settings for these names, making it very easy to set up for remote management.
How to deal with SNMP threats?
The easiest way to deal with SNMP threats is to set your firewall to block UDP ports 161 and 162 (and any other port you may have custom-configured for SNMP traffic) to the outside world.
Why is SNMP systeminfo string insecure?
SNMP is inherently insecure because SNMP messages are not encrypted.
What is SNMP in firewall?
SNMP provides an easy way for administrators to get topology information about their networks and even provides some management of remote devices and servers. However, you have to be very careful that you correctly block SNMP traffic at your firewall; otherwise, hackers can also use it to gather that valuable network information ...
When was SNMP developed?
SNMP is an Internet protocol developed in the 1980s when TCP/IP networks were blossoming and it was recognized that network management was becoming a major problem. In other words, SNMP was developed when access to the Internet was rare and very restricted. SNMP quickly became popular when RFC 1157 was published in 1990.
Is SNMPv3 a RFC?
There may be some hope for the future. The IETF is currently working on a new version of SNMP called SNMPv3, which does include some security enhancements. After years of work, SNMPv3 should soon be published as an RFC. Bottom line.

Purpose
- The Microsoft Windows implementation of the Simple Network Management Protocol (SNMP) is used to configure remote devices, monitor network performance, audit network usage, and detect network faults or inappropriate access.
Where Applicable
- SNMP uses a distributed architecture consisting of management applications and agent applications. The SNMP service implements an SNMP agent. To use the information the SNMP service provides, you must have at least one host that is running an SNMP management application. You can use third-party SNMP management software, or you can develop your own …
Developer Audience
- The APIs listed in the preceding section are designed for use by C/C++ programmers. Familiarity with SNMP and SNMPv2C, as well as a working knowledge of networking and network management concepts, are required.
Run-Time Requirements
- For more information about the operating system required to use a particular function, see the Requirements section of the reference page for that function.
Related Topics