
Third-party remote access is the system in which external users are able to connect with a defined network. The best third-party remote access platform will make sure that the connection is secure, controlled, and monitored at all times. Sadly, many enterprises still give their third-party vendors credentials that often provide privileged access.
What is third-party remote access?
Third-party remote access is the system in which external users are able to connect with a defined network. The best third-party remote access platform will make sure that the connection is secure, controlled, and monitored at all times. Sadly, many enterprises still give their third-party vendors credentials that often provide privileged access.
Why do companies allow remote access to vendors and services providers?
But many organizations are also allowing access to vendors and services providers because offices remain closed or they are restricting physical access to the office. Additionally, this third-party remote access is happening through organizations outsourcing specific tasks so that they can focus on their core business functions.
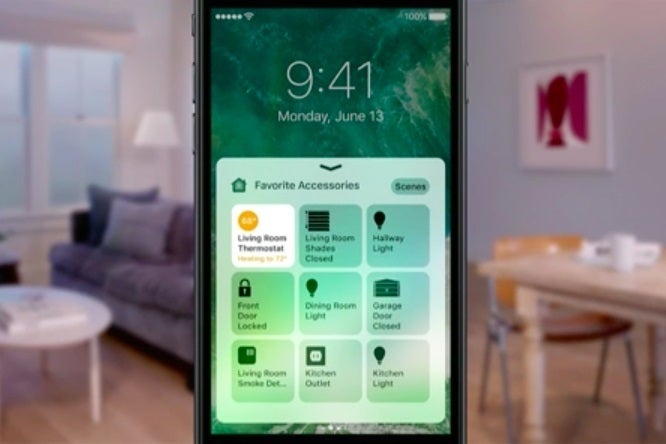
What are remote access utilities and how do they work?
These are exactly the scenarios that remote access utilities are made to handle. Remote access apps let you either access your home or office computer from another location, or allow others to have access to some or all of your files, as if they were actually sitting in front of your PC instead of somewhere else entirely.
Can my computer be remotely accessed?
The chances of your specific computer being remotely accessed, while not impossible, are very low. You can take steps to help prevent intrusions. Thanks! ↑ Yaffet Meshesha. Computer Specialist.

What is a third party connection?
Third Party Connection A direct connection to a party external to the Board. Examples of third party connections include connections to customers, vendors, partners, or suppliers.
What is third party VPN?
Third-party VPN services work by installing software, a browser plugin or a security hardware appliance between end devices and the internet. A VPN tunnel is then established between the end-user device and the service provider's VPN endpoint on the internet.
What are the three types of remote connections?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
What is considered remote access?
Remote access is the ability for an authorized person to access a computer or network from a geographical distance through a network connection. Remote access enables users to connect to the systems they need when they are physically far away.
What are the risks of third-party VPN services?
The Not-So-Good VPN Security RisksThird-party VPNs can't create or enforce policies that protect credentials. ... More secure VPN = Less productive workforce. ... High VPN support costs = Higher cost of doing business. ... All or nothing = VPNs create security risks. ... Lack of accountability creates third-party VPN risks.More items...•
Can my employer track my location through VPN?
Using VPN software will ensure that no one can know your real location by checking your IP address (internet address), whether it's your boss, clients, or IT department. What is this? You do need to get a subscription to a VPN service to do this.
What are the examples of remote access?
Examples of Remote AccessAllowing Employees At-Home Access To Work Devices. ... Employers Assisting Remote Employees When Needed. ... IT Specialists Troubleshooting Remote Devices. ... Employees Collaborating Easily Independent of Location. ... Remote Workers Accessing Their At-Home Computers from Portable Devices.More items...•
How do I set up remote access to my computer?
Set up remote access to your computerOn your computer, open Chrome.In the address bar, enter remotedesktop.google.com/access .Under “Set up Remote Access,” click Download .Follow the onscreen directions to download and install Chrome Remote Desktop.
What does a remote access server do?
A remote access server (RAS) is a type of server that provides a suite of services to remotely connected users over a network or the Internet. It operates as a remote gateway or central server that connects remote users with an organization's internal local area network (LAN).
How can I tell if someone is remotely accessing my computer?
How to Know If Someone is Accessing My Computer Remotely?Way 1: Disconnect Your Computer From the Internet.Way 2. ... Way 3: Check Your Browser History on The Computer.Way 4: Check Recently Modified Files.Way 5: Check Your computer's Login Events.Way 6: Use the Task Manager to Detect Remote Access.More items...•
Can someone remotely access my computer without my knowledge?
There are two ways someone can access your computer without your consent. Either a family member or work college is physically logging in to your computer or phone when you are not around, or someone is accessing your computer remotely.
Can someone control my computer remotely?
For any attacker to take control of a computer, they must remotely connect to it. When someone is remotely connected to your computer, your Internet connection will be slower. Also, many times after the computer is hacked, it becomes a zombie to attack other computers.
Is a VPN a third party app?
And one of the easiest ways to do that is using a third-party virtual private network, or VPN. As we've previously mentioned, a VPN is a service that allows users to connect to the internet via a third-party server which in-turn encrypts all of the user's data.
How do I download a free VPN for Windows 10?
Download Vpn Free For Windows 10 - Best Software & AppsHamachi. 2.3.0.78. 3.4. (41289 votes) ... IPVanish. 3.7.5.7. 4.2. (521 votes) ... Free VPN. 3.2. 3.3. (3551 votes) ... Avast Secure Browser. (551 votes) Free Download for Windows. ... iTop VPN. 1.3.0.967. 4.3. ... Chedot. 86.0.4240.932. 4.5. ... VyprVPN for Windows. 4.3.1.10763. 3.7. ... Windscribe. 2.4.10. 4.2.More items...
How can incorrectly configuring VPN clients lead to a security breach?
How can incorrectly configuring VPN clients lead to a security breach? A virtual private network (VPN) operates pretty much in binary mode: Either the secure connection is established or it isn't. If the secure connection does not successfully complete, it is not possible to send traffic to the secured resources.
Step 1: Map the remote access
What, who, from where, when, and why — all these aspects should be considered.
Step 2: Know who is explicitly accessing what and for what reason
This should tie back to either firewall rules, privileged access management (PAM) rules, data access rules, or application permissions.
Step 3: Monitor and audit the remote access
Once the access has been mapped, a matrix can be created of who is accessing what from where and when (then links can be defined). At this point, consideration of systems that monitor access is undertaken to decide on an effective system to implement.
Step 4: Report the third-party access
By reporting the access, the organization has visibility and can determine if the access is still required. For instance, if there has been no access for several months, an informed decision can be made regarding if the third-party access is still required going forward.
Step 5: Review the third-party access
Having a rigorous and scheduled third-party access review system is essential. This means that access is reviewed. A small committee, namely the stakeholder of the system and authority, should take responsibility for this process. Together, the committee with the stakeholder, decides if the access is still required.
Multifactor authentication (MFA)
When accessing systems, there is no reason not to use MFA. It’s vital as it’s a tough hurdle for attackers to overcome. This should be used as the first line of defense and mandatory third-party access control.
Centralized access management
Managing the access centrally helps with the technical and administrative actions that need to be performed. If access can be seen and controlled centrally, it is easier to manage. In the absence of a central system, the organization should consider implementing one so that the management is simple. Simple and secure often go hand in hand.
What is Shodan's spike in remote desktop protocol?
From the onset of the Covid-19 outbreak until the end of March, Shodan (a global search engine that scans and indexes internet-connected devices) tracked a 41% spike in Remote Desktop Protocol...
Who is Tonya Ugoretz?
Tonya Ugoretz, deputy Assistant Director of the FBI...
What is a crisis in remote access security?
A crisis in third-party remote access security. Over half of organizations have experienced a data breach caused by third parties that led to the misuse of sensitive or confidential information. An even larger number attribute the cause of the data breach to granting too much access to third parties.
Who sponsored the Ponemon report 2021?
The 2021 Ponemon report sponsored by SecureLink takes a deep dive into the third-party lifecycle, the cyber risks associated with each stage, and the statistics that reinforce the crisis in third-party management.
What is remote access app?
Remote access apps let you either access your home or office computer from another location, or allow others to have access to some or all of your files, as if they were actually sitting in front of your PC instead of somewhere else entirely.
What is GoToMyPC?
GoToMyPC is a mature, easy-to-use remote access software with the best available balance between features and ease of use. Unless you need support for Linux or enterprise-level operating systems, this is the app you want.
Is VNC Connect secure?
VNC Connect is solid, secure, and simple to use, once you get the hang of it. It has fewer features than other corporate-level remote access software, but it's also a lot less expensive.
Tips
Be aware that your computer may appear to turn on without input to install updates. Many modern computers are set to install system updates automatically, usually at night when the computer is not being used. If your computer appears to turn on without your input when you're not using it, it is likely waking from Sleep mode to install updates.
About This Article
This article was co-authored by Yaffet Meshesha and by wikiHow staff writer, Nicole Levine, MFA. Yaffet Meshesha is a Computer Specialist and the Founder of Techy, a full-service computer pickup, repair, and delivery service. With over eight years of experience, Yaffet specializes in computer repairs and technical support.
Third-Party Remote Access Definition
- Third-party remote access is the system in which external users are able to connect with a defined network. The best third-party remote access platformwill make sure that the connection is secure, controlled, and monitored at all times. Sadly, many enterprises still give their third-party vendors credentials that often provide privileged access. Fr...
Third-Party Best Practices: Securing Your Access Points
- Now is the time to get your vendors and platform aligned. The best way to protect your most valuable assets and make sure your vendors stay safe in case of a breach is to practice critical access management. Made up of three pillars (access governance, access control, and access monitoring), employing the best techniques to practice third-party access management is the be…
Third-Party Access Control
- Access control, or having precision and control over when and how a person can exercise their access rights, can apply to both internal and external users. It’s especially important to apply types of access control to third parties, as they carry with them the biggest risk. Access control is an additional layer of security on top of access governance that helps protect those assets that …